product
- What you can do with CrowdStrike
- CrowdStrike Modules Falcon
- Falcon Prevent(NGAV)
- Falcon Insight(EDR)
- Falcon OverWatch (Threat Hunting)
- Falcon Discover (IT Asset Management)
- Falcon Spotlight (vulnerability management)
- Falcon Adversary Intelligence
- Falcon Identity Threat Protection/Detection
- Falcon Cloud Security(CNAPP)
- Falcon Surface(EASM)
- Falcon Shield(SSPM)
- Falcon Next-Gen SIEM
service
Application for evaluation machine
- FAQ

CrowdStrike
CrowdStrike
Solutions provided by CrowdStrike
Various issues surrounding the IT environment in companies that bother the person in charge
- Inability to spot advanced attacks such as fileless malware
- Sophisticated attacks that are difficult to detect are increasing, but we do not have a monitoring system at 24365
- When an incident occurs, the attack route is unclear and cannot be identified
- When an incident occurs, it is impossible to grasp the situation of lateral expansion (spread of infection)
- Due to the promotion of telework, security cannot be guaranteed with perimeter defense products
- It takes time to deal with incidents
- Unable to control USB and understand how it is used
- Concerns about information leakage due to misconfiguration of SaaS
- You want to install a security product on all terminals, but you do not know which terminals are not managed
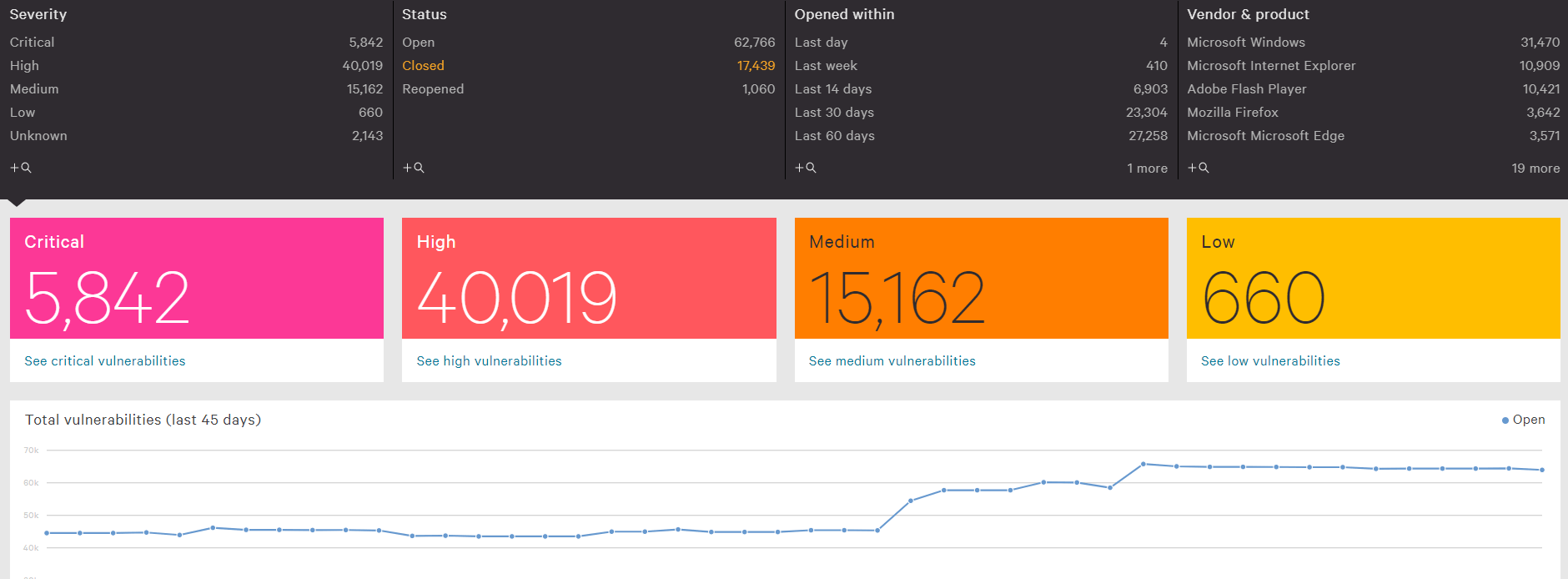
- Not knowing how many vulnerabilities exist within the company
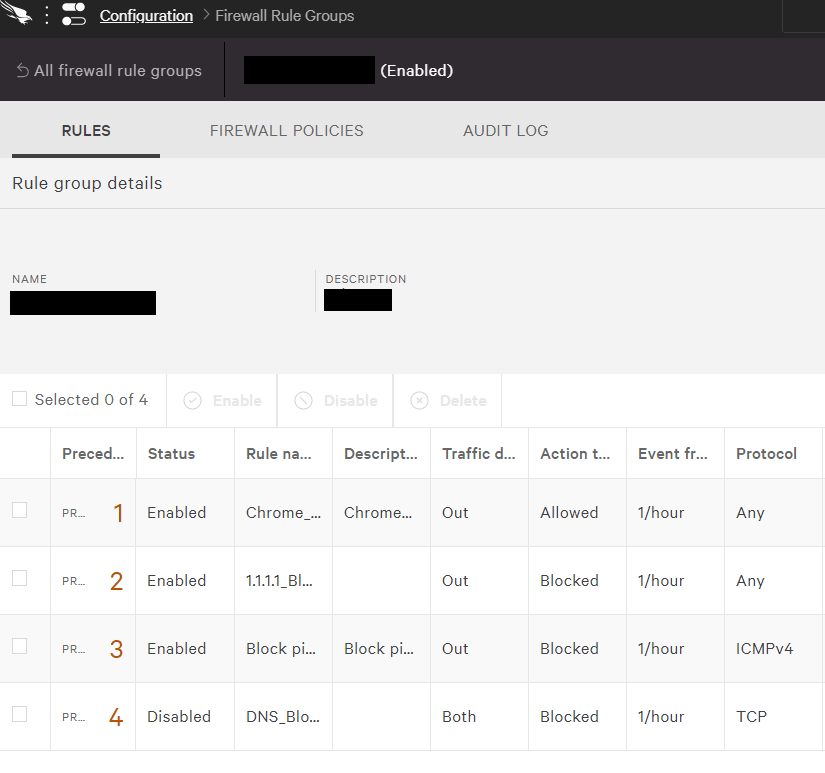
- The firewall settings of the terminal cannot be managed collectively
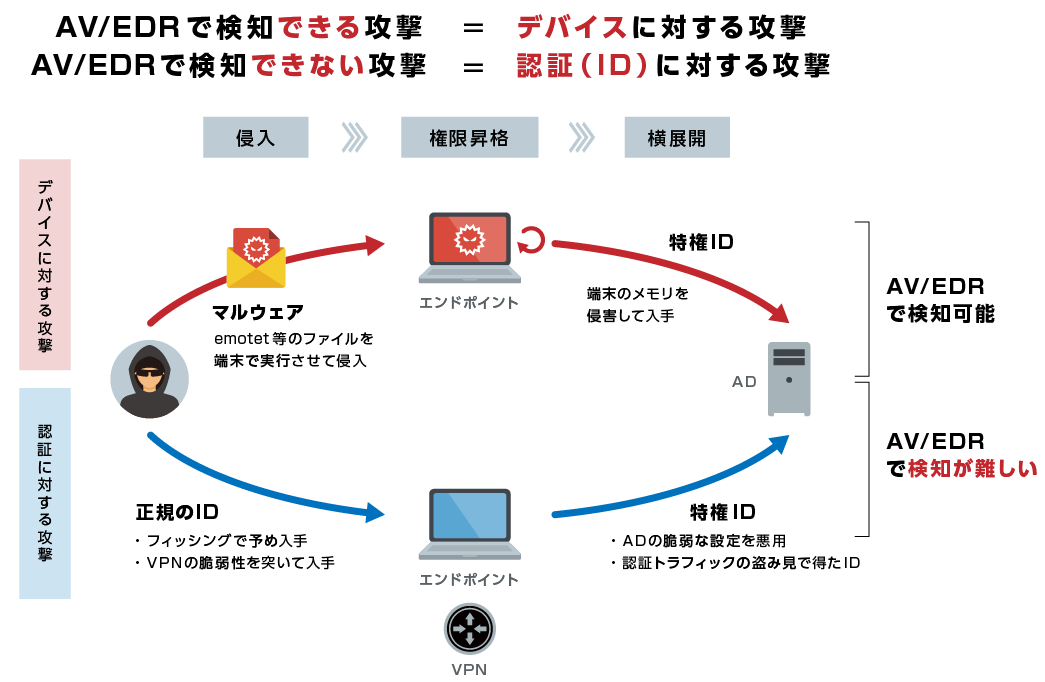
- Insufficient response to attacks targeting authentication (AD)
- Insufficient security measures for cloud assets
- As cloud services become more widely used, it is difficult to grasp the IT assets that need to be managed by the company.
- Difficulty managing multiple SaaS configurations used by various business divisions
CrowdStrikeFalcon uses machine learning, AI, behavior, and human eyes to detect, so it can detect not only known/unknown malware, but also advanced attacks such as fileless malware that are difficult to detect with conventional antivirus products.
