Specifications/Technical Information
Application for evaluation machine
- FAQ
I tried implementing Prisma Cloud's CSPM: Report function

In our previous feature article, we introduced the process from visualizing an alert to identifying the cause.
Of the CSPM (Cloud Security Posture Management) features available in Prisma Cloud, we will focus on the reporting feature this time.
Previous blog link
1. About Prisma Cloud CSPM
First, a quick rundown of what Prisma Cloud CSPM is: Prisma Cloud is an integrated platform for addressing security and compliance challenges in cloud environments. The CSPM feature is a solution for monitoring and reporting on excessive privileges, misconfigurations, and compliance with security policies and regulatory requirements for your cloud infrastructure.
2. Report function
The reporting function plays an important role in Prisma Cloud's CSPM. By simply checking the reports that are output periodically without accessing the GUI, you can understand the general issues, the affected assets, and how to deal with them. Another strength of Prisma Cloud's reporting function is that it can output only the necessary content and send it periodically to those who need it.
It can also output reports that can be used to share information with management, ranging from a summary of alerts that developers need to take note of to status of adherence to specific compliance policies.
For example, instead of checking a single alert individually, you can check all alerts within a certain period of time at once, which is very useful when you need to submit or save alerts within a period of time for routine work or audit purposes. By sharing only the necessary alert information, you can create a system that encourages action without issuing access IDs to the GUI for each person in charge, people in other departments, or cooperating companies.
Specific benefits of the report can be summarised as follows:
- Compliance monitoring:
At a glance, you can see whether your cloud environment is complying with security policies and regulatory requirements. - Risk Identification:
You can mitigate risk by identifying activities and configurations that violate security policies and regulatory requirements. - Guidelines for improvement:
It provides remediation for identified issues and offers guidance for improving security and compliance.
3. Trying out the report function
There are three types of reports that can be output with Prisma Cloud, and each one can be used for different analysis purposes.
- Cloud Security Report:
It allows you to check how much Prisma Cloud functionality is being used and what kind of security is being applied. It also helps you understand the trends of alerts that have occurred over a certain period of time. This is the most summary-based report of the three types. - Compliance:
It helps you select a specific compliance policy and understand how well you are complying with it. You can view a summary of the selected compliance policy and any current alerts for it. - Alerts:
You can specify a specific environment and output open alerts for it. You can check the total amount and content of alerts for each environment that each person in charge needs to handle without checking the console.
1. Generate reports
This time, I would like to check the extent to which the AWS account in the test environment complies with CIS Benchmark v1.3.0.
- Select "Cloud Security" from the tab at the top left of the screen and click "Reports" at the top.
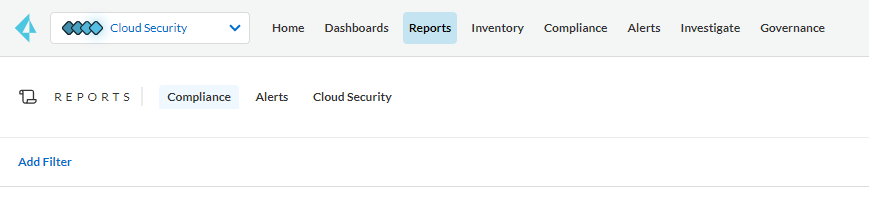
Figure 1. Reports screen
- Select the report you want to create from Create Report. In this example, select Compliance.
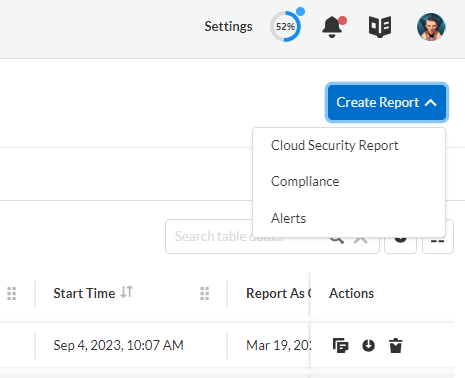
Figure 2. Select the report you want to generate
- Here, select which compliance you want to report on. In this example, select CIS v1.3.0 (AWS).
