
Cato Networks
ケイトネットワークス
CASB(キャスビー)とは?定義や機能、メリット、選び方のポイントを解説

MicrosoftのOne DriveやDropboxのようなクラウドサービスはもはや企業活動に欠かせないものとなりました。しかし、その裏にはリスクも隠れています。
例えば、許可していないクラウドサービスを従業員が勝手に使うなどです。これらを放置しておくと、情報漏洩や企業信頼の失墜にもつながることもあります。
そこでこの記事ではクラウド領域のセキュリティ対策において重要視されるCASB(Cloud Access Security Broker 読み方:キャスビー)について分かりやすくご紹介します。複数のクラウドサービスもCASBで一元管理でき、業務効率を損ねることなくセキュリティを強化できます。CASBのメリットや、導入方法についても合わせてご紹介しますので、ぜひご覧ください。
CASBとは?
CASBとは クラウドサービスのセキュリティを一括管理するソリューション
CASBとは、2012年、米国Gartner社(ガートナー)が提唱したセキュリティ対策の概念です。企業とクラウドサービスの間にCASBを設置することで、クラウドサービスの利用状況を可視化し、アップロードの監視・制御も可能になります。 1つのCASBで複数のクラウドサービスを監視できるので、一貫性のあるセキュリティポリシーを設定でき、運用・管理も効率化されます。最近ではSASE (Secure Access Service Edge、サシー)に組み込まれることも増えてきました。SASEとは、CASB、FWaaSのようなセキュリティサービスと、SD-WANのようなネットワークサービスを1つにまとめた、ゼロトラストの境界情報防御のネットワークセキュリティアーキテクチャです。 そんなCASBは、ソフトの要件として4つの機能が提唱されています。
【CASBの4機能】
- 可視化
- データセキュリティ
- 脅威防御
- コンプライアンス
上から順番に詳しく解説します。
1. 可視化
組織で使うクラウドサービスの利用状況を見える化する機能です。アクセス状況やファイルのアップロード・ダウンロードも一目瞭然になります。未許可のクラウドサービスも監視し、リスクの高いクラウドアプリケーションを解析し、情報流出を防止します。
2. データセキュリティ
CASBはデータ中心のセキュリティを施します。ファイル内のキーワード検索といった機密情報を識別する方法をいくつも用意し、精度の高い情報漏洩対策を施します。
また、自社内のデータだけでなく、クラウドに保存したデータに暗号化を施し安全性を高める機能もあります。データの種類や重要度ごとにアクセス制限をかけるなど、細かいセキュリティ対策が可能です。
3. 脅威防御
企業として許可していない端末や、ユーザー、ソフトウェアなどがクラウドにアクセスすることを防止し、脅威から防御します。マルウェアの検出・隔離にも対応し、重要情報の流出を防ぎます。
4. コンプライアンス
設定したセキュリティポリシーをもとに、クラウドサービスを監視・制御します。セキュリティ担当者が禁止した情報を含むファイルのアップロードなどを禁止し、コンプライアンスを遵守します。
【CASBで検知できる重要情報(一例)】
- クレジットカード番号
- マイナンバー
- 特定の拡張子を持つファイル など
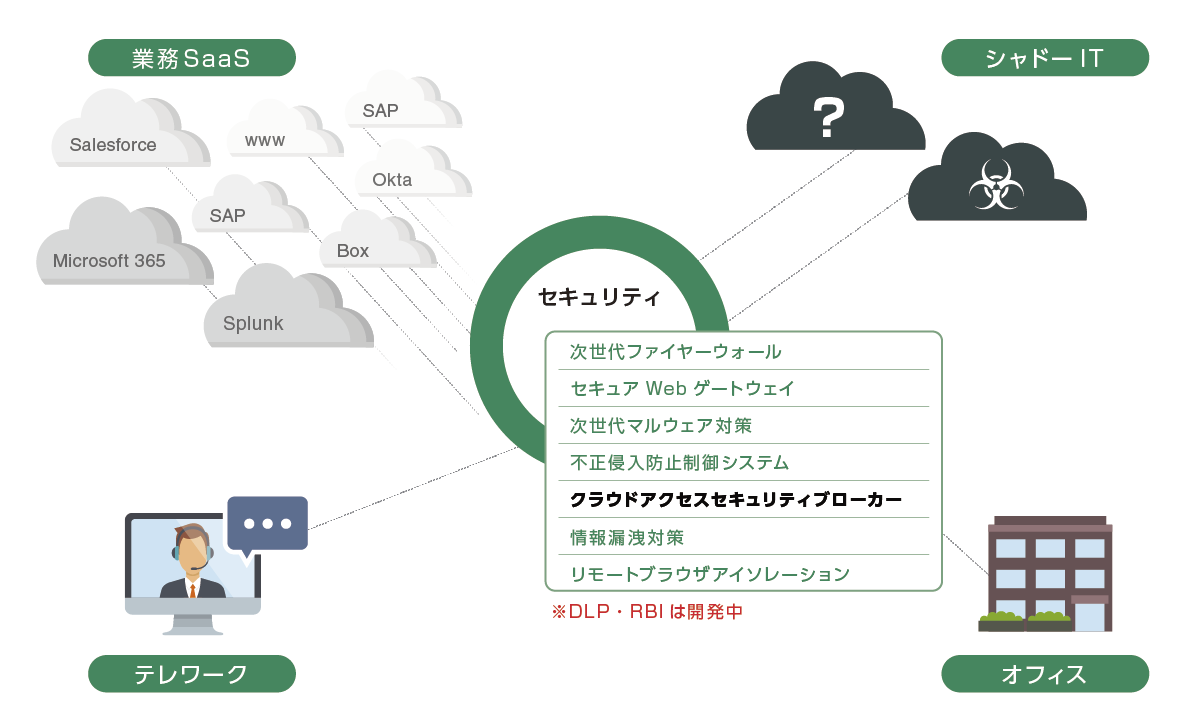
上記のような機能を搭載するCASBが普及してきた背景には、未許可のクラウドサービスを従業員が勝手に使用する、シャドーITが増加しているためです。
