product
- What you can do with CrowdStrike
- CrowdStrike Modules Falcon
- Falcon Prevent(NGAV)
- Falcon Insight(EDR)
- Falcon OverWatch (Threat Hunting)
- Falcon Discover (IT Asset Management)
- Falcon Spotlight (vulnerability management)
- Falcon Adversary Intelligence
- Falcon Identity Threat Protection/Detection
- Falcon Cloud Security(CNAPP)
- Falcon Surface(EASM)
- Falcon Shield(SSPM)
- Falcon Next-Gen SIEM
service
Application for evaluation machine
- FAQ

CrowdStrike
CrowdStrike
Vulnerability Management (Falcon Spotlight)
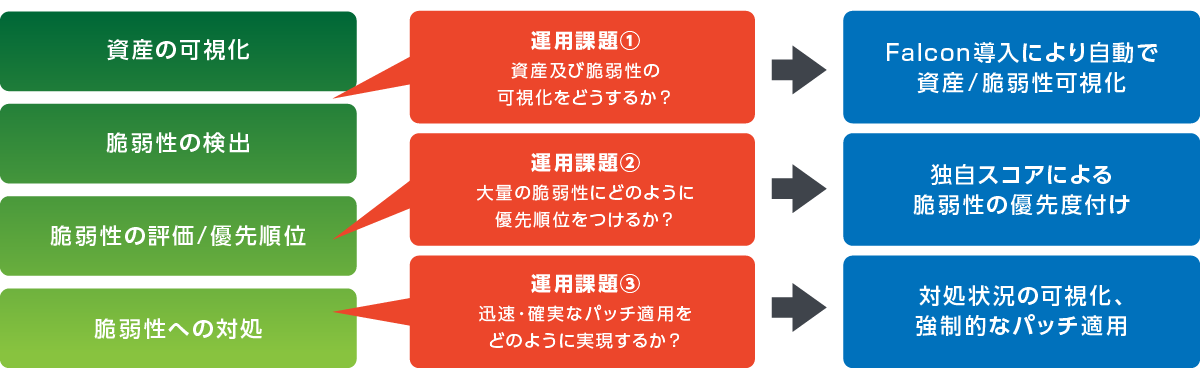
CrowdStrike Falcon Spotlight is a vulnerability management solution that automatically collects information on vulnerabilities (CVE) and patch application status on devices and servers and visualizes them in near real time.
We provide comprehensive support for vulnerability countermeasures by providing functions that solve customers' operational issues in each phase of the vulnerability countermeasure cycle: "visualization of vulnerabilities", "prioritization of countermeasures" and "patch application". .
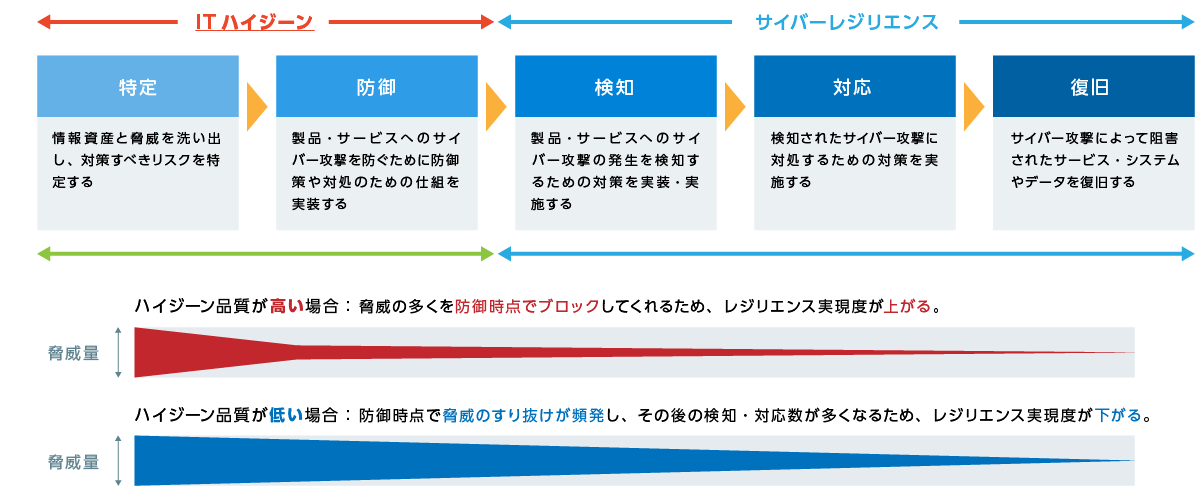
In order to protect the system from threats, it is necessary not only to quickly detect an attack that has occurred and take appropriate countermeasures and restore the "response (cyber resilience)" process, The process of “prevention (IT hygiene)” to identify and prevent cyberattacks is also important.
