product
service
Specifications/Technical Information
solution
Application for evaluation machine

Forescout
ForeScout
solution
building security
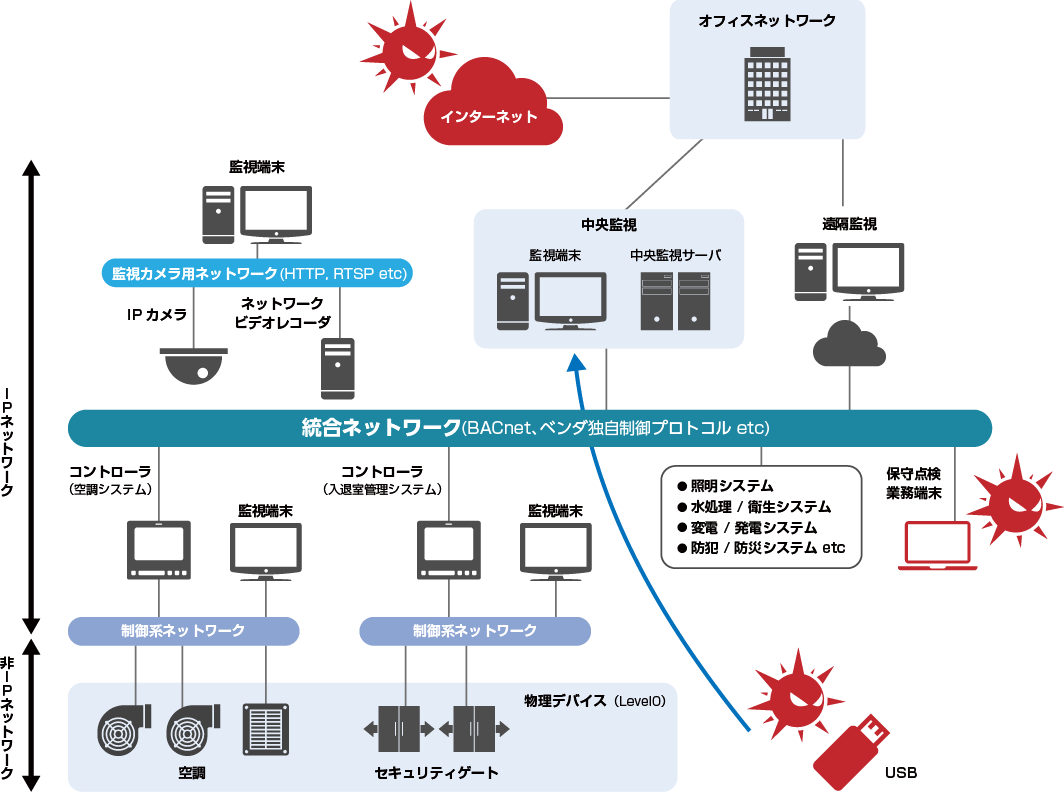
Attention is focused on the necessity of cyber security for building systems in Japan. The conventional common sense that a building is isolated from the Internet and uses its own communication protocol to prevent cyberattacks is no longer valid.
The "Guidelines for Cyber-Physical Security Measures for Building Systems" also point out that although attacks on buildings are increasing worldwide, security measures are extremely lagging and the damage is likely to spread.
マクニカでは上記の現状を解決する最適なソリューションをご提供します。
*2019/6 Silent Defense has changed its name from Security Matters to ForeScout.
The current state of dangerous building systems
Problems faced by the building
そもそもサイバーセキュリティを考慮した設計になされていないビルシステムでは下記の深刻な課題を抱えています。
- Not using encryption or authentication
- Software often out of date
- Unable to grasp the whole picture of the network
Possible security risks
- Threat intrusion via office network
- Threat intrusion via carry-on media
- internal fraud
Challenge: What are the best security measures for building systems?
