Do you have any concerns about factory security measures?
- Uncertainty about whether our factory is safe
- I don't know what to do about factory security
- IT, OT, and IoT coexist in an environment, but we want to implement security measures without spending unnecessary costs.
- There are many standards and guidelines, how should I comply with them?
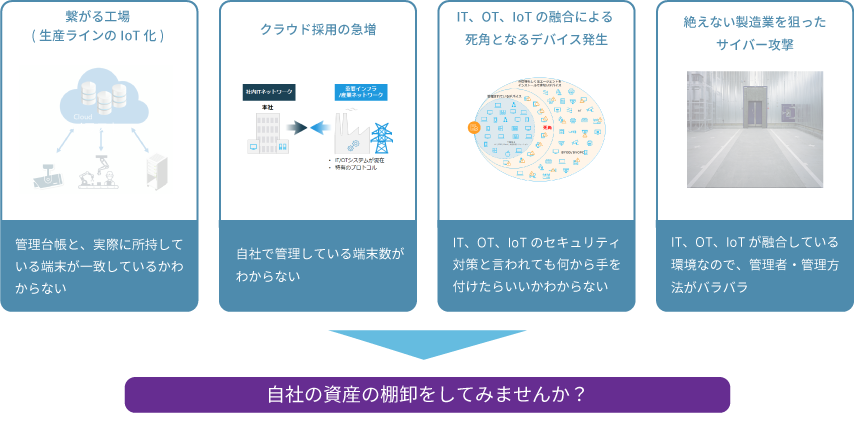
With smart factories, there are more opportunities for factories that were not connected to the outside to connect with the outside. In addition, in the manufacturing industry, the use of various devices such as IoT and the shift to DX using data are accelerating.
On the other hand, cyberattacks targeting the manufacturing industry, which tends to affect the entire supply chain, are increasing, and there are many cases where even major manufacturing companies have suffered damage such as factory shutdowns and ransom demands.
In addition, terminals installed in factories may not be updated with OS and applications to ensure stable operation, making them more susceptible to cyberattacks.
Security is not limited to the IT field, but the importance of factory security measures is being recognized again these days. Before your factory is attacked, you need to effectively and safely implement the best security measures for your manufacturing environment.
Factory security 3 steps and solutions
The basics of factory security are the same as general IT security measures, but here we will introduce three steps to get started with factory security.

STEP1 Asset grasp
Do you have an accurate grasp of the assets under your control? As the first step in security measures, it is necessary to understand the current situation.
Identify the importance of assets from information assets, physical assets (terminals, etc.), system diagrams, and data flow diagrams in the target range.
By grasping the current company assets and determining the priority of assets to be protected, it is possible to implement correct security measures without omissions.
Macnica provides agentless solutions that can accurately and in real time visualize various IT/IoT/OT devices connected to the network. Identify coverage and gaps across your digital environment, and see in real time which locations and devices are targeted for attack.
STEP2 Risk assessment
Once the assets to be protected within the target scope have been identified, a risk assessment is conducted based on the threats to the assets, their importance, and the likelihood of occurrence, identifying threats and prioritizing responses.
Threat information depends not only on individual systems, but also on what industry the factory being analyzed belongs to and how it is operated, so a high level of security knowledge is required to detect threats and assess risks. increase.
At Macnica, we provide highly accurate risk assessment services by combining our security expertise with the experience we have gained from providing support to factory customers.
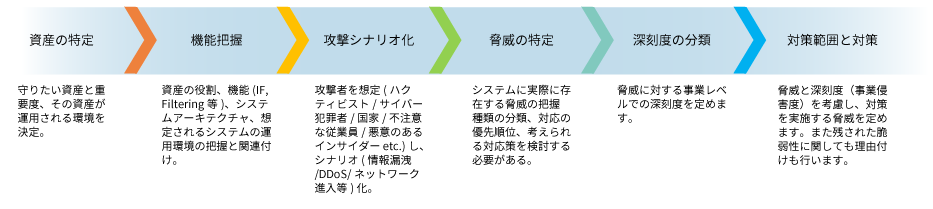
STEP3 Examination and implementation of countermeasures and monitoring
We consider and implement optimal countermeasures based on the risk assessment conducted in STEP2.
At manufacturing sites, it is necessary to protect "safety", "continuous operation" and "quality", so it is necessary to take countermeasures that do not affect these and are operable on site. In addition, security measures are not finished once they are introduced.
In order to continuously maintain the safety of the factory, it is necessary to divide the realization of audit items into short-term and medium-term, create a roadmap, and consider the optimal audit infrastructure and operation.
At Macnica, we provide comprehensive support through consulting based on risk assessment results, from determining the security measures that should be introduced, to considering the optimal operational method that suits the customer's system, to realizing efficiency and labor savings. Masu.
Please feel free to contact us as we will support the most suitable factory security measures for our customers.
