product
- Why choose Splunk
- Installation record
- price
- Splunk Enterprise Security
- Splunk Phantom (SOAR)
- Splunk ITSI (Next Generation IT Operations)
- Splunk Observability Cloud
- Splunk UBA
- Macnica CSIRT App Basic
- App for Splunk for Financial Institutions
- Splunk Analytics for Hadoop
- About Apps
- Splunk Edge Hub
- What is Splunk
service
- Dashboard/SPL Creation Pack [Implementation/Building Support]
- Version upgrade service [implementation and construction support]
- Smart Security Monitoring App [Original App/Service]
- Splunk × LANSCOPE Original App [Original App/Service]
- Security Monitoring App for Box [Original App/Service]
- Cloud Security Monitoring App [Original App/Service]
- List of services
Specifications/Technical Information
Application for evaluation machine
- FAQ

Splunk
Splunk
The Enterprise Security App is a paid add-on that enables advanced threat detection and significantly reduces incident detection and response times.
By combining Splunk Enterprise and Splunk Enterprise Security, it is possible to build a security intelligence platform that can perform advanced security analysis in real time, even in large-scale IT environments.

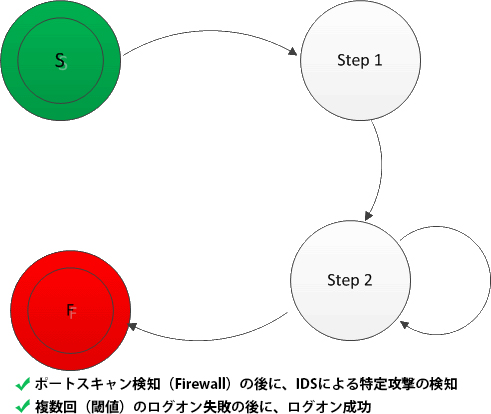
- Detection by correlation analysis
- Incident management
- Dashboard for incident investigation

