product
- What you can do with CrowdStrike
- CrowdStrike Modules Falcon
- Falcon Prevent(NGAV)
- Falcon Insight(EDR)
- Falcon OverWatch (Threat Hunting)
- Falcon Discover (IT Asset Management)
- Falcon Spotlight (vulnerability management)
- Falcon Adversary Intelligence
- Falcon Identity Threat Protection/Detection
- Falcon Cloud Security(CNAPP)
- Falcon Surface(EASM)
- Falcon Shield(SSPM)
- Falcon Next-Gen SIEM
service
Application for evaluation machine
- FAQ

CrowdStrike
CrowdStrike
IT Asset Management (Falcon Discover)
CrowdStrike's Falcon Discover is a module that visualizes IT assets within an organization based on terminal logs collected by Falcon Insight (EDR).
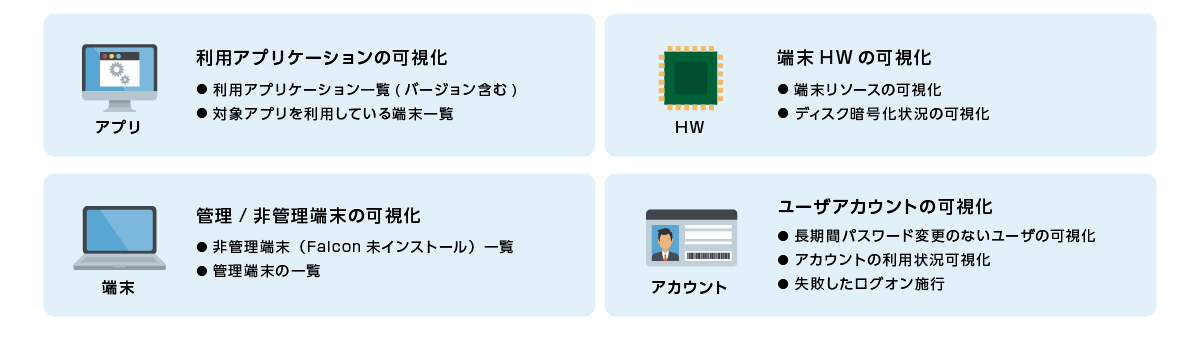
It is possible to visualize the shadow areas in the customer environment from the perspective of "application", "managed / unmanaged terminal", "HW", and "account".
Focus on IT hygiene
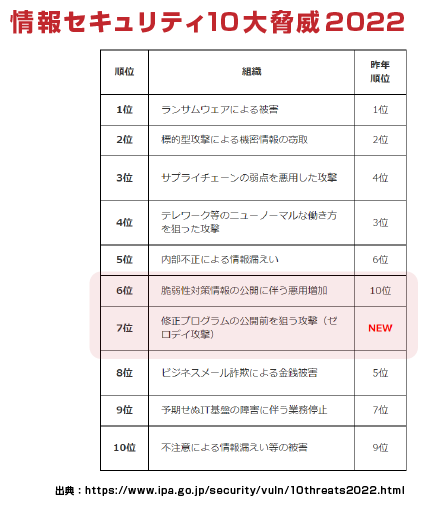
Recently, there have been many cases of attacks using vulnerabilities*, such as malicious attacks such as unauthorized access and ransomware.
* Refers to information security defects caused by program defects or design errors in computer OS and software.
The concept of IT hygiene (also known as cyber hygiene, security hygiene, and IT hygiene management) is attracting attention as a countermeasure against these threats.
IT hygiene is a concept that aims to keep endpoints up-to-date and appropriate, maintain the health of the system, and protect it from internal and external threats.