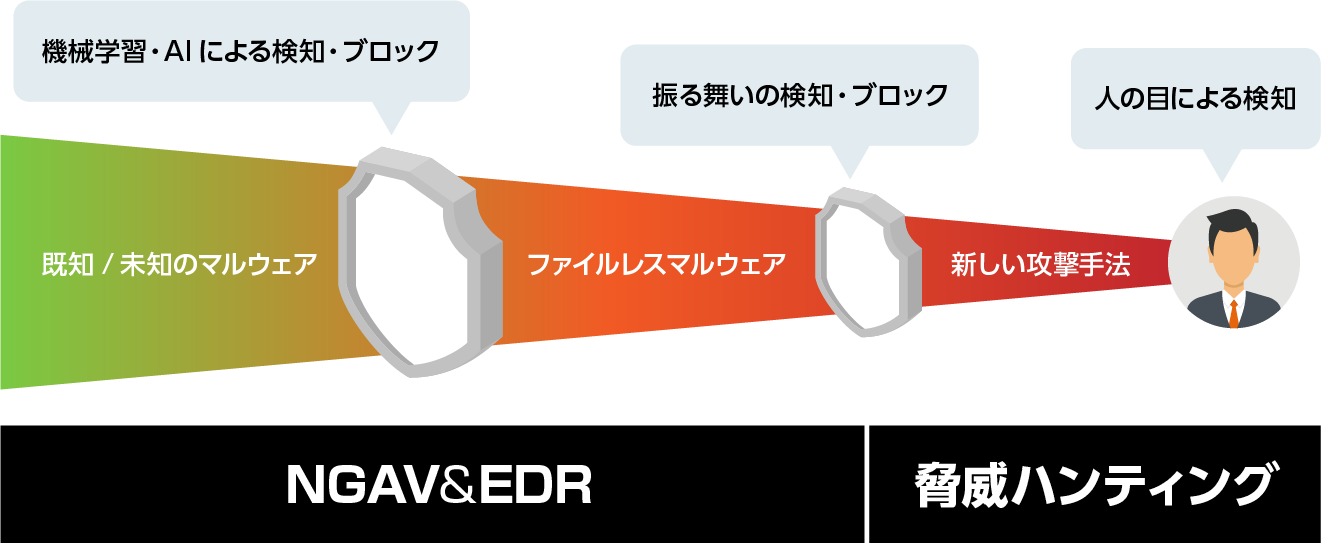
- Click here for details of NGAV products [Falcon Prevent]
- Click here for details on EDR products [Falcon Insight]
- Click here for details of threat hunting products [Falcon OverWatch]
- Are you really okay with that EDR? [CrowdStrike Falcon] for EDR product operation
- Protect your company from advanced cyberattacks with NGAV! [Crowd Strike Falcon]
CrowdStrike Falcon's OverWatch monitors your environment 24 hours a day, 365 days a year, not only detects advanced threats that machines cannot detect, but also investigates the extent of impact and advises on countermeasures. Because of the monitoring system regardless of time, threats that landed outside business hours can also be detected.
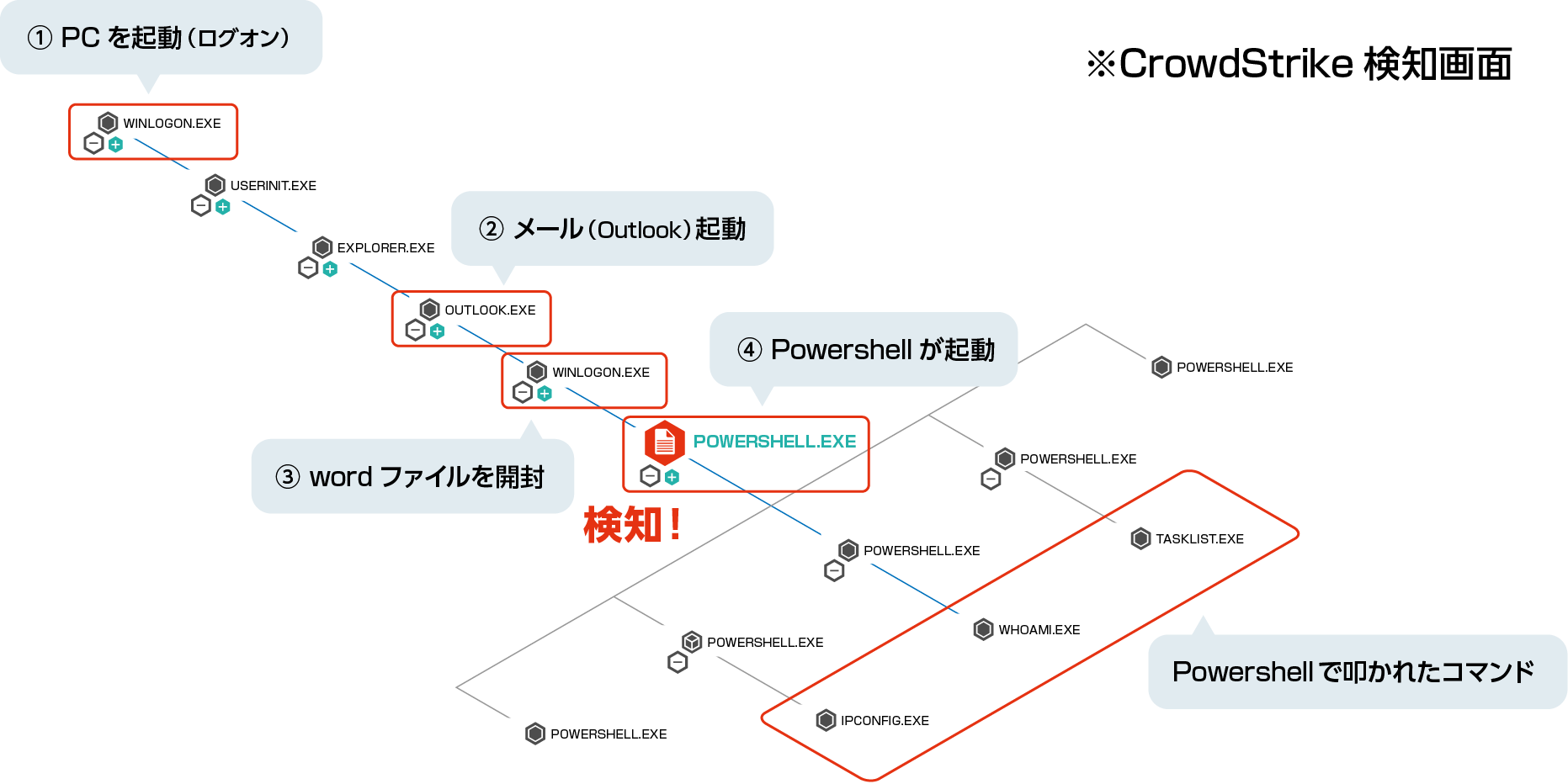
CrowdStrike Falcon records logs in the cloud in real time, so even if an attacker deletes traces from the terminal, it is possible to investigate the details of the incident such as the intrusion route. Process activities are visually displayed in chronological order, making it easy to understand the incident status.
