product
- Line up
- Network Security: Trellix (formerly FireEye) Network Security
- Network Security: Trellix (formerly McAfee) Advanced Threat Defense
- Network Security: Trellix (formerly McAfee) Network Security Platform
- Endpoint: Trellix (formerly FireEye) HX
- Endpoint: Trellix (formerly McAfee) Mvision
- Data Protection: Trellix Data Security
- Email Security: Trellix (formerly FireEye) Server Edition
- Email Security: Trellix Cloud Edition
- Security Operations: Trellix (formerly FireEye) Helix
- Security Operations: Trellix (formerly McAfee) SIEM (Security Information and Event Management)
- Enhanced cloud governance: Trellix (formerly FireEye) Cloudvisory
- File Security: Trellix (formerly FireEye) Malware File Storage Scanning
- Integrated Management Solution: Trellix (formerly FireEye) Central Management
- NDR Solution: Network Investigator (NI) / Packet Capture (PX)
- Cloud-based File Threat Protection: Trellix IVX Cloud
Specifications/Technical Information
- Trellix (formerly FireEye) Technical Information
- Trellix (formerly FireEye) Specifications
- Network Security: Trellix (formerly FireEye) Network Security Technical Information
- Network Security: Trellix (formerly McAfee) Network Security Platform Technical Information
- Network Security: Trellix (formerly McAfee) Network Security Platform Specifications
- Network Security: Trellix (formerly McAfee) Advanced Threat Defense Technical Information
- Network Security: Trellix (formerly McAfee) Advanced Threat Defense Specification
- Email Security: Trellix (formerly FireEye) Server Edition EX Series Technical Information
- Email Security: Trellix (formerly FireEye) Server Edition EX Series Specifications
- Integrated Management Solution: Trellix (formerly FireEye) Central Management (CM) Series Specifications
- Security Operations: Trellix (formerly McAfee) SIEM (Security Information and Event Management) Technical Information

Trellix
Trellix
Trellix (formerly McAfee) Mvision
Device to Cloud security platform by Trellix (formerly McAfee)
Trellix (formerly McAfee) MVISION lineup
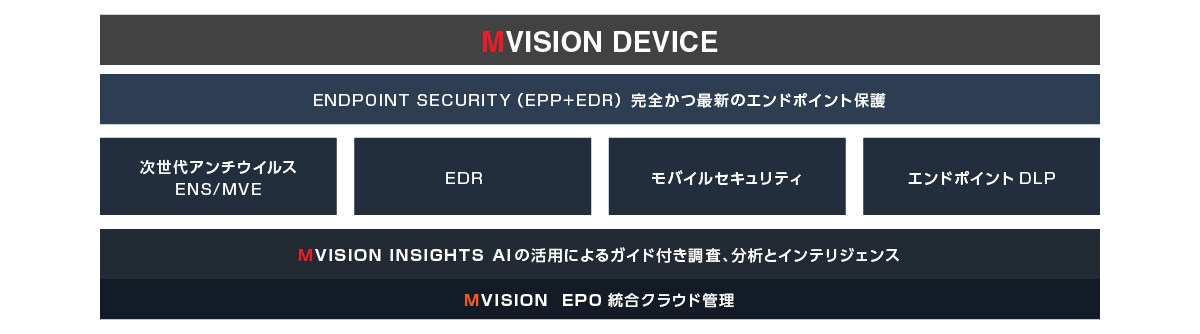
McAfee MVISION Product Brief
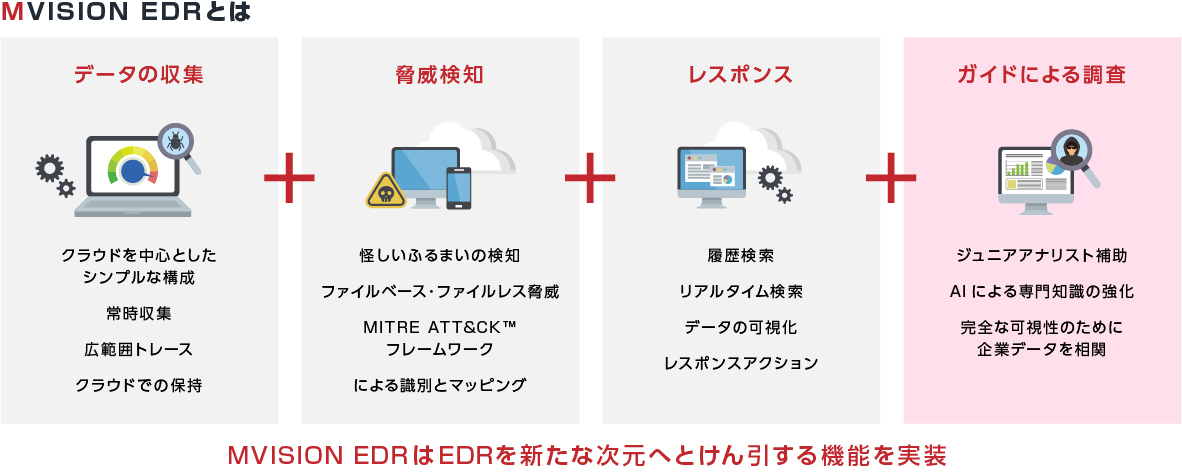