In realizing security, many customers aim to realize "countermeasures" rather than "prevention" and introduce antivirus and EDR products. However, even if the process of "handling" is achieved at a high level, if "prevention" is not achieved, many threats slip through defenses, resulting in an enormous number of alerts to be dealt with. As a result, it is conceivable that sufficient protection cannot be achieved or that the number of man-hours required for implementation increases. If you're "preventive," you'll be able to forestall many of the threats and focus on the alerts that really need to be addressed.
In order to achieve IT hygiene, which is a "prevention" process, it is necessary to identify the vulnerabilities that exist in the environment and apply patches to especially high-risk vulnerabilities quickly and reliably.
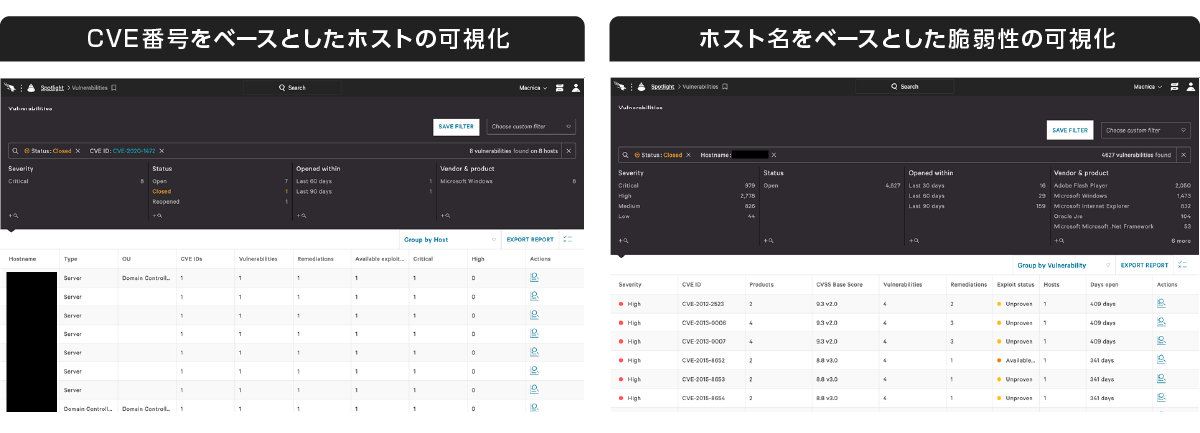
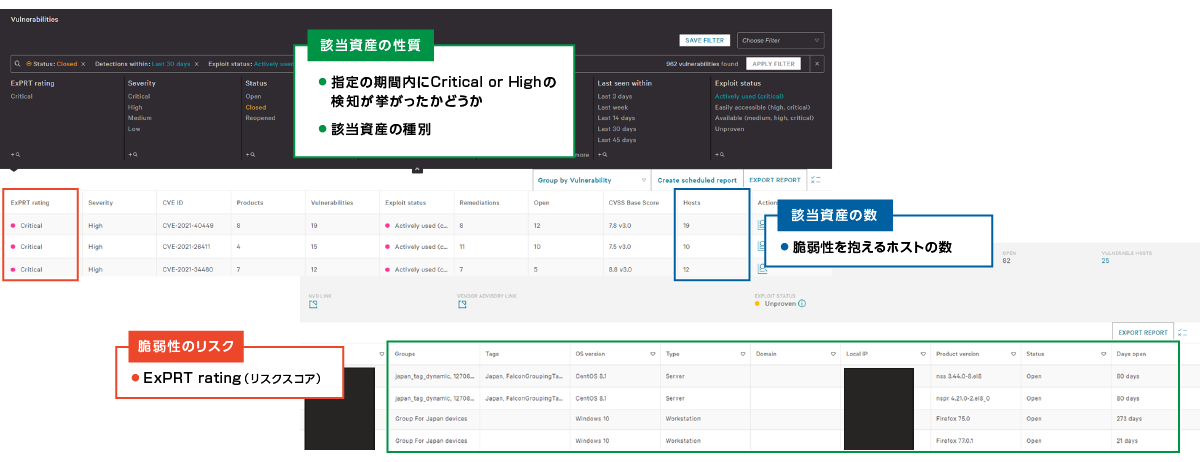
(1) Visualization of assets and vulnerability status in the environment
Falcon Spotlight visualizes vulnerabilities existing in the environment from log information collected by sensors. You can also search for vulnerabilities by host name, product name, CVE number, etc. With this, for example, it is possible to search for vulnerabilities that exist in the device in order to investigate the device detected by EDR, or to use the CVE number when information on a high-risk vulnerability is disclosed. It is possible to search for the presence or absence of impacts in the environment by using