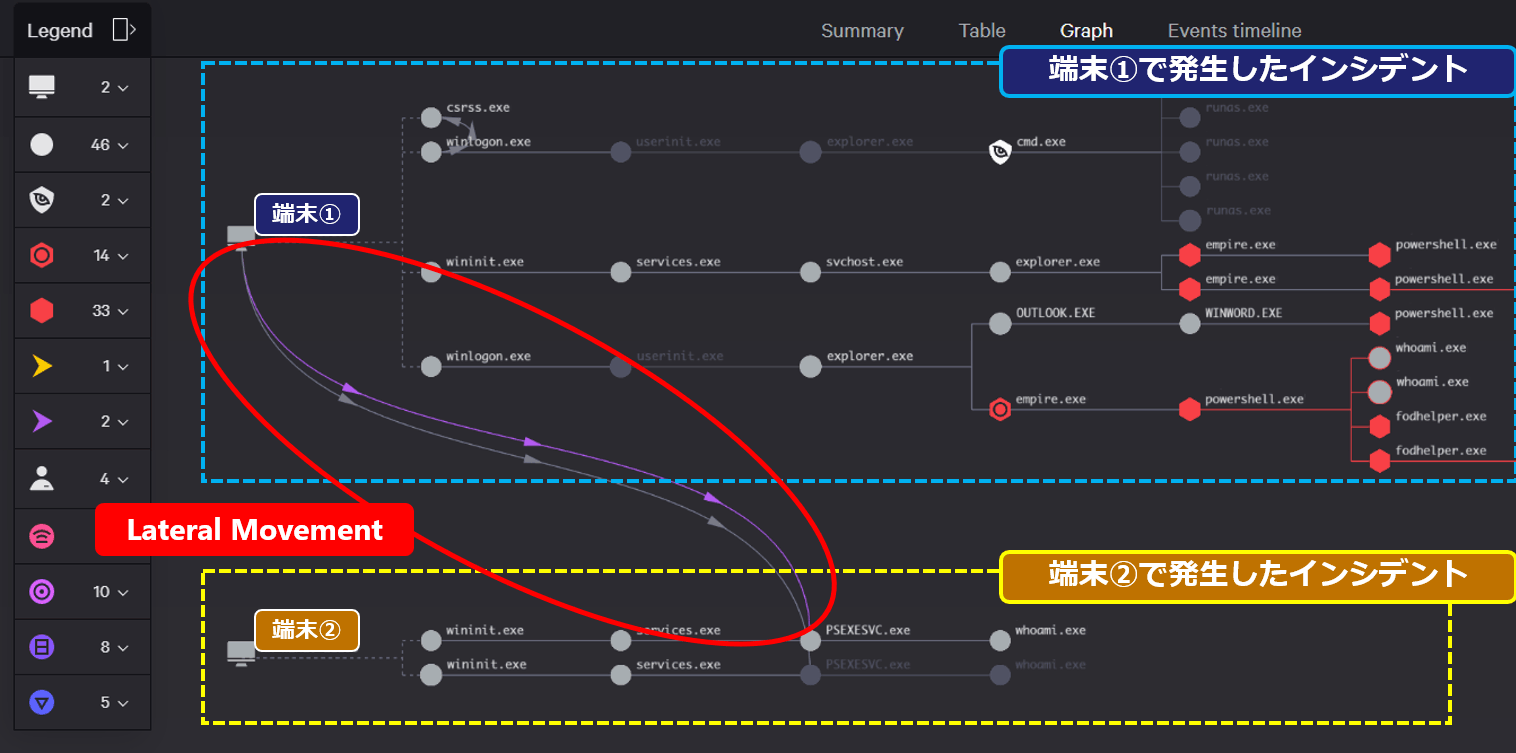
CrowdStrike Falcon not only investigates by alert, but also aggregates alerts and investigates by incident, so the number of alerts can be reduced by more than 10 times and can be displayed, reducing the operational load. Furthermore, it is possible to grasp the horizontal deployment situation from terminal to terminal.
