product
service
Specifications/Technical Information
solution
Application for evaluation machine

Forescout
ForeScout
solution
factory security
Why do we need factory security
Increased awareness of security in smart factories
The trend of IoT in factories will accelerate more and more in the future. As various devices are connected to the network, the need for security measures becomes urgent. Even if we are not always connected to the outside world, it is impossible to be completely cut off from the outside world. There are many cases, such as WannaCry and NotPetya, in which an incident occurs at a production site and the line stops, resulting in a large amount of loss.
There is a tendency to think that there are still few incidents in Japan. However, since there is no obligation to report unless personal information is leaked, it is assumed that there are many damages that are not actually reported. The need for security measures within the supply chain is also increasing, and if measures are not implemented, it may affect business.
| Company/Organization | detail | Malware name |
|---|---|---|
| major car companies |
Production stop at domestic factories |
Wanna Cry |
|
major car companies |
Operation stop at overseas factory |
Wanna Cry |
|
Overseas nuclear power plant |
Radioactivity monitor system failure |
Not Petya |
|
Overseas manufacturing industry |
Production stop (manual operation) |
Locker Goga |
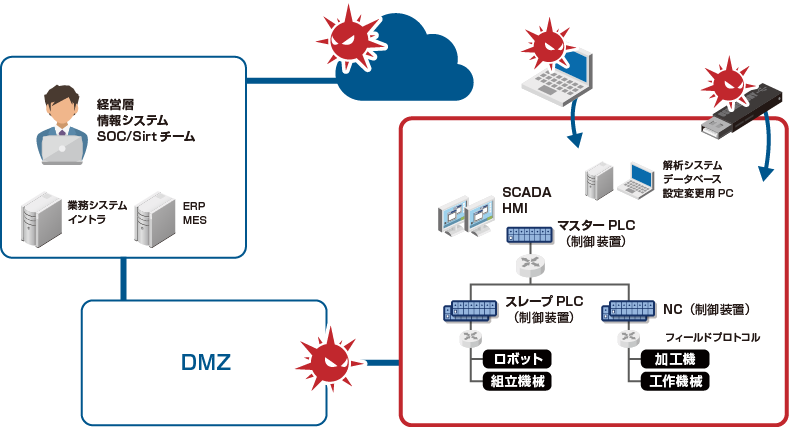
Cybersecurity Threats Approaching Factories
Cybersecurity risks in factories
In many factories, stable operation is a major premise, and security measures are secondary. It has been pointed out that there is a high possibility that the infection has already spread in many factories where measures have not been taken.
The following security risks are possible.
- Via IT network
- Via a terminal brought in from outside
- Via maintenance company

- Loss of competitiveness due to theft of confidential information on production technology
- Product defects and physical destruction due to falsification of production-related data
- Maximize damage by rapidly spreading infection to other networks
- Financial loss and credibility loss due to suspension of production and services
Failure to implement security measures for stable operation will actually threaten the factory.
To keep the factory secure
Representative security measures
| Countermeasure solution |
Overview |
Threats that can be handled |
|---|---|---|
| antivirus | Detects malicious viruses that infect Windows machines by checking against virus definition files that are updated daily. Requires installation on a PC or server in the control system. |
Although it is possible to prevent known malicious programs from infecting PCs and servers, it is not possible to detect or block the reception of unknown malicious programs or illegal communications. |
| Application control | Prevent execution of files other than previously permitted files. Requires installation on a PC or server in the control system. | It can prevent malicious programs from infecting PCs, servers, etc., but cannot detect or prevent illegal communications from other devices. |
| Security patch management | Understand devices with vulnerabilities that exist in the system. | It is possible to grasp terminals with known vulnerabilities, but it is not possible to grasp unknown vulnerabilities (zero-day). |
| Measures against external USB memory | By scanning the inside of the USB memory, it prevents malicious program infection through the USB memory. Requires installation on a PC or server within the control system, or installation of dedicated scanning equipment within the premises. | Although it is possible to prevent malicious programs from infecting PCs and servers via USB memory, it is not possible to prevent unscanned USB memory from being brought in unless an agent is installed on the PC or server. |
| network isolation | It is used to block unnecessary communication among the communication that crosses each area. Requires network configuration changes during installation. | Unauthorized communication can be prevented by setting permission/rejection of communication across areas, but it is difficult to reject all unauthorized communication from the viewpoint of convenience and operation. |
| network monitoring | Visualize the system and detect abnormal communication by learning normal communication in the factory network. Network switches may need to be changed during installation. | It can detect communication that changes due to malicious program infection or intrusion of an external terminal as an anomaly, but the physical medium for obtaining communication to be monitored is limited to Ethernet cables. |
| Terminal management | Visualize and manage terminals connected to the factory network. Detect when an unmanaged terminal is connected. It can also be used for asset management. | By visualizing and managing the terminals connected to the factory network, it is possible to detect connections of unauthorized terminals and connections of unmanaged terminals. Device management can also quarantine devices that violate company policies. |
| access control | Visualize and manage terminals connected to the factory network. Detect when an unmanaged terminal is connected. It can also be used for asset management. | By visualizing and managing the terminals connected to the factory network, it is possible to detect connections of unauthorized terminals and connections of unmanaged terminals. Device management can also quarantine devices that violate company policies. |
Unlike IT systems, it is difficult to introduce software in a factory network that cannot be stopped. There are many legacy systems, and it is common that it is difficult to secure them individually.
