product
- Line up
- Network Security: Trellix (formerly FireEye) Network Security
- Network Security: Trellix (formerly McAfee) Advanced Threat Defense
- Network Security: Trellix (formerly McAfee) Network Security Platform
- Endpoint: Trellix (formerly FireEye) HX
- Endpoint: Trellix (formerly McAfee) Mvision
- Data Protection: Trellix Data Security
- Email Security: Trellix (formerly FireEye) Server Edition
- Email Security: Trellix Cloud Edition
- Security Operations: Trellix (formerly FireEye) Helix
- Security Operations: Trellix (formerly McAfee) SIEM (Security Information and Event Management)
- Enhanced cloud governance: Trellix (formerly FireEye) Cloudvisory
- File Security: Trellix (formerly FireEye) Malware File Storage Scanning
- Integrated Management Solution: Trellix (formerly FireEye) Central Management
- NDR Solution: Network Investigator (NI) / Packet Capture (PX)
- Cloud-based File Threat Protection: Trellix IVX Cloud
Specifications/Technical Information
- Trellix (formerly FireEye) Technical Information
- Trellix (formerly FireEye) Specifications
- Network Security: Trellix (formerly FireEye) Network Security Technical Information
- Network Security: Trellix (formerly McAfee) Network Security Platform Technical Information
- Network Security: Trellix (formerly McAfee) Network Security Platform Specifications
- Network Security: Trellix (formerly McAfee) Advanced Threat Defense Technical Information
- Network Security: Trellix (formerly McAfee) Advanced Threat Defense Specification