Representative security measures
| Countermeasure solution |
Overview |
Threats that can be handled |
|---|---|---|
| antivirus |
Detects malicious viruses that infect Windows machines by checking against virus definition files that are updated daily. Requires installation on a PC or server in the control system. | Although it is possible to prevent known malicious programs from infecting PCs and servers, it is not possible to detect or block the reception of unknown malicious programs or illegal communications. |
| application Control |
Prevent execution of files other than previously permitted files. Requires installation on a PC or server in the control system. | It can prevent malicious programs from infecting PCs, servers, etc., but cannot detect or prevent illegal communications from other devices. |
| Security patch management |
Understand devices with vulnerabilities that exist in the system. | It is possible to grasp terminals with known vulnerabilities, but it is not possible to grasp unknown vulnerabilities (zero-day). |
| Measures against external USB memory | By scanning the inside of the USB memory, it prevents malicious program infection through the USB memory. Requires installation on a PC or server within the control system, or installation of dedicated scanning equipment within the premises. | Although it is possible to prevent malicious programs from infecting PCs and servers via USB memory, it is not possible to prevent unscanned USB memory from being brought in unless an agent is installed on the PC or server. |
| network isolation | It is used to block unnecessary communication among the communication that crosses each area. Requires network configuration changes during installation. | Unauthorized communication can be prevented by setting permission/rejection of communication across areas, but it is difficult to reject all unauthorized communication from the viewpoint of convenience and operation. |
| network monitoring | Visualize the system and detect abnormal communication by learning normal communication in the building system. Network switches may need to be changed during installation. | It can detect communication that changes due to malicious program infection or intrusion of an external terminal as an anomaly, but the physical medium for obtaining communication to be monitored is limited to Ethernet cables. |
Unlike IT systems, it is difficult to install software in building systems that have many unstoppable devices.
As a result, there are very few ways to detect an attack, and in many cases it is not until there is actual physical damage that an attack is detected.
Even if an attack is noticed, it is difficult to completely identify the path and target of the attack, and since the entire network is not understood, it is difficult to determine which devices need to be restored in order to deal with the physical damage. It is also difficult to find out.

In a building system, many devices are linked on the network to monitor and control the system, so "network monitoring" is a countermeasure against all kinds of cyberattacks on the building system.
