product
service
- Simple Security Consulting [Consulting]
- Splunk SOAR Automation Assessment Service [Consulting]
- Dashboard/SPL Creation Pack [Implementation/Building Support]
- Version upgrade service [implementation and construction support]
- Splunk Premium Apps construction support service [implementation and construction support]
- Splunk Security Log Analysis Start Package [Original App/Service]
- Splunk × CrowdStrike Falcon Insight, Macnica Original App [Original App/Service]
- Government uniform standard compatible App [Original App/Service]
- Smart Security Monitoring App [Original App/Service]
- Splunk × LANSCOPE Original App [Original App/Service]
- Security Monitoring App for Box [Original App/Service]
- Cloud Security Monitoring App [Original App/Service]
- SIEM Operation Monitoring Service [Original App/Service]
- List of services
- Macnica Premium Support for Splunk (utilization support, version upgrade monitoring)
- Macnica Premium Support for Splunk Skill Up Package
Specifications/Technical Information
Application for evaluation machine
- FAQ

Splunk
Splunk
security consulting
(simple package)
Simple Security Consulting Package
~Framework-Based Risk Assessment & SIEM Use Case Design~
For SIEM users "Simple Security Consulting Package -Framework-Based Risk Assessment & SIEM Use Case Design-" (hereafter referred to as this service) is a fit & gap analysis with the MITER ATT&CK framework by experts and the risks extracted from it. We provide the design of detection rules (SIEM use cases) to deal with as a package service.
The biggest feature of this service is that it can be provided at a fixed low price (from 9 million yen) by consulting in a short period of about 1 month and packaging it.
In this service, we mainly implement the following four points and provide assessment results and recommendations as output. We will present a detailed assessment report and present information that can be used both for decision-making by management and for considering countermeasures at the operation site.
- Reconciliation analysis of MITER ATT&CK framework and customer environment (identification of key risks/gaps)
- Identify the necessary detection rules (SIEM use cases) from the framework
- Provide specific and detailed detection rule designs/design proposals
- Deliver the results of 1. to 3. in a detailed document format (assessment report)
Expert support for difficult security framework adaptation

In recent years, cyberattacks have become more sophisticated, and it is said that it is impossible to completely prevent attackers from intruding or infringing. In such a situation, prompt incident response is required, and security measures based on log analysis (detection/correlation rules/alert management/analysis, etc.) using SIEM are one of the most important measures that corporate security departments should consider. is.
In order to effectively utilize SIEM as the core of security measures, it is essential to effectively design detection rules according to the purpose and advance design for log management and analysis operation linked to it. Effective methods for design include security frameworks such as the security standards published by various organizations, the MITER ATT&CK framework, and CIS Controls®. Utilizing the framework comprehensively and effectively covers the security risks faced by companies and the methods of attackers based on the knowledge of experts and experts. and design can be considered. On the other hand, since it is highly specialized and difficult to understand, general user companies need to acquire security skills and knowledge to fully utilize it, and it will take some time to make effective use of it. .
In this service, experts who are proficient in all security domains, SIEM, and Splunk support the design of security measures centered on SIEM through collation analysis with the MITER ATT&CK framework. This will help customers who wish to improve the level of security measures to implement countermeasures using the framework.