- Email Security: Trellix (formerly FireEye) Server Edition EX Series Technical Information
- Email Security: Trellix (formerly FireEye) Server Edition EX Series Specifications
- Integrated Management Solution: Trellix (formerly FireEye) Central Management (CM) Series Specifications
- Security Operations: Trellix (formerly McAfee) SIEM (Security Information and Event Management) Technical Information

Trellix
Trellix
Cloud-based security operation platform “Trellix (formerly FireEye) Helix”
As corporate security measures shift from "product introduction" to "operation", issues related to security operation are becoming apparent.
Helix uses Trellix (formerly FireEye) proprietary threat intelligence, cloud service monitoring, and automation technology to comprehensively solve multiple issues facing security operators with a single solution. increase.
Issues and Ideals in Security Operations
- Threats are becoming more sophisticated and increasing year by year
- Not enough security personnel
- Inability to visualize threats in the cloud environment
- Spending time on simple/repetitive tasks

- Next-generation SIEM
- Ability to deal with sophisticated and increasing threats with fewer resources
- cloud security
- Achieving both the security of the cloud environment and the convenience of operations
- security orchestration
- Operators can concentrate on the work that should be done by “people”
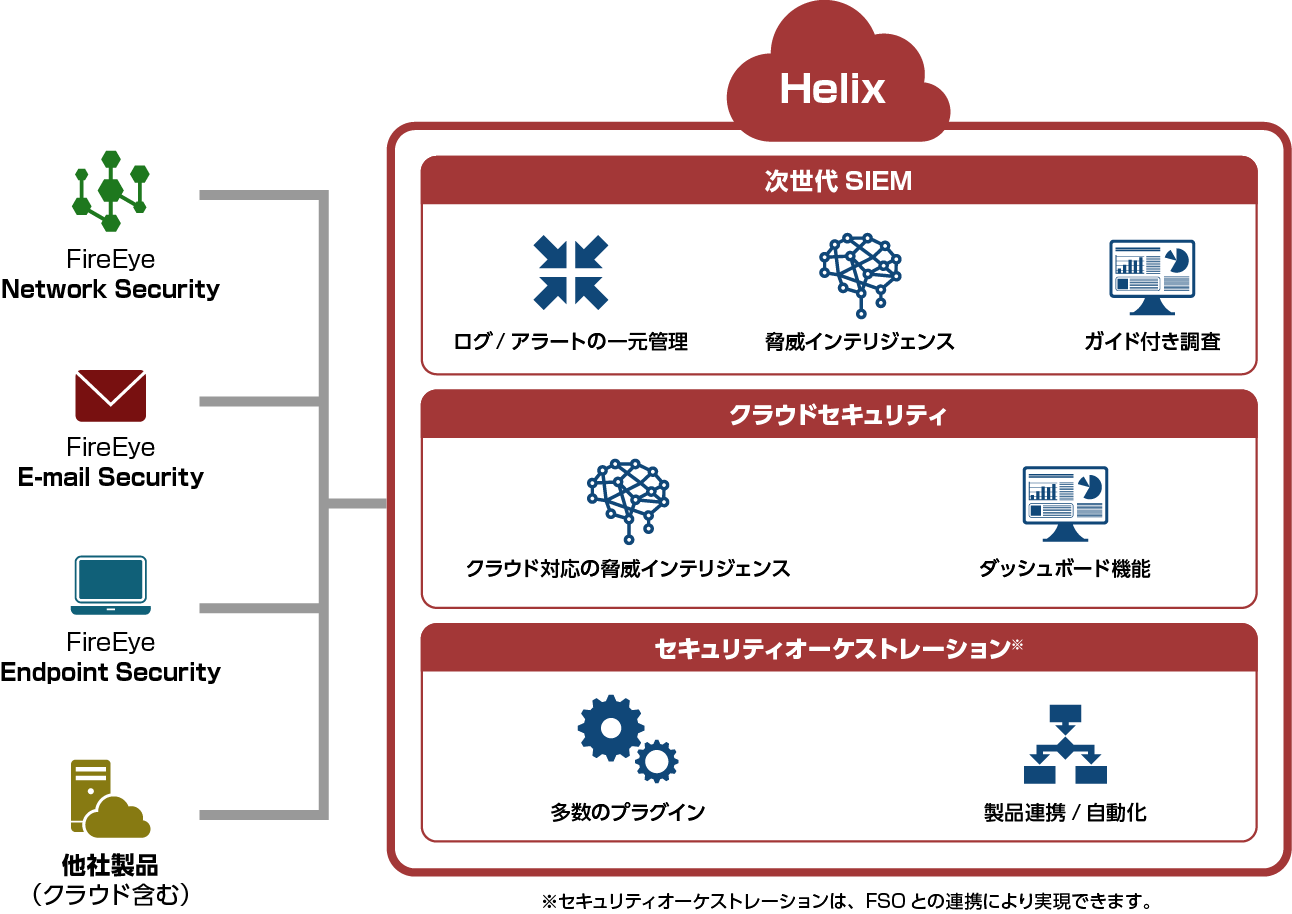
Helix Feature Overview
Helix has many functions that support the decision-making of operators at each step from alert occurrence to response.