- Data analysis platform
- Dashboard & Reports
- Incident investigation and management
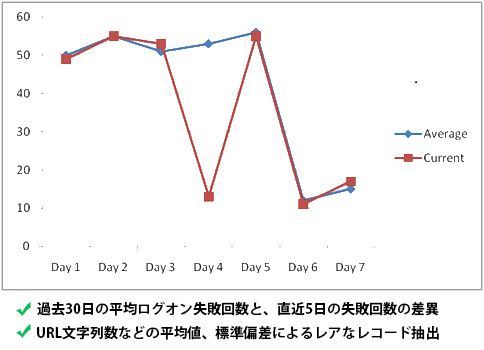
- statistical anomaly
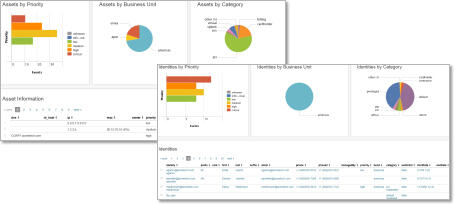
- Company assets and employee information
concept
- All data required for detection and investigation is available without normalization
- Equipped with all necessary functions for monitoring, operation, investigation, and analysis
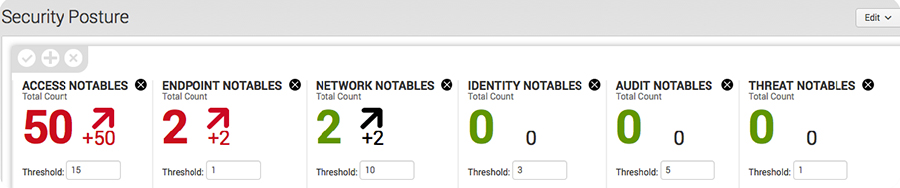
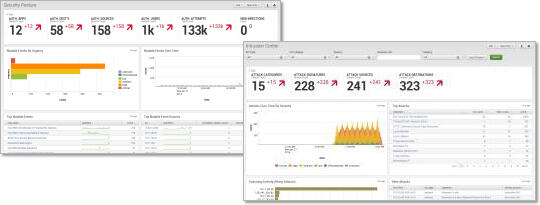
Security Posture
- Real-time view of critical security KPIs
- Setting each threshold
- Color display change
- Trend display
- Statistical comparison with historical data
- View security KPIs based on risk score
- Configurable risk score for any event
- Internal asset/internal axis can be drilled down
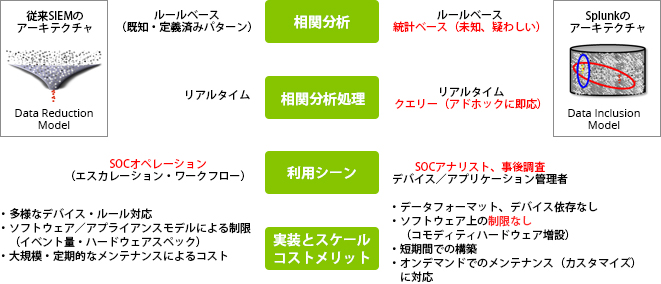
Correlation analysis enabled by Splunk
- Rule-based: known and defined patterns
- Statistical Base: Unknown/Suspicious
Detection using statistics
- external attack
- internal audit
| category | surveillance themes | Scenario example | Output frequency | data source |
|---|---|---|---|---|
| network malware |
Outgoing |
New external HTTP/HTTPS, DNS, etc. connection activity that has not occurred in the last 6 months |
Daily |
Proxy, FW, IDS/IPS, etc. |
|
Outgoing |