Gap analysis with security framework
~Risk analysis by experts + detection rules to deal with risks~
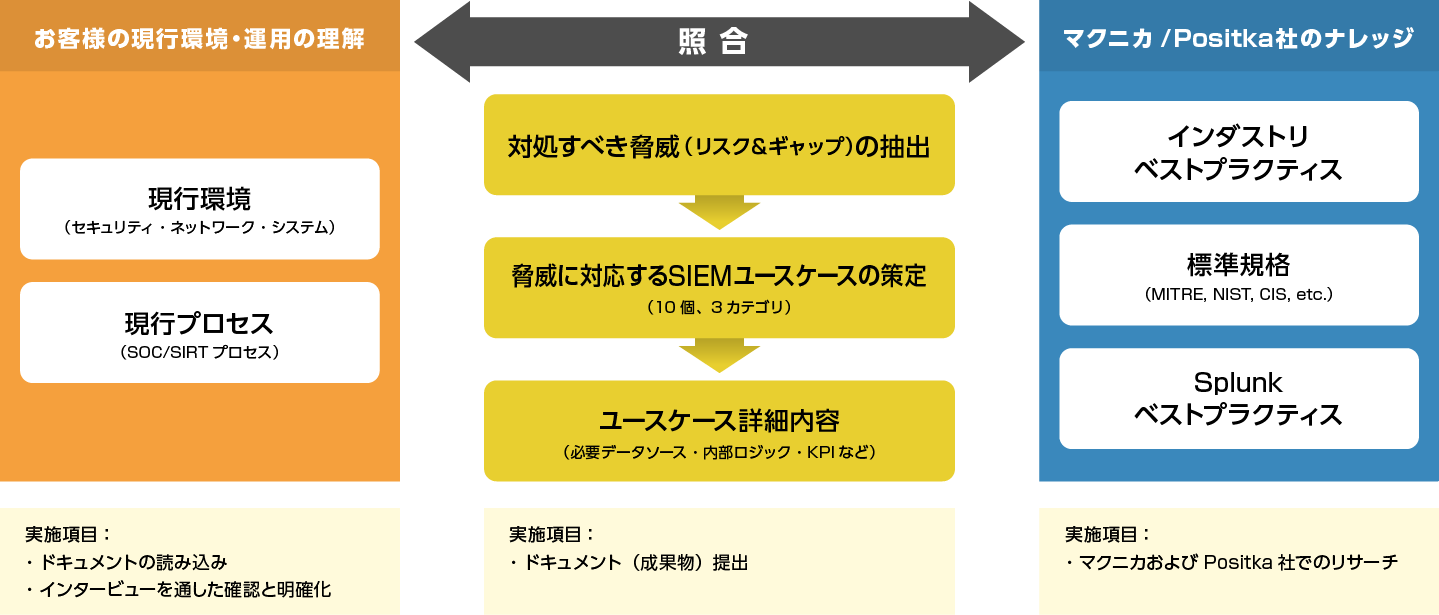
Our service proceeds as follows. At every step, experts familiar with all elements of security and SIEM respond, making it possible to provide high-quality suggestions and recommendations in a short period of time.
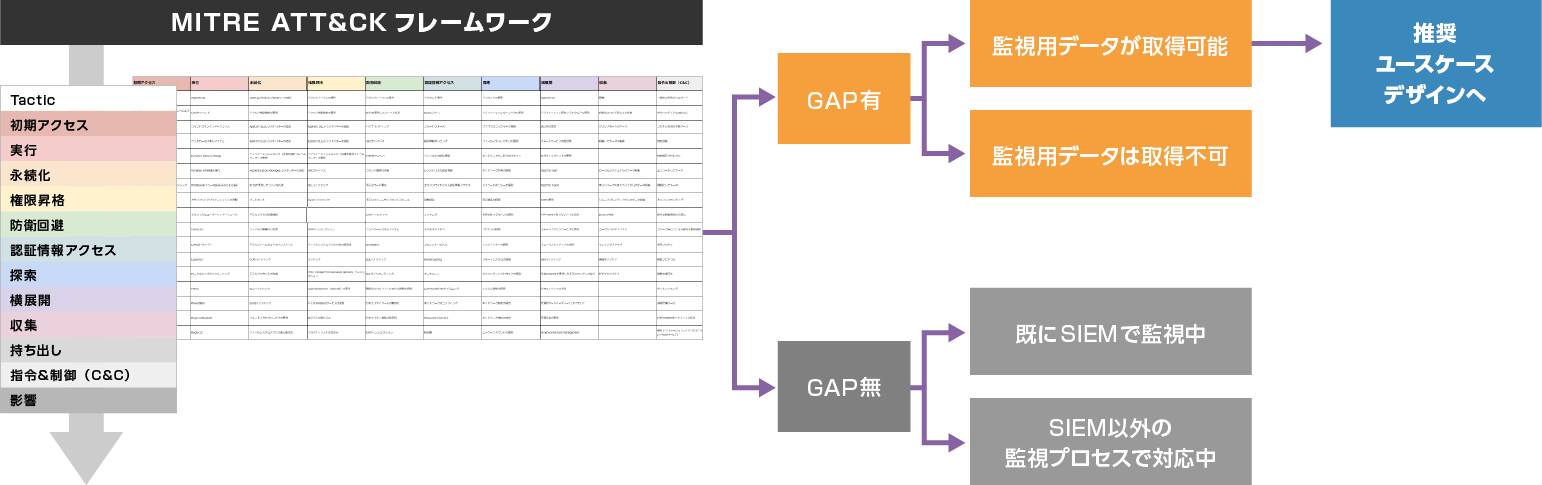
The assessment of this service utilizes the MITER ATT&CK framework to assess the status of security measures in the customer's environment in comparison with the latest risks and attacker techniques. After that, we design "detection rules" that supplement the major risks and major gaps extracted as the assessment results (up to 10 rules). The assessment can be completed in a short period of about two weeks using a templated pre-interview sheet.
