product
- What you can do with CrowdStrike
- CrowdStrike Modules Falcon
- Falcon Prevent(NGAV)
- Falcon Insight(EDR)
- Falcon OverWatch (Threat Hunting)
- Falcon Discover (IT Asset Management)
- Falcon Spotlight (vulnerability management)
- Falcon Adversary Intelligence
- Falcon Identity Threat Protection/Detection
- Falcon Cloud Security(CNAPP)
- Falcon Surface(EASM)
- Falcon Shield(SSPM)
- Falcon Next-Gen SIEM
service
Application for evaluation machine
- FAQ

CrowdStrike
CrowdStrike
EASM(Surface)
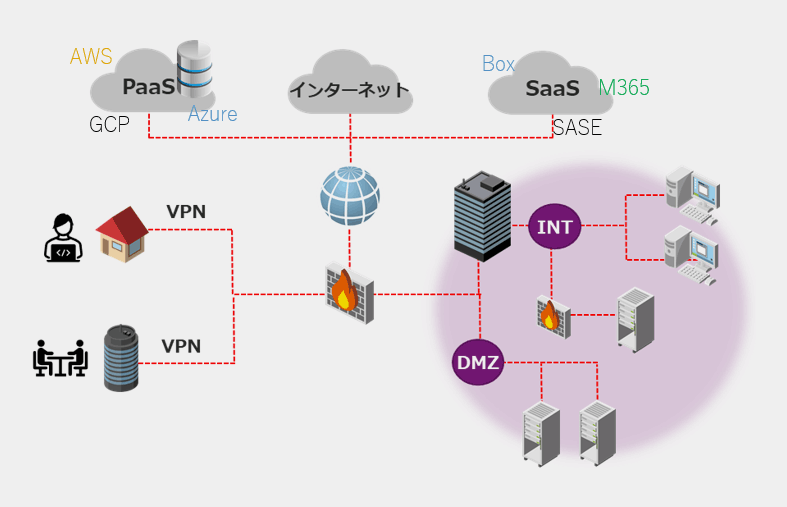
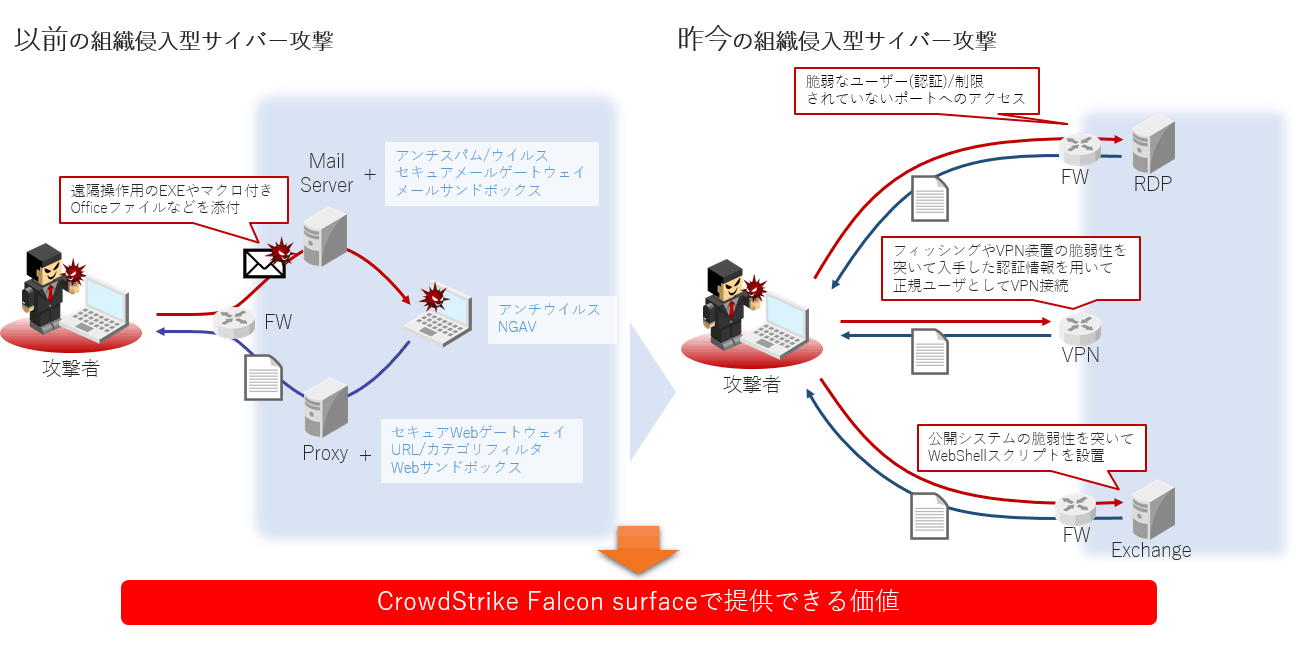
CrowdStrike Falcon Surface is a product in the area called EASM *1 that manages IT assets that are open to the public, understands their risks, and visualizes vulnerabilities.
