
Cato Networks
ケイトネットワークス
Cato CASB(クラウド・アクセス・セキュリティ・ブローカー)
デジタル変革におけるクラウド利用の増加とシャドーIT対策
企業のデジタル変革、テレワークの対策などで企業のアプリケーションはクラウド環境へ移行しています。しかし、情報システム部門が把握していないクラウドサービスの数はリモートワークの普及により、さらに増大しています。
Cato SASEクラウドでは、クラウドサービスのリスクを管理するために、 最速かつ簡単に実行できるCASB(Cloud Access Security Broker)ソリューションを提供します。
「CASBは、組織のクラウド移行によって生み出される重要な可視化と制御に対応しますが、ビジネス全体で真に効果的に利用するためには、グローバルSASEプラットフォームに統合する必要があります」(Cato Networksの共同創設者兼CEOのShlomo Kramer氏)
CASBをクラウド上のCato SPACEエンジンに組み込むことで、Cato SASEクラウドの強みである、グローバルなアクセス拠点、豊富なシステム情報、クラウドのスケーラビリティや自己修復/維持機能を活用できます。Cato CASBは、短期間で導入でき、操作が簡単で、サイバーセキュリティリスクを可視化できます。
CatoCASBデモ動画(5分):使いやすいCatoSASEクラウドポータルから、すぐにCatoCASBメニューへアクセスできます。
クラウドアプリケーションリスクを管理する4つのステップ
Cato SASEクラウドはクラウドアプリケーションのデータリスクを管理するための4つのステージ(可視化、評価、防御、保護)すべてに対応しています。