- EDR: MVISION EDR
This is an EDR product equipped with McAfee's unique incident analysis guide function. By collecting a large amount of logs and alerts collected from agents and using the guide function to display the thinking logic of security analysts with hypotheses and QA to guide how to deal with them, even inexperienced analysts can be advanced. operation becomes possible.
- Next-generation AV: MVISION Endpoint
Security features such as multi-layered control by machine learning detection function and recovery function by remediation (rollback) are enhanced. For customers who are already using Windows Defender, by linking with Windows Defender, it is possible to operate together with Defender through the integrated management function of Windows Defender.
- ePO: MVISION EPO
It is a SaaS type platform that realizes integrated management of security infrastructure. Terminals of various platforms such as Windows/Linux/Mac can be centrally managed, and tens of thousands of terminals can be managed on one platform.
- MTD: MVISION MOBILE
Threats specific to mobile devices such as man-in-the-middle attacks and rogue access points can be detected and automatically dealt with.
- MTD: MVISION Insights
Block various attacks using data collected from a huge number of sensors.
Trellix Endpoint Security Solution Brief
MVISION EDR Overview
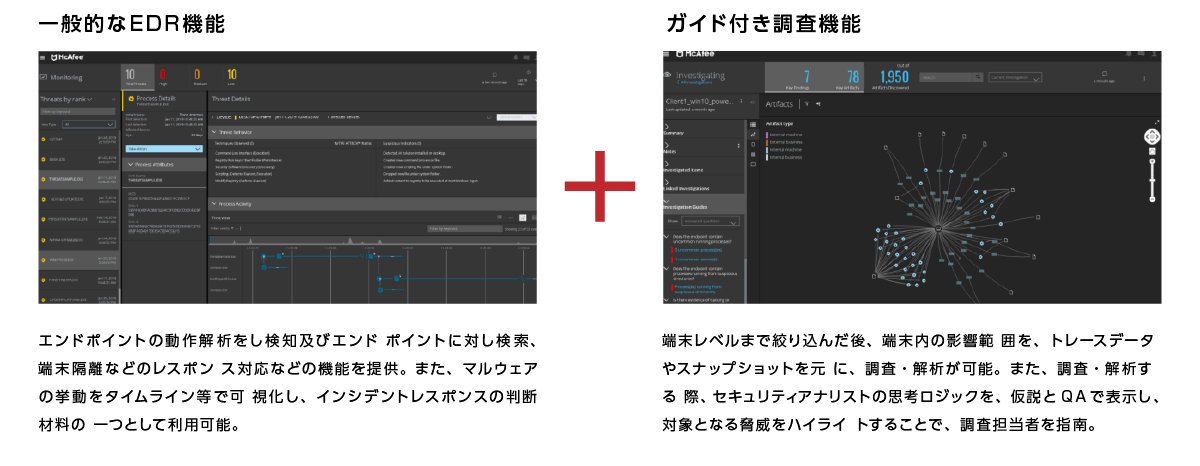
Guided investigation function
Investigation support function provided by MVISION EDR
Trellix (formerly McAfee) Endpoint Security Overview
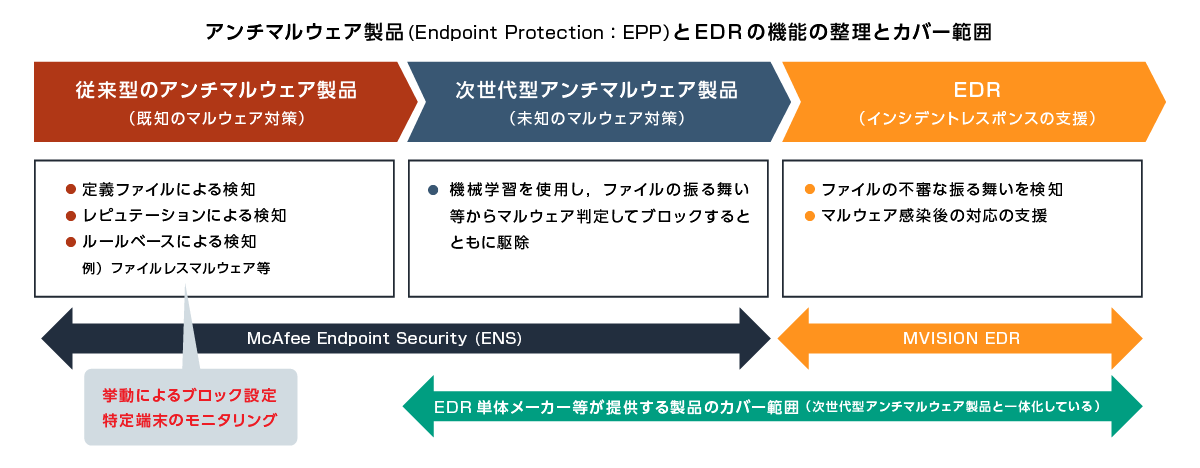
There are two options for endpoint security for Windows.
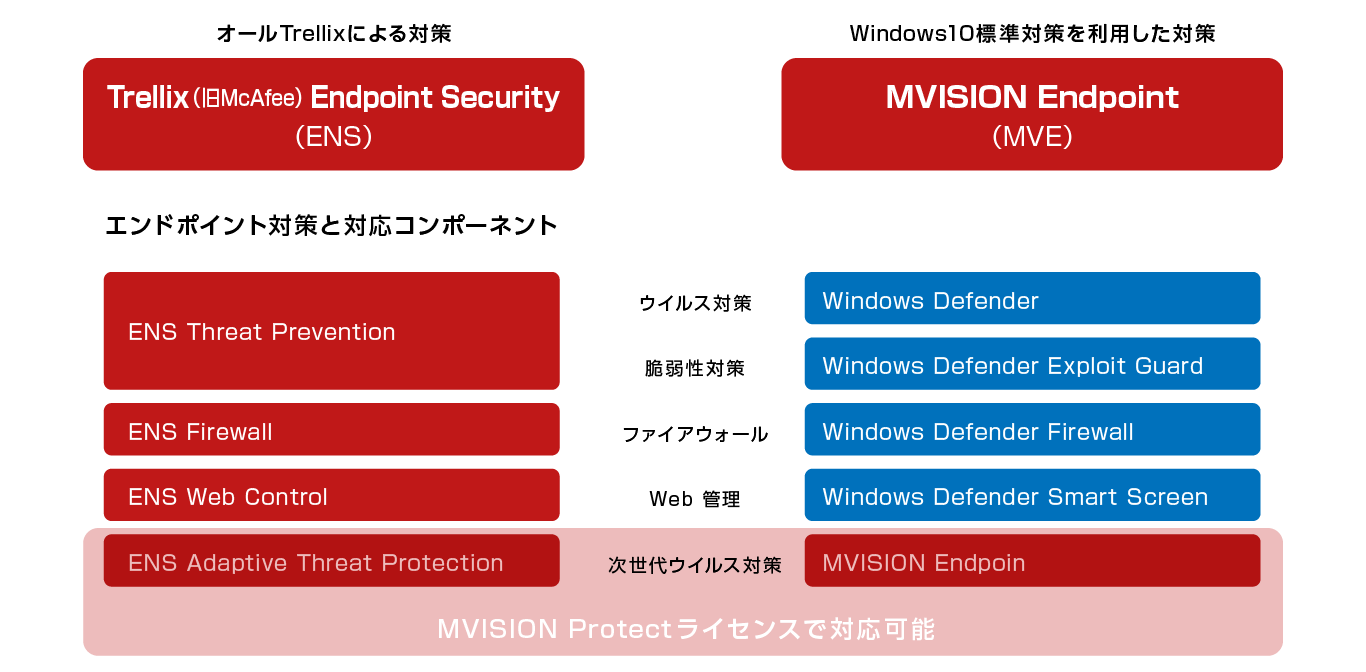
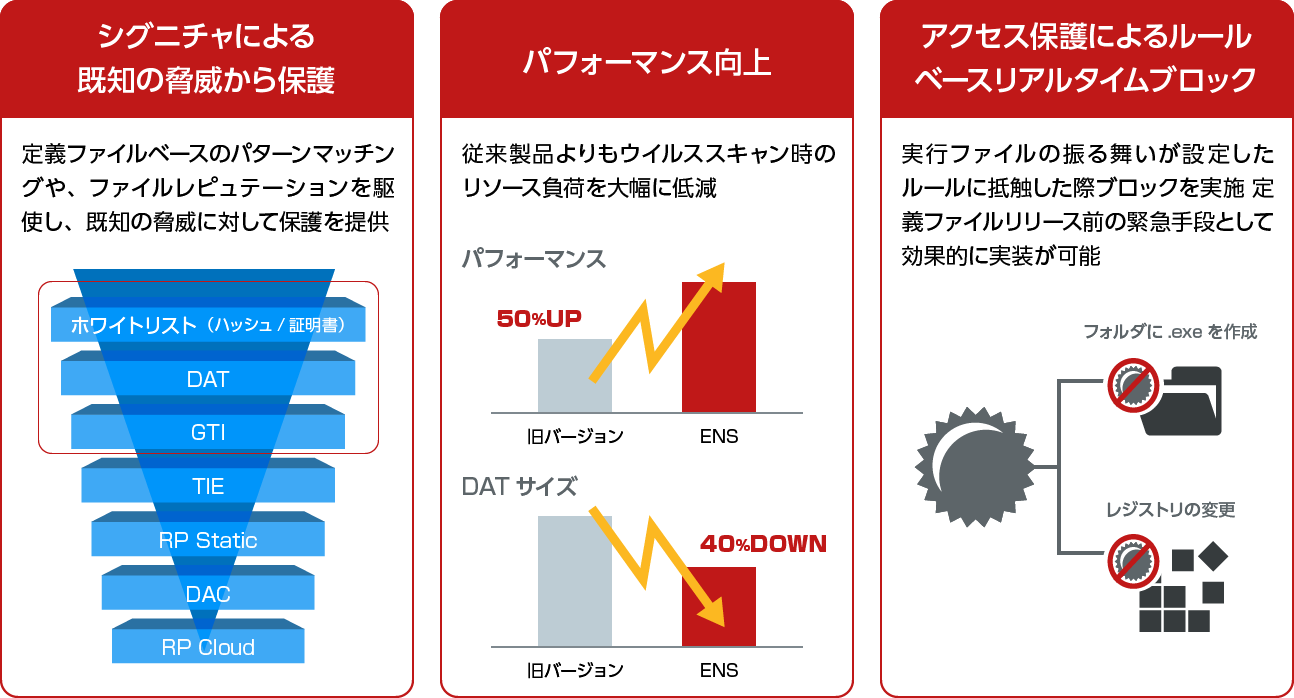
Antivirus
- Efficient protection against known malware
- Rule base block also implemented
- Advanced script scanning (AMSI integration)
- In Windows 10, a new mechanism has been implemented to allow another program to call the scanning function of the antivirus software installed on the computer. Using an interface called the Antimalware Scan Interface (AMSI), you can pass content from within the program to antivirus software to check for malware.