In addition to visualizing the IT assets of not only the parent company but also subsidiaries and affiliates, we also utilize CrowdStrike Holdings、Inc. 's abundant intelligence on attackers and score countermeasures to improve the efficiency and effectiveness of our customers' responses. take action.
*1 EASM (=External Attack Surface Management)
EASM is an abbreviation for External Attack Surface Management, and as the name suggests, it is a product genre for identifying assets exposed to the outside (Internet) that can be attacked and managing their vulnerabilities. Reduce the risk of being attacked by attackers by continuously understanding your company's assets and their risks.
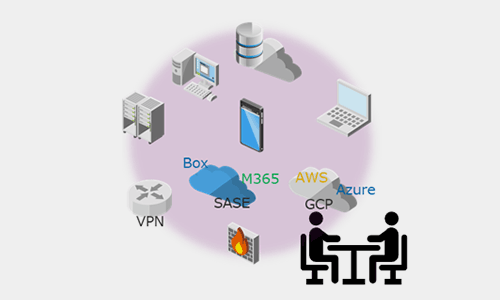
- Monitor all assets exposed to the internet
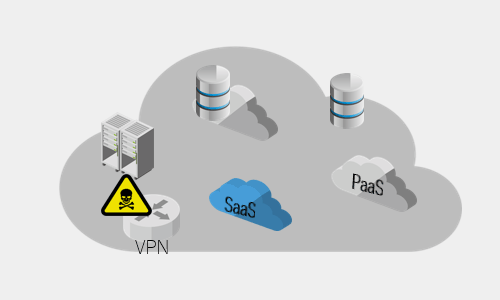
- Scoring your entire environment and identifying priority assets for action
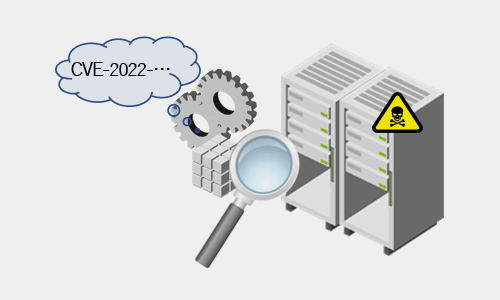
- Identification and visualization of vulnerabilities in vulnerable servers and NW devices
Due to the recent shift to the cloud due to the use of hybrid work, DX, and IoT, customers are increasingly using the cloud environment, and the number of assets and systems that are exposed to the public is increasing more than ever. increase. While this situation has increased convenience for customers, it has also led to the occurrence of security risks that are different from conventional ones, and the need to manage assets has also increased.
Task
- Increased Assets Increase Complexity and Decrease Visibility
- Assets not managed by the IT department increase, making it difficult to keep track of
- Risk of inappropriate settings due to lack of product expertise
- It becomes difficult to grasp the assets owned by the company or subsidiaries.
- The number of cases involving customer assets that have been disclosed to the public is increasing.
