product
- About Cato Networks
- About Cato Cloud
- Unification of shadow IT countermeasures by Cato CASB,
- Information leakage countermeasures with Cato Smart DLP
- Safe website browsing with Cato RBI
- CATO socket Easily connect existing LAN environment to SASE. Migration to SASE made easy
- Cato SASE XDR
- Cato DEM(Digital Experience Monitoring)
service
Application for evaluation machine
- FAQ

Cato Networks
Cato Networks
What is the difference between Cato Client application VPN and ZTNA?
When I first heard about Cato VPN Client, I had these questions.
- Is Cato a VPN even though it's ZTNA?
- I don't know much about VPNs and ZTNA, but VPNs aren't that good, are they?
Overview
- What is ZTNA (Zero Trust Network Access)?
A major feature is that by inspecting all traffic, only safe communication can be passed. - What is a VPN (Virtual Private Network)?
It's about communication technology (virtual leased line), not about the common remote work environment. A common remote work environment is the perimeter defense described below.
(*Since there are many articles on the Internet about ZTNA and VPN, I made it simple)
Existing remote work environment (perimeter defense)
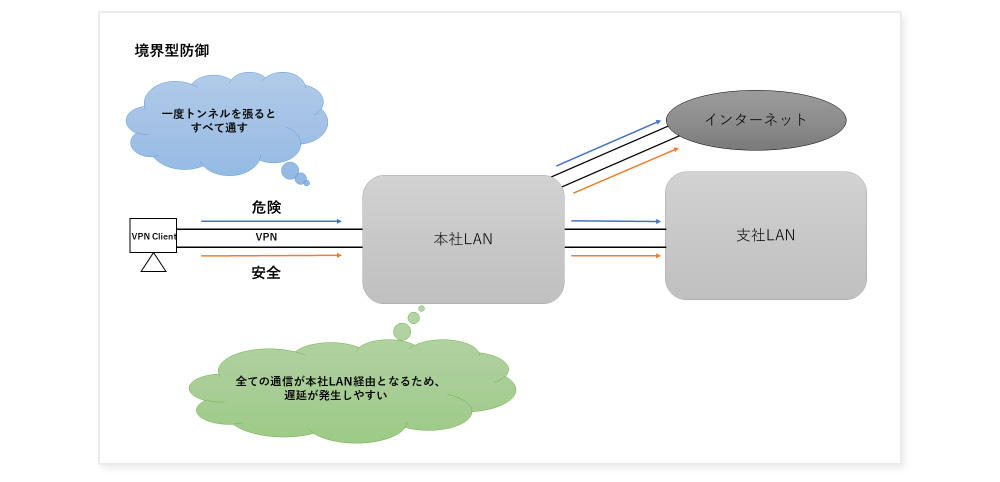
Demerit
- Once allowed to connect, various accesses to the corporate network are possible.
→ There is a risk of unauthorized access by malicious employees, the loss or theft of user authentication information, and the removal of confidential data when leaving the company. - In the case of the above example, since all communications are routed through the head office LAN, accesses concentrate on the VPN device, causing traffic congestion and delays.
Secure access from outside the office with Cato VPN Client
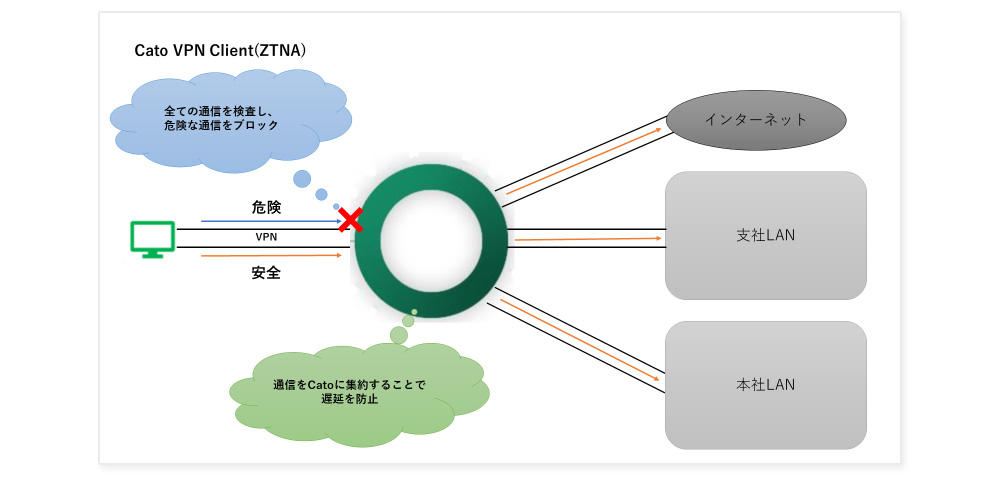
merit
- Since all communications are inspected even after permission to connect to Cato, access restrictions and malicious/dangerous access are blocked. Granular control over security protection.