- Even with multiple layers of obfuscation, the malicious script will eventually be rendered readable and the plain code will be handed over to the script processing engine. At that stage, the scripting engine can call a new Windows AMSI API to request scanning of the rendered content.
- Powershell, VB Script, Java Script code can be handed over by AMSI to NES for scanning.
Vulnerability countermeasures
Endpoint Security Threat Prevention
- Exploit prevention
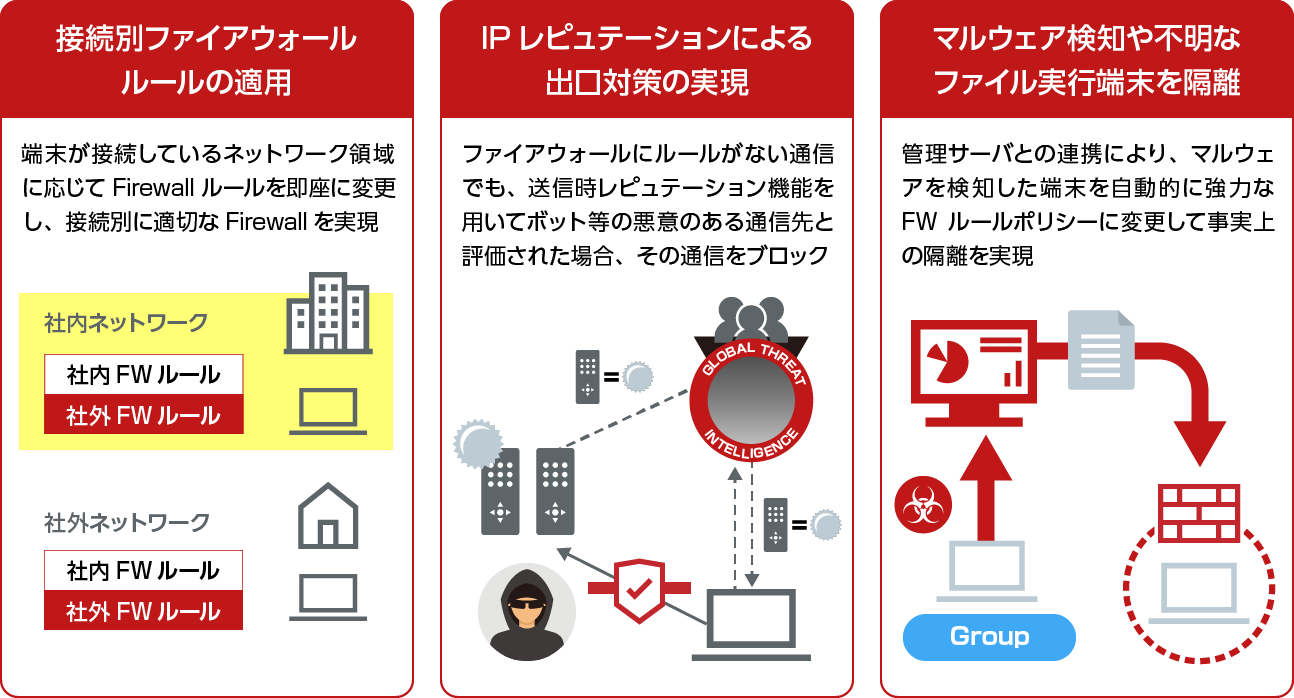
firewall
Endpoint Security Firewall
- Flexible and Robust Firewall Functionality
- Network isolation is also realized
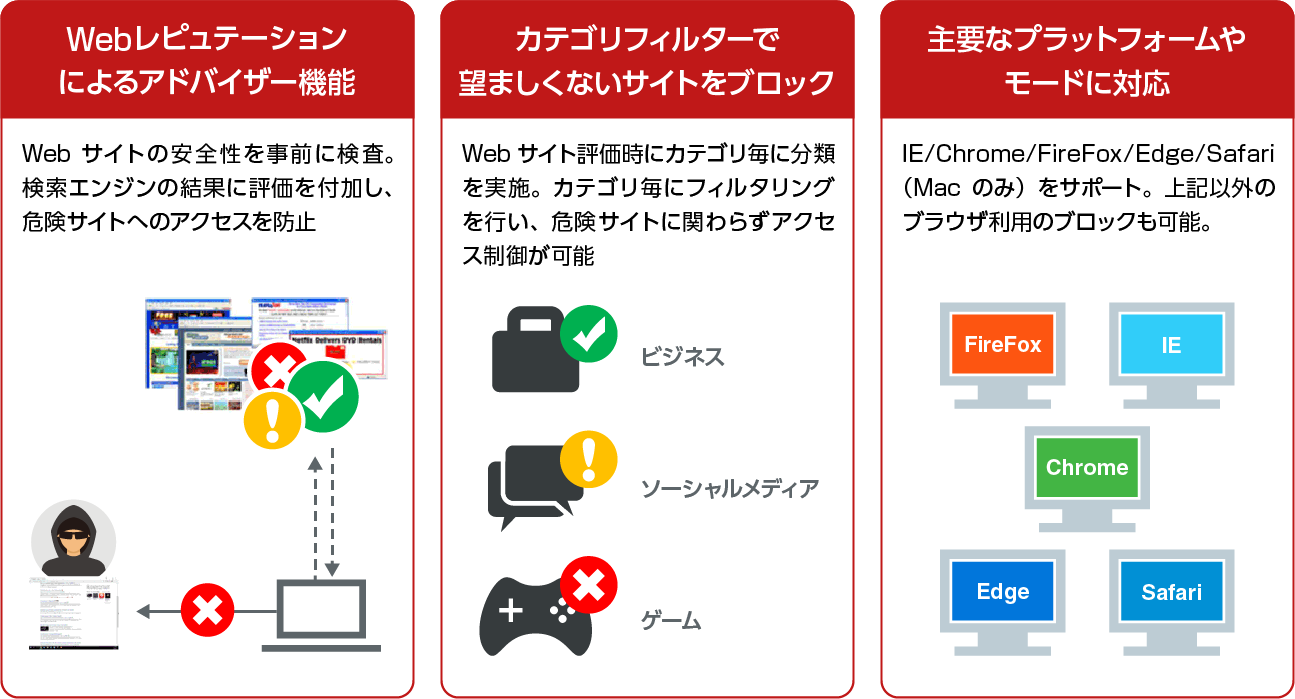
Web management
Endpoint Security Web Control