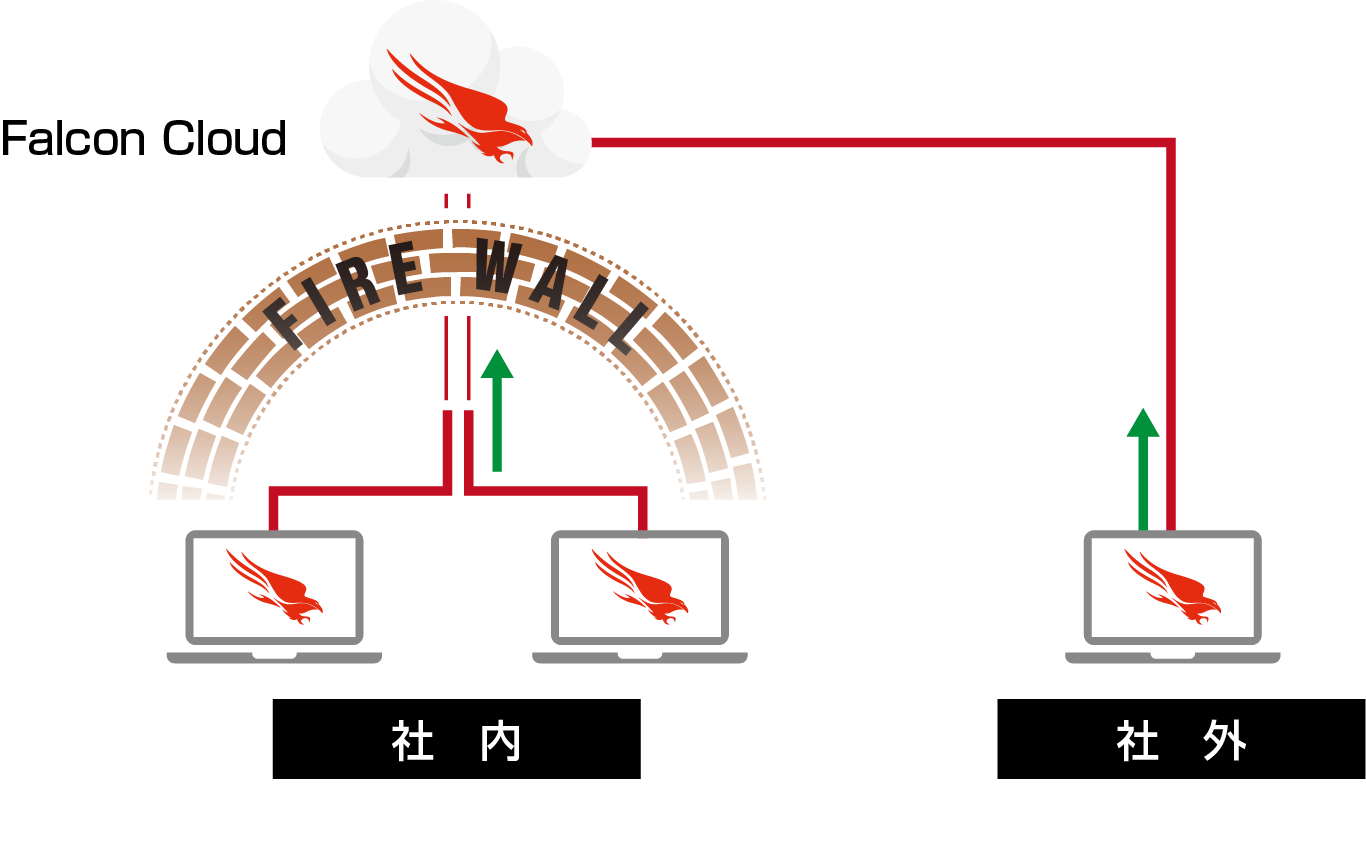
Since CrowdStrike Falcon takes a SaaS approach, logs are recorded in the cloud in real time as long as the device is connected to the network, regardless of the location of the device. Real-time detection and blocking are also performed, so it is possible to reliably defend against threats even on terminals outside the company.