Flow of service implementation
Image of gap analysis
Design optimal detection rules (SIEM use cases)
-Detailed and specific design that can be immediately applied to operation-
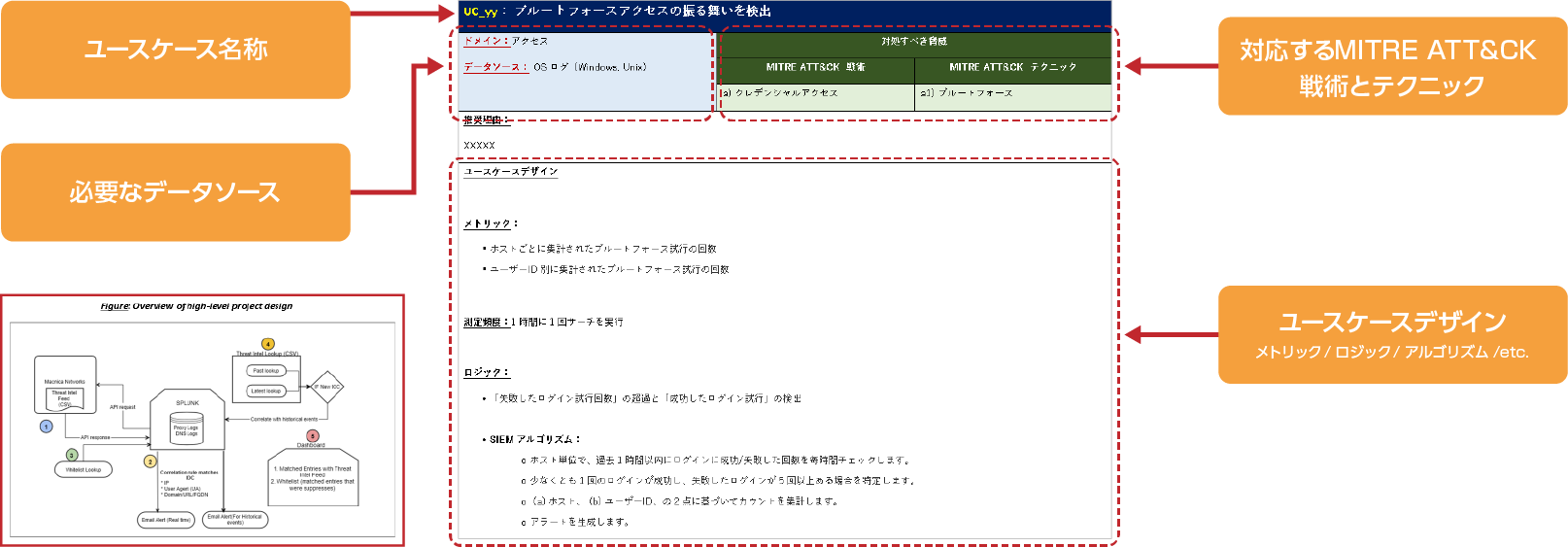
Splunk experts will design rules for the 10 extracted detection rules (SIEM use cases). The detection rule design is provided in a format that includes specific and detailed design information such as corresponding framework threats, data sources required for implementation, SIEM internal logic, measurement frequency and metrics. It provides implementation-level specific information so security teams can refer to this information for immediate implementation consideration.
Together with the results of the assessment phase (steps 1 to 3), it is provided in a detailed document format, so it can be used by security personnel to consider designs and for executives to make decisions on security measures.
Customers will be able to reference this information and create SIEM use cases on Splunk. If it is difficult to implement it by yourself, you can use our separate service "Dashboard Creation Pack" and we can implement the use case on your behalf.
特徴① パッケージ化により低価格・短期間を実現

Regular security domain consulting takes at least 3 months or more and costs tens of millions of yen, so many customers find it difficult to request it. This service realizes short-term and low-cost security consulting through simplification and packaging.
Security and SIEM experts will respond, embodying GAP analysis with the MITER ATT&CK framework and recommended SIEM countermeasures at a high level, while emphasizing ease of use for customers that can be realized in a short period of time and at a low price. .
Feature 2: Assessment using the MITER ATT&CK framework
The MTIRE ATT&CK framework is a systematization of the flow and methods of cyberattacks by MITER, a well-known non-profit organization that implements CVE numbering, and is used by enterprise companies to consider security measures. It is designed to give "specific and exhaustive suggestions" that are useful in practice.
