
ULTRA RED
ultra red
EASM solution ~ Continuously detects critical vulnerabilities in externally disclosed assets & proves attack opportunities ~
What is EASM (External Attack Surface Management)?
EASM (External Attack Surface Management) is a system that continuously monitors poorly managed servers and network devices that are exposed to the outside world (External Attack Surface) in order to prevent attackers from infiltrating your organization. , an initiative to address vulnerabilities.
The top cause of recent major incidents is due to External Attack Surface.
In particular, attackers often target servers at overseas bases and group companies, where corporate security measures tend to be particularly lax, as well as servers set up by business departments without permission, and vulnerabilities are actually exploited. As the number of cases of serious damage is increasing, it is necessary to take immediate measures. EASM's efforts are to address these issues.
Features of ULTRA RED
ULTRA RED has its development base in Israel, one of the world's leading cyber powers, and provides military-grade security solutions developed by engineers from the Israeli military's world-class 8,200 cyber units. By leveraging the experience and knowledge cultivated by our cyber team and making full use of automated attack emulation technology, we are able to demonstrate the existence of vulnerabilities within an organization and the effectiveness of intrusions, and continuously manage them.
ULTRA RED has the following features compared to other EASM solutions, and provides asset managers with appropriate information and response procedures, allowing them to make decisions based on real risks. .
- Risk detection from an attacker's perspective
Using the same TTP (Tactics, Techniques, Procedures) as an actual attacker, it accurately presents possible points of intrusion and attacks. By clarifying points that should be prioritized and automatically detecting risks in advance, it is possible to take countermeasures from an advantageous position over attackers. - Prioritize vulnerability response based on real risk
It is possible to understand the priority of response by scoring vulnerabilities on a scale of 1 to 5 based on the severity of threats backed by attack emulation. - CTEM (Continuous Threat Exposure Management) platform that integrates three technologies
By combining not only EASM, but also attack emulation technology (ABAE) using technology cultivated in cyber warfare, information (CTI) including the Dark Web, Deep Web, cyber criminal forums and underground transactions, etc. Address key points and weaknesses in vulnerability and threat exposure management
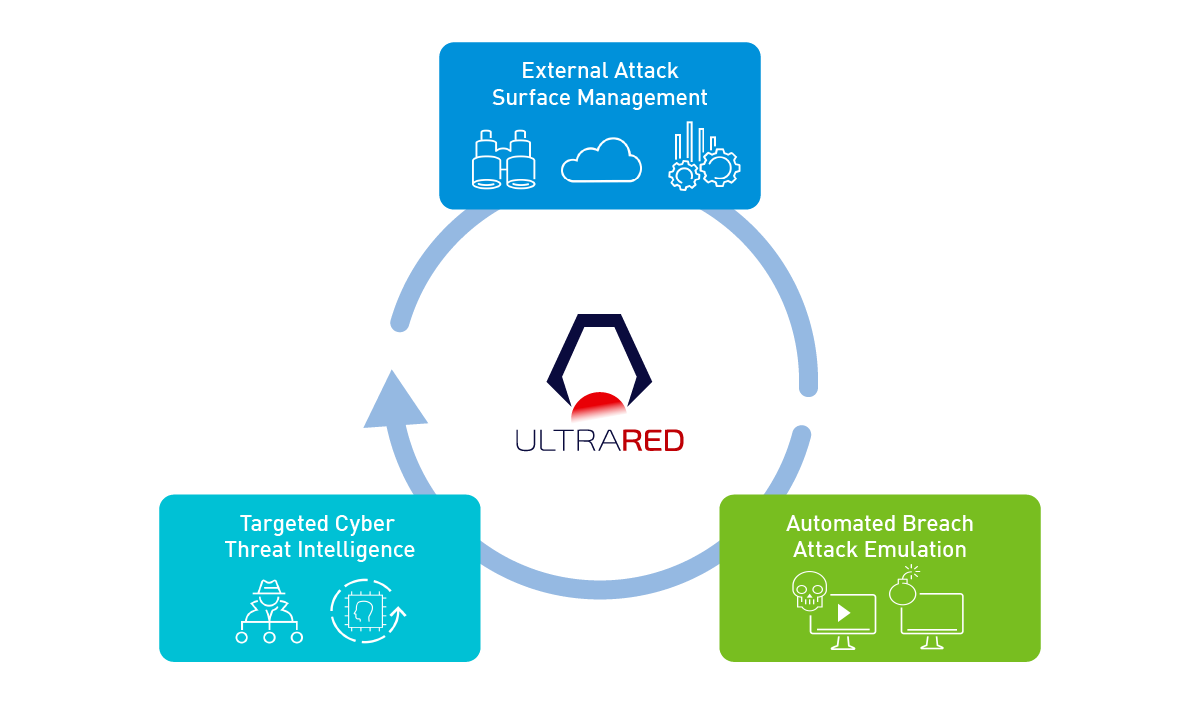
*1 Understanding and managing external areas that may be subject to attacks (EASM: External Attack Surface Management)
*2 Attack emulation (ABAE: Automated Breach Attack Emulation) using technology cultivated in cyber warfare.
*3 Information including the Dark Web, Deep Web, cybercriminal forums, underground transactions, etc. (CTI: Cyber Threat Intelligence)
Case study
About ULTRA RED
ULTRA RED is a company that provides cybersecurity solutions software as a service (SaaS). By understanding external public assets and not only detecting vulnerabilities in your own organization, but also providing information on what steps to take to prevent external intrusions, your customers will be able to protect themselves from attacks. reduce the risk of leaking.
| company name | ULTRA RED Ltd. |
| Established | 2020 |
| location | Israel, Tel Aviv |
| representative | CEO Eran Shtauber |
| website | https://www.ultrared.ai/ |
Inquiry/Document request
Macnica ULTRA RED
- TEL:045-476-2010
- E-mail:ULR-info@macnica.co.jp
Weekdays: 9:00-17:00