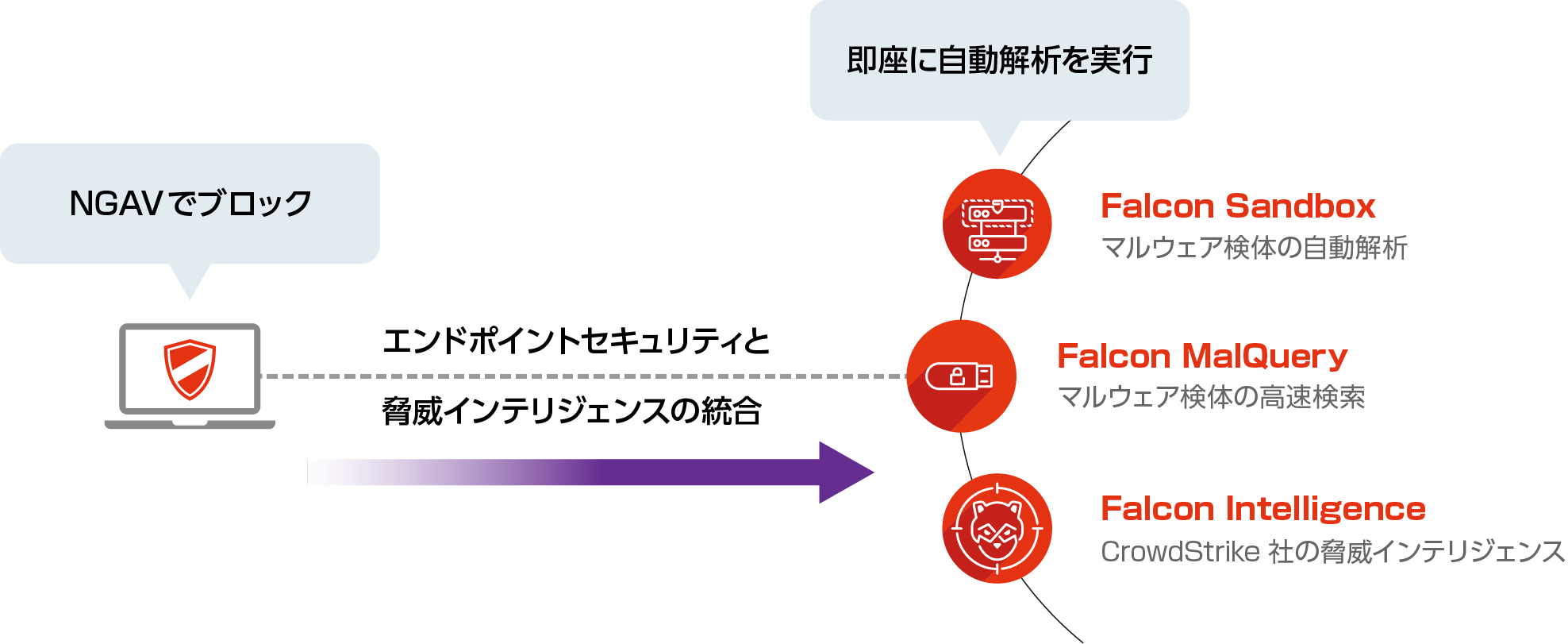
Attacks detected by Falcon Prevent are reliably blocked (by quarantining files and stopping processes, etc.) and automatically link with Falcon Adversary Intelligence to immediately analyze the behavior of files used in attacks, identify attackers, and check for the presence of related malware, thereby significantly reducing the time it takes to respond.
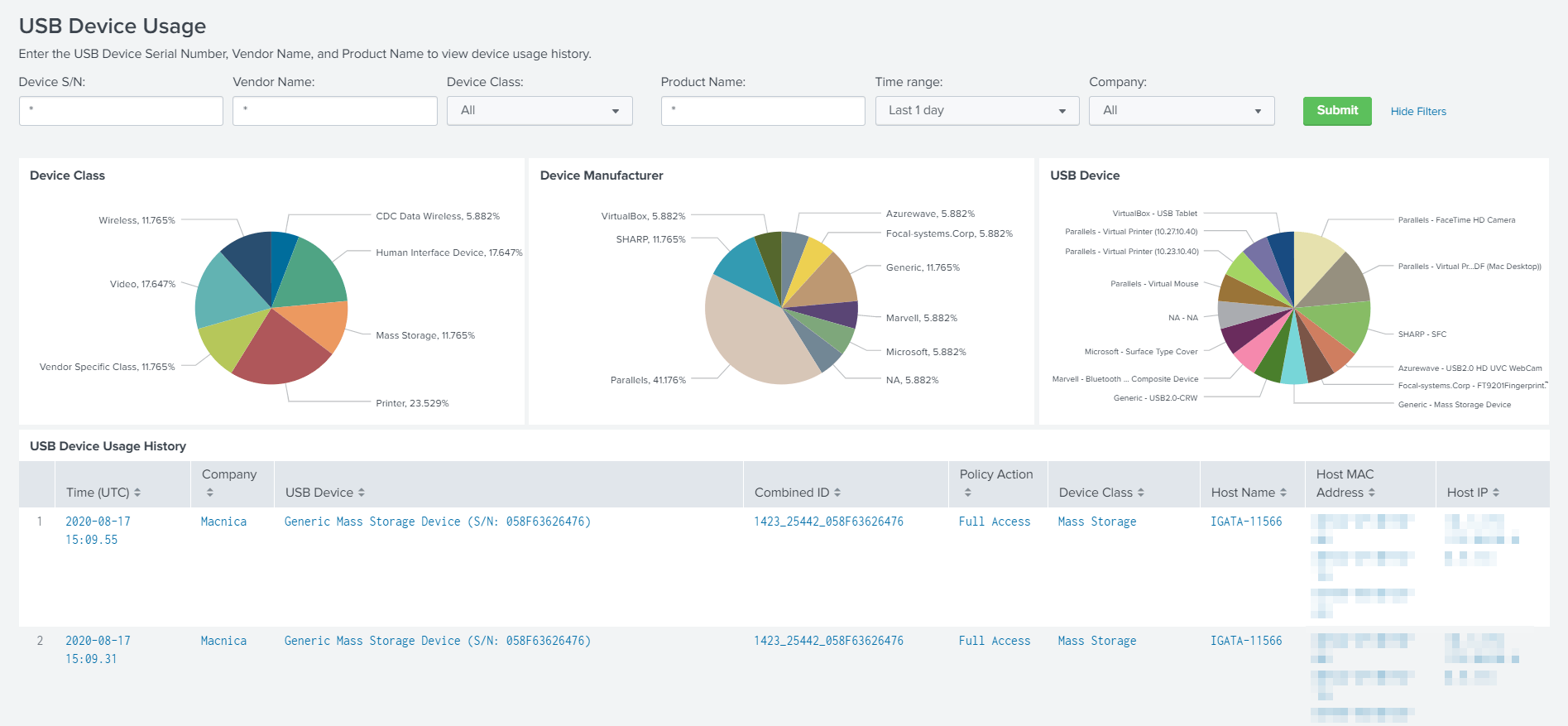
Falcon USB Device Control can visualize device classes (types) used, manufacturers, and device trends. In addition, it is possible to control USB devices by specifying a policy (it can also be divided into groups), and even if it is blocked by a policy, it is possible to check which USB device was used, when and by which terminal.