- Lack of visibility due to asset growth
- Increase in assets not permitted by the IT department
- Risk of lack of expertise
- Inability to identify assets within the company
1. Visualization of customer assets in real time
2. Prioritization based on rich attacker information
3. Presentation of guided improvement steps
(1) Visualization of customer assets in real time
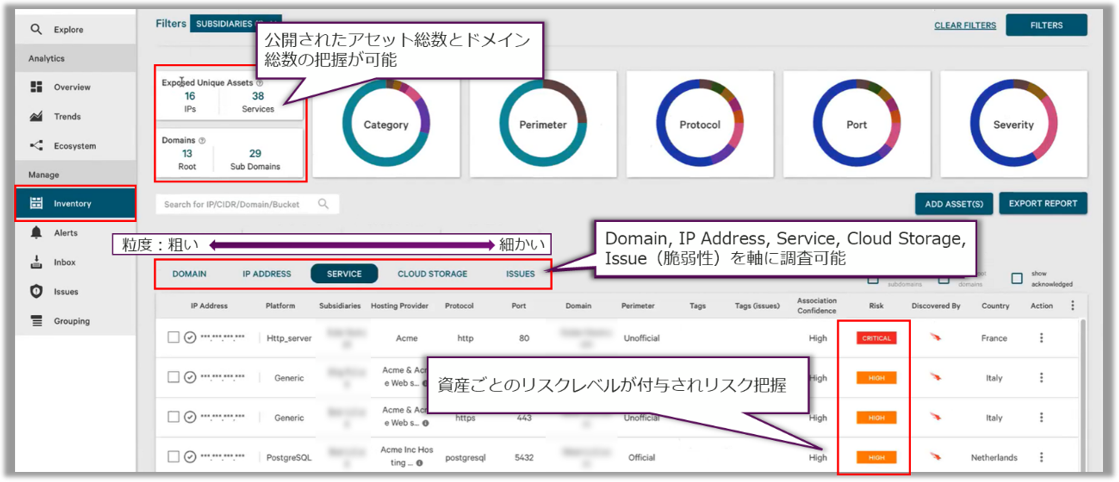
You can grasp the risk score of the entire customer environment based on the collected asset information and the summary of asset information such as IP addresses and domains published to the outside.
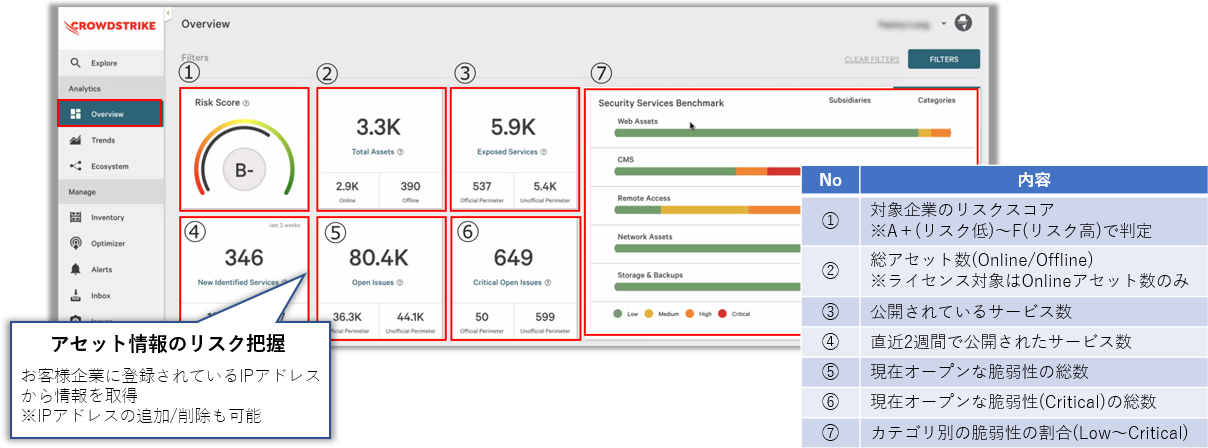
In addition, since newly confirmed customer assets are updated in real time from the management screen, it is possible to always grasp the entire customer environment.