Countermeasures: Network monitoring solutions
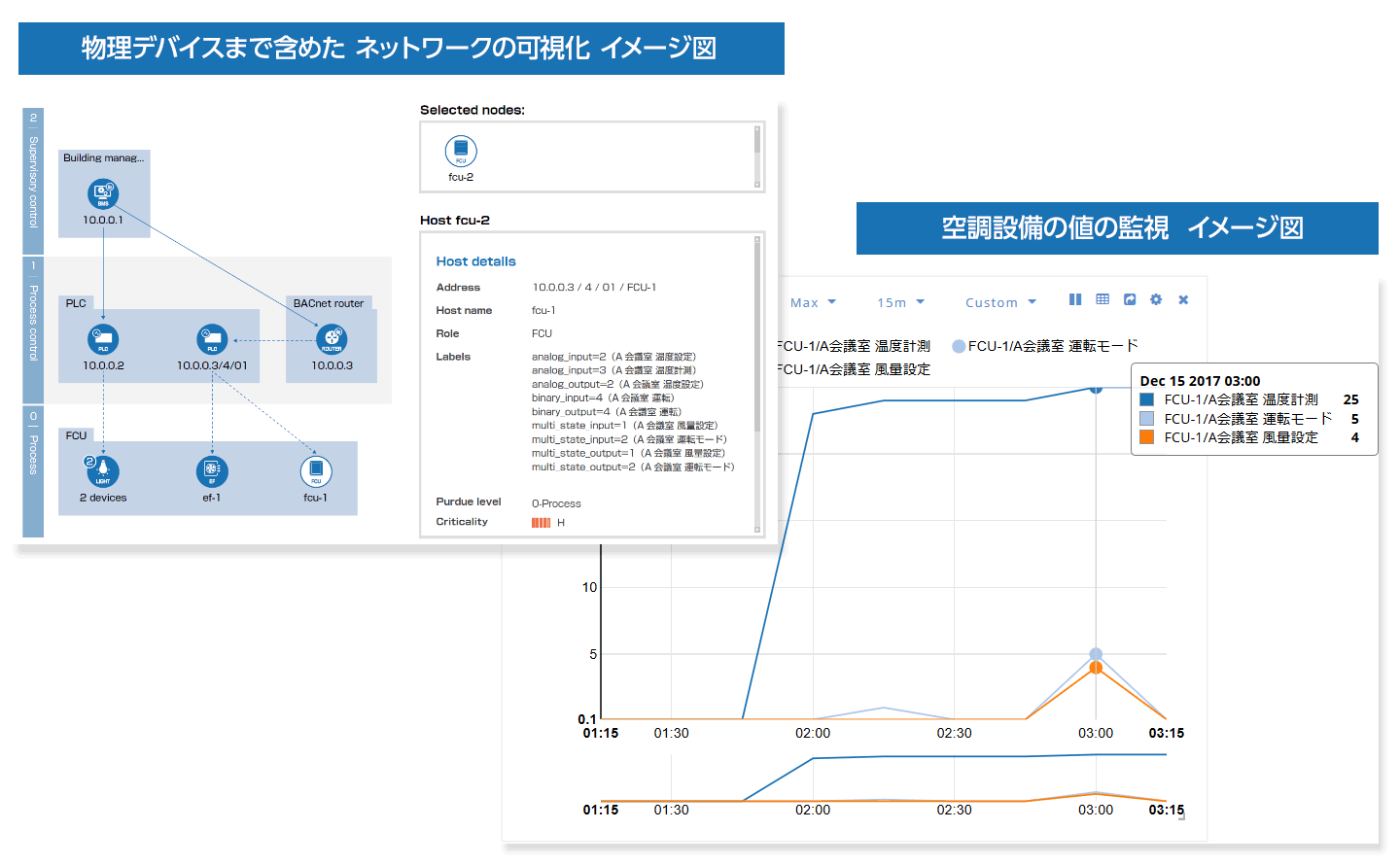
DPI (Deep Packet Inspection) products can automatically perform network monitoring, anomaly detection, network configuration diagram creation, asset management, etc. without affecting existing systems.
List of representative functions of DPI products
| function | Overview | Purpose of use |
|---|---|---|
| Baseline setting |
A function that learns normal communication within the system as a baseline and detects communication that deviates from that as an anomaly. |
It is used to comprehensively detect anomalies in building systems at the network level. |
| threat intelligence | A signature prepared by a manufacturer to detect attacks that can pose a threat to building systems and dangerous situations that can lead to attacks. | By using it in combination with the baseline setting, it is used to notify the user of the content of the detected abnormality in more detail. |
| network mapping | A function that maps each device on the network configuration diagram and displays it along with the communication direction and the role of each device. | It is used to identify and restore damaged devices in the event of an abnormality, and to determine risks in network configuration. |
| Asset management | A function that creates a list of detailed information such as the vendor name, communication protocol, firmware version, etc. in addition to the IP address and MAC address of each device. | It is used as an asset ledger to check the information of each device at the time of cyber attack damage or maintenance / maintenance. |
| Dashboard | A function that displays information acquired by DPI products, such as the content of detected alerts and traffic volume, in tables and graphs. | ビルシステムの現在の状況や過去からの推移状況を表やグラフで可視化する為の機能。 |
Download the white paper for detailed measures
A guide to cyber security measures for everyone involved in building systems
~It will not be enough after being exposed to the threat~
*This white paper was published in the June issue of Ohmsha, a practical magazine for building equipment.
Solution: Network-monitored secure building
Benefits of eyeInspect (formerly SilentDefence)
- network visualization
Identify and manage devices and communications within the system, including vulnerability information. - Anomaly detection
By learning and monitoring normal communication, and combining whitelist and blacklist, unknown and known anomalies can be detected at an early stage.
The above is achieved with a passive configuration that does not load the network.
In the "Guidelines for Cyber-Physical Security Measures for Building Systems" formulated by the Ministry of Economy, Trade and Industry, in building systems, possible security incidents, their risk sources, and security policies for them are organized, and attached as "Security Measures Considering the Life Cycle" It is published.
Macnica has summarized how ForeScout's eyeInspect (formerly SilentDefence) solution satisfies each of the above countermeasures, so please take a look.