Next-generation SIEM
Log/alert collection
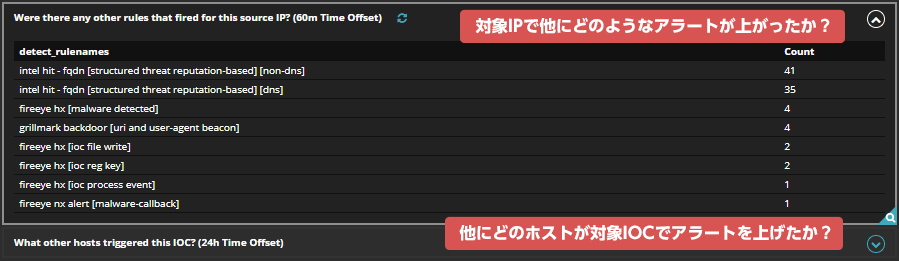
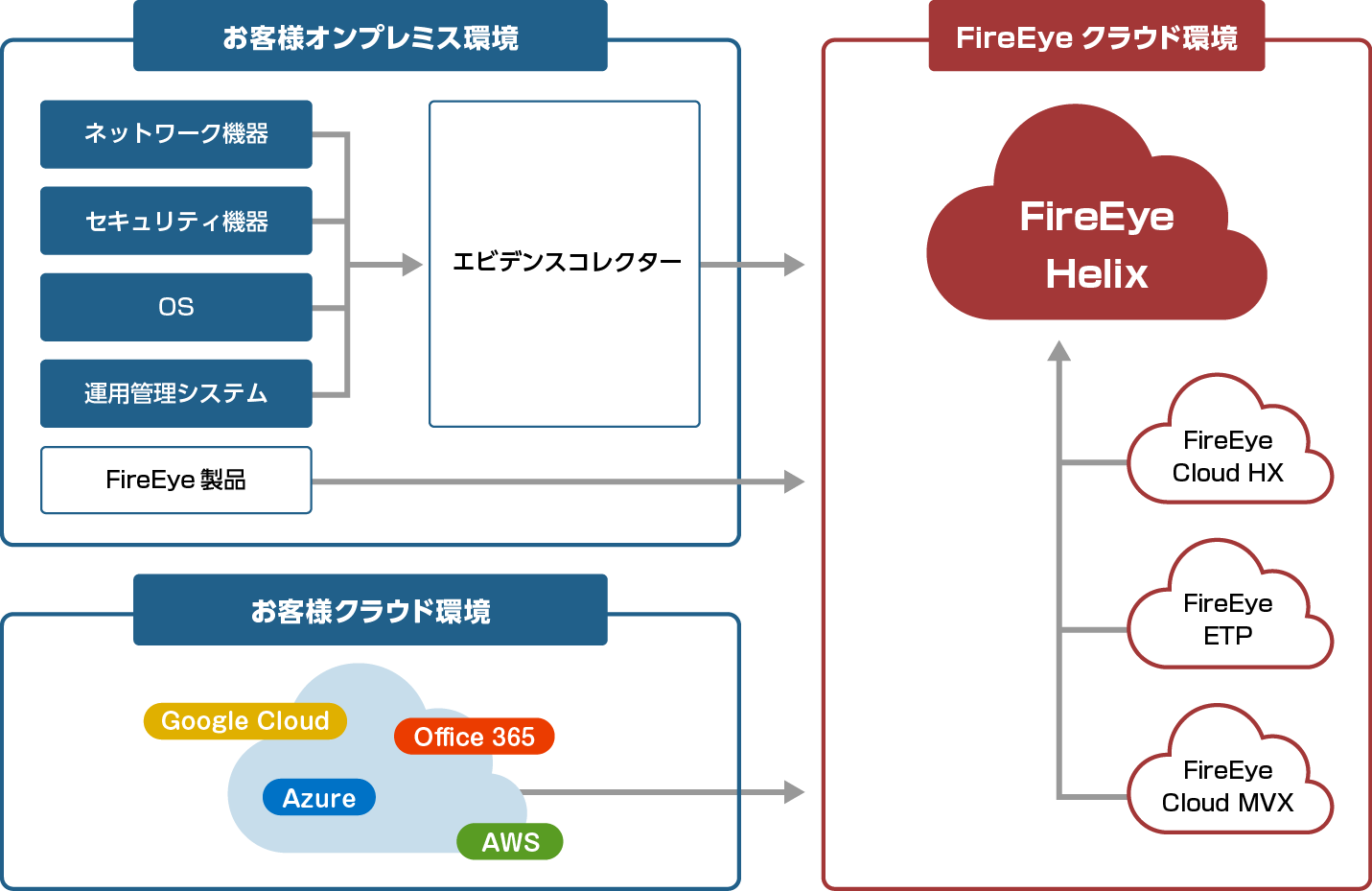
Helix can collect not only Trellix (formerly FireEye) products, but also logs/alerts from many vendors, including network equipment, security equipment, cloud products, and other third-party products.
