product
- What you can do with CrowdStrike
- CrowdStrike Modules Falcon
- Falcon Prevent(NGAV)
- Falcon Insight(EDR)
- Falcon OverWatch (Threat Hunting)
- Falcon Discover (IT Asset Management)
- Falcon Spotlight (vulnerability management)
- Falcon Adversary Intelligence
- Falcon Identity Threat Protection/Detection
- Falcon Cloud Security(CNAPP)
- Falcon Surface(EASM)
- Falcon Shield(SSPM)
- Falcon Next-Gen SIEM
service
Application for evaluation machine
- FAQ

CrowdStrike
CrowdStrike
Threat Intelligence (Falcon Adversary Intelligence)
Falcon Adversary Intelligence is an automated threat analysis platform module that integrates threat analysis, malware database, threat intelligence, and digital risk monitoring.
Discovered malware and suspicious files can be analyzed, and the results can be collated with CrowdStrike's threat intelligence, such as information about related malware and attackers.
We contribute to strengthening customer security by providing information on threats.
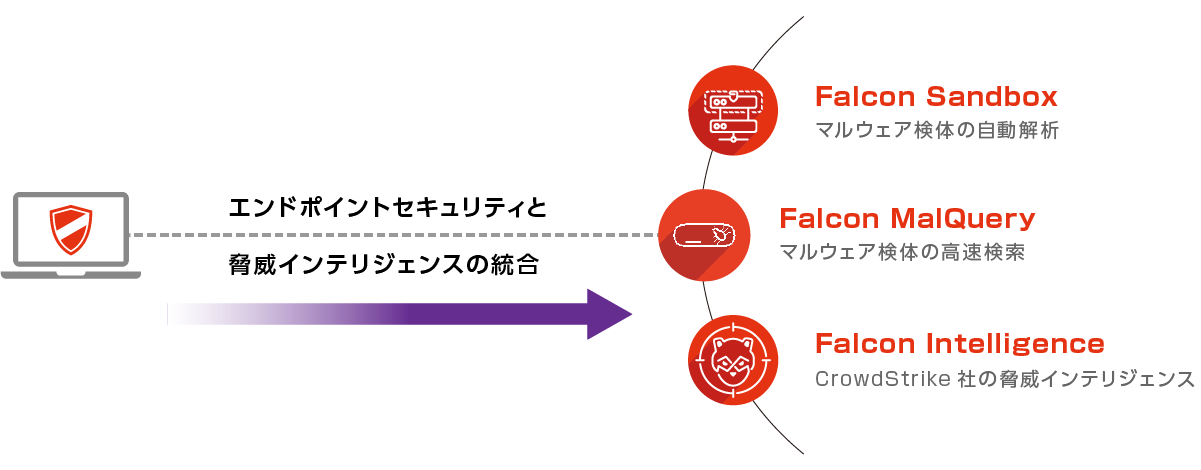
When a malware is detected, it can be treated as complete by blocking or quarantining, but it is not possible to confirm what kind of impact it may have if the malware actually infringes.
In addition, if there is no information on the existence of similar malware or the methods of attackers, there is a possibility of additional detections and impacts.
The use of threat intelligence is effective when obtaining information such as what kind of attacker uses what kind of malware, tools, and methods to cause what kind of impact.
By using threat intelligence to confirm the type of attack instead of leaving it as it is when a detection occurs, it is possible to strengthen your company's security measures.
Three Values That Falcon Adversary Intelligence Can Achieve
1. Immediately understand the purpose and impact of an attack and strengthen your organization's security system
When a malware is detected, the response can be completed by blocking or isolating the malware, but in order to determine what impact the malware might have if an intrusion actually occurs, external investigations and experts must often be relied upon, which can delay the initial response.
Utilizing threat intelligence makes it possible to instantly obtain information on what type of attacker is using what malware, tools, and methods, and what impact they are causing, enabling a rapid initial response and contributing to strengthening an organization's security system.