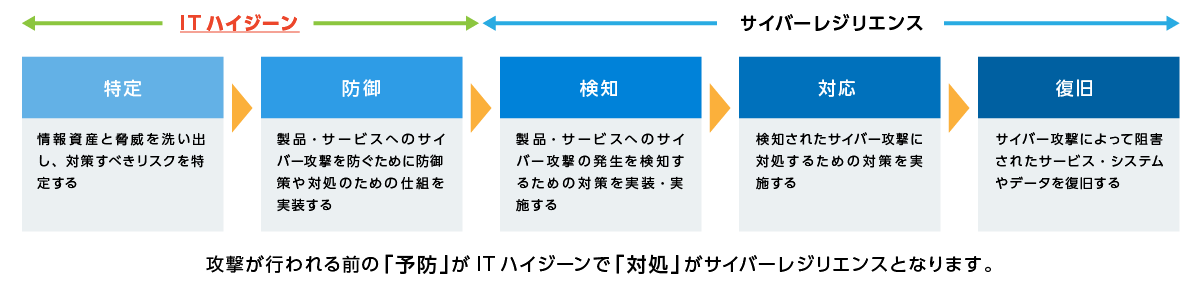
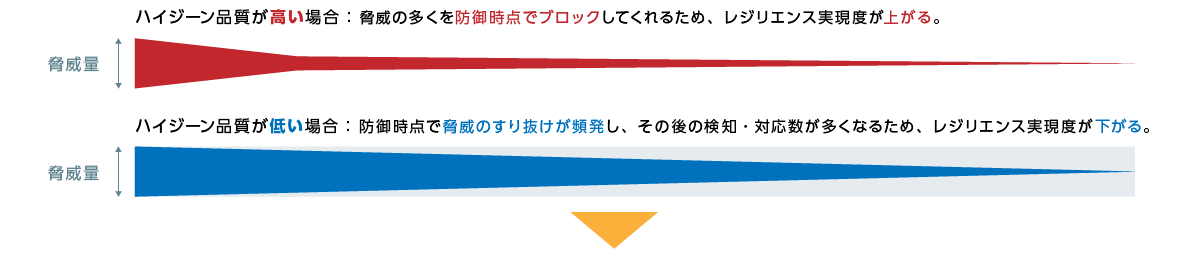
Having visibility across your environment is the first step towards IT hygiene. With Falcon Discover, you can address potential blind spots within your organization.
Value provided by CrowdStrike Falcon Discover
(1) Visualization of applications used
Visualize applications installed on devices with sensors from multiple perspectives, such as versions, devices with sensors installed, and devices without sensors
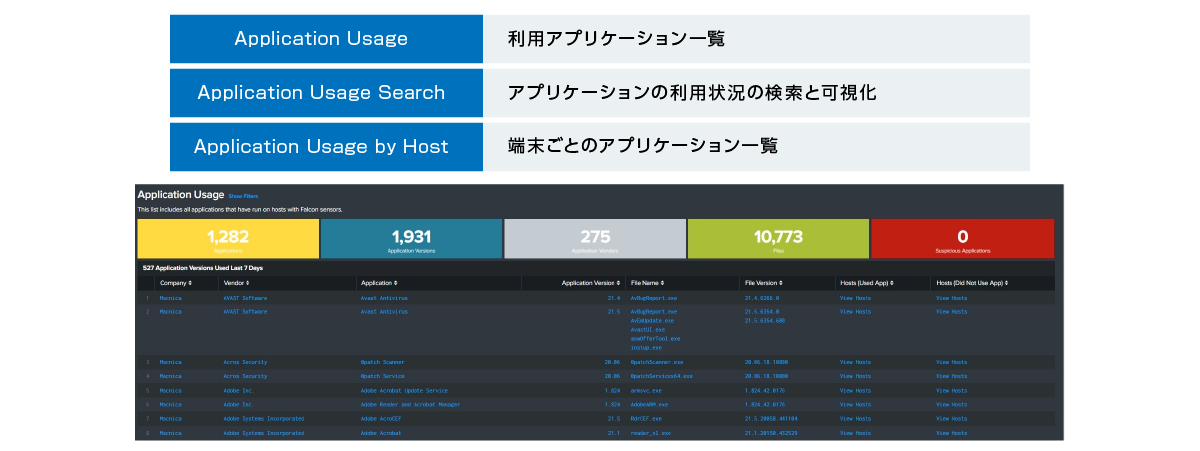
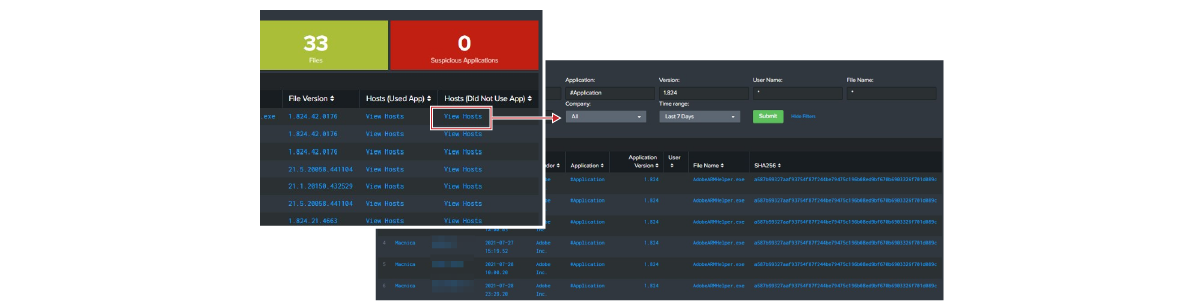
Extract the list of terminals using the application and the list of terminals not using the application
You can check each version and visualize whether it is being operated properly and on which terminal it is being used.