- Websites with many infection routes are inspected before malware strikes
Next-generation antivirus
Endpoint Security Adaptive Threat Protection
- machine learning
- Dynamic Application Containment (DAC)
- Rollback function
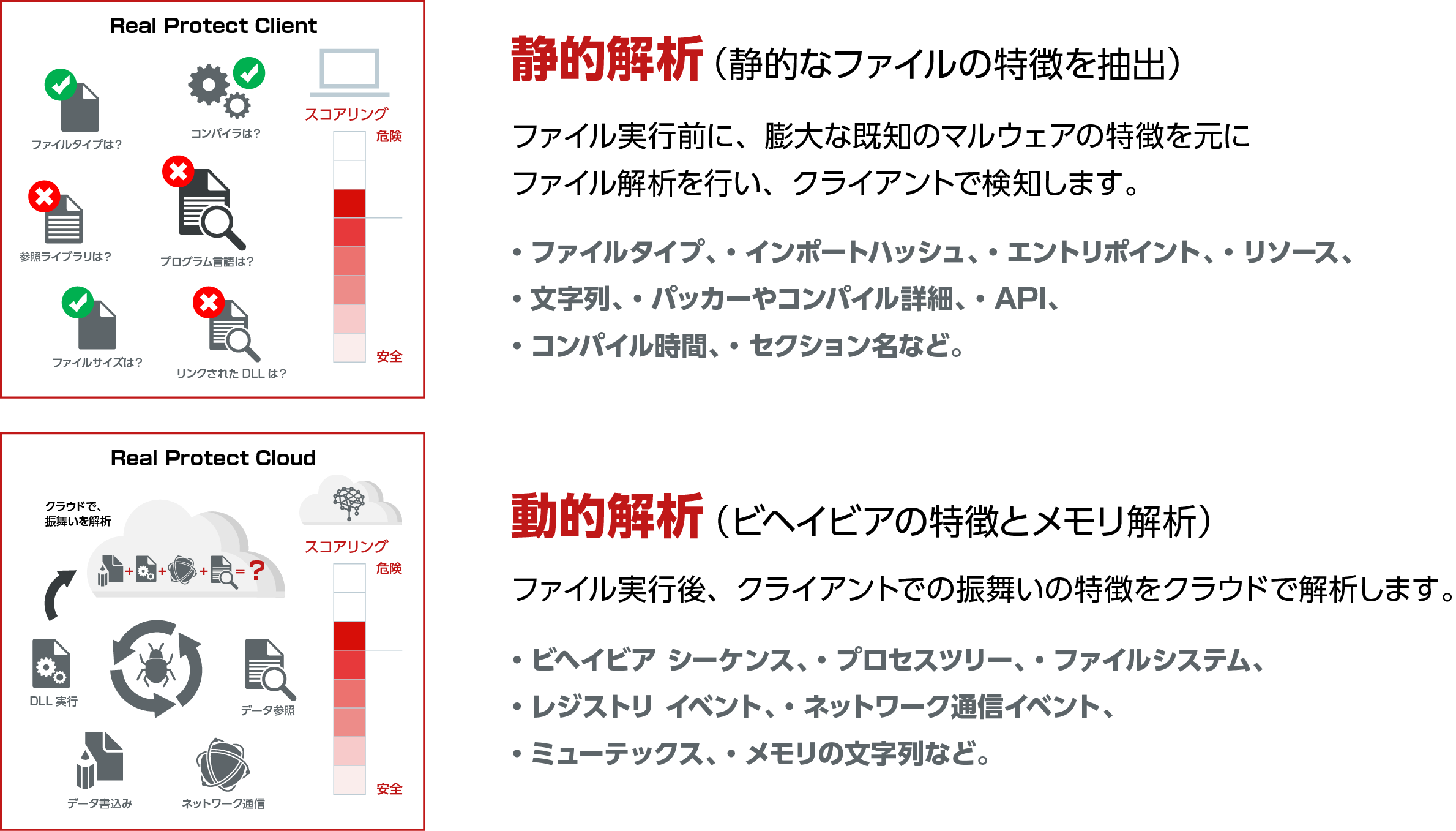
Dynamic Application Containment (DAC)
- Monitors processes that could not be identified as threats and blocks (contains) only malicious behavior
- Targets processes that could not be judged as "trusted" or "threat" by file reputation
- Although the process is running on the system, it is almost impossible to affect the system because it cannot perform dangerous actions prohibited by the rules.
- Example of limitation of operation by DAC
- Characteristic Behavior of Ransomware
- Diffusion using NW and external media
- Unauthorized access to other processes (injection)
- Creating files in different executable formats (downloaders, droppers work)
Rollback function
- Rolls back the changes made by the threat, restoring as much of the original state as possible before the threat ran.
- Monitors the behavior of processes with a reputation of Unknown or lower and their child processes.
- If a monitored process behaves illegitimately, it terminates the process and restores it to its pre-execution state.
Inquiry/Document request
In charge of Macnica Trellix Co., Ltd.
- TEL:045-476-2010
Weekdays: 9:00-17:00