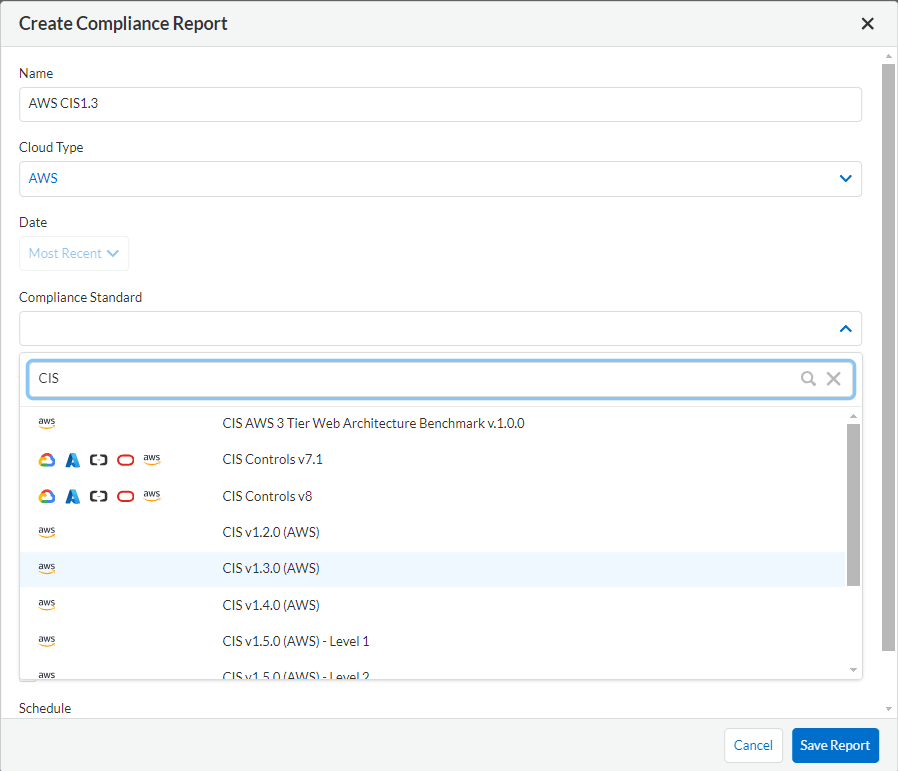
Figure 3. Compliance report advanced settings screen
- You can also send reports on a regular basis by entering an email address and setting the Schedule to Recurring.
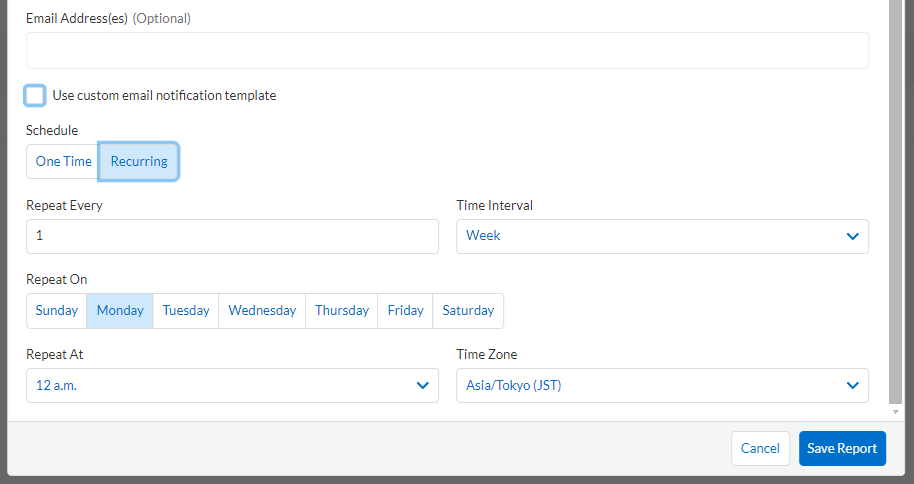
Figure 4. Setting screen for periodical sending to email address
- The settings are now complete. When I clicked the Download button for the report, it was downloaded immediately. Let's take a look at the report that was actually generated.