File transfers and attachments exceeding the average (maximum, minimum, etc.) transfer size by xx% over the past 6 months |
Daily |
Proxy, FW, Mail |
|
|
Outgoing |
Individual investigations of sudden malware-related connection activity, registry changes, etc. (for the past 3 months, etc.) |
Ad-hoc |
Proxy, Host Log/Registry |
|
| Individual survey |
Incoming |
Detailed log investigation of damaged sites, etc. (data for the past 3 months) |
Ad-hoc |
Web, APP, DB |
| internal investigation |
Insider |
Using a user account that has not been used in the last 6 months (suspected use of a stall account) |
Monthly |
OS (AD), APP, DB |
|
maintenance operation |
Operation or change of virtual host/important database without application/approval |
real time |
Workflow, VMs, DB, OS |
|
|
KPIs |
Comparison of security training participants and policy compliance (access, logon, terminal use), SOC response trends, results, etc. |
quarter |
Course data, AD, FileSv, Registry |
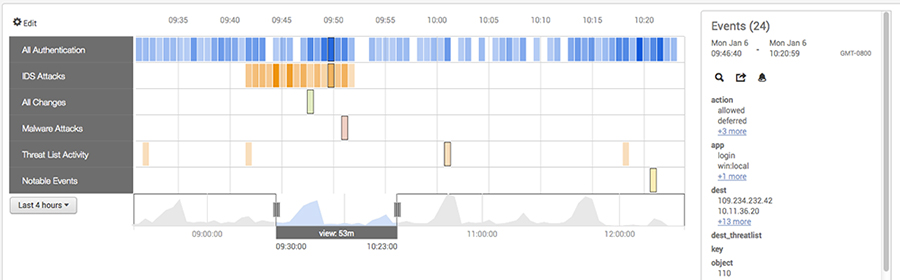
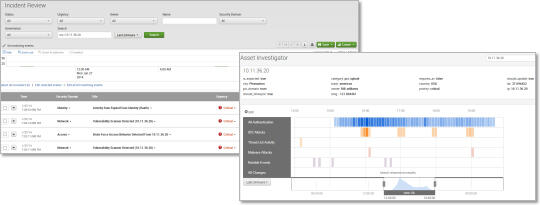
Event Investigator
- Investigate suspicious behavior based on internal assets and employees
- Display events of each device in chronological order
- Select specific events and visually correlate them with all company assets and employees
- Selecting a specific event displays the information necessary for investigation on the right
