AWS Fargate環境に適用できるコンテナセキュリティって?

ここ最近、AWS Fargate環境を採用されているお客様からコンテナセキュリティの実装に関するお問合せを頂くことが非常に多くなってきました。既にAWS Fargate環境でPrisma Cloudを利用したコンテナセキュリティを実装されているお客様もいらっしゃいますが、改めてAWS Fargate環境に対してどのようなセキュリティ実装が可能なのか?をお伝えたいと思います。
AWS Fargateのメリット
ご存知の方も多いと思いますが、AWS Fargateとは何か・そのメリットから振り返りたいと思います。AWSのWebサイト上に詳しく記載されていますが、ポイントは以下だと考えています。
- コンテナのメリットを享受しながら、ホストOSやそこに紐づくミドルウェア等の構築が不要になる
- EC2インスタンスついて考慮しなくてもよい
- 需要に合わせたスケーリングも非常に容易
AWS Fargateを利用することで、本来必要なアプリケーション開発に集中できること、インフラレイヤの管理に対する特別なスキルセットや経験がなくてもよくなる点が、多くの企業で採用が広がっている理由かと思います。
AWS Fargateにどのようなセキュリティを実装できるのか
AWS Fargateの利用により、インフラレイヤの様々な要素を考慮する必要がなくなりますが、セキュリティリスクへの対処を全く考慮しなくてよい訳ではありません。例えば、AWS Fargate上で実行するコンテナイメージは利用者にて作成するため、そこに脆弱性やコンプライアンス違反が発生する可能性があります。また、AWS Fargate上で実行されているワークロードに対して、外部から攻撃が発生するリスクは当然生じます。
そこで、Prisma CloudではAWS Fargateに対して、主に以下のようなセキュリティ機能を提供します。
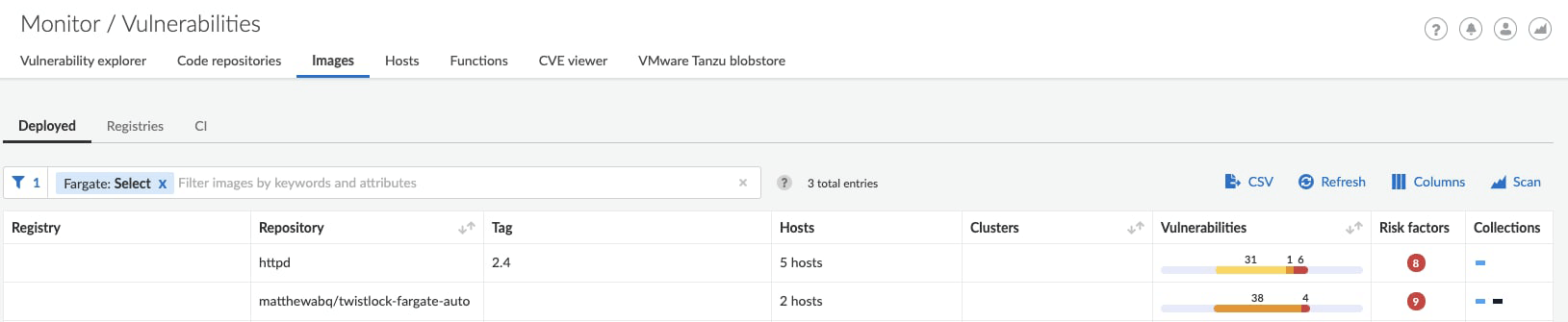
- コンテナイメージの脆弱性スキャン
Fargateタスクをスキャンしてコンテナイメージに含まれる脆弱性を自動的にスキャンさせることができます。これにより、セキュリティ重要な脆弱性が含まれたままコンテナが動作し続けることを防ぐことができます。
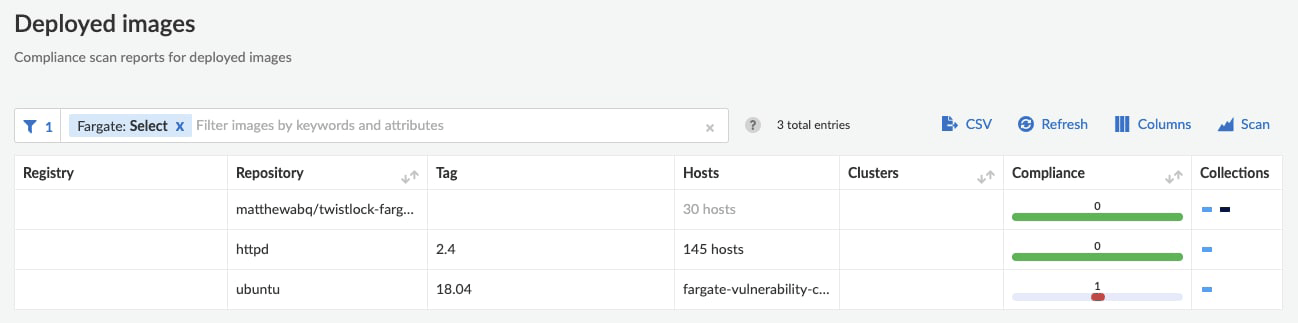
- コンプライアンススキャン
Fargate環境に対して適切な定義済みルールセットを用いて、コンテナイメージのコンプライアンスチェックを行うことができます。これによって、コンプライアンス(例えば、コンテナ内にPrivate Keyが含まれていないか、SSHログインができる状態になっていないか、マルウェアを含んでいないか等)を保った状態のイメージを利用し、無用なセキュリティリスクを排除することができます。