2. Analyzing the report
Now let's analyze the report.
- Regarding the structure of the report, if you check the downloaded PDF file, you will see that it is arranged in order from the cover to the table of contents, allowing you to access the necessary items at a glance.
Figure 5. Table of contents page
- The Executive Summary shows the number of violating resources (Failed) and the problematic items at a glance. In this case, it appears that three items other than Storage are violating the policy.
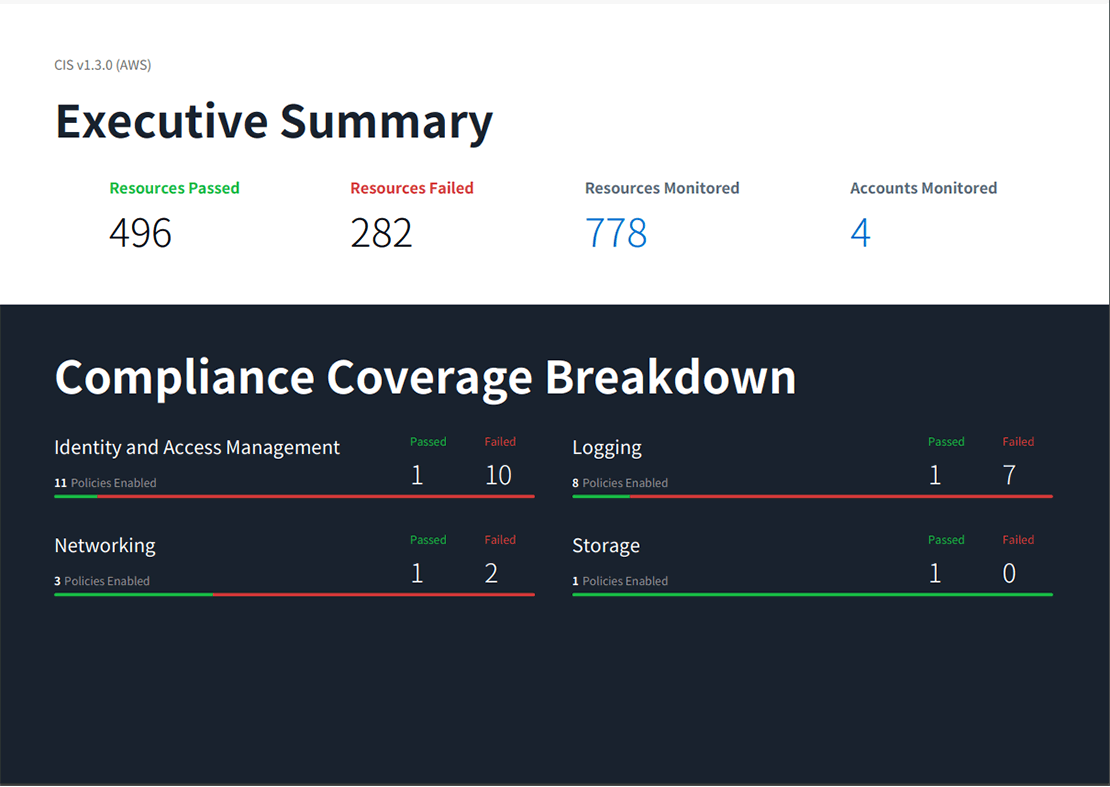
Figure 6. Report overview page
- Next, a details page has been created for each of the four items mentioned above, making it easier to grasp the overall picture. This time, I would like to take a look at the overview of Identity and Access Management. The number of violations for each policy is summarized, and if all of the policies are marked as Failed here, you can use this as material to consider whether the policy should be enabled in the first place.