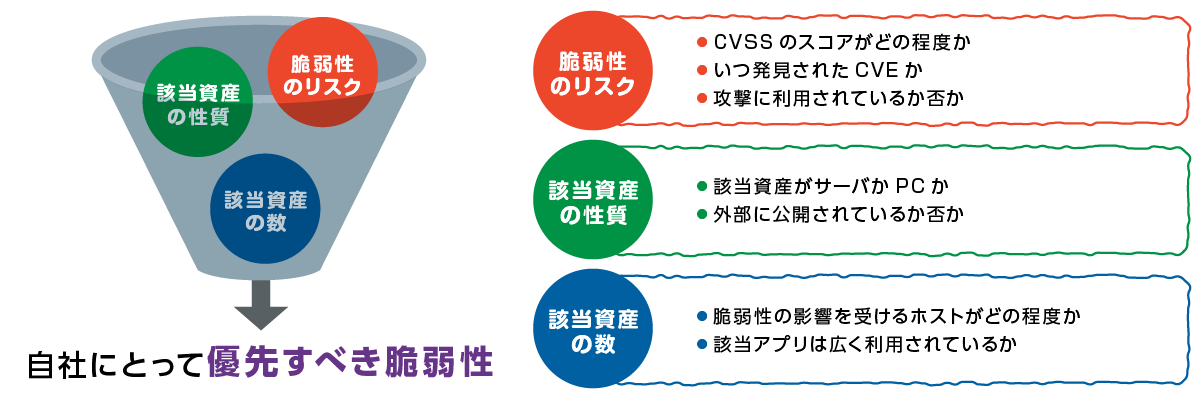
(2) Prioritization of vulnerabilities
Vulnerability can be narrowed down using information such as "vulnerability risk", "property of assets", and "number of assets", which are the criteria for prioritizing visualized vulnerabilities.
As a vulnerability risk index, you can use not only the standard vulnerability assessment score CVSS, but also the score from CrowdStrike's own ExPRT Rating. The ExPRT Rating dynamically determines whether a vulnerability is currently a threat based on its frequency of use in recent attacks and the activity of nation-state attackers.
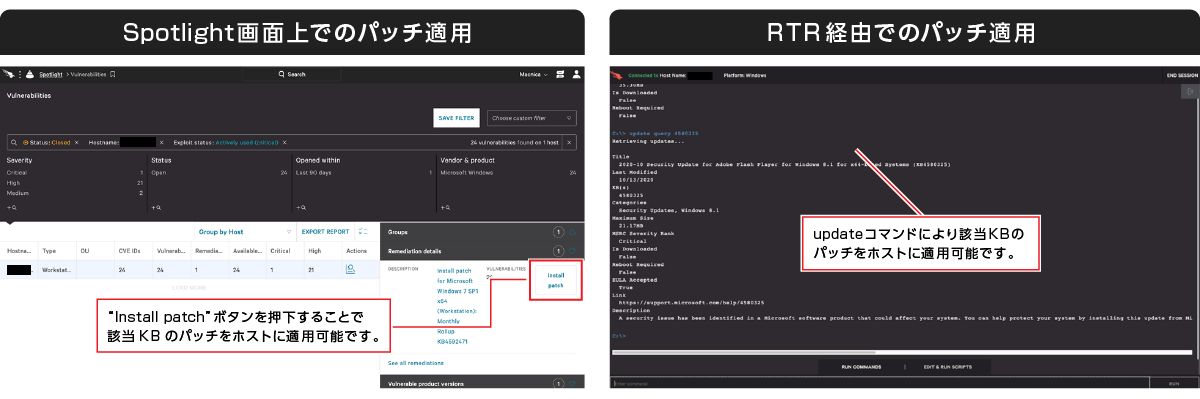
③Remote patch application via Falcon console
Falcon Spotlight also has features for dealing with discovered vulnerabilities. Microsoft patches to fix vulnerabilities can be applied to the host from the console. You can also visualize the patch application status. This makes it possible for administrators to fix vulnerabilities without relying on host users.
Inquiry/Document request
In charge of Macnica CrowdStrike Co., Ltd.
- TEL:045-476-2010
- E-mail:crowdstrike_info@macnica.co.jp
Weekdays: 9:00-17:00