1.可視化: 新しいシャドーIT ダッシュボード
Catoは、リスクの高いアプリケーションの総数、最もリスクの高いアプリケーションのリスト、それらにアクセスするユーザー数、およびリスク別の配布を含む通信の総使用量をまとめて一覧表示する、シャドウITダッシュボードを従来からのSASE管理ポータルに導入しました。
CASBのためのデータ送受信用のゲートウェイ機器やユーザエージェントの追加インストールなどは不要です。Cato CASBをお申込みいただければ、CATO SASEクラウドの管理メニューより、ボタンをONにするだけで、Cato CASBの機能がすぐにご利用できます。
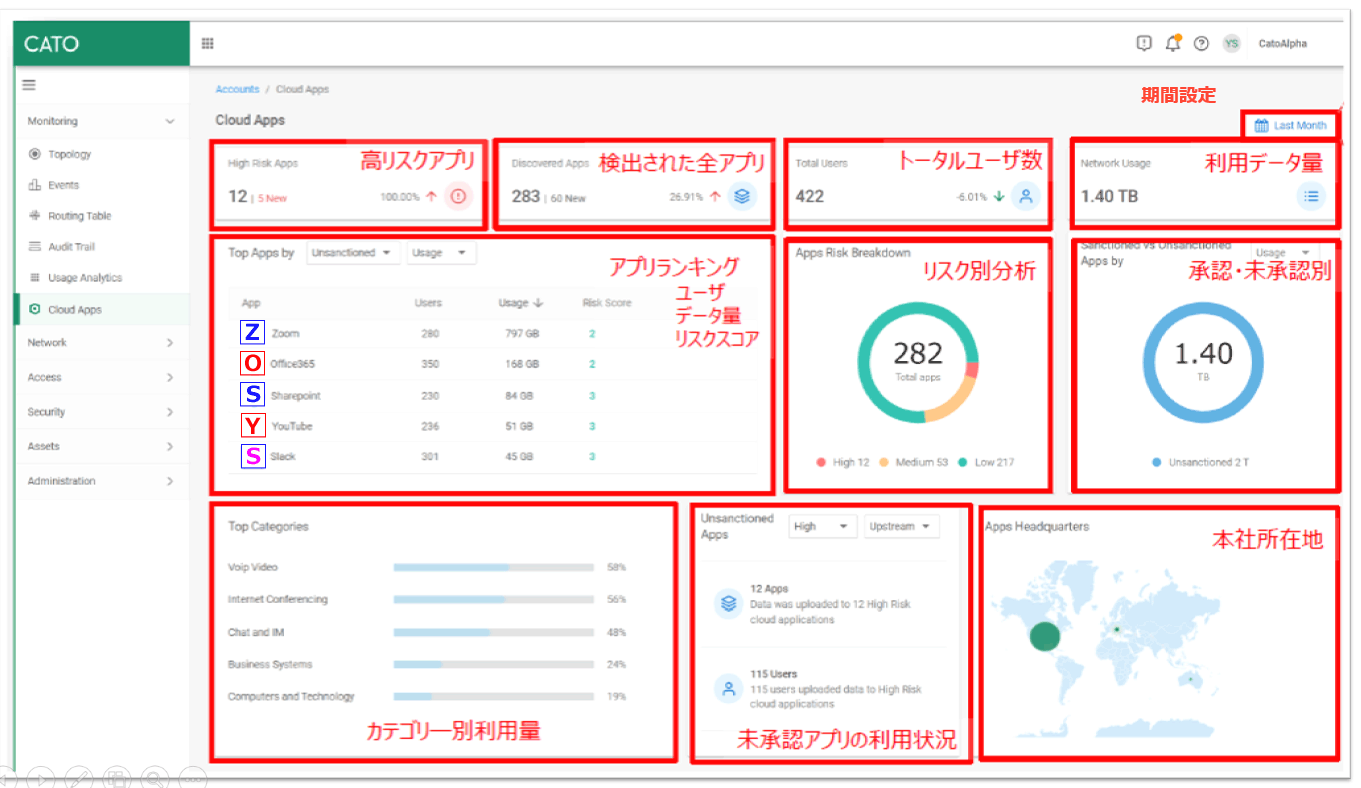
シャドウIT ダッシュボード:企業は許可された(Sanction)アプリケーションの状況と未許可(Unsanction)のアプリケーションの状況のスナップショットを取得できます。
2.評価: Cato アプリケーション信頼性エンジン (ACE)
未許可のアプリケーションを特定した IT リーダーは、ブロック、制御、または許可すべきかを判断する前に、リスクを評価する必要があります。
Cato CASBは、複数のソースからのデータ収集を自動化し、各アプリケーションの迅速かつ正確な評価を可能にする、独自のアプリケーション信頼性エンジン (ACE - Application Credibility Evaluator)を構築しました。包括的な分析 (一般的な企業情報、コンプライアンス対応情報、セキュリティ対応情報) を対象に、3つの指標が集約されます。