(2) Visualization of managed/unmanaged terminals
Visualize terminals with/without sensors and NW devices
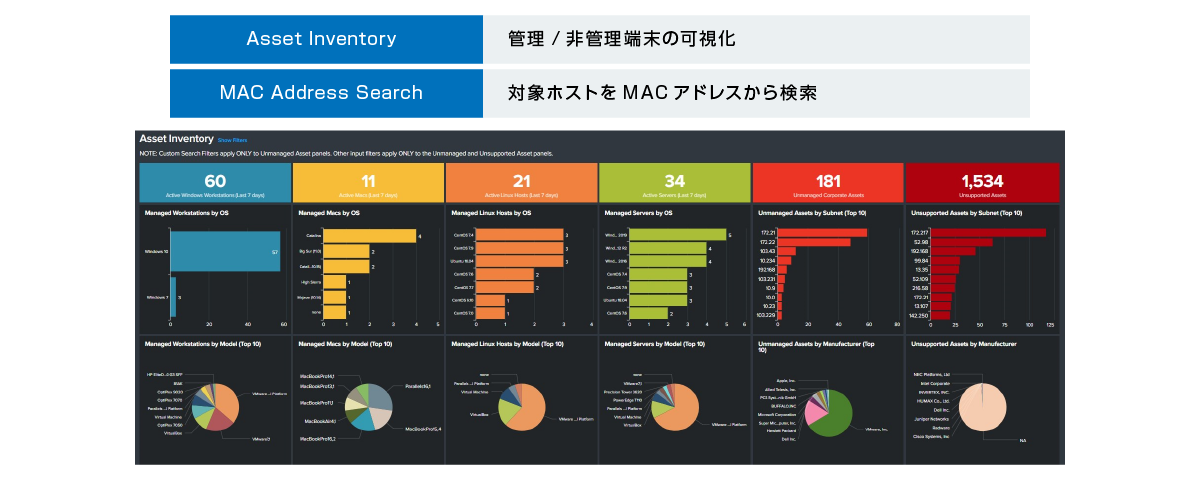
Based on the ARP information of the terminal where the sensor is installed, the equipment where the sensor is not installed is visualized, and based on the vendor information, the equipment where the sensor can be installed (Unmanaged Corporate Assets) and the network equipment where the sensor cannot be installed (Unmanaged Corporate Assets) Visualize Unsupported Assets