- Cato uses UDP (DTLS tunnel) as the default connection method, so lightweight and secure communication is realized.
<Point 1: Abundant control methods>
- Not only IP, FQDN, domain, but also application level can be controlled
(Simply select the appropriate application from Applications. Easy to set) - You can also block calls from specified countries.
- Inspection with IPS and Anti-Malware (optional) is also possible
- With the CASB function, it is also possible to control by the operation of the application such as YouTube viewing prohibition and Twitter posting prohibition
- With DLP function, it can be controlled by the contents of the file to be downloaded
⇒Since all these are controlled in PoP (Point of Presence), it is completed only with Socket. Operational burden is reduced.
All communications are routed through Cato, reducing congestion due to the centralization of perimeter-type defense in-house GWs.
(All communications use Cato's full-mesh, dedicated private backbone. With over 75 PoPs worldwide, communication takes the shortest path between PoPs.)
<Point 2: Flexible access method>
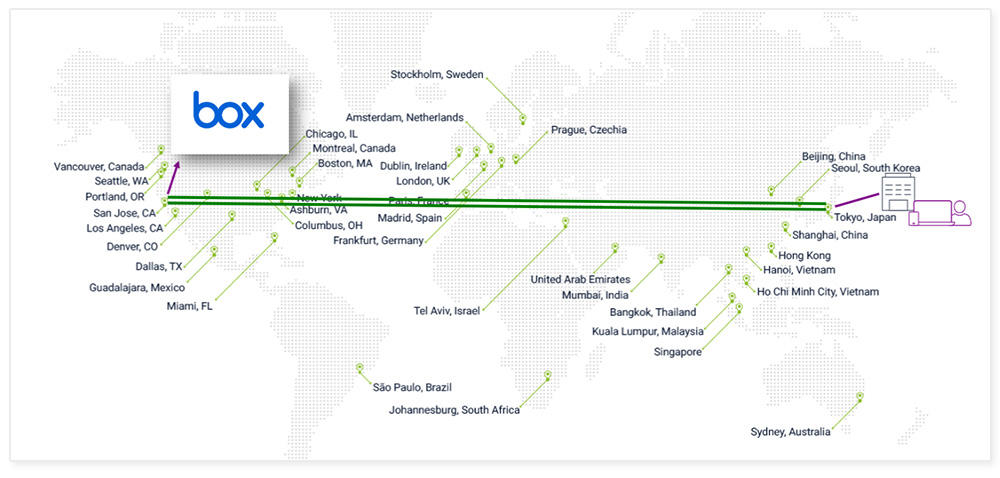
The image below shows a user in Tokyo accessing box, a cloud collaboration service located in the United States, through Cato's backbone.
- You can NAT to the corresponding IP at PoP.
(Valid when the source IP is restricted on the SaaS application side) - While there are apps that can connect globally, there are often SaaS apps that are only available in that country. In addition to fixed IP restriction (NAT), there is also a Route via function that allows only arbitrary communication to go through Tokyo PoP. By using this, users at overseas business trips and overseas bases can also use Japanese SaaS applications.
Additional information (by-product?)
Since all traffic is inspected, it is possible to know what kind of communication was being carried out. You can easily check the access destination and risk level on the management screen of Cato.
⇒ Everything the user was doing can be confirmed by Cato.