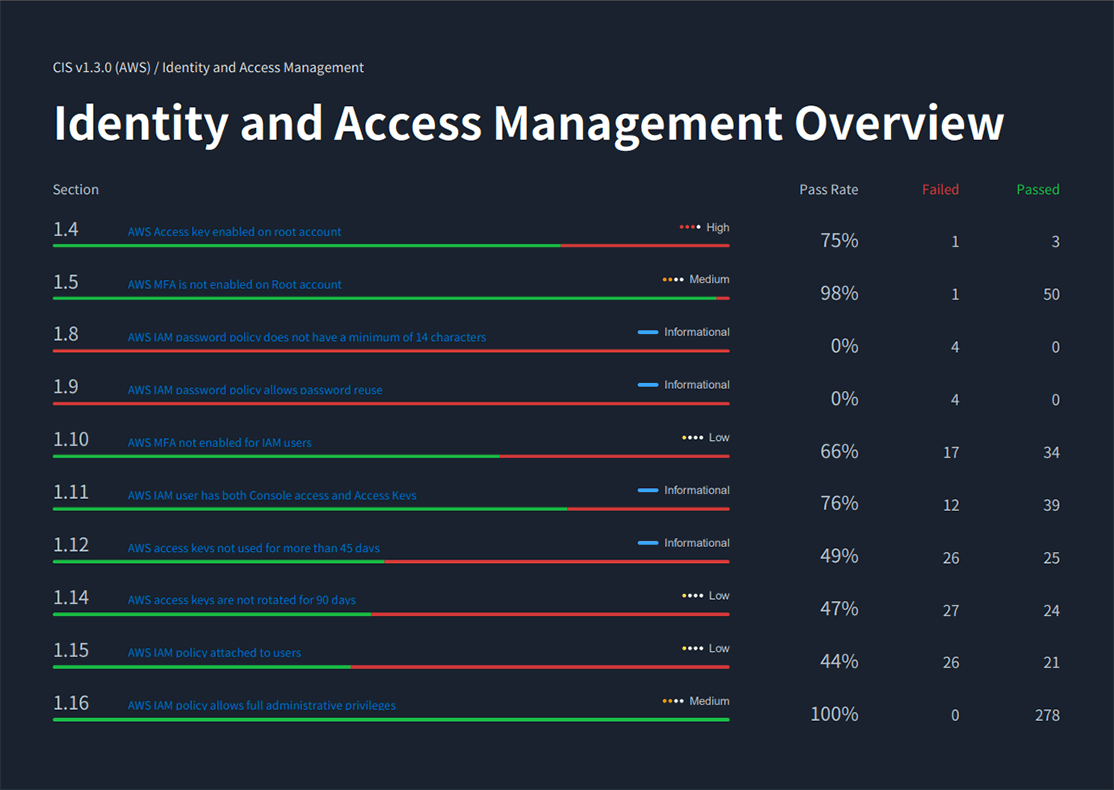
Figure 7. Identity and Access Management Overview page
- The next page displays an overview of each policy, recommended configuration methods, and the names of violating resources, all on one page. Unlike the console, there is no need to switch screens, so it is possible to complete the response just by looking at this page. Links on the page take you to the Prisma Cloud GUI, making this a useful report for those who actually respond to alerts.