Ministry of Economy, Trade and Industry Building System Guidelines Correspondence Table
~Using eyeInspect (formerly SilentDefence)~
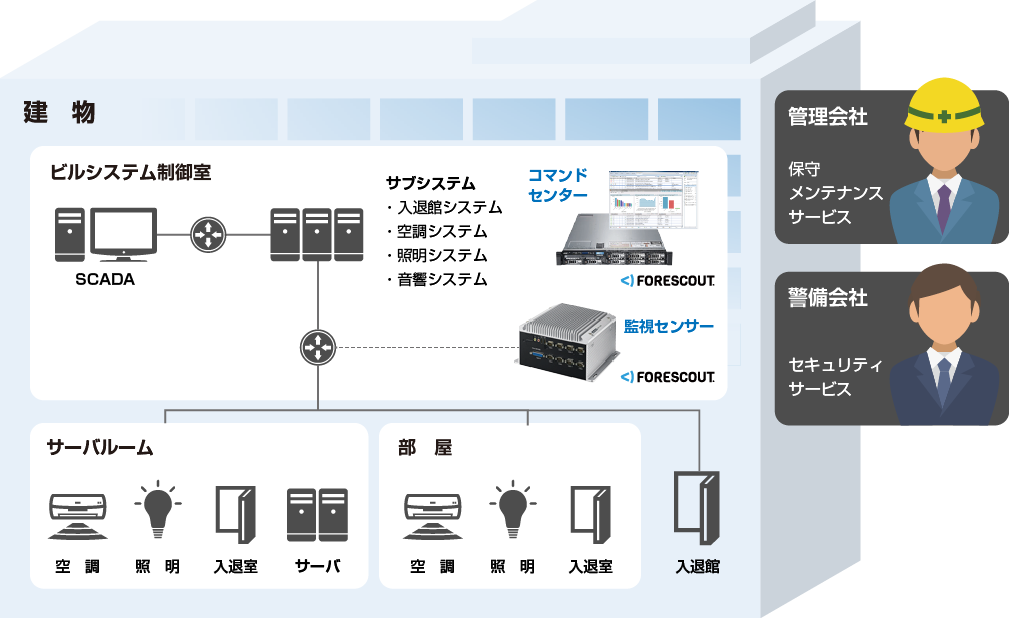
Solution: Physical Device Visibility Option
Macnica Physical Finder
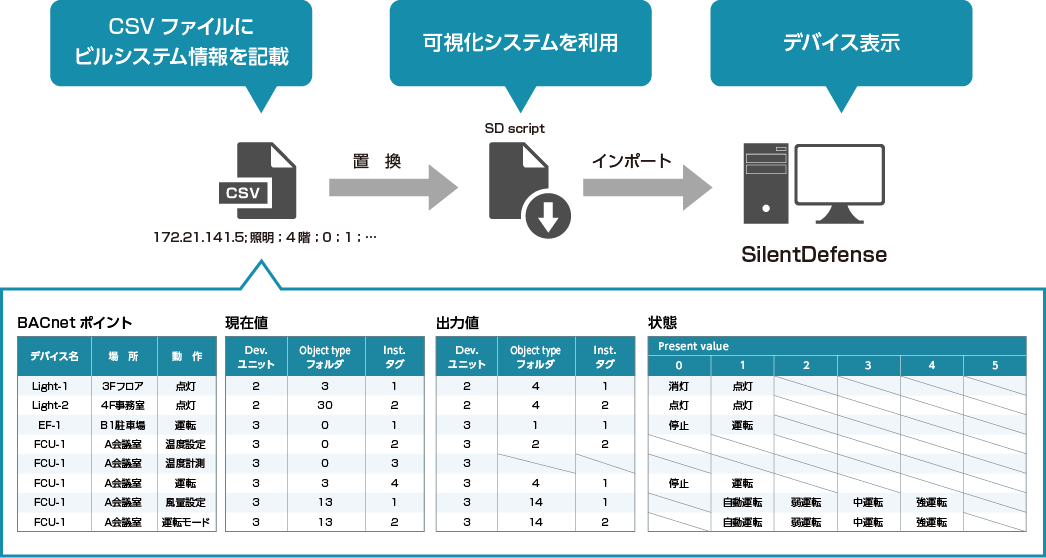
BACnet による操作対象となる物理デバイスをeyeInspect(旧SilentDefence)上で可視化するシステム(Macnica Physical Finder)をマクニカにて開発し提供しております。
Solution: Introducing Assessment Service
meeting

Installation, communication analysis

Result report, purchase consideration
*We may provide this service in collaboration with our Macnica sales partners.
report image

Optimal measures for building systems
Download the white paper for more information
A guide to cyber security measures for everyone involved in building systems
~It will not be enough after being exposed to the threat~