②Analysis of unknown and suspicious files and identification of threats in a short time
Detailed analysis of suspicious files requires specialized knowledge and the involvement of external companies, and investigations can take time. In the meantime, there is a risk that similar attacks may spread inside and outside the company, or that containment may be compromised.
By utilizing threat intelligence, it is possible to instantly execute and analyze the behavior of not only suspicious files quarantined by EDR, but also unknown attachments received by email and suspicious URLs in an isolated environment on the cloud, making it possible to visualize malware operations, data tampering, etc. Analysis tasks that previously required the assistance of experts can now be judged and handled in a short time by SOC and IT personnel.
3) Monitor information on the Internet and strengthen predictive detection and information leak prevention measures
It is difficult to monitor for signs of information leaks or attacks on your company's data in areas that cannot be found through general Internet searches, such as the dark web, deep web, underground forums, and social media, and in many cases you only become aware of a data leak after you have been attacked.
By utilizing threat intelligence, it is possible to constantly monitor these areas that are invisible on the normal Internet and quickly detect signs of leaks of your company's brand name, account information, and confidential data, as well as posts of attack plans. Signs of information leaks and targeted attacks that were previously only noticed after an attack can now be visualized before an attack, leading to rapid countermeasures.
①Analysis function (Sandbox)
Box analysis of files detected and quarantined by CrowdStrike's NGAV capabilities, as well as other suspicious files.
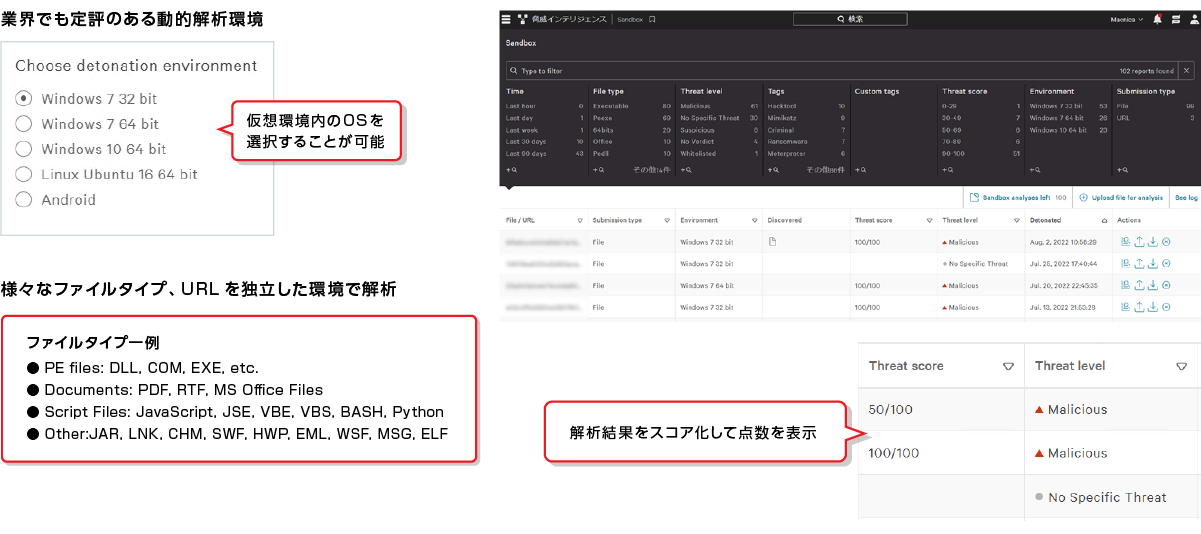
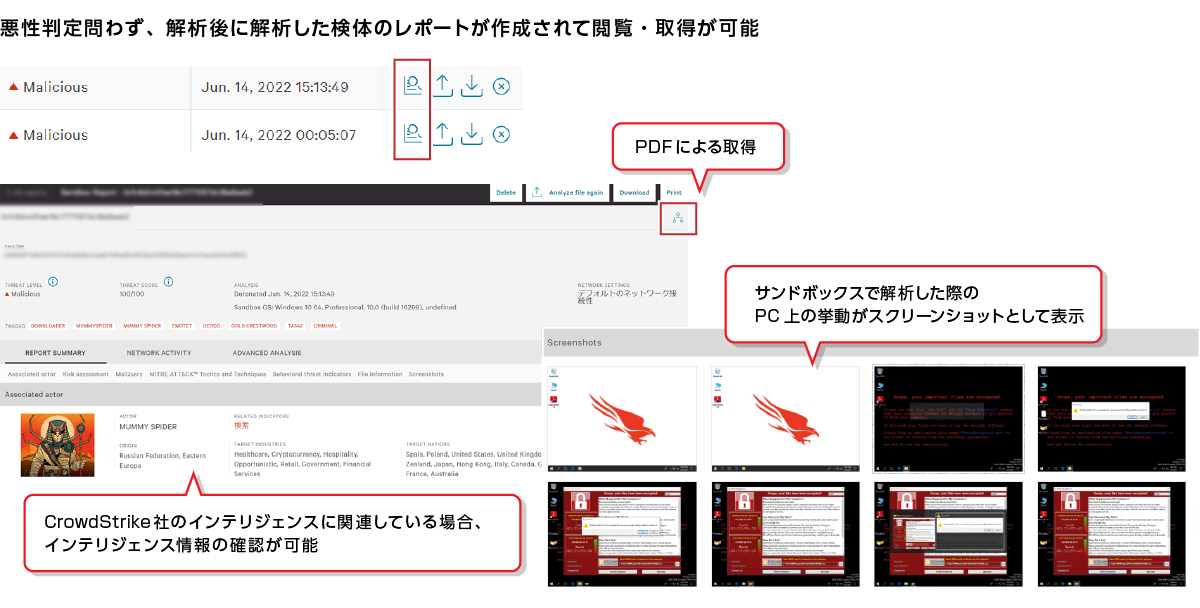
Analysis results can be obtained as a report.
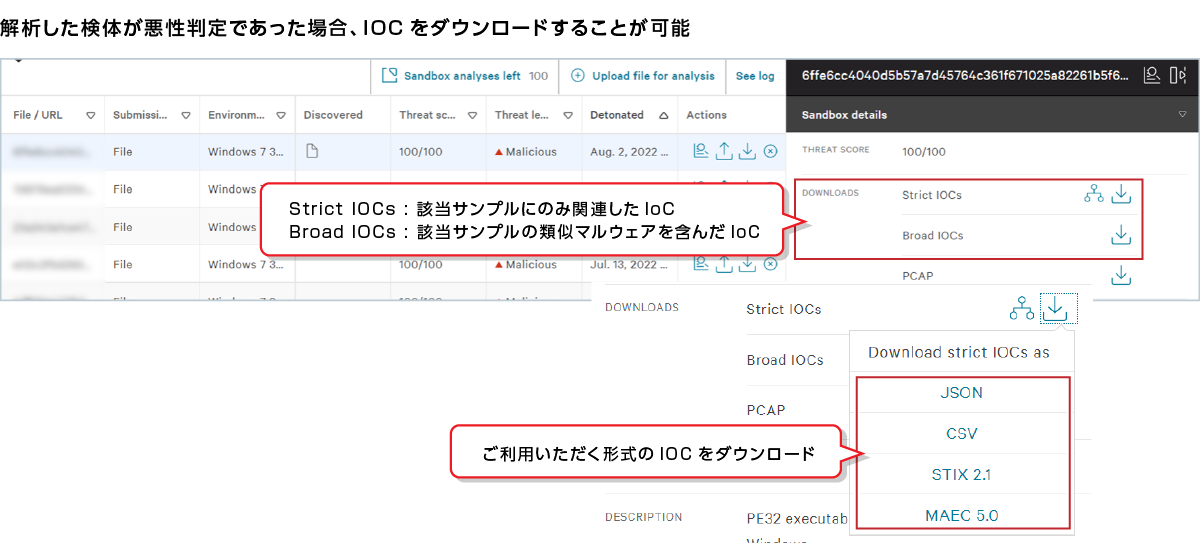
If the analysis result is malignant, you can download an IOC that can be used in other security products.