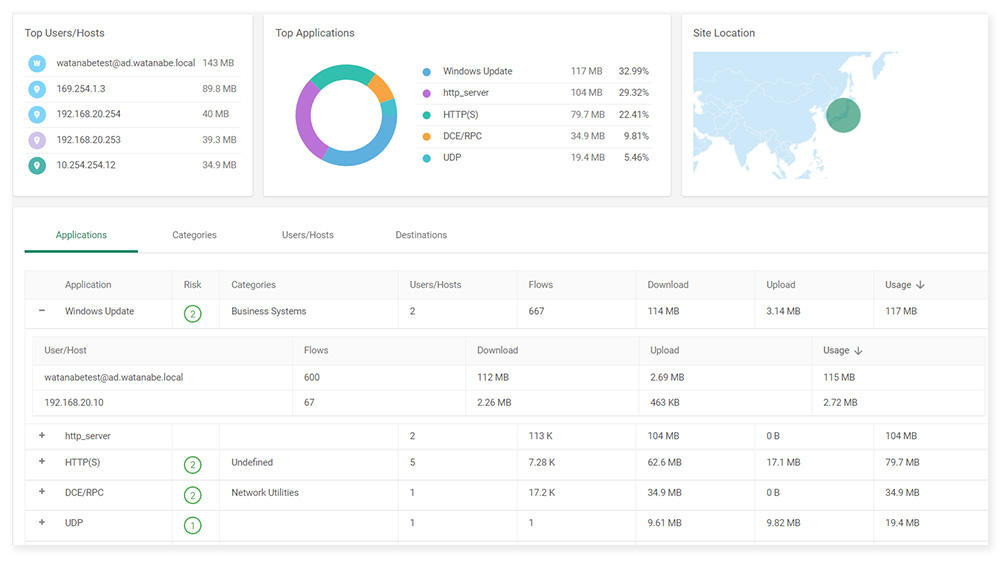
For example, as shown in the photo above, you can check who was doing what communication.
The answer to the question at the beginning is this!
- Is Cato a VPN even though it's ZTNA?
⇒ Cato VPN Client allows remote users (outside the company) to communicate safely (ZTNA) and comfortably by using VPN technology. - I don't know much about VPNs and ZTNA, but VPNs aren't that good, are they?
⇒ It's not that the VPN is bad, it's that the perimeter defense is bad.
→ It was good until now, but remote work and hybrid work have become established, so we should change to an environment where we can work anywhere. - Difference from SSL-VPN
⇒ SSL-encrypted VPN protects the content of communication from a security point of view, but if the ID and password are compromised, the target files and other information can be accessed as is. You can't control access for risky employees. In the case of CATO, communication can be controlled by elements other than IDs, so the strength of security measures can be increased.
Also, compared to the combination of SSL-VPN and point security products such as firewalls and proxies, Cato has a single-pass architecture by software in the cloud, and encryption, decryption, and optimization processing of all security services are processed at high speed. be.
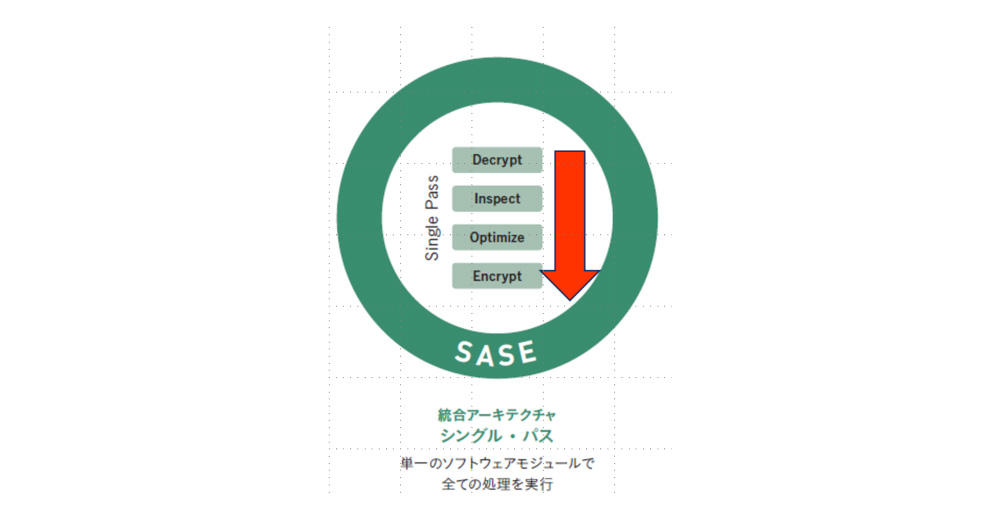
Summary
VPN is a technology, so if you choose how to use it, you can use it safely, securely and comfortably.
Using Cato Cloud for remote access also enhances security functions and establishes safe and stable communication.

About the Author: Mr.GW
A novice engineer whose hobby is traveling by bicycle. Cato's support SE is working hard every day to be of use to our customers.
Inquiry/Document request
Macnica Cato Networks
- TEL:045-476-2010
- E-mail:cato-sales@macnica.co.jp
Weekdays: 9:00-17:00