Centralized management of logs/alerts
Not only Trellix (formerly FireEye) products, but also logs/alerts from many vendors, including third-party products, are centrally managed with Helix. It also automatically prioritizes according to the content of the alert.
threat intelligence
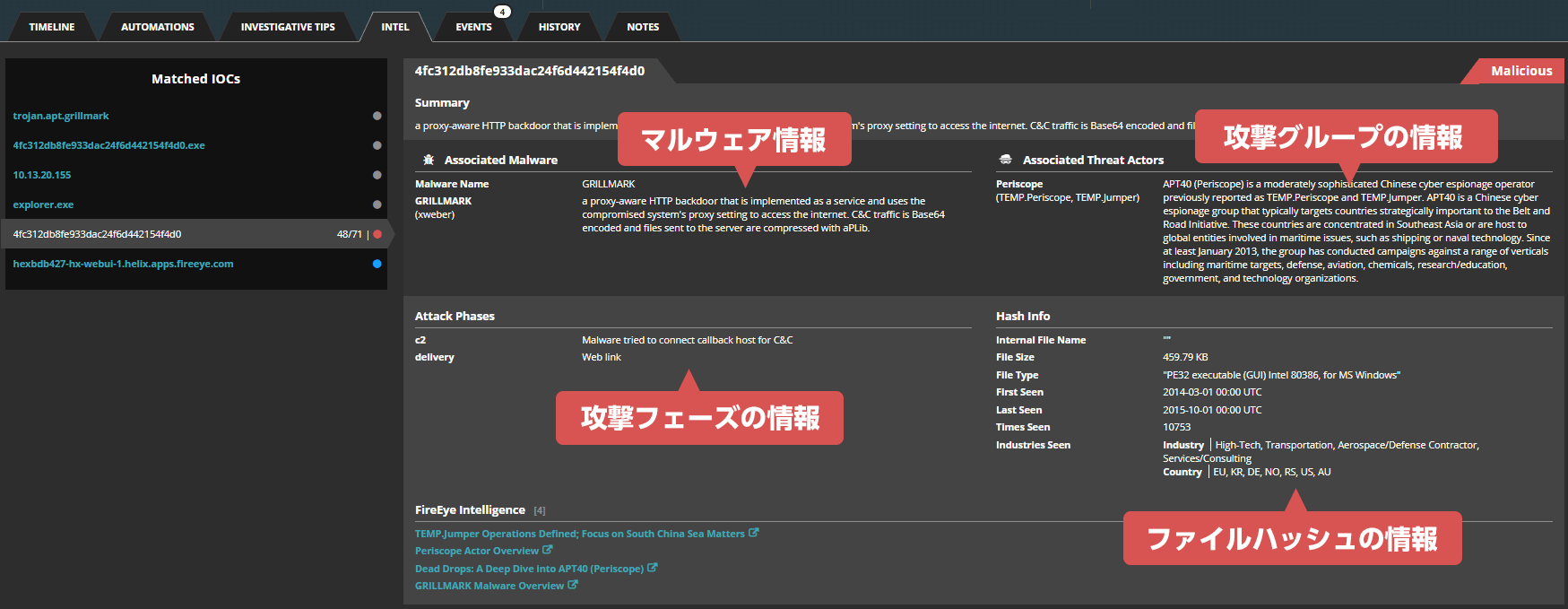
Logs captured by Helix can be matched with Trellix's (formerly FireEye) intelligence to detect threats that other companies' products could not detect.
In addition, threat intelligence can automatically associate attacker information with each alert.
Examples of attacker information: Attack group, malware, attack phase, file hash, etc.
Guided survey
Based on the knowledge of Trellix's (formerly FireEye) Incident Response Team (Mandiant), it automatically recommends items to check according to the content of the incident, allowing immediate investigation.
This shortens the initial response time.
