Splunk
スプランク
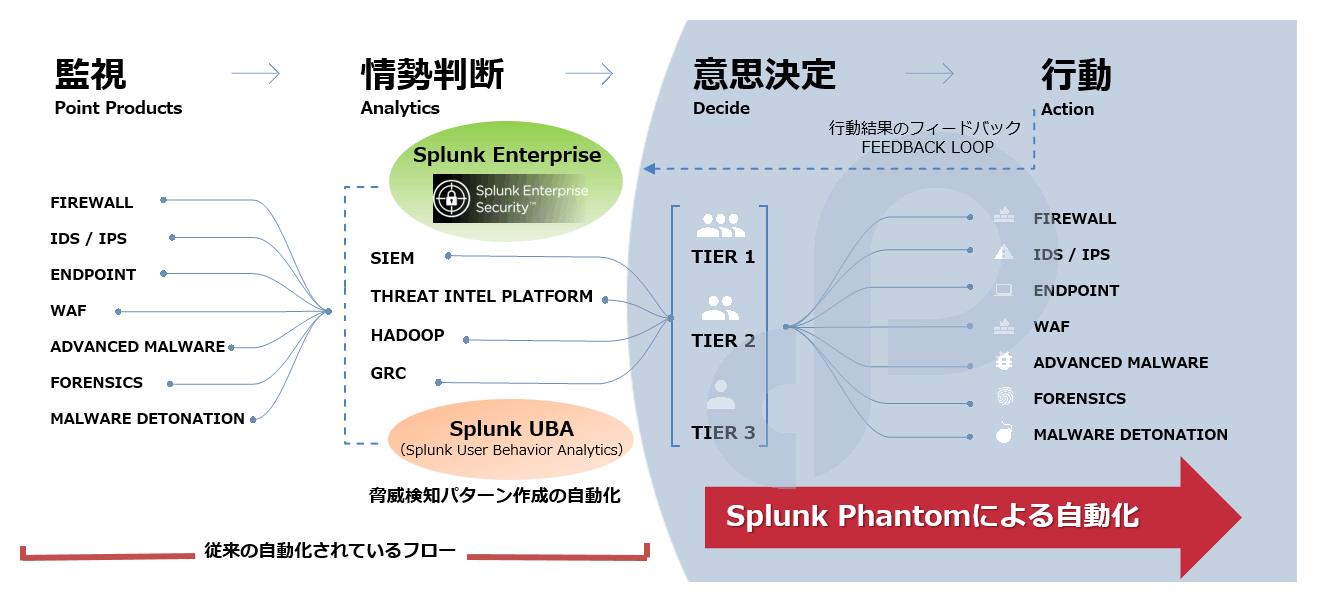
Splunk Phantomはセキュリティ運用におけるタスクの自動化と他製品連携により、効率的で正確な運用を実現するSOAR※製品です。
導入済みのセキュリティデバイスやSIEM製品からの相関分析アラートをトリガーに、インシデント対応のタスクを自動実行する事で運用者の意思決定、対応を迅速化します。
※SOAR(=Security Orchestration and Automated Response)とはセキュリティの製品連携、タスク自動化による運用効率化を実現する新しいカテゴリです。
企業のセキュリティ運用における課題