ネットワーク上に表示される実際のアプリケーションを分析するのは、Catoの膨大なデータレイクフローメタデータに対して動作する機械学習アルゴリズムです。現在、Catoの規制コンプライアンス検証には、HIPAA、PCI、およびSOC 1-3が含まれています。セキュリティ機能の検証には、多要素認証、保管時のデータの暗号化、および SSOが含まれます。
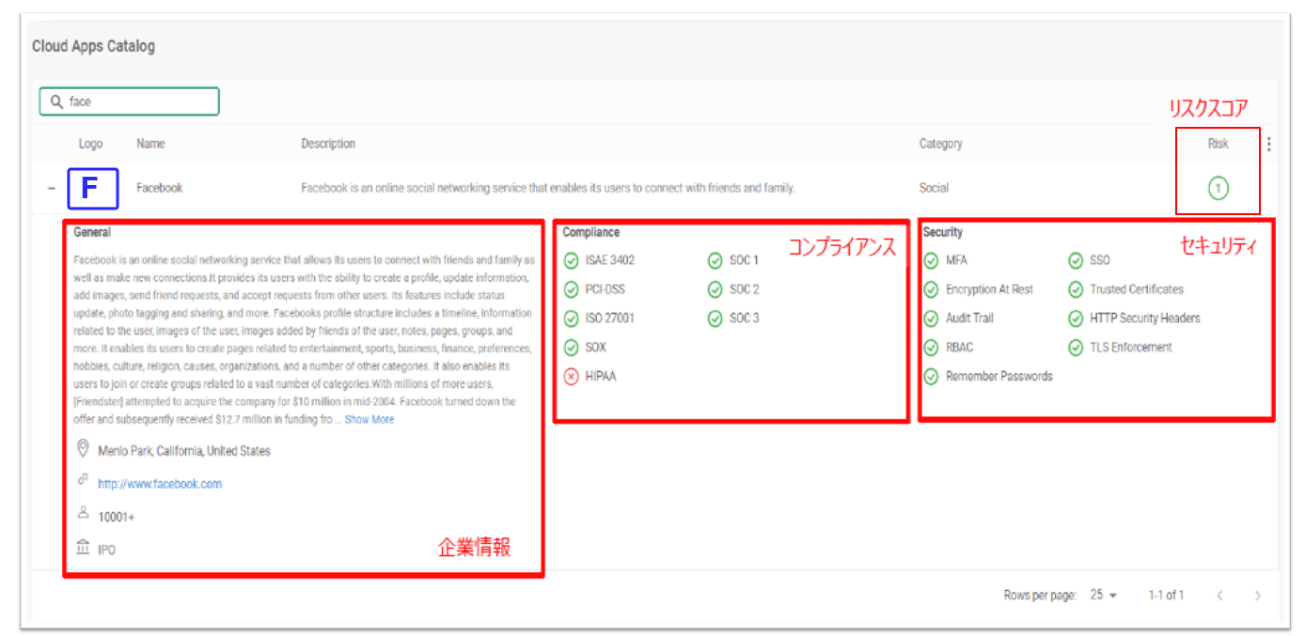
クラウドアプリケーションカタログ:CatoのACEのデータマイニングを使用し、すべてのアプリケーションに対して企業情報、コンプライアンス対応情報、セキュリティ対応情報を常時自動更新して提供します。
3.制御: Cato CASB ルールでアクセスポリシーを定義します
ネットワーク上で不正なアプリケーションを発見し、リスクを評価した後、ITリーダーは、対応方法を決定する必要があります。Cato CASBを使用すると、アプリケーション上できめ細かいアクセスを得られます。ルールを使用すると、一致条件、ルールが適用された場合に実行する指定されたアクション、関連する重大度レベル、およびアラートまたはイベントを生成するかどうかを定義できます。
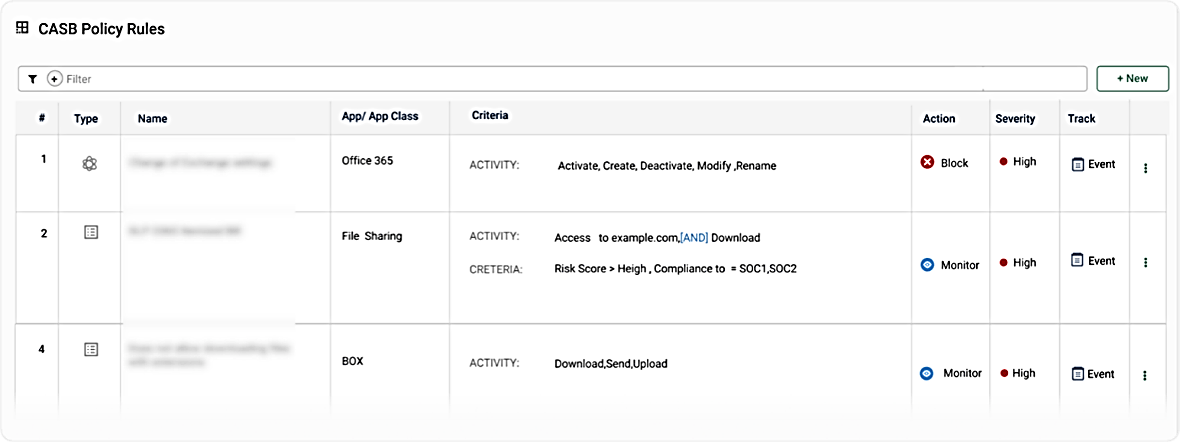
Cato CASB ポリシールールビュー:企業全体にわたるアプリケーションのきめ細かな制御が可能
4.防御: Cato は脅威と侵害を検出し、ブロックします。
最後の段階は、SaaS の使用を確実に保護することです。Cato SASEクラウドの持つセキュリティツールの統合で実現できます。
すべての SaaSトラフィックは、次世代ファイヤーウォール(NGFW)、セキュリティウェブゲートウェイ(SWG)、侵入防止システム*(IPS)、および 次世代アンチマルウェア*(NGAM)の複数のセキュリティツールによって処理されます。これらのツールを組み合わせることで、さまざまな脅威から包括的な保護を提供します。 *オプション