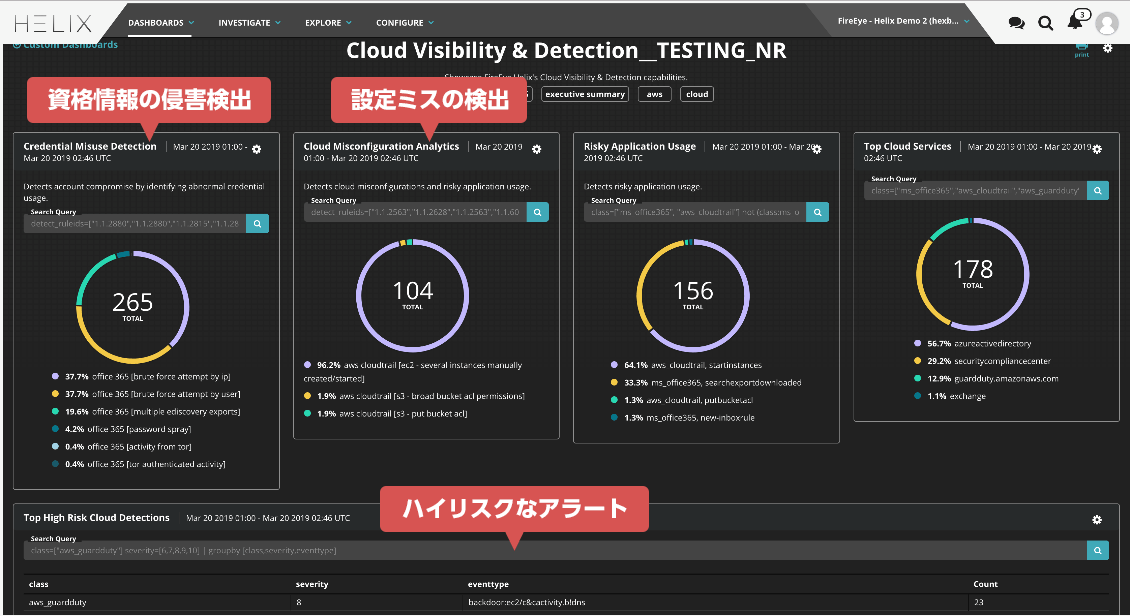
cloud security
Cloud-enabled threat intelligence
Apply rules based on threat intelligence from Trellix (formerly FireEye) implemented in Helix to logs/alerts in the cloud environment to uncover previously undetectable threats.
You also have the flexibility to create custom rules.
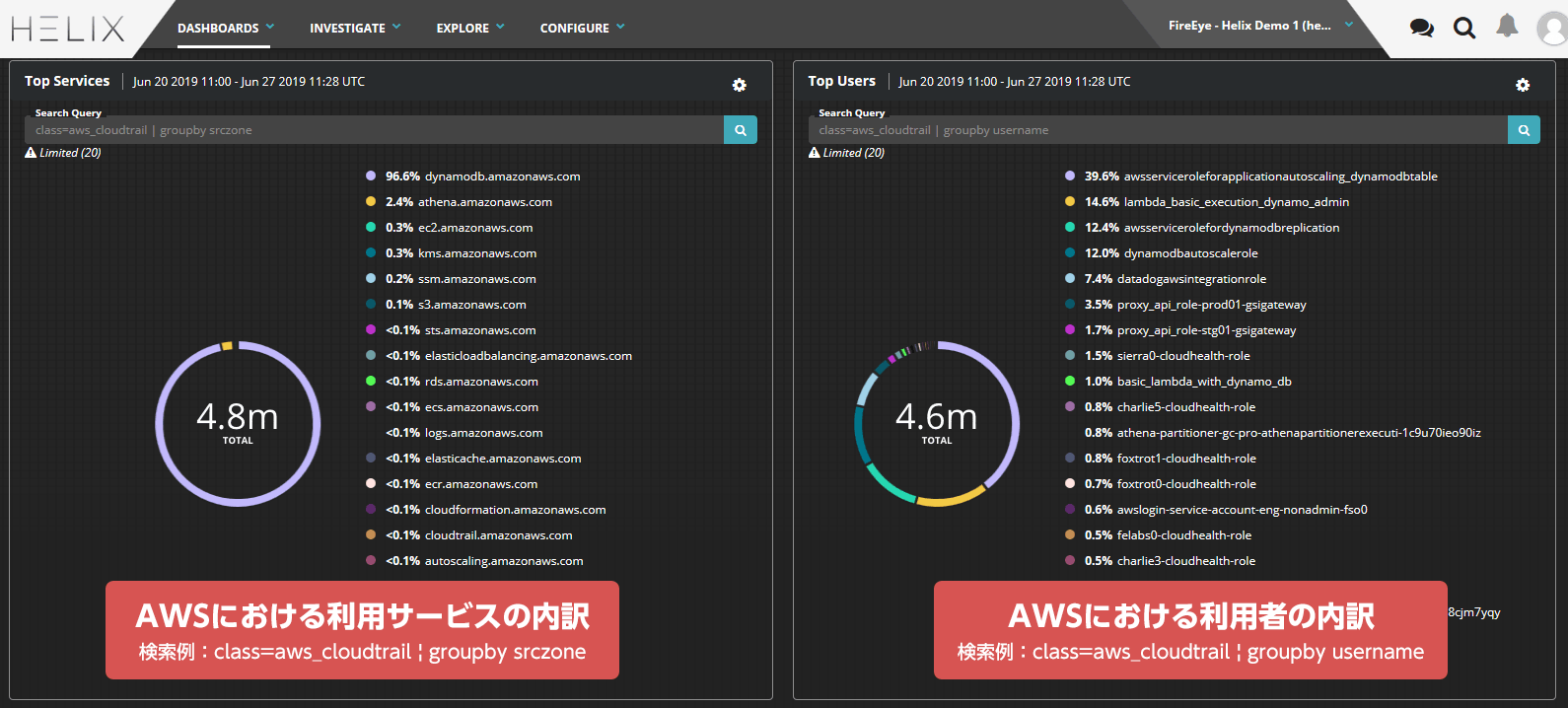
Dashboard function
In addition to the built-in dashboards, you can create custom dashboards according to your environment.
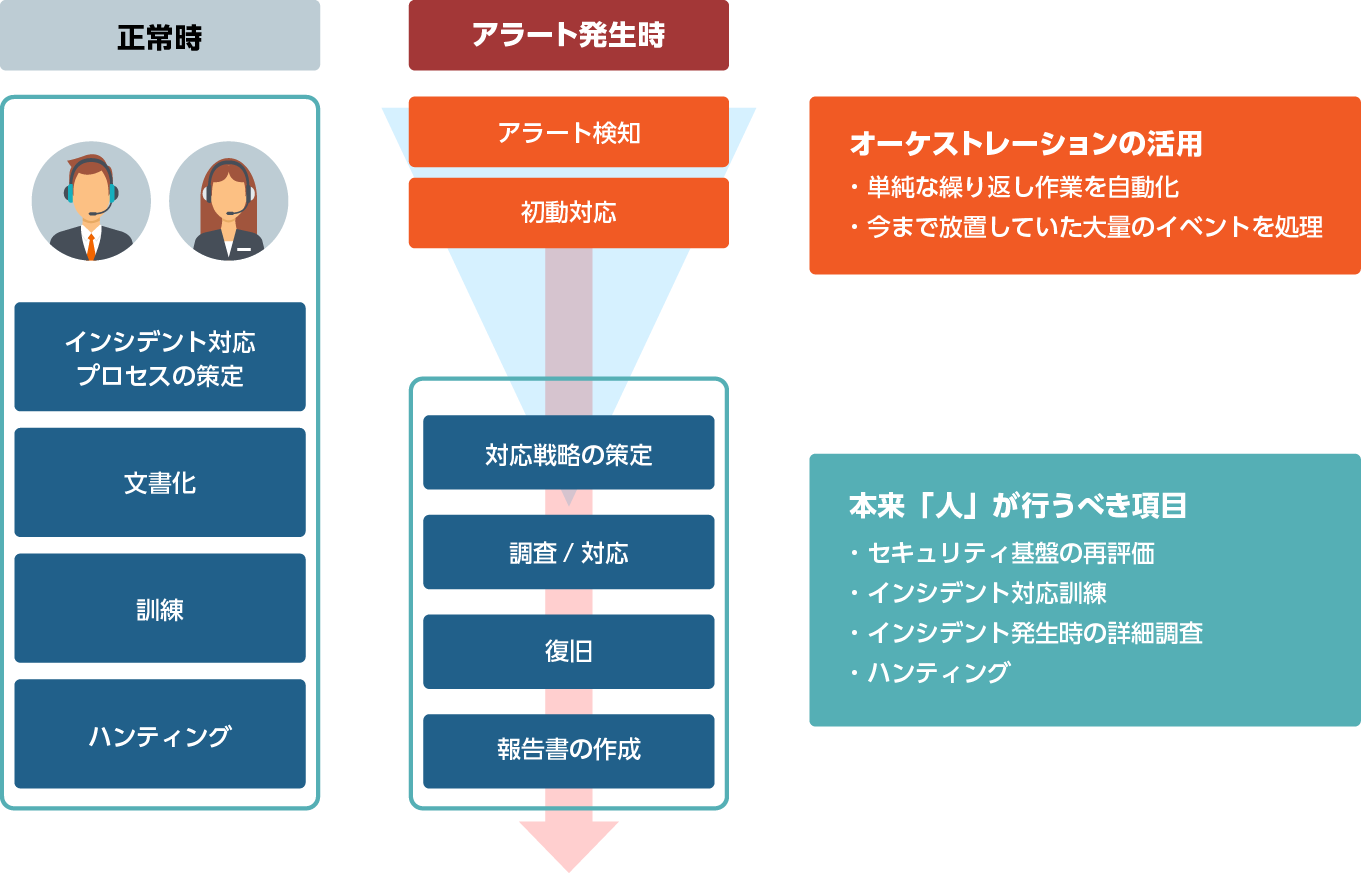