What is needed is a measure that can immediately detect where an abnormality is occurring when something happens and understand where it will be affected, in other words, network monitoring using DPI.
DPI is an effective countermeasure ~SilentDefense Solution~
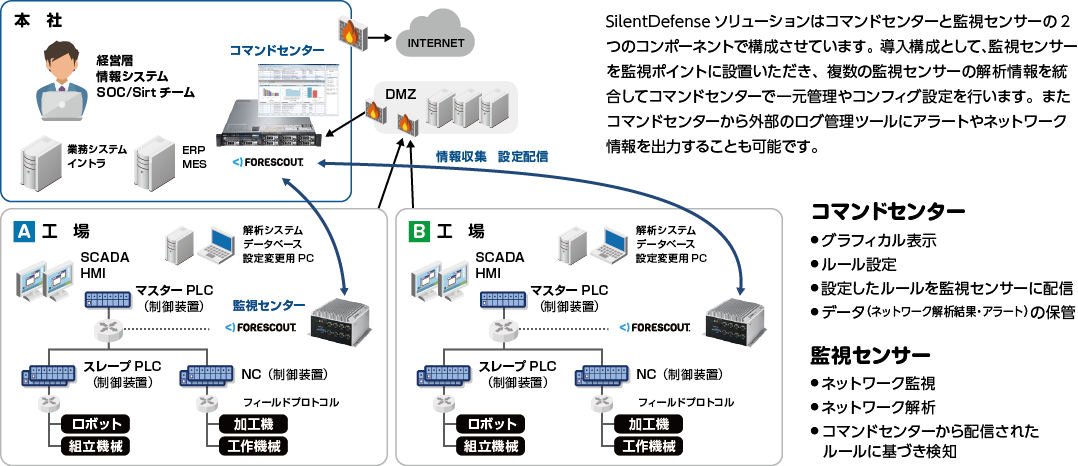
Installation configuration image
DPI (Deep Packet Inspection) products can automatically perform network monitoring, anomaly detection, network configuration diagram creation, asset management, etc. without affecting existing systems. ForeScout's SilentDefense solution provided by our company does not burden the network and realizes a secure control system.
Effective Countermeasures -Forescout Solution-
Forescout Solution Brief
Forescout products can automatically perform comprehensive asset management, network monitoring, anomaly detection, network configuration diagram creation, access control, etc. without affecting existing systems. Forescout's Forescout Platform solution provided by our company realizes a secure control system without imposing a load on the network.