Shadow ITとSanctioned(認可された)IT
Shadow IT(シャドーIT)とは、組織内で使われるシステムや端末、ソフトウェアなどが、従業員や各部門の独自判断によって使用されていて、経営者やセキュリティ担当者がそれを把握できていない状況を指します。 Shadow ITの対義語であるSanctioned IT(サンクションIT)は、企業が許可したものを使用している状況です。 ポイントとして、シャドーITを行っている従業員は悪意を持たず、業務効率化のために許可されていないIT機器やクラウドサービスを活用していることが多い点です。
【シャドーITの事例】
- 個人のメールアドレスで企業とデータをやり取りする
- 許可していないクラウドストレージに勝手にファイルをアップロードする
- 個人のクラウド環境を業務に使用する
しかし、従業員に悪意はないとしてもシャドーITには大きなリスクが伴います。
短期的には、データの流出やマルウェアの感染など、重大な情報流出を引き起こす可能性があります。
中長期的に見れば、会社の機密情報が従業員によって個人的に管理されている状態となるため、従業員が退職時にデータを持ちだす可能性や、個人環境のセキュリティ事故による情報漏洩、コンプライアンスが遵守できていないとして、企業の信頼失墜につながることもあります。
そこで便利なのがCASBです。
CASB導入のメリットと注意点
ここではCASBを導入するメリットと、注意点について解説します。
CASBを導入する3つのメリット
1つ目は、クラウドサービスで業務効率を向上しながら、セキュリティを高められる点です。
CASBがクラウドサービスをリアルタイムで監視し、不正を検知します。複数のクラウドサービスに契約していてもCASBは1つでよく、セキュリティポリシーも統一でき、運用・管理も楽になるでしょう。
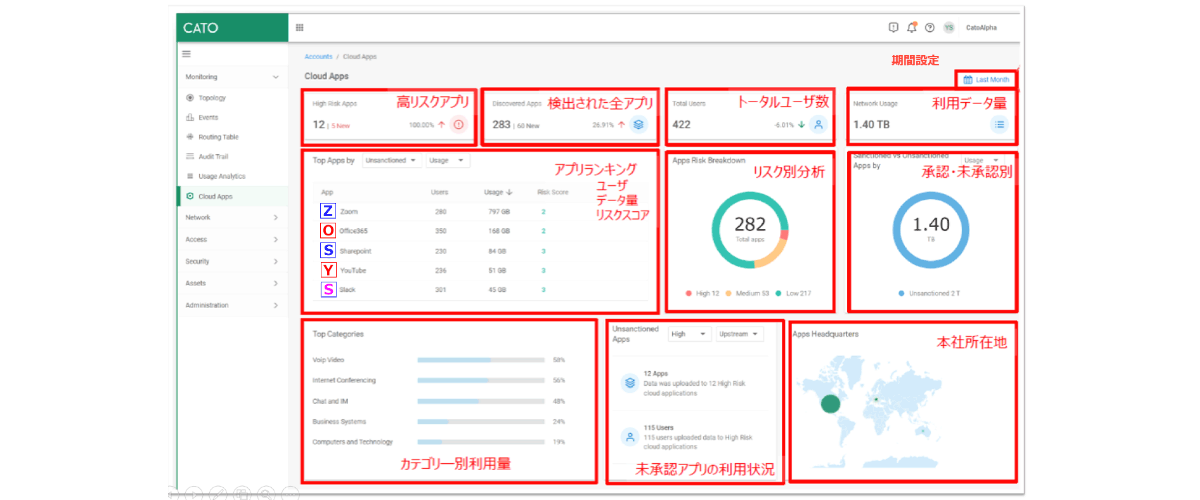
2つ目のメリットは、分析結果を可視化できる点です。
クラウドサービスへのアクセス状況などを分析し、ダッシュボードでわかりやすく確認できます。CASB管理画面で全体の利用状況を確認できるため、セキュリティ違反や不正行為を発見しやすくなるだけでなく、従業員が好んで利用しているクラウドサービスについても把握することが可能です。
3つ目は、リモートワーク導入に適している点です。
リモートワークには、クラウドサービスが欠かせません。CASBはリモートワーク時も強固なセキュリティ対策を施せます。端末に直接CASBエージェントを導入することも可能であるため、自宅からのローカルブレークアウトもセキュアに守ることが可能です。
CASBの注意点
CASB製品の中には、リアルタイムの監視・制御ができない製品もあります。加えて、クラウドサービス側で情報流出などの事故があった場合は、CASBだけでは対策できないことにご注意ください。また、CASBだけで全てのセキュリティ対策を行えるわけでなく、外部からのサイバー攻撃などの対策もあわせて考えましょう。
CASBを導入するだけでなく、シャドー ITが横行しないよう社員への教育も重要です。
代表的なCASBの導入方式
CASBには3種類の導入構成があり、それぞれで監視できる領域や得意分野が異なります。
API型
自社で契約しているクラウドサービスに、APIでCASBを連携する導入構成です。CASBと連携させたクラウドサービスの利用状況や、アクセス状況などを監視します。契約していないクラウドサービスの監視はできないこと、API連携に対応していないクラウドサービスには使用できないことに注意しましょう。重要情報がそれほど多くなく、クラウドにアップロードしたものだけを監視できれば良い場合などは、API連携構成が採用されます。