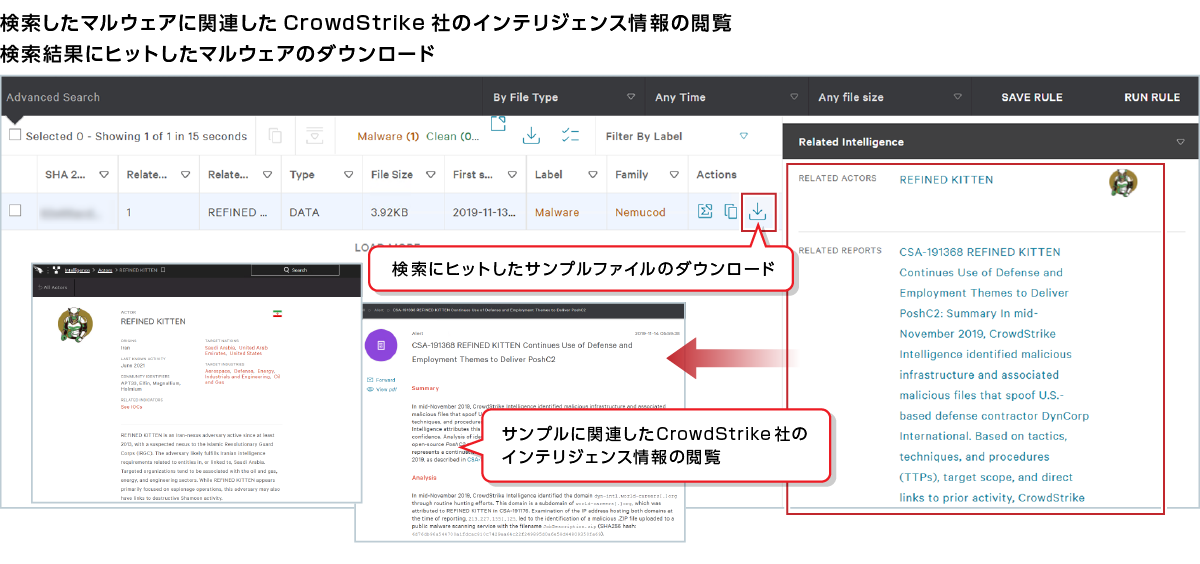
②Malware database (MalQuery)
You can search for malware using CrowdStrike Holdings、Inc. 's intelligence and view information on similar malware.
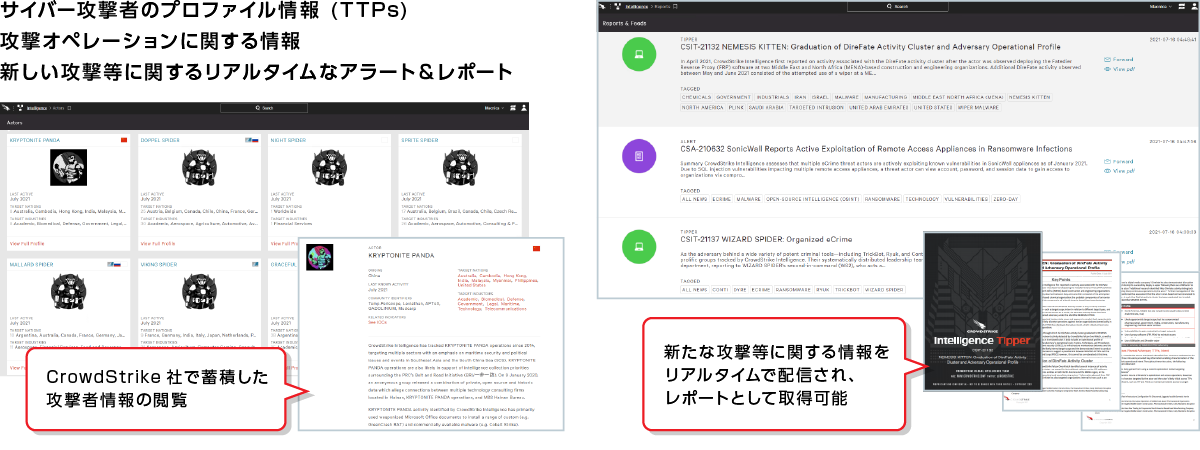
3) Threat Intelligence regarding attackers
Information and reports on cyber attacker profiles and attack operations are available.