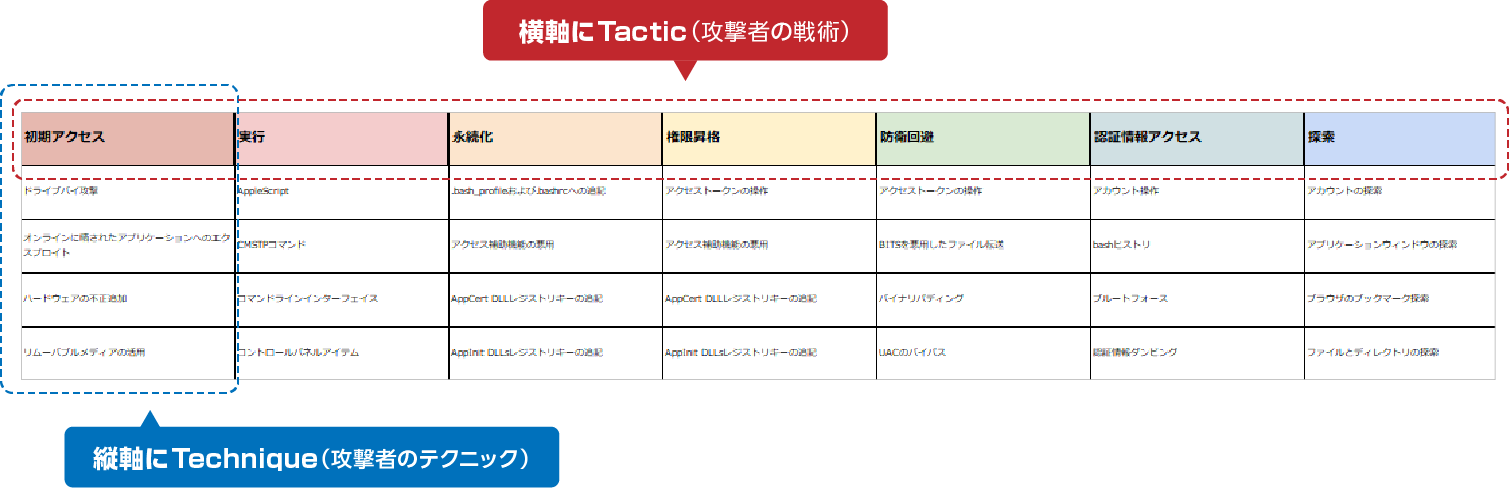
As shown in the figure below, the horizontal axis shows the attacker's tactics, and the vertical axis shows the attacker's techniques (technologies used). It is a framework that can be covered.
Based on the knowledge of experts and experts, it comprehensively and effectively covers the security risks faced by companies and the techniques used by attackers. becomes possible.
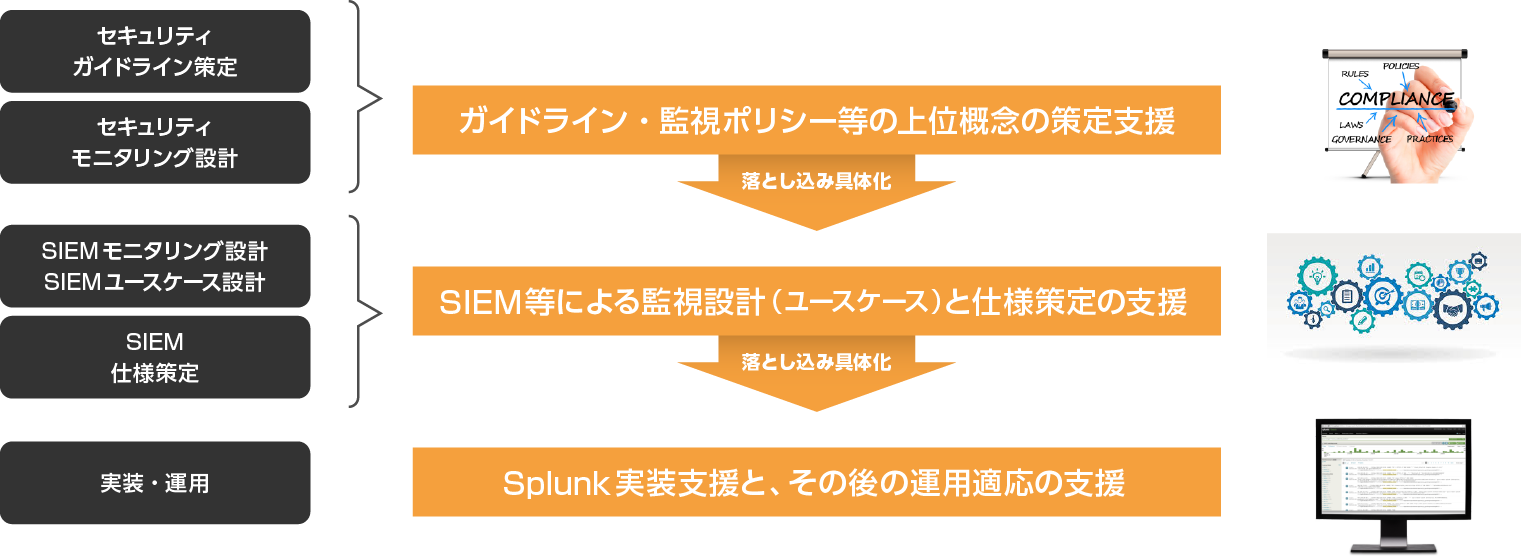
Feature 3: Consistency from framework adaptation to setting level
One of the features of our consulting services is that we can consistently support everything from the design of security concepts (guidelines/framework, etc.) to the SIEM design/configuration/implementation layers.