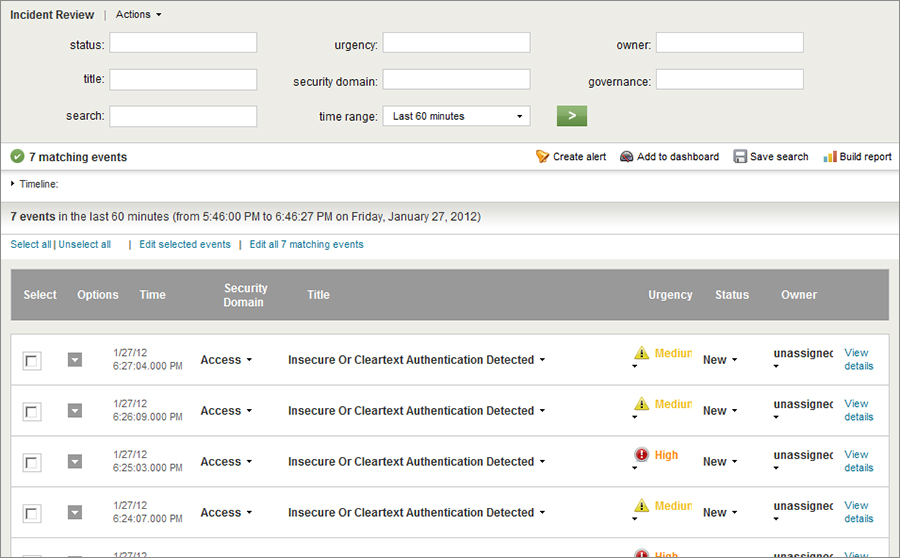
Incident Management
- Workflow function
- Indication of high priority incident alarms requiring immediate attention
- Annotation, escalation function
- Correspondence history (ticketing)
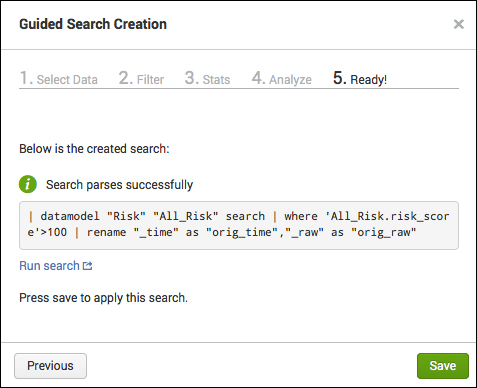
Correlation analysis rule creation guide
- Simplify relationships between various data
- GUI-based creation of complex rules
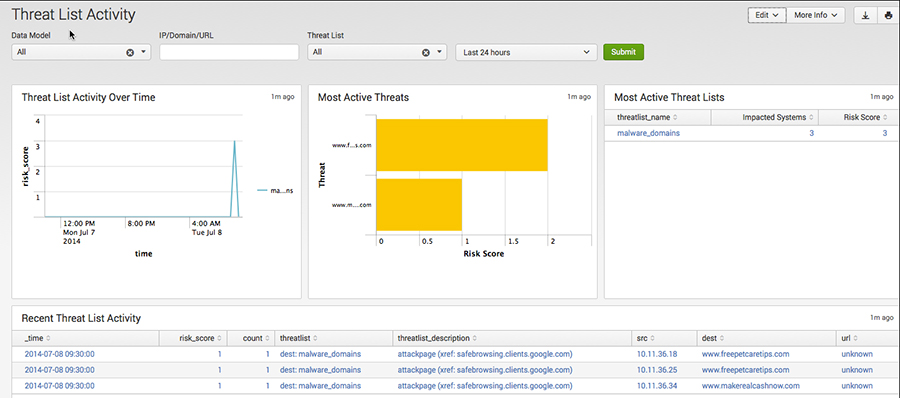
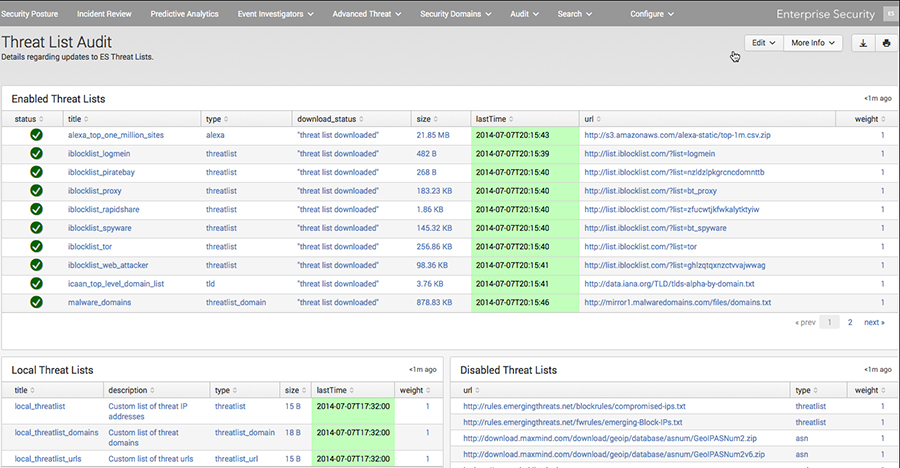
Threat information
- Aggregation, utilization, and activity visualization of threat information feeds
- Leverage open source threat intelligence
- Aggregate commercial threat information
- in-house blacklist
- Deduplication and weighted scoring possible
- Visualize feed status
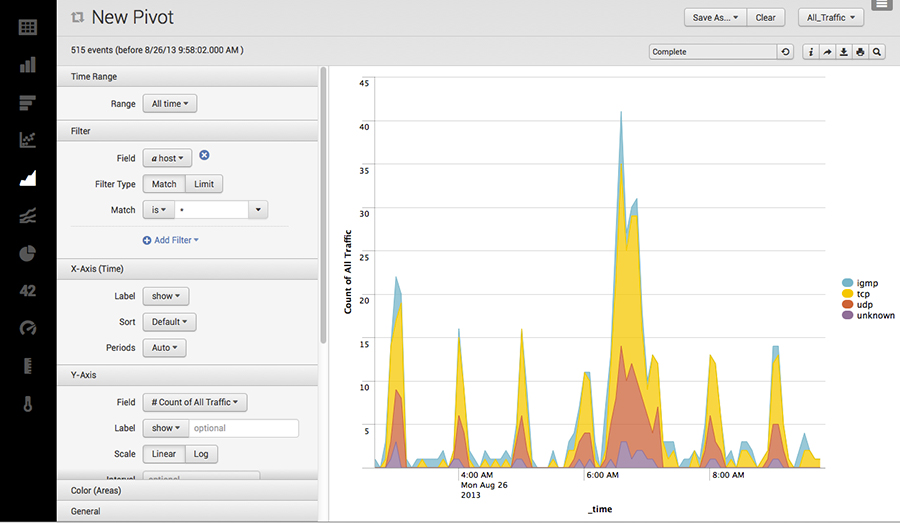
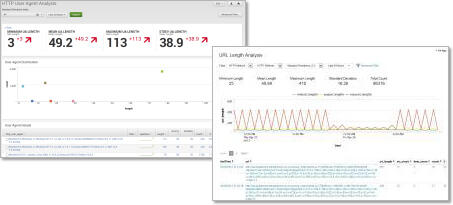
Analysis function
- Pivot functionality available for security analysis and reporting
- Create a new report
- Create a new dashboard
- High-speed technology allows immediate confirmation of results
- Intuitive GUI that even non-technical people can understand
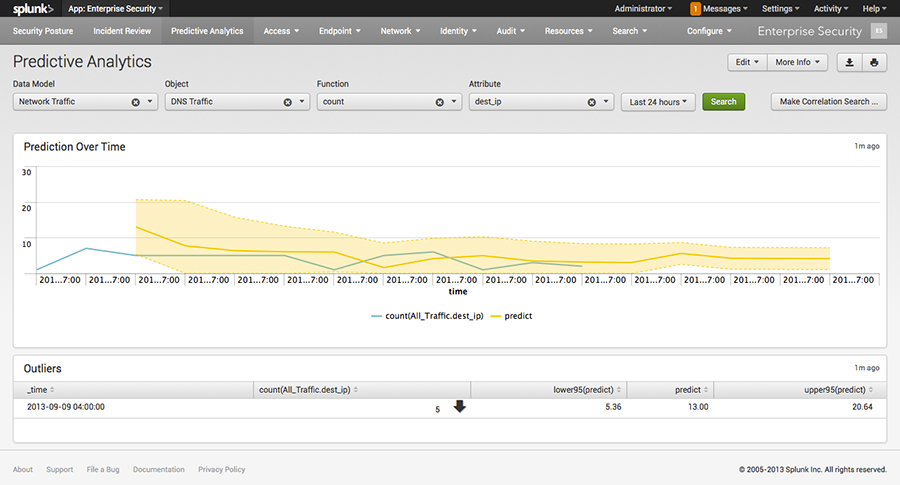
- Prediction function
Weekdays: 9:00-17:00
Inquiry/Document request
In charge of Macnica Splunk Co., Ltd.
- TEL:045-476-2010
- E-mail:splunk-sales@macnica.co.jp
Weekdays: 9:00-17:00