インライン型
インライン型は、自社の端末からクラウドサービスに接続するまでの通信経路内にCASBを配置する導入構成です。クラウドサービスにアップロードする前に通信を遮断するには、この構成が採用されます。自社で契約していないシャドウの利用状況まで監視でき、重要情報が多く強固なセキュリティ対策を施したい企業におすすめです。
ログ分析型
企業で設置しているゲートウェイ端末を介する通信を監視する導入構成です。ファイルの中身まではチェックできないため、ある程度シャドーITを許容し、危険だと思われるクラウドサービスの利用だけ制限したい場合に適しています。ログ分析型は、アクセス先のURLをベースに通信を監視します。可視化機能や脅威防御機能でリスクを検知したときは、ゲートウェイ端末と連携して、該当するURLへのアクセスを禁止する形でセキュリティ対策をとります。
CASB製品を選定する際のポイント
CASB製品を失敗せずに選ぶ6ポイントをご紹介します。導入にはコストがかかりますので、以下を参考にご検討ください。
①導入要件の整理・明確化
CASB製品は数多く開発されています。
全製品の機能や価格を比較し、1つ1つ導入試験を行うと膨大な時間と労力がかかります。速やかに導入を進めるため、優先事項を整理しておきましょう。必須条件、希望条件を洗い出し、それぞれに優先順位をつけておくのがおすすめです。
②自社で運用するのか他社にアウトソースするのか
CASBを導入したあと、自社で運用する方法と、他社に運用を依頼する方法があります。自社で運用する場合には、定期的にセキュリティポリシーを見直したり、クラウドサービスの利用状況を定期的に監視したりする必要があります。自社運用は手間に見えますが、メリットも多くあります。分かりやすい管理画面のCASB製品を選べば操作もしやすく、自社内で素早い対応を取れるようになります。
③導入構成について事前に検討されているか
CASBには3つの構成があり、それぞれで得意分野が異なります。どのサービスについて、何を目的に、どこまで制御したいかを考え、3構成のどれを採用するか検討しましょう。また、CASB製品1つでは企業のセキュリティ対策は完璧と言えません。他のセキュリティソリューションと共存させていくことになります。導入を検討しているCASBが、企業で導入している既存のセキュリティソリューションやSASEと共存できるか確認しておきましょう。加えて、CASBを導入することにより、従業員に利用方法の周知や教育が必要かも整理しておくと安心です。
④導入に手がかからない
CASBは製品ごとに導入が簡単なものと、そうでないものがあります。一部のCASBは、導入時にデータ取得用のサーバーを設置したり、ネットワーク構成を変えたり、大規模な導入計画が必要になることもあります。一方クラウドで動作するCASBは、比較的シンプルに短期間で導入できます。
他にも、機能を段階的に実装できる製品や、導入サポートもついているCASBを選ぶと安心です。
⑤クラウドでスケールアウトできる
将来、企業で使用するモバイル端末やユーザー数が増加したとき、クラウド側でスケールアウトできるCASB製品を選ぶと対応が楽になります。インライン型のCASB製品は企業とクラウドサービスの通信経路内にCASBを配置するため、ネットワークに遅延が発生したり、CASB製品側でトラブルがあった場合に通信が遮断されたりすることもあります。リモートワークによって、使用端末数が一気に増加する可能性もあります。クラウドでスケールアウトできるCASBを選ぶのがおすすめです。