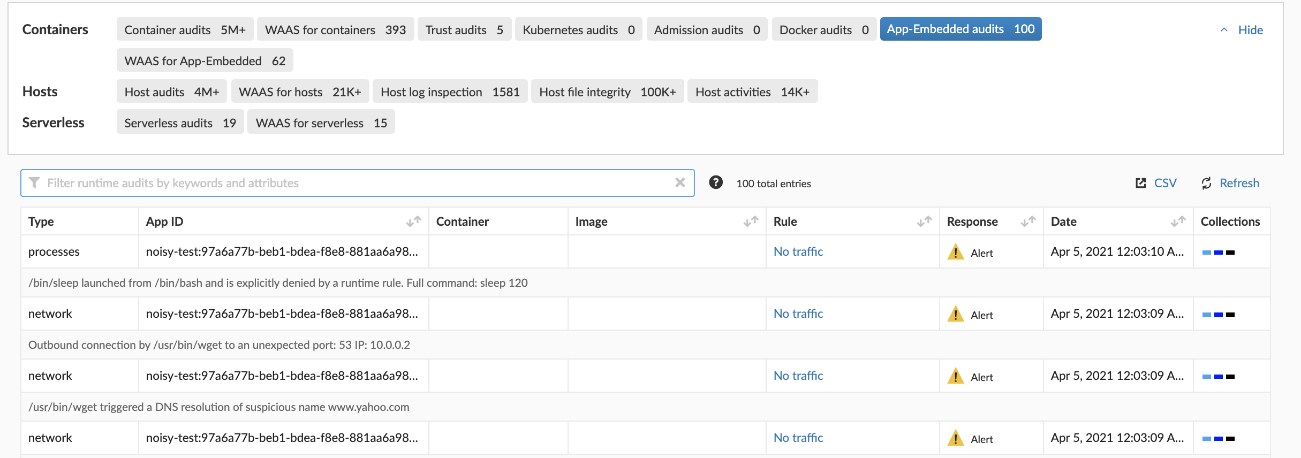
- ランタイム防御
サイドカー方式で配置されるFargate用のDefenderによって、コンテナが定義された通りの動作をしているかをモニタし、もしポリシー違反となるような動作を検出した場合に通知・自動対処を行うことができます。また、Prisma Cloudで提供されているWeb Application and API Security(WAAS)機能によって、Fargate上で実行されているコンテナへのリバースプロキシとして、流れてくるトラフィックを検査し、設定したポリシーに従ってL7レベルのセキュリティ実装をシームレスに行うことができます。これにより、OWASP Top 10といったWebアプリケーションのセキュリティリスクからFargate環境を保護することが可能となっています。
AWS FargateへPrisma Cloudを実装する際の構成
Fargate環境を保護するために、通常のDefenderとは異なるApp-Embedded Defenderを利用しますが、これはFargateタスクで実装します。(Prisma Cloudのコンソール上やAPIでタスクを自動生成することが可能です)生成したタスクにはPrisma Cloudサイドカーコンテナが含まれており、これがポリシーの取得や監査結果の送信など、コンソールとの全ての通信を処理する形となります。
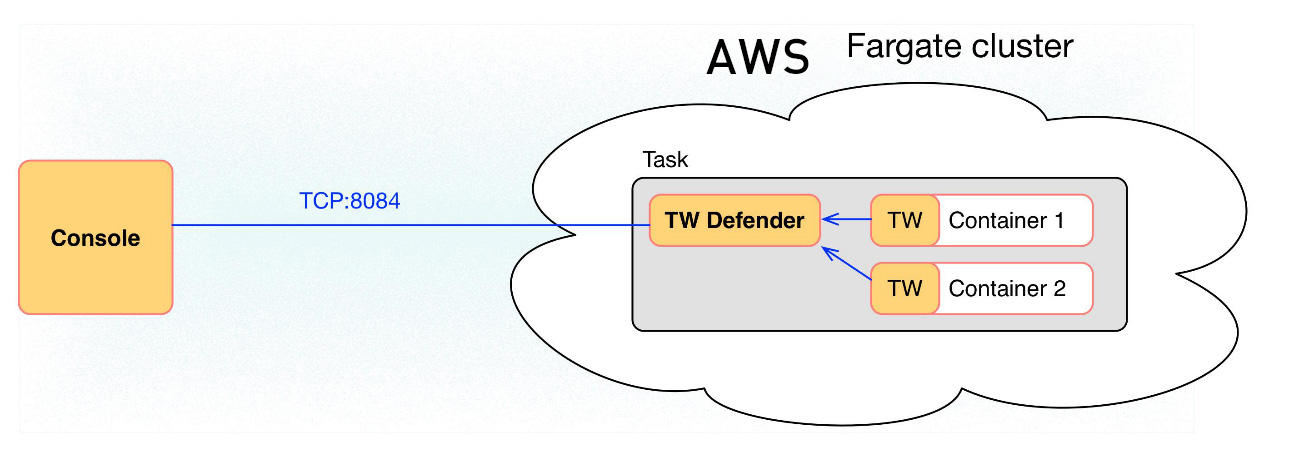
画像:https://docs.paloaltonetworks.com/prisma/prisma-cloud/21-04/prisma-cloud-compute-edition-admin/install/install_defender/install_app_embedded_defender_fargate.htmlより引用
まとめ
Prisma Cloudを利用することによって、AWS Fargateの様々なメリットを享受しながら、対処すべきセキュリティ脅威から保護することができます。Fargateを既にご利用している/利用計画中でセキュリティ対策にご関心のある方は、ぜひお問合せください。
お問い合わせ・資料請求
株式会社マクニカ DevOps 担当
- TEL:045-476-1972
- E-mail:twistlock@macnica.co.jp
平日 9:00~17:00