近年のサイバー攻撃の激化により、組織のセキュリティ対策において、運用の複雑化、コスト増、スキル不足、人材不足といった課題が増加しています。Splunk Phantomは負担の増すSOC・CSIRTに対し、以下の価値を提供します。
人材の不足
製品を利用
連携がなく独立
かかる時間

- 反復作業の自動化による作業工数の削減、リソースの集中
- 自動検出、調査、応答により、迅速なインシデント対応と時間の削減
- セキュリティインフラの統合による作業の効率化
Splunk Phantom 6つの機能
Splunk Phantomは6つの機能で組織のセキュリティ運用を支援します。
① オートメーション
インシデント対応手順をプログラム化(Playbook化)、反復的なタスクを自動処理する事で工数を削減します。
さらに、自動アクションは数秒で実行されます。意思決定の為のインテリジェンスを自動で取得することが可能です。
② オーケストレーション(製品連携)
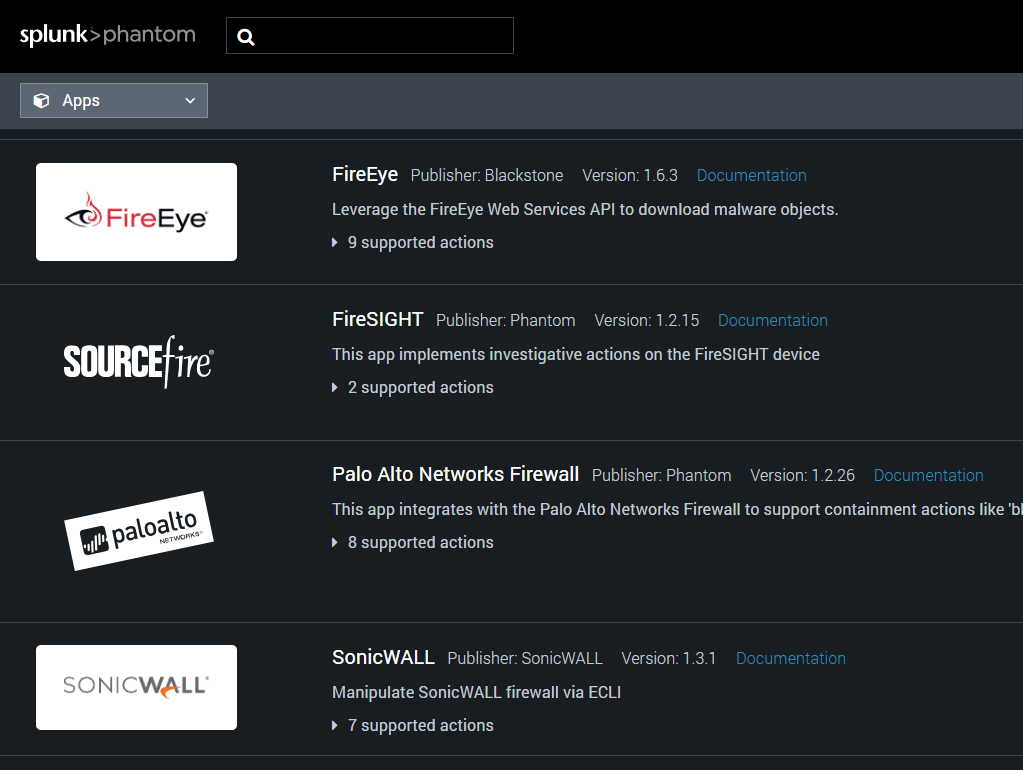
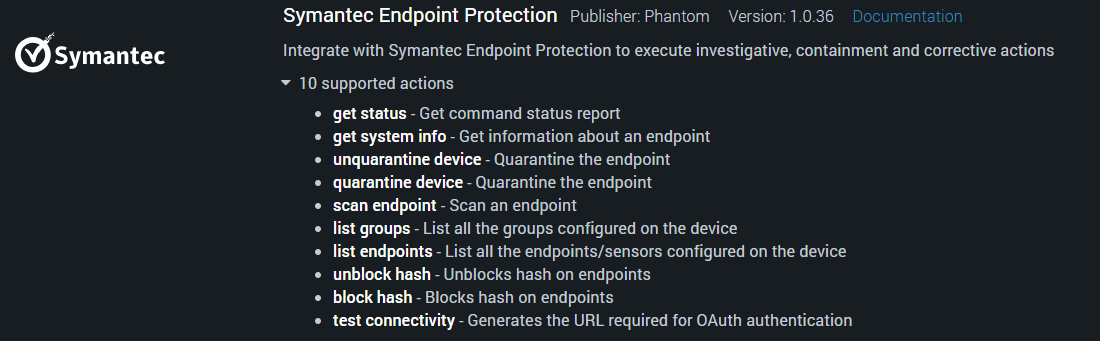
他製品・ツールが提供しているAPIを利用し、情報取得や設定変更を実施します。
APIはAppsという形でテンプレート化します。Splunk Phantomは200種類以上のAppsを用意しており、1000以上のAPIを実行する事が可能です。