General security consulting provided by other companies supports the design of guidelines and monitoring policies. Most of the time it is requested. However, it is difficult for most of our customers to put the high-level concepts into solution specifications and adapt them to actual operations on site, which requires a great deal of time and effort, and is difficult to achieve in a short period of time.
In the security consulting service we provide, we present recommendations in a concrete form, from security frameworks and standards assessments to Splunk SIEM configuration proposals and specification levels. This is made possible by the support of members who are well versed in security, SIEM, and Splunk. In addition, if necessary, it is also possible to substitute for implementation work and maintenance work by using another service.
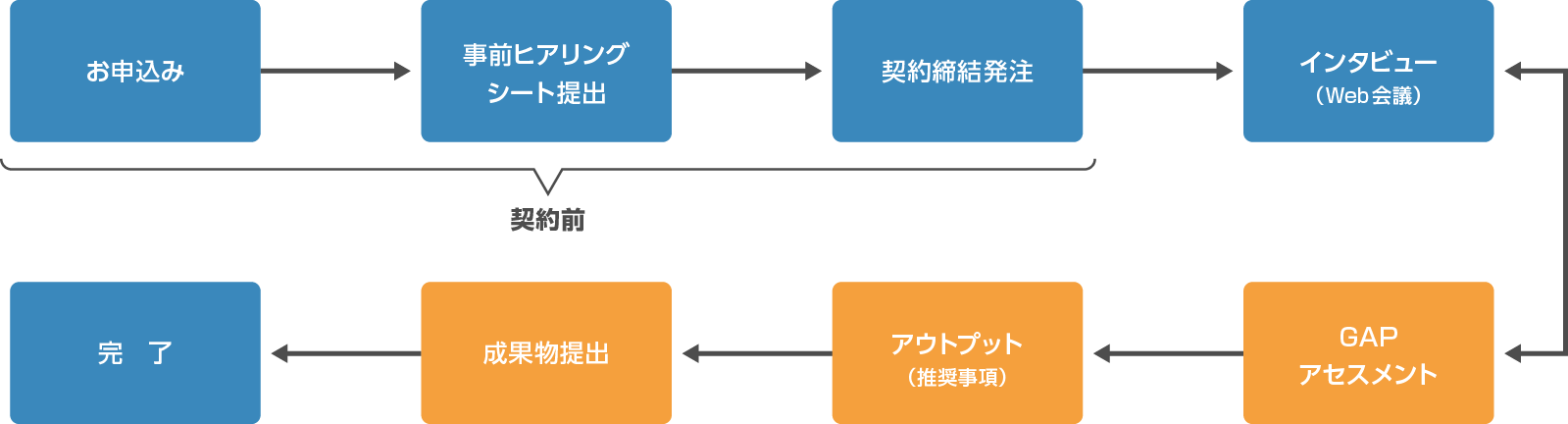
Flow from application to service provision
Cost, period, etc.
| cost | From 9 million yen (excluding tax) |
|---|---|
| period | about 10 weeks |
| type of contract | Quasi-delegation contract |
| Contractor | Customer -Macnica (some work is subcontracted to partner companies) |
| Artifact | Provision of assessment report (Word document format) (1) Analysis result report (2) Recommended SIEM use cases ③ SIEM use case design |
Inquiry/Document request
In charge of Macnica Splunk Co., Ltd.
- TEL:045-476-2010
- E-mail:splunk-sales@macnica.co.jp
Mon-Fri 8:45-17:30