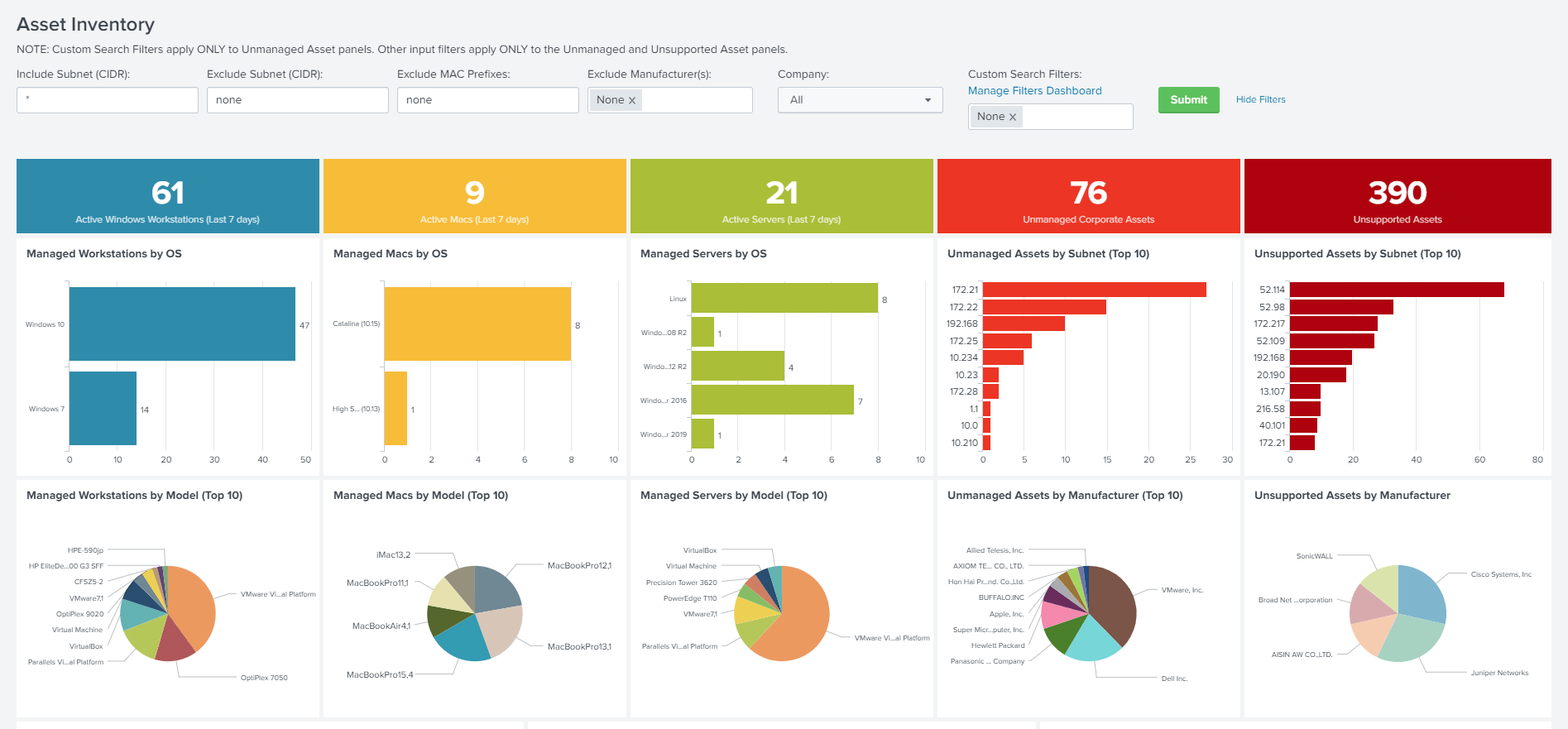
The asset management function of Falcon Discover not only visualizes what kind of assets the terminals/servers on which Falcon is installed are used, but also information on terminals on which Falcon is not installed. It is possible to find unmanaged terminals.