Security orchestration*
現在、多くのお客様が「セキュリティ運用者の不足」を運用上の課題に挙げております。
Helix's security orchestration function automates simple/repetitive work and a large number of events that have been left unattended due to lack of human resources and time. The purpose is to strengthen the foundation.
*Security orchestration can be realized by linking with FSO.
lots of plugins
In addition to Trellix (formerly FireEye) products, we have plug-ins for many other companies' products, and as of December 2019, we have a total of 214 built-in plug-ins. (Hereafter, some examples)
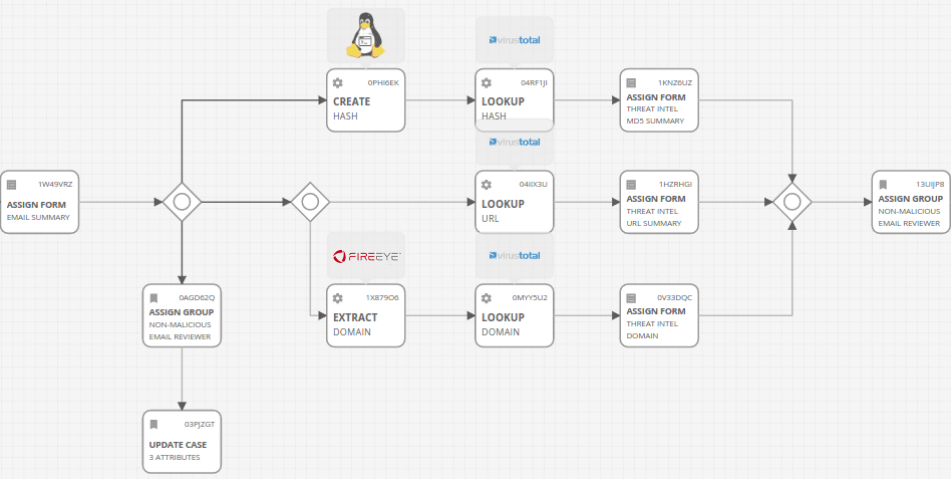
Product linkage/automation
Create playbooks that combine conditions and actions based on preset policies.
example)
Conditions: If Severity is High and the terminal requires attention,
Action: Isolate the device from the network
Deployment configuration
Helix Startup Support Service
Service overview
This is Macnica unique service to help customers make the most of Helix/FSO, which has a wealth of functions, and to help customers start up operations smoothly.
