
ULTRA RED
ultra red
Discovery
automatic asset discovery
Comprehensive discovery of IT assets exposed outside the organization (Internet), including web servers, FTP servers, VPN servers, etc. By registering the seed domain that will be the discovery source, related domains will be automatically detected.
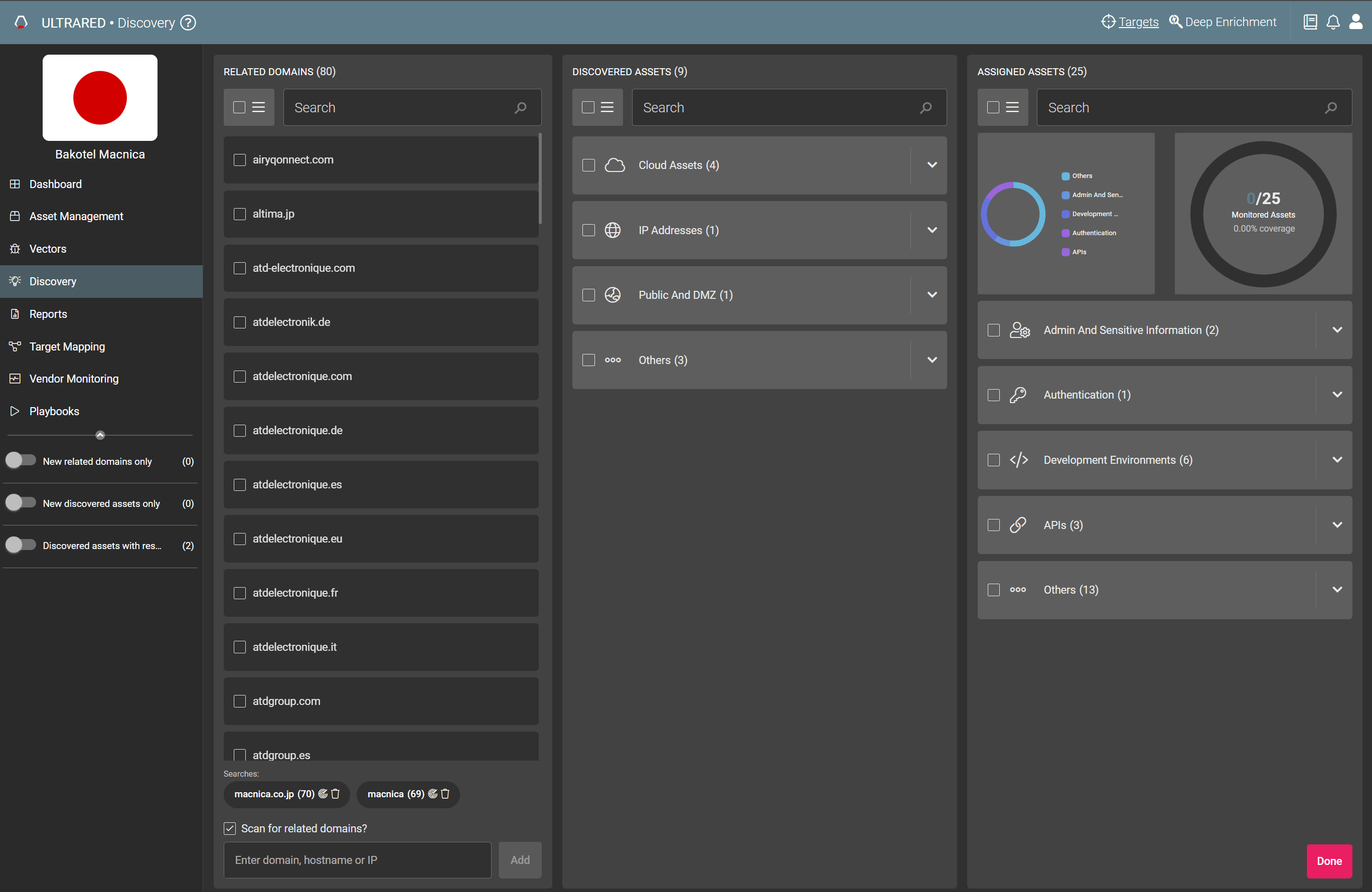
discovery chain
Information such as WHOIS information, DNS, and server certificates is used to detect assets.
You can check how the discovered assets were discovered.
Provides ease of determining the authenticity of your company's assets.