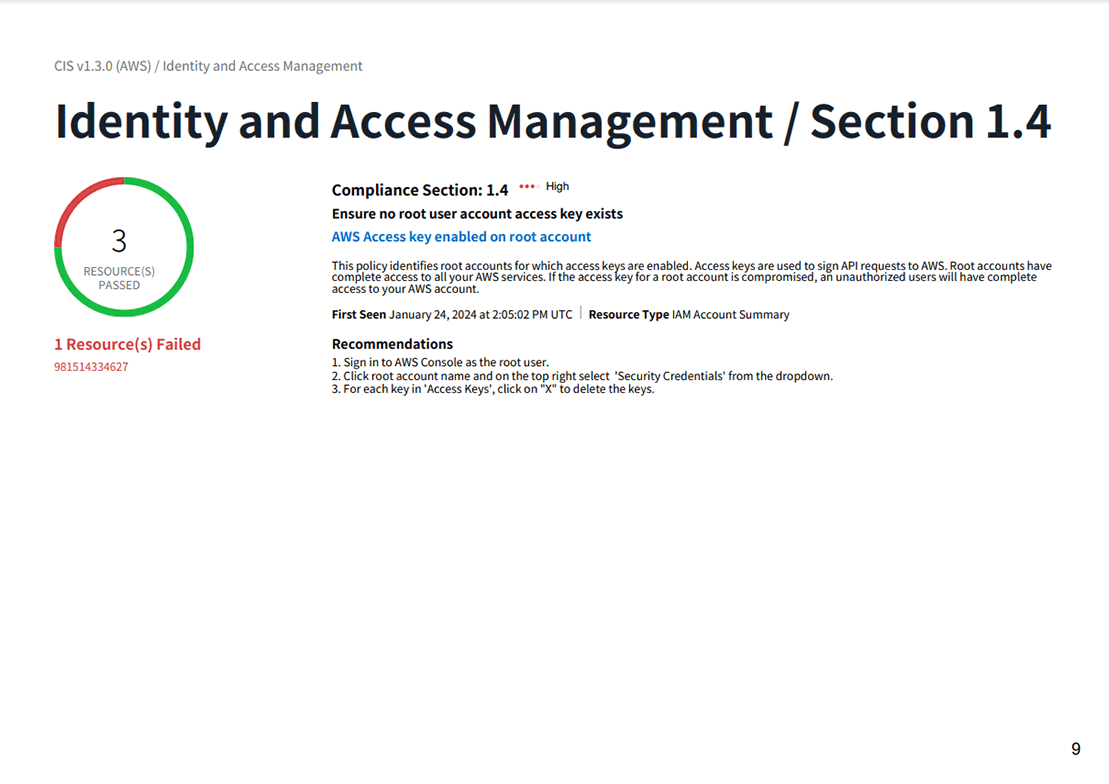
Figure 8. Policy details page
- Since this was a testing environment, there were a large number of violations, but we were able to see at a glance which part had the violation and what action to take, which demonstrated how easy it was to use.
Summary
In this article, we have written about implementing the Prisma Cloud reporting function and reviewing the actual reports. The Prisma Cloud reporting function is a valuable tool for clearly showing compliance with security policies and risks in cloud environments and for proving compliance with audits and regulatory requirements.
As companies rapidly make use of the cloud, it has become increasingly difficult for a specific department to exercise overall control alone. However, by utilizing this function, you can easily generate the information required for cloud security audits and provide the necessary data, which can then be used to set up operations in which each relevant party and department can respond to alerts autonomously. This is a very effective method, so please consider using it.
Related video: "Achieving Secure Application Development -Improving Security Baselines with Posture Management-"
Providing a secure work environment for employees is a common challenge for all businesses. Suppression of security incidents is also recognized as a major issue in application development sites, but there are situations in which developers have to lower the priority of security due to unique reasons, and the importance of security is neglected. is not uncommon. In this session, we will explain Posture Management, a preventive solution for implementing the minimum mechanism necessary to reduce the probability of security incidents in the development environment and significantly improving the security baseline.
Inquiry/Document request
In charge of Macnica DevOps
- TEL:045-476-1972
- E-mail:twistlock@macnica.co.jp
Weekdays: 9:00-17:00


