product
- Line up
- Network Security: Trellix (formerly FireEye) Network Security
- Network Security: Trellix (formerly McAfee) Advanced Threat Defense
- Network Security: Trellix (formerly McAfee) Network Security Platform
- Endpoint: Trellix (formerly FireEye) HX
- Endpoint: Trellix (formerly McAfee) Mvision
- Data Protection: Trellix Data Security
- Email Security: Trellix (formerly FireEye) Server Edition
- Email Security: Trellix Cloud Edition
- Security Operations: Trellix (formerly FireEye) Helix
- Security Operations: Trellix (formerly McAfee) SIEM (Security Information and Event Management)
- Enhanced cloud governance: Trellix (formerly FireEye) Cloudvisory
- File Security: Trellix (formerly FireEye) Malware File Storage Scanning
- Integrated Management Solution: Trellix (formerly FireEye) Central Management
- NDR Solution: Network Investigator (NI) / Packet Capture (PX)
- Cloud-based File Threat Protection: Trellix IVX Cloud
Specifications/Technical Information
- Trellix (formerly FireEye) Technical Information
- Trellix (formerly FireEye) Specifications
- Network Security: Trellix (formerly FireEye) Network Security Technical Information
- Network Security: Trellix (formerly McAfee) Network Security Platform Technical Information
- Network Security: Trellix (formerly McAfee) Network Security Platform Specifications
- Network Security: Trellix (formerly McAfee) Advanced Threat Defense Technical Information
- Network Security: Trellix (formerly McAfee) Advanced Threat Defense Specification
- Email Security: Trellix (formerly FireEye) Server Edition EX Series Technical Information
- Email Security: Trellix (formerly FireEye) Server Edition EX Series Specifications
- Integrated Management Solution: Trellix (formerly FireEye) Central Management (CM) Series Specifications
- Security Operations: Trellix (formerly McAfee) SIEM (Security Information and Event Management) Technical Information

Trellix
Trellix
In recent years, cyber attacks have been increasing, and their methods are becoming more sophisticated. In order to respond to these threats, a security monitoring system called "XDR" is required, which improves visibility and detection by cross-analyzing information from multiple sensors such as networks, endpoints, and clouds.
As a first step toward realizing XDR, we are proposing a variety of solutions that utilize XDR's core platform, Trellix Helix.
Let's strengthen our defenses against threats that are difficult to detect and deal with using a single product together with Trellix, which offers a wide range of security products!
- "Helix × NX: Discover invisible threats! Network strengthening solution"
- "Strengthening the security level of Helix x HX terminals x Reducing operational burden"
- "EPP Enhancement Proposal for Helix x ENS x TIE ENS Users"
- "Helix x ETP x MS365: Strengthening measures against attacks targeting authentication information"
For more information on each solution, please contact us at the bottom of the page.
Helix × NX
Discover invisible threats! Network strengthening solution
- NX × Helix provides comprehensive visibility into threats, from advanced to invisible
- Multiple alerts are consolidated into one, making it clear which threats need to be investigated
- If EDR is implemented, it can be used in conjunction with this solution to check threats to devices in a series of flows.
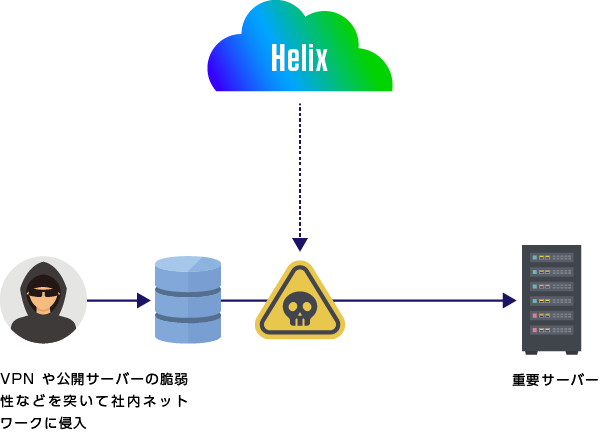
※NX:https://www.macnica.co.jp/business/security/manufacturers/trellix/nx.html
Helix × HX
Strengthening the security level of terminals × Reducing operational burden
- Helix-specific HX detection rules
- Windows event logs are also analyzed.