⑥防御をリアルタイムでできる
従来のCASBはログを監視・分析してシャドーITを発見するため、リアルタイムの通信制御ができないものが主流でした。しかし近年ではリアルタイムの制御が可能なCASBが登場し、アップロードが禁止されているファイルを発見した際には、途中でアップロードを中断するものもあります。データ流出を予防したい場合には、リアルタイムの制御が可能なCASBを選びましょう。
おすすめのCASBサービス
マクニカがおすすめするCASB製品「Cato CASB」をご紹介します。
「Cato CASB」はSASEである「Cato SASEクラウド」に含まれる機能です。
Cato CASBはクラウドで動作するCASB製品で、セキュリティ担当者と従業員のどちらにとっても使いやすいのが特徴です。SD-WANとグローバルバックボーン上のPoPによる分散環境で、通信の最適化が実行されるため、クラウドへのアクセススピードが遅くなることはありません。
管理画面「シャドーITダッシュボード」では、クラウドサービスのアクセス状況だけでなく、リスク別分析や未許可のアプリケーションを利用していないか一覧で確認できます。
独自開発の「Cato アプリケーション信頼性エンジン」を搭載し、未許可のアプリケーションがあれば、リスクを自動で判断してセキュリティ担当者の業務量を減らします。
すべてクラウドで動作するため、リモートワークにも対応。モバイル端末の利用も監視でき、リモートワーク中のシャドーITを防止します。
構築が簡単で、導入費用を抑えられる点も選ばれるポイントです。Cato CASBの導入には、データ取得用のサーバーやネットワークの変更などもありません。すぐに利用開始できます。
さらに詳しい機能やCato CASBのデモ動画は、こちらからご覧ください。
まとめ
リモートワークが普及する昨今、CASBはクラウドサービスを安全に利用するために欠かせないソリューションです。クラウドサービスの利用状況を監視し、不正が見つかれば警告・遮断なども行えます。従業員の業務効率を下げないままセキュリティ対策を向上したい方は、ぜひCASBをご活用ください。
また、シャドーITを予防するには従業員への周知教育も重要ですが、それだけでは0になりません。万一の情報流出、企業の信頼失墜につながるまえに、セキュリティ対策を施すことが重要です。
マクニカでは世界でも数少ない、Cato Networks社のDistinguished Support Provider認定を取得しております。SASEに関する導入コンサルティングや、認定EXPERTによるセミナー、SASE導入ご相談会も開催しております。お困りのことがあれば、お気軽にご相談ください。

株式会社マクニカ
ネットワークス カンパニー 第3営業統括部 第2営業部 第4課 SASE EXPERT
鈴木富士雄
1989年株式会社マクニカ入社、米国光ファイバー製品を担当。インターネット商用解禁とともに米国のサーバーの利用を開始する。その後情報システム部門にてマクニカwebmasterとしてWebサイト企画運営を行う。2005年よりクラウドサービスの営業、2010年よりSplunk製品担当としてCSIRTの啓蒙を行う。2019年よりCato Networks製品マーケティング担当
お問い合わせ・資料請求
株式会社マクニカ Cato Networks 担当
- TEL:045-476-2010
- E-mail:cato-sales@macnica.co.jp
平日 9:00~17:00