また、既存のAppsにない場合でもPythonコードで新規に作成する事が可能です。
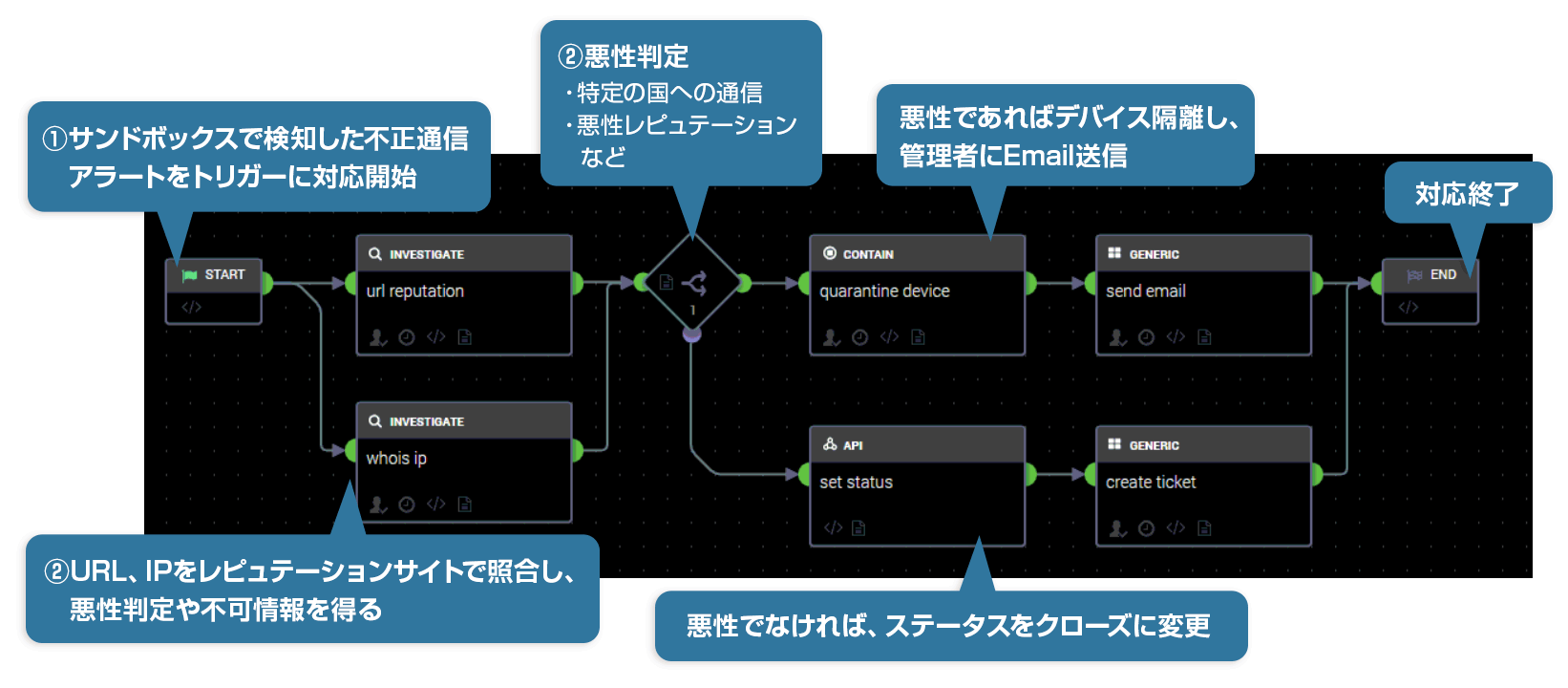
連携例:VirusTotalに自動でIPレピュテーション情報を問合せ、取得/悪性の場合、IPをFWのブラックリストに登録
シナリオ例
③ コラボレーション
セキュリティ運用ツールをSplunk Phantomに一元化し、共通の画面やチャット機能を提供することで、全ての関係者にインシデントの経緯、状況共有を実現します。
担当者間の相談や意見交換、SOC部門からネットワーク管理者への説明までSplunk Phantom上で実施する事により、チーム間・役割の壁を取り払い、効率的なオペレーションを可能にします。