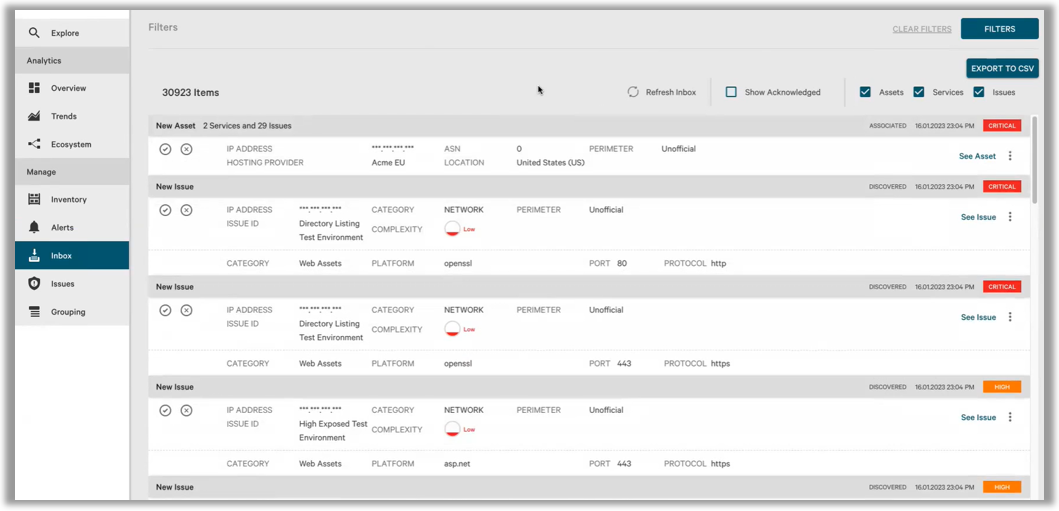
(3) Prioritization based on a wealth of attacker information
You can grasp the total number of publicly available assets, domains, IP addresses, etc., and check the risk status of specific assets according to categories such as domains, IP addresses, services, vulnerabilities, etc.
(3) Presentation of guided improvement steps
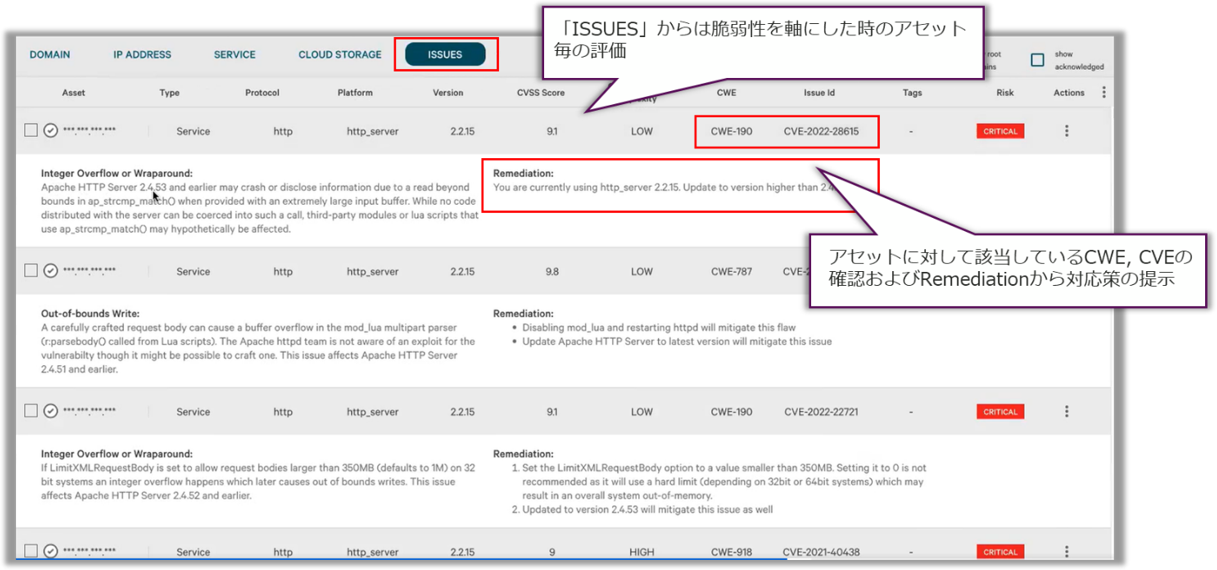
Guided countermeasures are presented for assets linked to publicly disclosed CWEs and CVEs, so you can understand what to do with which assets.
Inquiry/Document request
In charge of Macnica CrowdStrike Co., Ltd.
- TEL:045-476-2010
- E-mail:crowdstrike_info@macnica.co.jp
Weekdays: 9:00-17:00