The application visualization function of Falcon Discover visualizes the applications and versions installed on each terminal, so when an application vulnerability is announced, it is possible to investigate which terminal has the vulnerability. Possible. In addition, Spotlight automatically collects and visualizes vulnerabilities (CVE) and unapplied KB that exist in the terminal, so it is possible to visualize vulnerabilities in real time.
Windows OS standard firewall can be managed from Falcon's management console. Set firewall policies via Falcon's agent for rapid rule enforcement across your environment.
Falcon Identity Threat Protection/Detection learns authentication traffic in the deployment environment, making it possible to detect and block attacks against authentication (ID) that are difficult to detect and block using conventional AV/EDR.
Falcon Cloud Security provides visibility into cloud misconfigurations and protects cloud workloads, containers, and Kubernetes applications.
This module provides the following three functions:
Identifying cloud service misconfigurations (IOM) and suspicious behavior/attacks (IOA),
Compliance status can be checked.

Visualize and manage the permissions associated with IDs on cloud services.
It helps to identify IDs that have been granted excessive privileges and ensure proper use of privileges.
Cloud workloads, containers, and Kubernetes environments
Provides visibility and threat protection.
Falcon Surface enables visualization of a customer's publicly-available IT assets and the associated risks and vulnerabilities, helping with customer IT operations and security measures.

- Monitor all assets exposed to the internet
- Scoring your entire environment and identifying priority assets for action

- Identification and visualization of vulnerabilities in vulnerable servers and NW devices
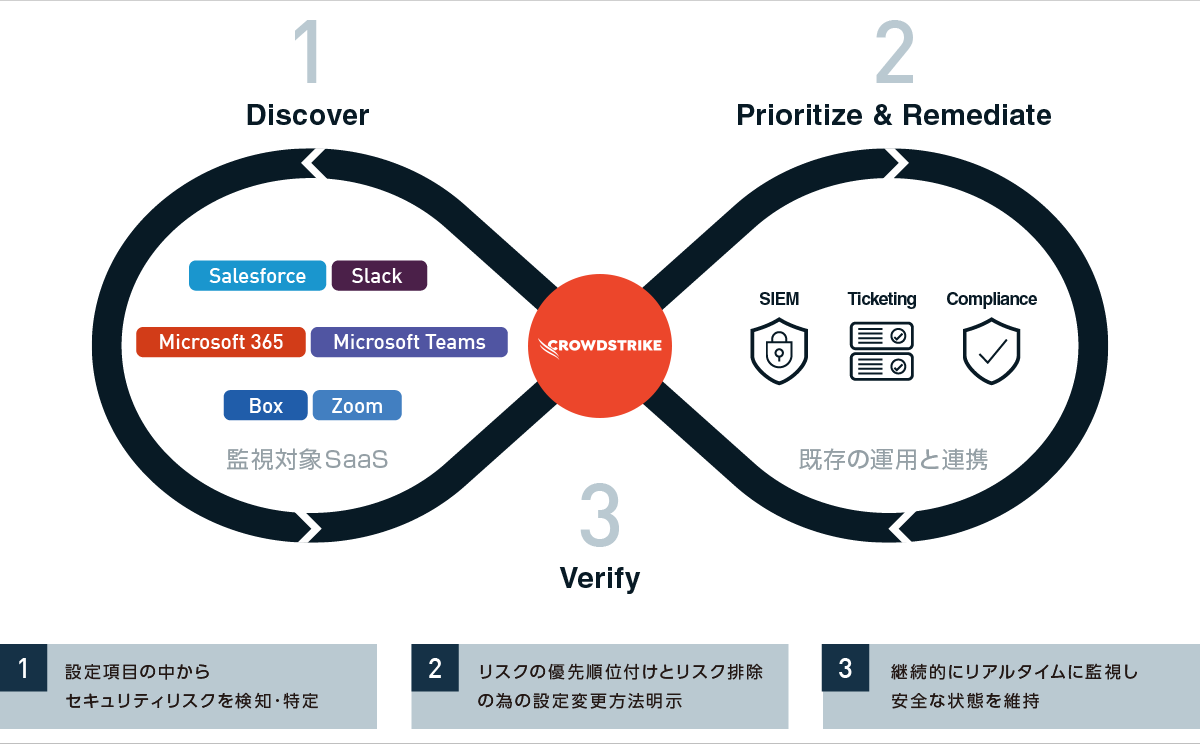
Falcon Shield is an SSPM solution (SaaS Security Posture Management) that audits SaaS settings. It provides a function to continuously check whether security settings and compliance with various compliance standards are met in order to ensure the safe use of SaaS.
It enables cross-sectional risk management of SaaS used by various business divisions, and realizes best practices that reflect the latest state of SaaS, security frameworks, etc. As part of your current security operations, you can manage SaaS governance with minimal additional effort.
Inquiry/Document request
In charge of Macnica CrowdStrike Co., Ltd.
- TEL:045-476-2010
- E-mail:crowdstrike_info@macnica.co.jp
Weekdays: 9:00-17:00