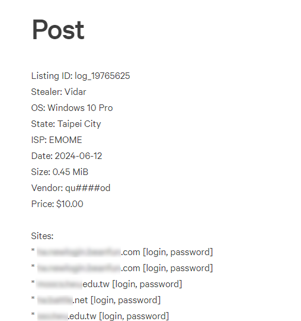
④Digital risk monitoring (Recon)
You can monitor underground markets, social media, online message boards, leak sites, etc., and visualize in real time whether your company's information has been leaked.
Recon search target
- Dark Web
- Social media
- Underground Forum
- IRC Channel
You can create monitoring rules to be notified if a leak is found.
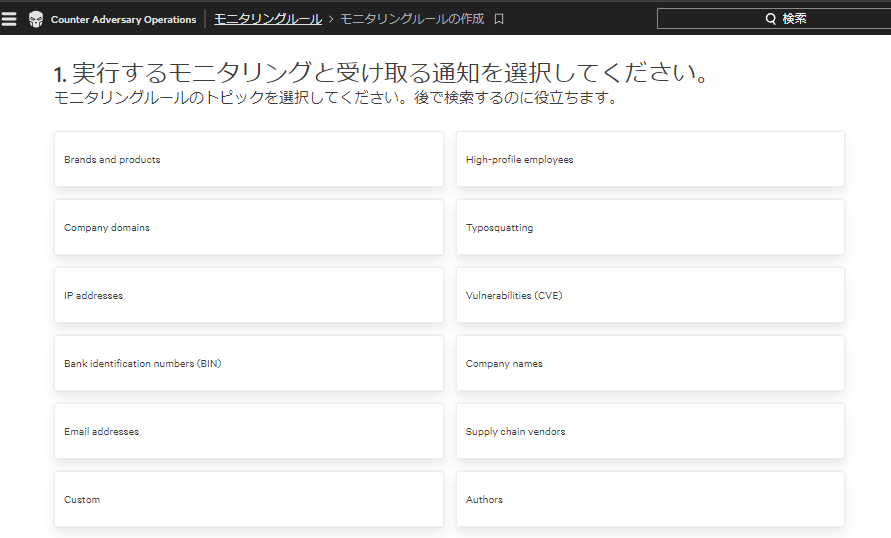
Fusion SOAR can also be used to manage tickets in conjunction with ServiceNow or Jira if a leak is found.
|
Examples of categories that can be monitored |
detail |
|
Author |
Names or aliases of contributors to specific sites or sources |
|
Bank Identification Number (BIN) |
The first part of a credit card number that identifies which financial institution the card belongs to. |
|
Brands and Products |
The brands and products that the company owns or produces. |
|
Company Domain |
A web domain owned by your organization. |
|
company name |
Interest groups and organisations within the industry. |
|
email address |
Contact's email address or distribution list |
|
Executive |
Name of the leader of your organization |
|
IP address |
Sensitive IP addresses in your environment. |
|
supplier |
A third-party partner that an organization uses to produce goods or services. |
|
Typosquatting |
Newly created or recently updated variations of domains that use terms that impersonate an organization or brand. *If a malicious domain is found, you can request a takedown. |
|
Vulnerabilities (CVE) |
Common Vulnerabilities and Exposures (CVE) or publicly known cybersecurity threats. |
Inquiry/Document request
In charge of Macnica CrowdStrike Co., Ltd.
- TEL:045-476-2010
- E-mail:crowdstrike_info@macnica.co.jp
Weekdays: 9:00-17:00