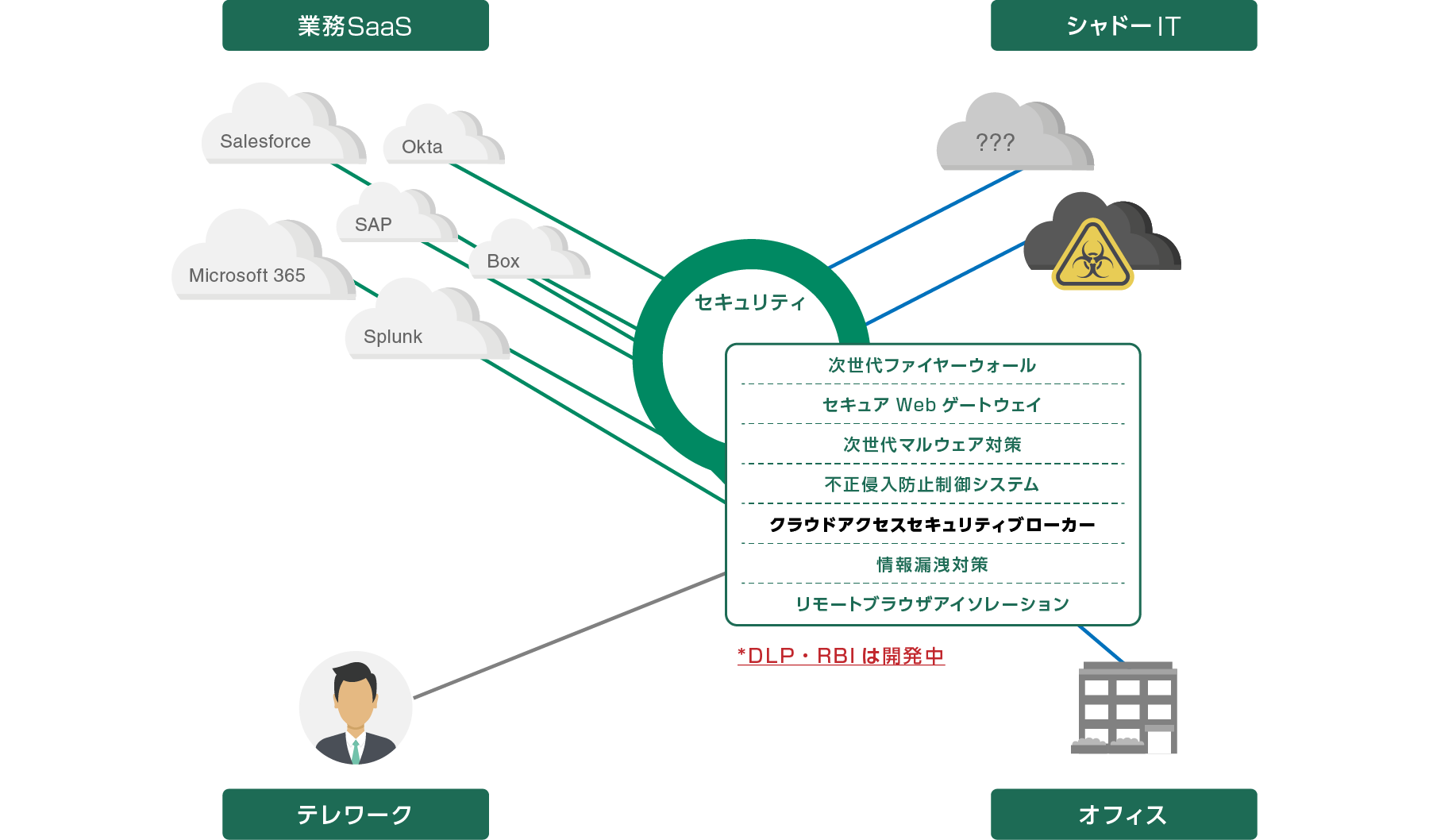
Cato CASBのメリット
Cato CASBを使用すると、真のSASEプラットフォームのメリットをクラウドアプリケーションリスク管理の対策に取り入れることができます。従来のスタンドアロン型のCASBソリューションでは、大規模な導入計画が必要で、数ヶ月単位で構築時間がかかります。一方、Cato CASBは、SASEの機能に組み込まれているため、データ取得用のサーバや機器、接続設定は不要で、クラウドアプリケーションへのアクセスを完全に可視化し、制御する機能をすぐに利用できます。
Cato CASBはCato SASE クラウドの一部として、世界中70ヵ所以上のPoP経由で、データセンターやモバイルといった拠点やユーザーがどんな場所からでも利用可能です。SDP/ZTNA機能も実装しているため、テレワーク社員の自宅からのシャドーIT対策も同時に可能になります。
この広範囲なサービス展開により、海外拠点やグループ企業でクラウドアプリケーションにアクセスする場合でも、すべてのクラウドアクセスに対して企業ポリシーを一元管理できます。レガシーCASBソリューションの対象範囲は、場所や利用可能な機能によって実装が異なります。
そして、Cato CASBは、Cato SASEクラウドの多層脅威防御のフルパワーを活用できます。クラウドベースのファイルアクセスは、Catoの高度な次世代マルウェア対策*およびIPS*(侵入防止システム)エンジンによって検査されます。