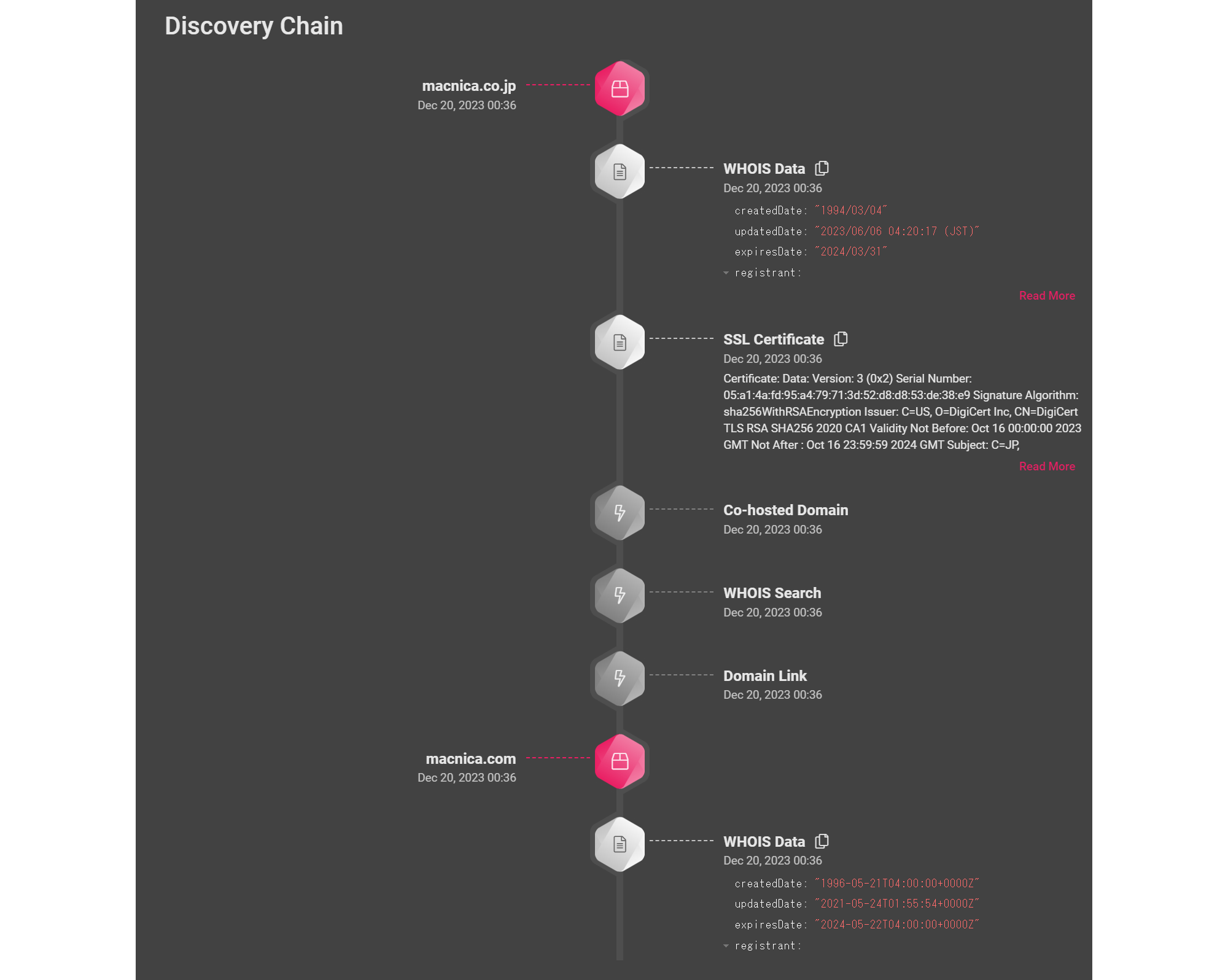
Asset Management
asset card
Manage various information used in discovered assets of your company. Visualizes various information such as the presence or absence of vulnerabilities in each asset, components used, versions of various software, open ports, etc. You can also tag information that cannot be confirmed from outside, such as the organization you belong to or related brands, with any name.