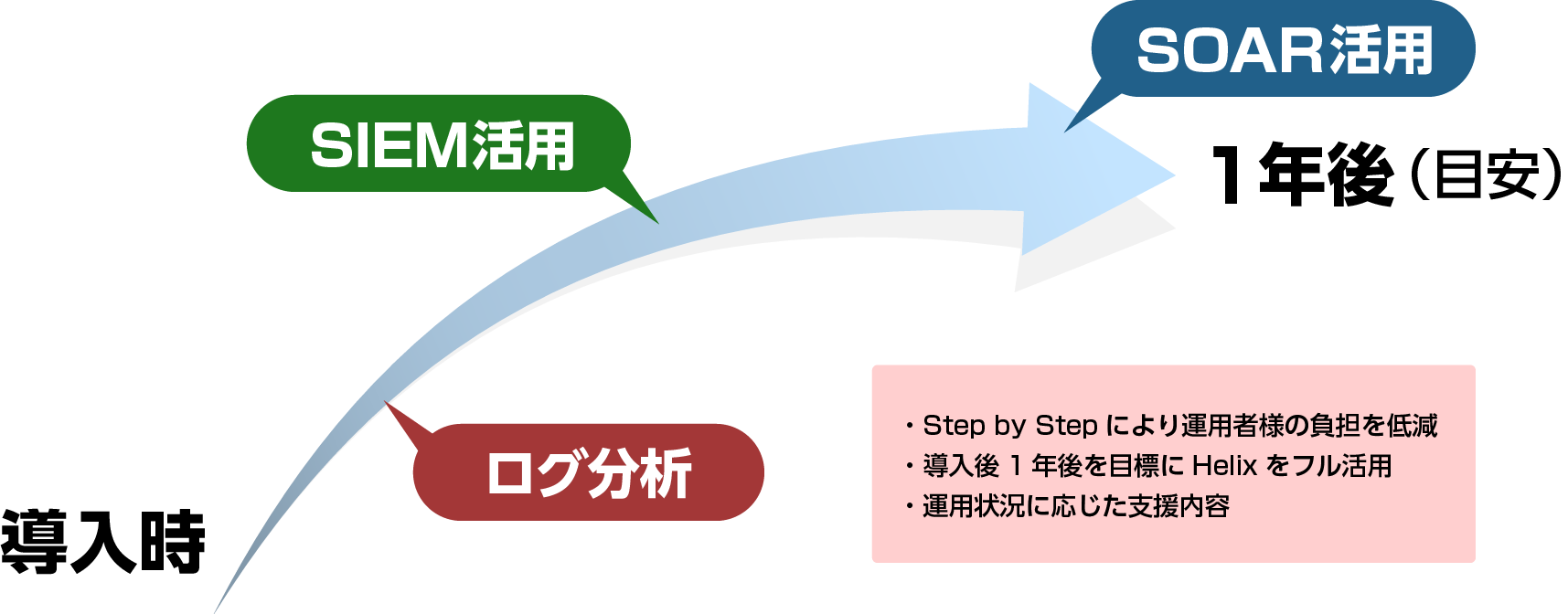
Details of support
Our engineers will visit you on a regular basis, and will explain how to operate Helix and provide consultation on custom dashboards and playbooks according to your Helix usage.
Implementation example: Implementation of operational support a total of 5 times
Inquiry/Document request
In charge of Macnica Trellix Co., Ltd.
- TEL:045-476-2010
Weekdays: 9:00-17:00