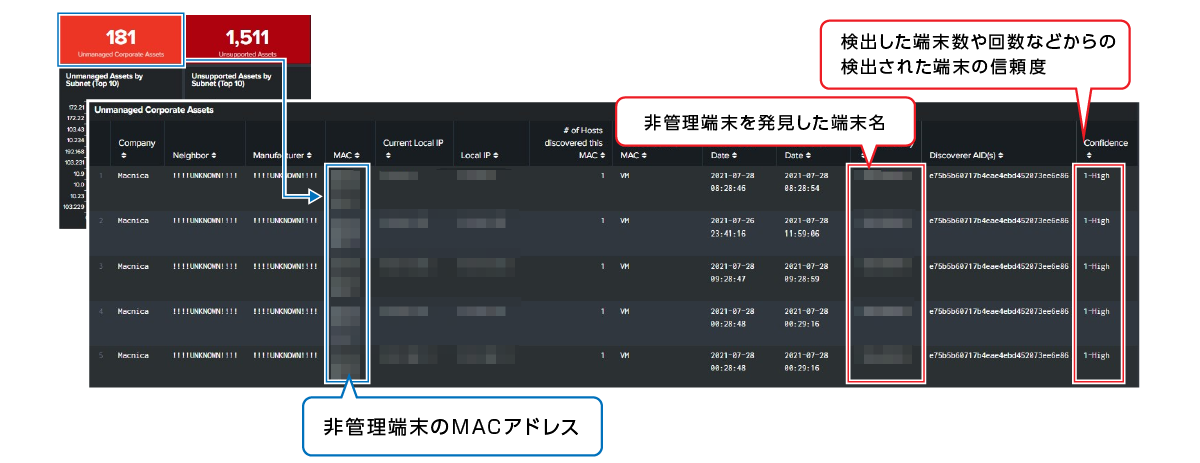
Value provided by CrowdStrike Falcon Discover
Visualization of terminal HW
Visualize HW information, resources, and device encryption status of terminals where sensors are installed
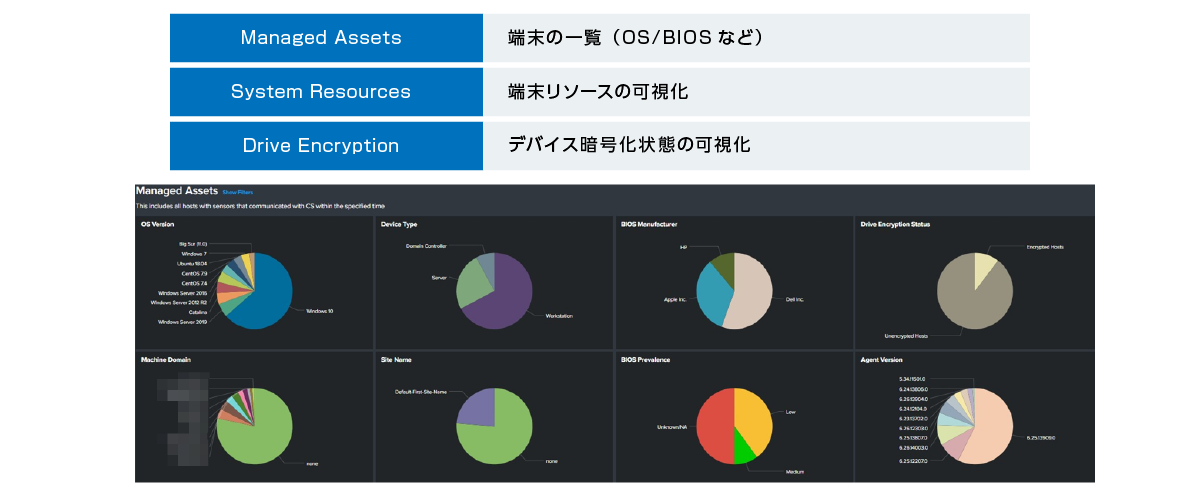
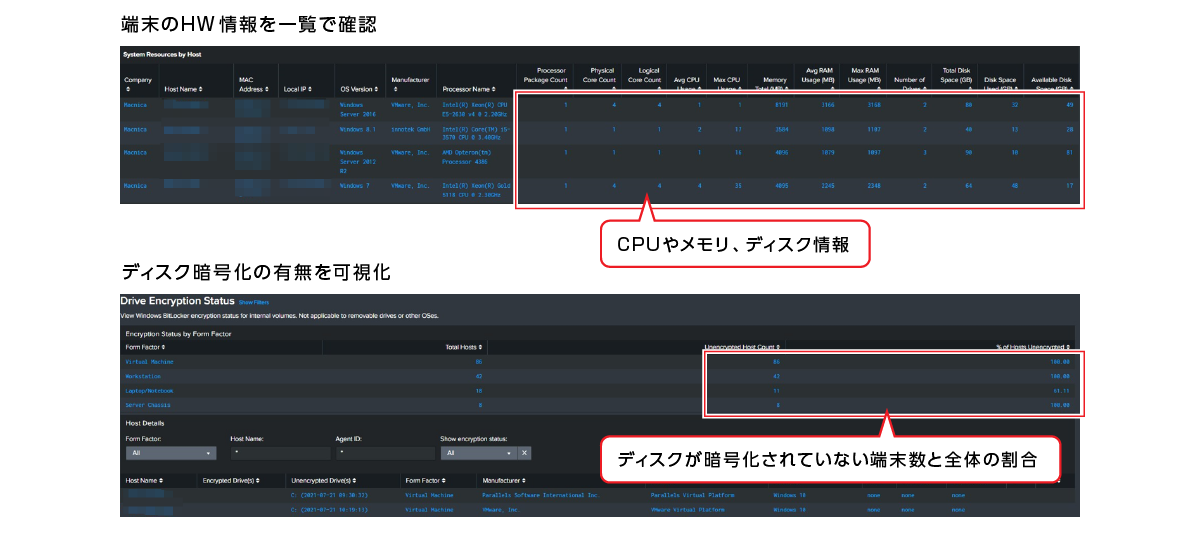
Value provided by CrowdStrike Falcon Discover
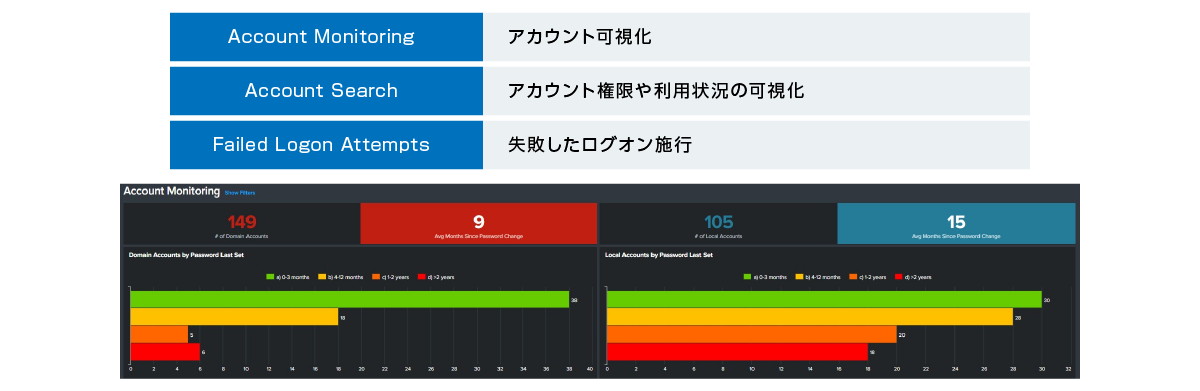
④ Visualization of user accounts