場所や情報資源へのアクセス制御は、Cato 次世代ファイヤーウォール(NGFW)およびセキュリティウェブゲートウェイ(SWG)を通じて制限されています。従来のCASBでは、これらのコンポーネントはすべて別ベンダーとの組み合わせ、機能追加が必要とされ、それぞれの接続作業と検証、工事が必要になります。 *オプション
| スタンドアローンCASB | Cato 内蔵 CASB | |
| 構築・導入 |
長期かつ複雑 CASBプロジェクトでは、すべてのユースケースを確実にカバーするために、ネットワークマッピングと計画が必要。 |
高速かつシンプル CatoのCASBを有効にするために、計画、ネットワークの変更、展開、構成は必要ありません。CASB機能を有効にすると、追加の学習期間は不要で、すぐに実施できる。 |
| 検査用のビッグデータの範囲 |
部分的 通常、通信履歴のログなどの内部情報のみ。 |
すべて 完全なSASEサービスの一部として、様々なSaaSのデータや、すべてのプロトコルおよびネットワークセキュリティ機能から豊富な情報を得る。 |
| アプリケーションの対象範囲 |
狹い 通常、SaaSがメインとなり、IaaSは限定的。 |
広い SaaS、IaaS、WAN の利用をすべて対象に。 |
| インラインモード実施での粒度 |
低い インラインモードでの粒度は粗く、より高い粒度の適用は、アウト・オブ・バンドモードで API を使用する必要があり、リアルタイムの防御は不可能。 |
高い インライン モードでありながら、非常に細かいルールを利用できる。 |
お問い合わせ・資料請求
株式会社マクニカ Cato Networks 担当
- TEL:045-476-2010
- E-mail:cato-sales@macnica.co.jp
平日 9:00~17:00


