product
- Why choose Splunk
- Installation record
- price
- Splunk Enterprise Security
- Splunk Phantom (SOAR)
- Splunk ITSI (Next Generation IT Operations)
- Splunk Observability Cloud
- Splunk UBA
- Macnica CSIRT App Basic
- App for Splunk for Financial Institutions
- Splunk Analytics for Hadoop
- About Apps
- Splunk Edge Hub
- What is Splunk
service
- Dashboard/SPL Creation Pack [Implementation/Building Support]
- Version upgrade service [implementation and construction support]
- Smart Security Monitoring App [Original App/Service]
- Splunk × LANSCOPE Original App [Original App/Service]
- Security Monitoring App for Box [Original App/Service]
- Cloud Security Monitoring App [Original App/Service]
- List of services
Specifications/Technical Information
Application for evaluation machine
- FAQ

Splunk
Splunk
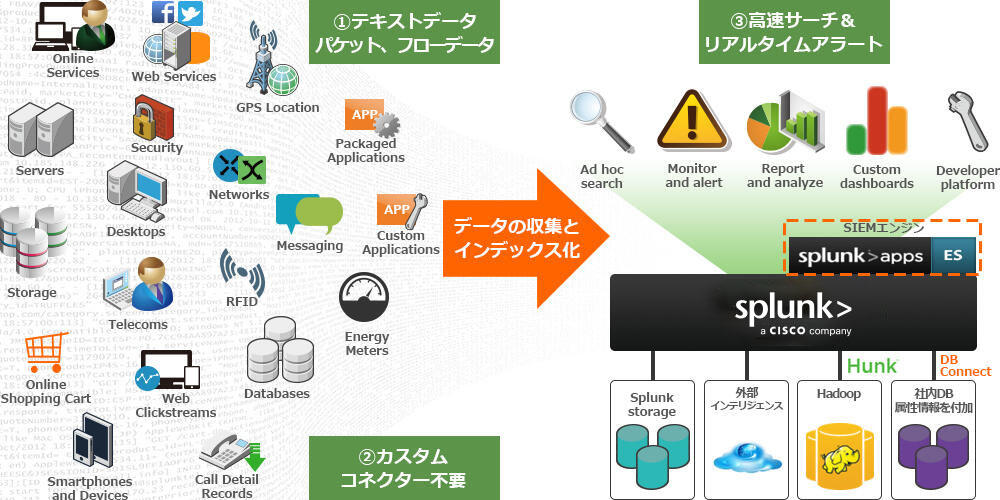
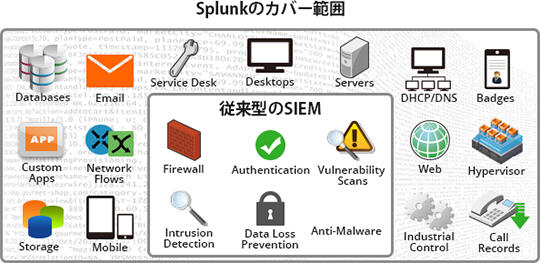
About the SIEM function
What SIEM features does Splunk provide?
Splunk can import data from any device or system if it is converted into text, and can be searched and analyzed.
There are two ways to use Splunk as a SIEM: create detection rules only with Splunk and use it as a SIEM, or implement a paid add-on called Enterprise Security with correlation rules and use it as a SIEM.
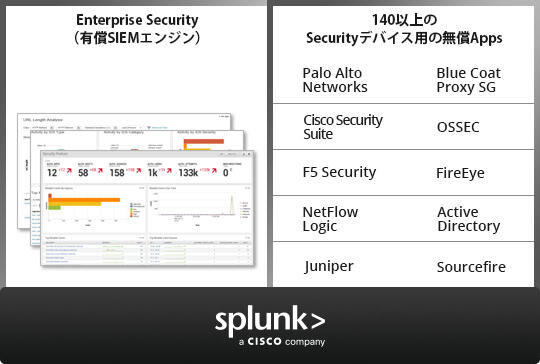
Dedicated Apps Developed for Security
By combining Enterprise Security, which is a paid App developed for SIEM, and free Apps for individual devices, it is possible to utilize Splunk according to the customer's environment and usage.
What is your track record as a SIEM function?
Splunk as a SIEM
It is positioned as a leader in the SIEM category of the Gartner Magic Quadrant, and the number of cases where Splunk is adopted as a SIEM is increasing.
Splunkはセキュリティ専門製品ではないにもかかわらず、SIEM製品と同格の評価を受けております。さらにワールドワイドで9000社以上の導入実績があるなか、2800社以上がセキュリティ用途でSplunkを導入しています。
Why Splunk is rated as a "SIEM" feature so much even though it's not a security product
- Security-specific correlation analysis and alert rules
- Supports logs from many security devices
- Rich report templates
- Prioritize the importance of alerts from security devices
- A ticketing system that allocates responsibility for investigations and shares investigation status

- Unsupported data source, schema definition
- Search function for problem identification, analysis speed, scalability

- Realize data collection, storage, search, and alerts in one product
- 高いスケーラビリティ (200TB/日)
- Runs on common hardware
- The same data can be used for purposes other than security, high ROI results
- Any data can be imported as long as it is text
- Strengths in high-speed search and data extraction
- Statistical analysis using past data
| Common SIEM products | Splunk ES | |
|---|---|---|
| Correlation analysis | Rule base (known/predefined patterns) | Rule-based Statistics-based (unknown, suspect) |
| Correlation analysis processing | real time | Real-time query (ad-hoc on-the-fly) |
| Correlation based | rule base | statistics base |
| Use scene | SOC operation (escalation workflow) |
SOC Analyst, Postmortem device/application administrator |
| implementation and cost advantage of scale |
Compatible with various devices and rules Limited by software/appliance model (event volume/hardware specs) Large-scale, regular maintenance costs |
Data format and device independent No software restrictions (commodity hardware expansion) Build quickly Supports on-demand maintenance (customization) |
| architecture |
Traditional SIEM architecture
 |
Splunk architecture
 |
Weekdays: 9:00-17:00
Inquiry/Document request
In charge of Macnica Splunk Co., Ltd.
- TEL:045-476-2010
- E-mail:splunk-sales@macnica.co.jp
Weekdays: 9:00-17:00