Visualize HW information, resources, and device encryption status of terminals where sensors are installed
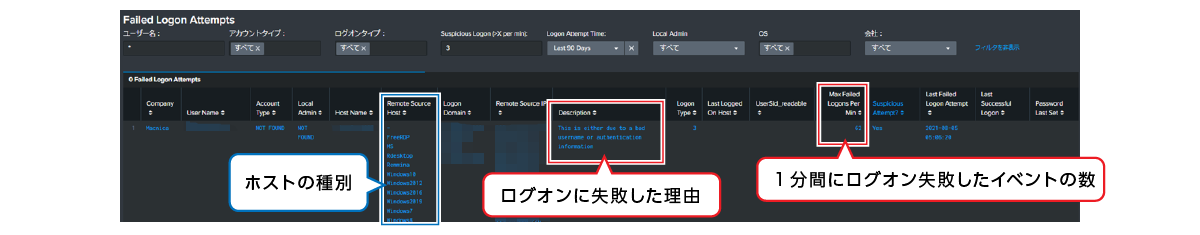
Check the type of account logged in (Local or Domain) and whether you have administrator privileges.
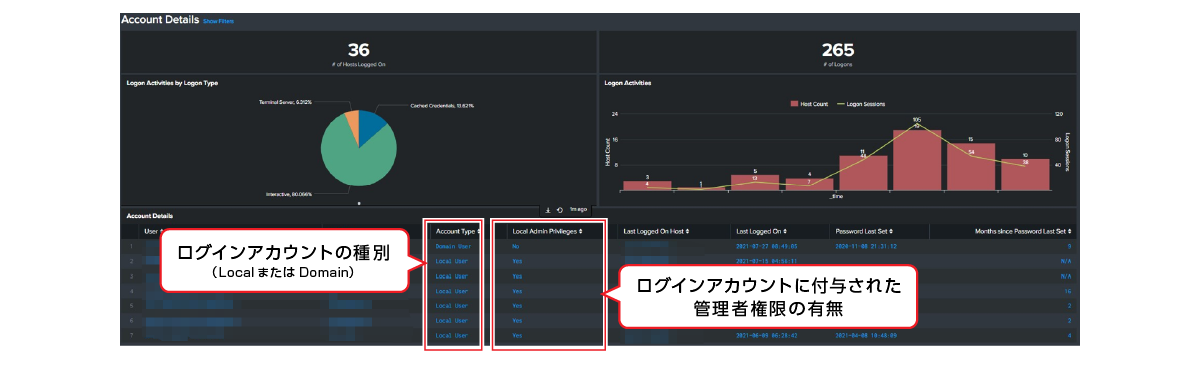
Visualize failed logon events and discover suspicious behavior
Inquiry/Document request
In charge of Macnica CrowdStrike Co., Ltd.
- TEL:045-476-2010
- E-mail:crowdstrike_info@macnica.co.jp
Weekdays: 9:00-17:00