- Visualize the whole picture of alerts
- Detects low-risk threats on their own
- Quantifying the risk level for each threat
- Provides a series of steps required for investigation
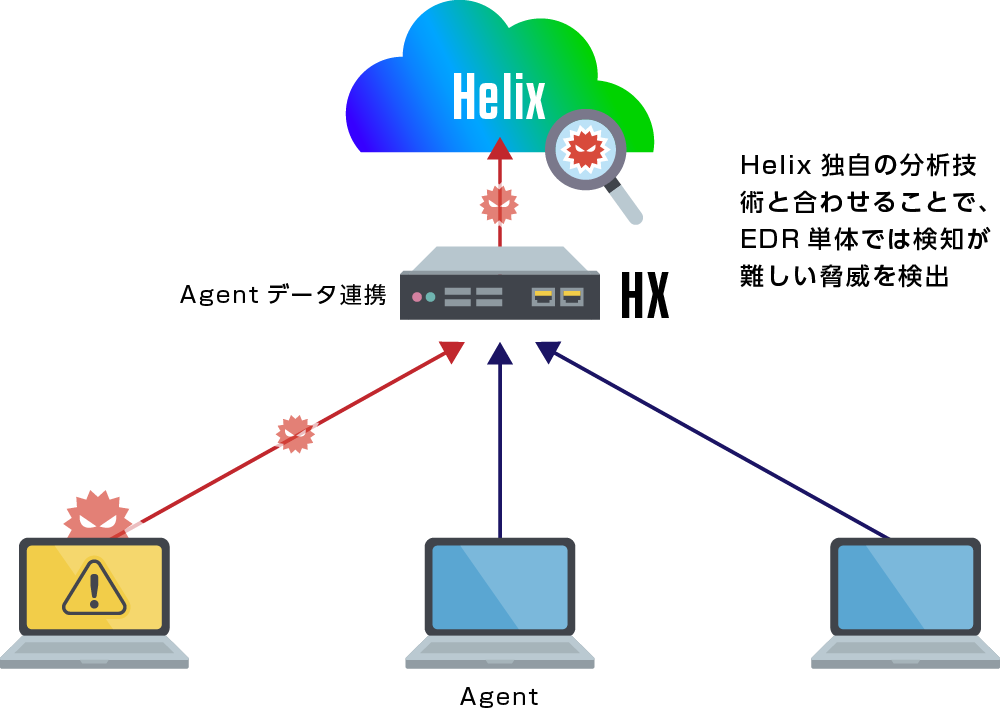
※HX:https://www.macnica.co.jp/business/security/manufacturers/trellix/endpoint.html
Helix × ENS × TIE
EPP Enhancement Proposal for ENS Implemented Users
- Strengthening "detection" and "investigation"
- "Response" that TIE EDR does not provide
- "Reduce costs" related to implementation
- Reduces work hours
- Introducing the core part of Trellix XDR, "Helix"
- Log collection from other products is also possible
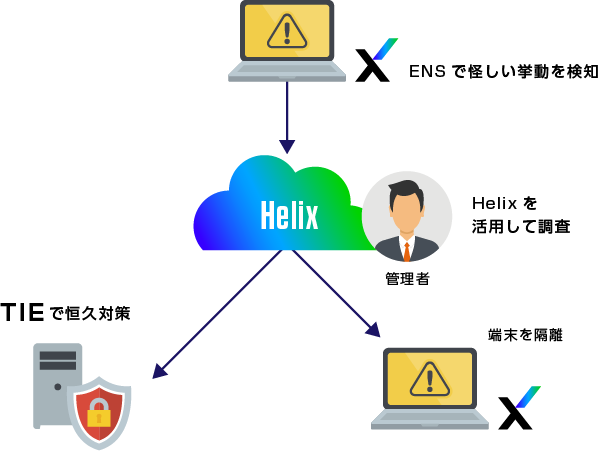
※ENS:https://www.macnica.co.jp/business/security/manufacturers/trellix/tes.html
TIE:https://www.trellix.com/products/threat-intelligence-exchange/
Helix × ETP × MS365
Proposal for strengthening measures against attacks targeting authentication information
- Abundant functions allow you to take measures against phishing emails and spoofing attacks
- Able to detect malicious behavior associated with activities that are difficult to detect using email security products alone
- Aggregate and display multiple related alerts
- Centralized management of alerts for multiple products
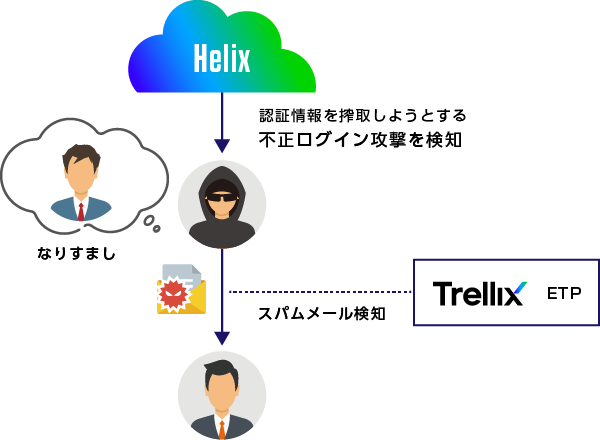
※ETP:https://www.macnica.co.jp/business/security/manufacturers/trellix/etp.html
Inquiry/Document request
In charge of Macnica Trellix Co., Ltd.
- TEL:045-476-2010
Weekdays: 9:00-17:00