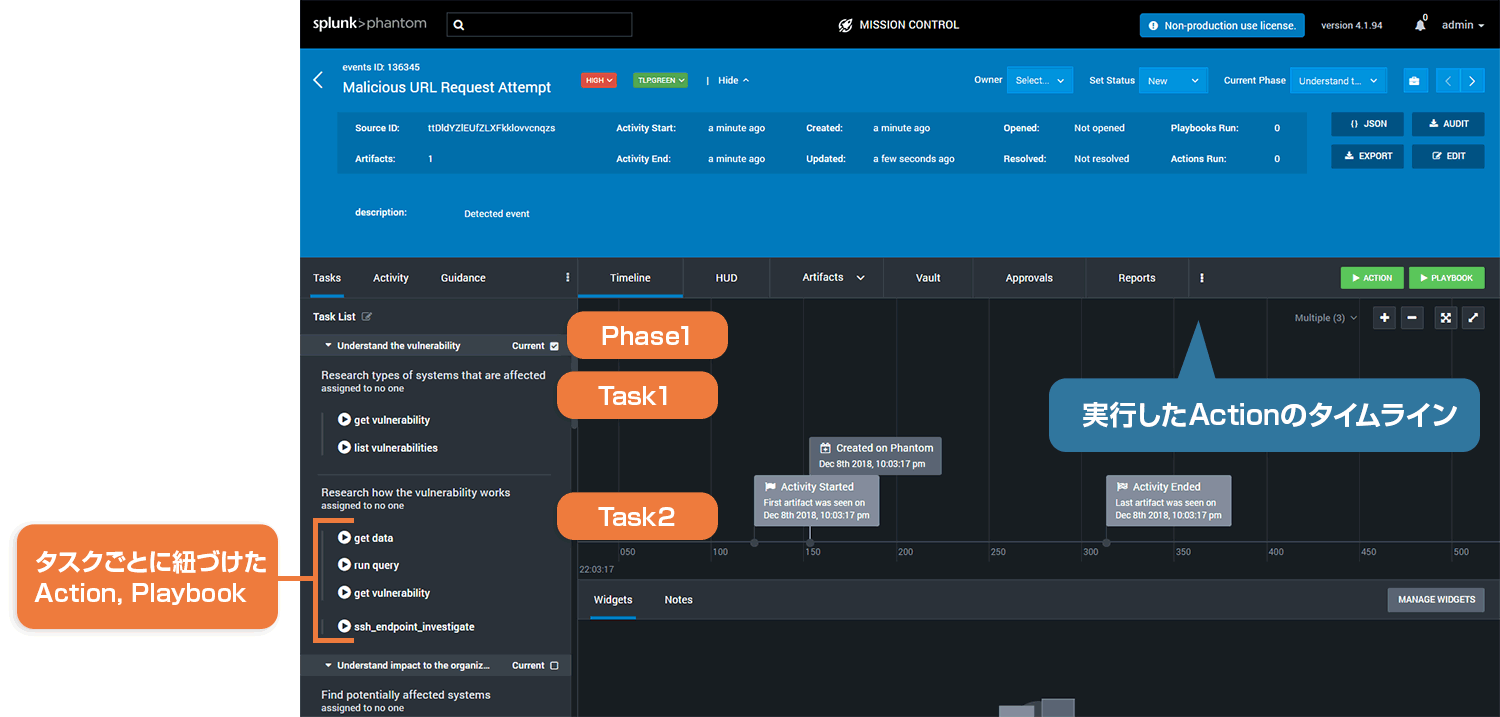
④ イベントマネジメント
発生したセキュリティイベントを管理します。
発生日、ステータス、緊急性などを参照し、イベントを効率的に管理する事が出来ます。
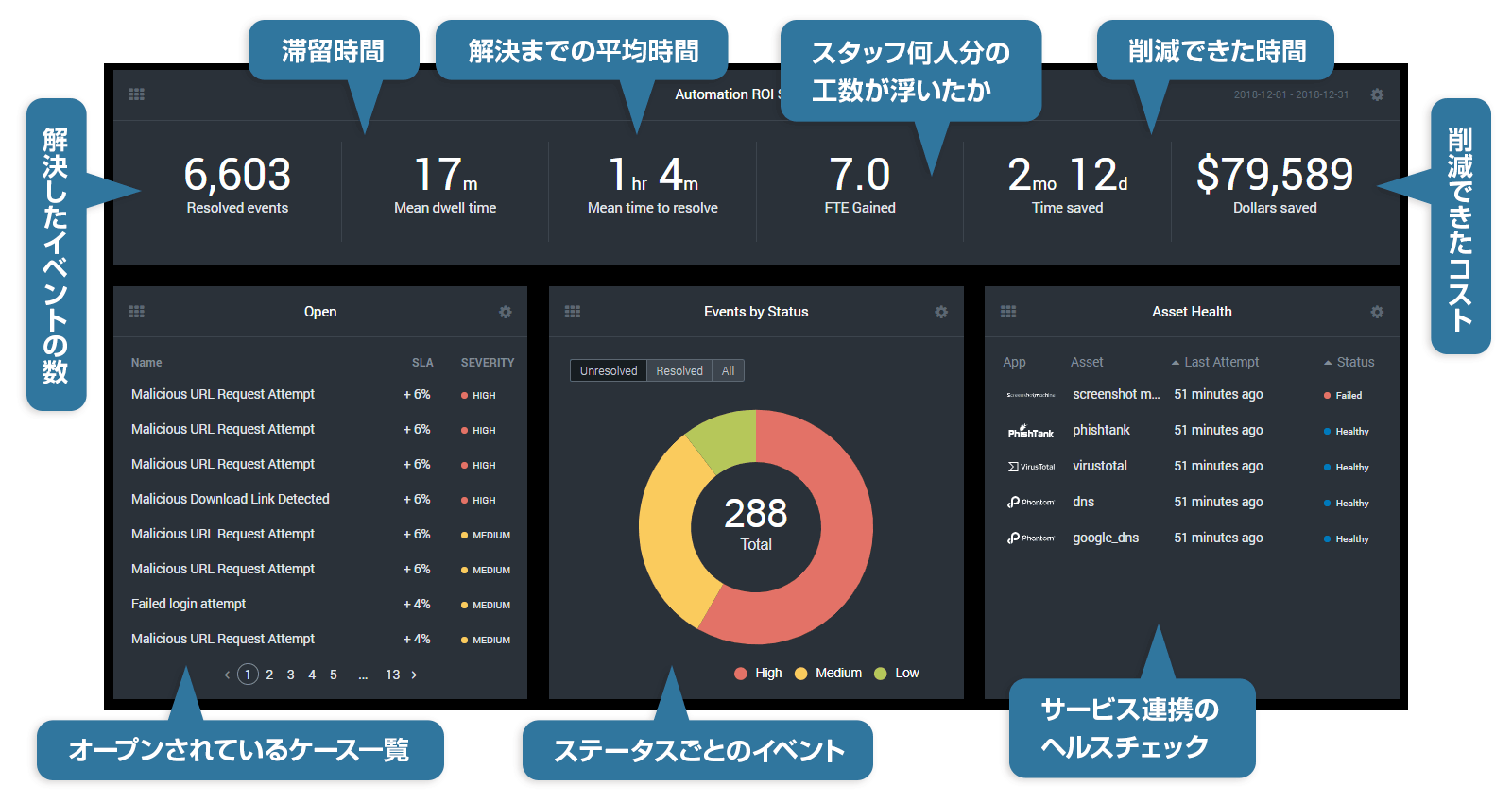
⑤ ケースマネジメント
⑥ レポートティング
お問い合わせ・資料請求
株式会社マクニカ Splunk 担当
- TEL:045-476-2010
- E-mail:splunk-sales@macnica.co.jp
平日 9:00~17:00