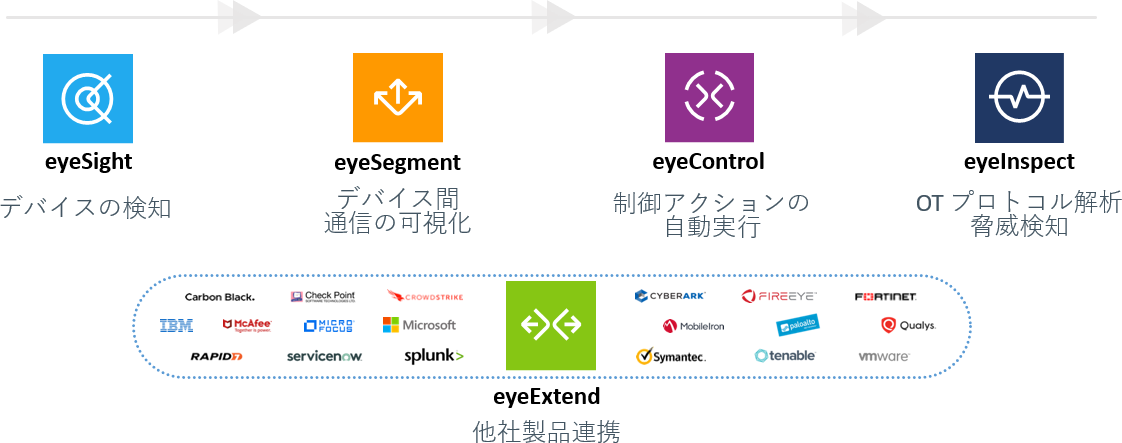
Forescout Solution Strengths
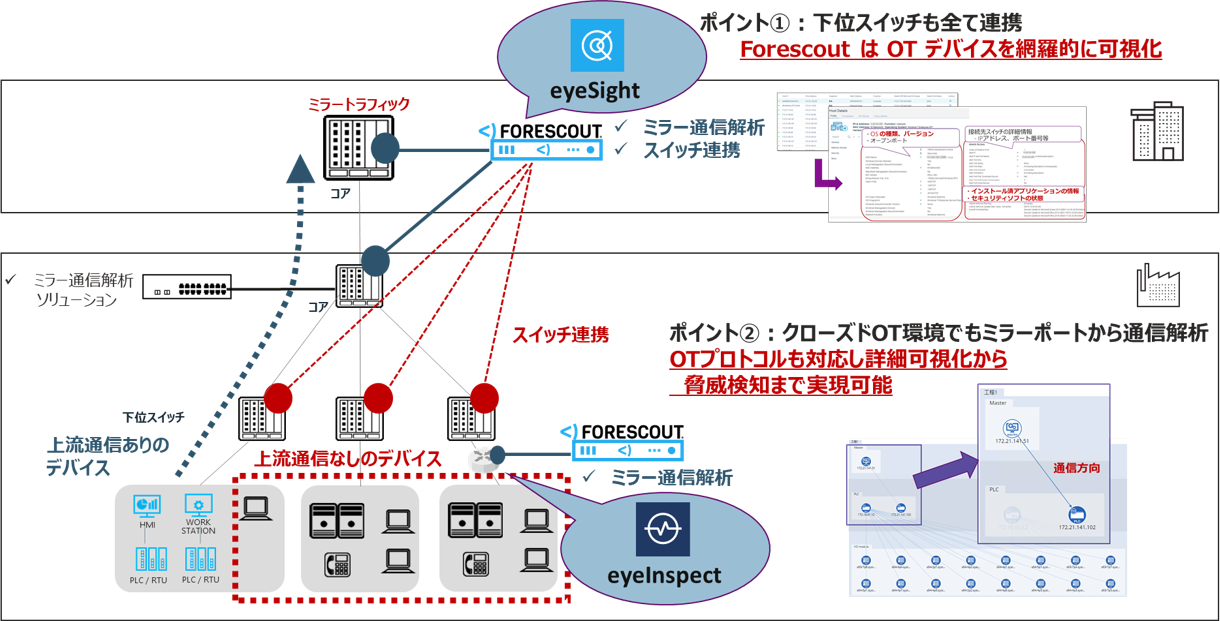
Broad coverage and exhaustive visualization
工場の対策を行う際、DPI(Deep Packet Inspection)製品を導入するお客様が多いですが、一般的なDPI製品は可用性を重視するあまりパッシブな情報解析のみで、工場全体の対策実施に大量のセンサーが必要となってしまうことが課題となります。Forescoutソリューションは工場の運用に影響を与えず様々な手法を用いて効果的に情報取得が可能です。網羅的な可視化と管理、またDPI製品の機能も有した工場セキュリティソリューションです。
Advantages of the SilentDefense Solution
Number of protocols supported
Communication that flows through control system networks such as factories mainly uses OT-specific protocols that are different from IT networks. Compared to other DPI products, our protocol analysis capability has been highly evaluated due to our track record of analyzing the payload part of packets from the beginning.
| Manufacturing communication protocol | Information system communication protocol |
|---|---|
| CC-Link (Field, FieldBasic, Control), SLMP, Melsoft, EtherNet/IP, EtherCAT, OPC-AE, OPC-DA, Modbus ASCII, Modbus RTU, Modbus/TCP, Vnet/IP, VNet IP WAN, CDP | FTPDATA, FTP, HTTP, MS-SQL, NetBIOS, NTP LDAP, OracleTNS, SMB, SSL, STP, Telnet |
* Even if it is not supported, it has the function of asset visualization and detection rule creation by script.
*The above is a representative example. Please contact us for other information.
Various support and knowledge
Forescoutは既に多数のユーザー様にご愛顧頂いており、弊社ではナレッジを蓄積しております。
We are able to provide operation support, introduction support, and assessment services based on our extensive implementation experience and established support.
Download the document for details
Let's start factory security measures
~What should be done in factories in the IoT era~