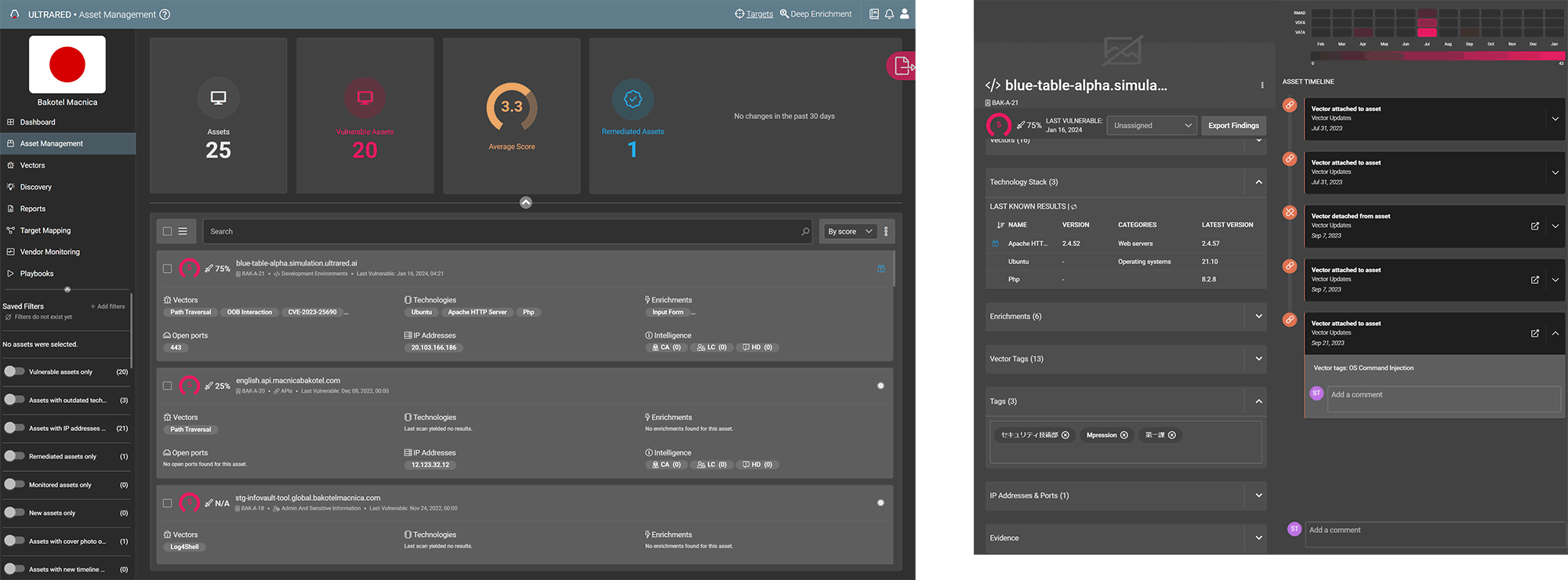
Filter function
Filtering by various information of visualized assets is also implemented. Instantly access the information you need, such as assets using specific components, assets with specific ports open, and assets with the same tag.
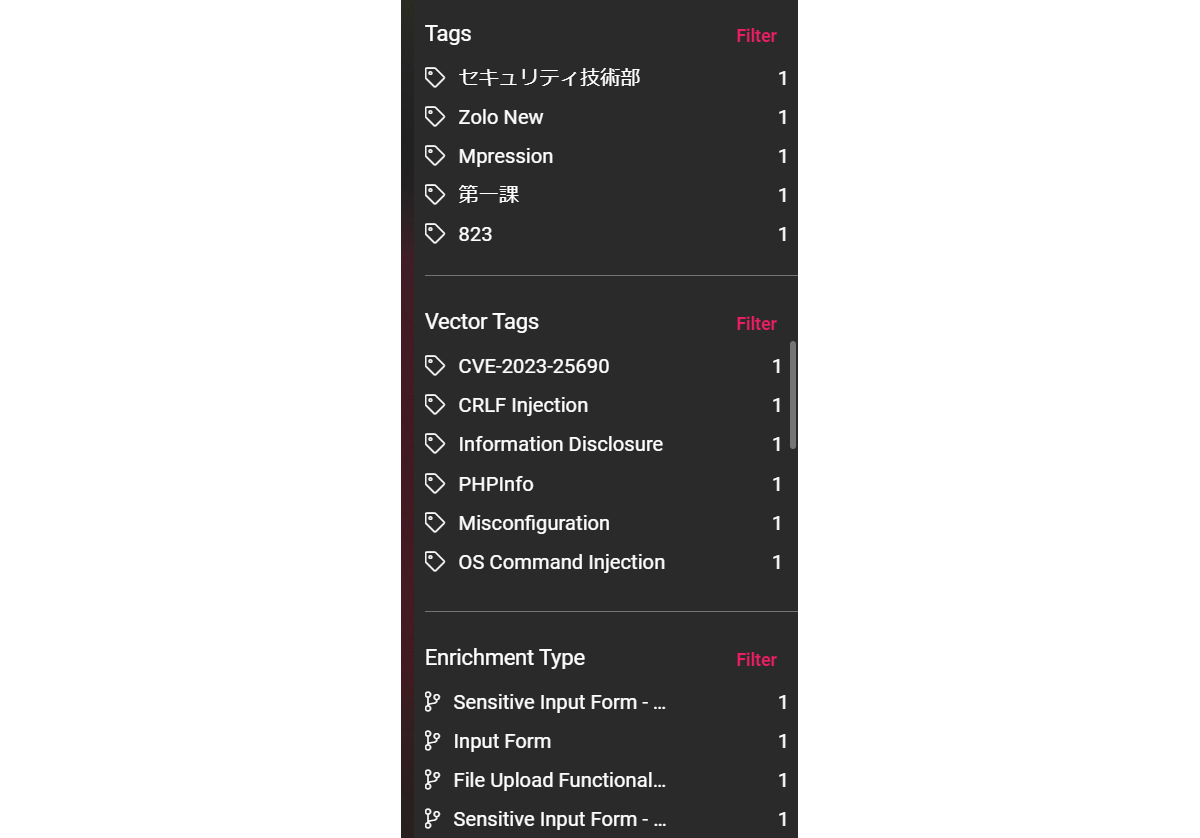
Vector
Verification by scanning
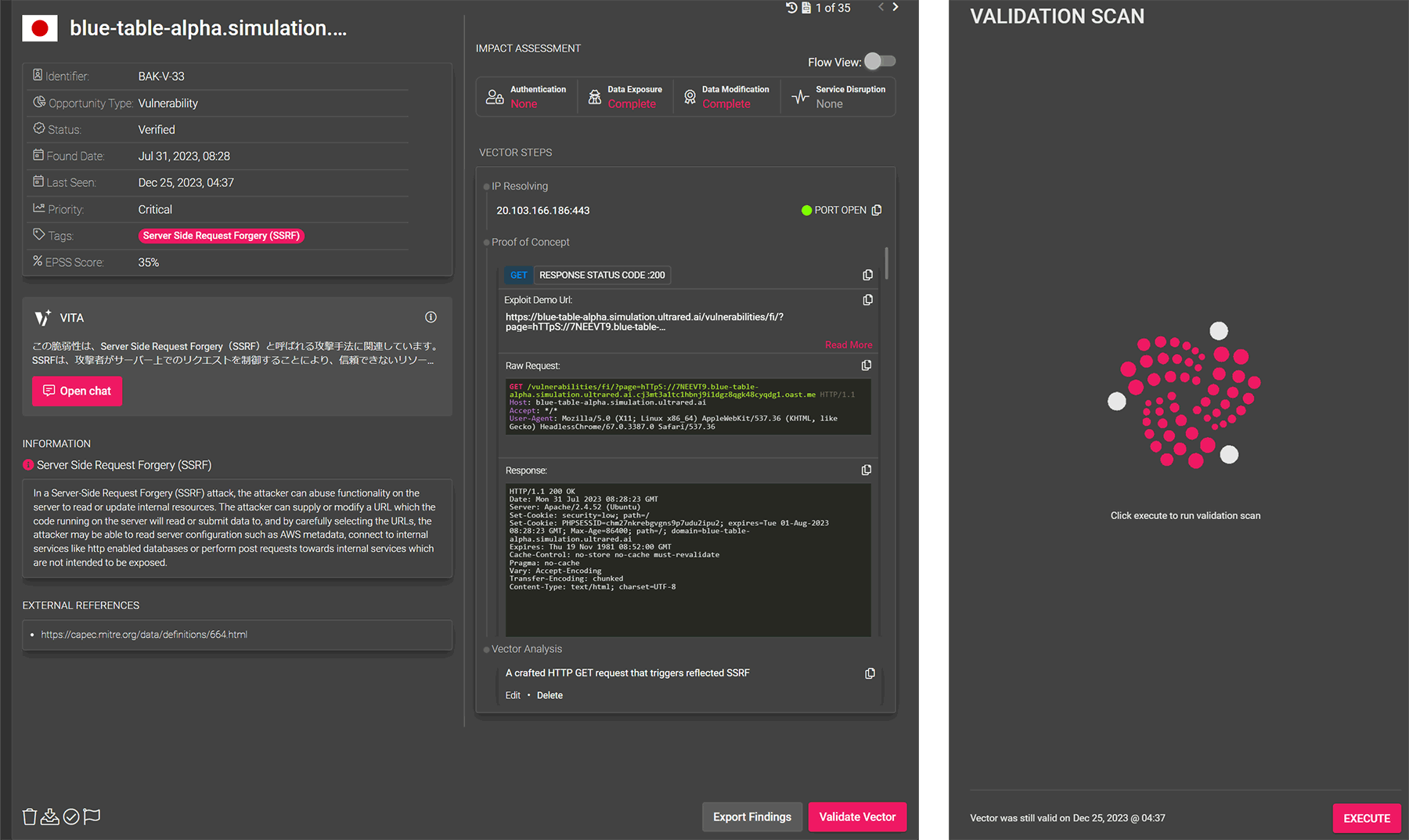
Externally scan managed assets with sanitized attack emulation. Visualize vulnerabilities and weaknesses in public assets from the same perspective as an attacker. By reporting only vulnerabilities that have been verified through scanning, we eliminate reports of vulnerabilities that do not actually exist (overdetection), where only the possibility is indicated based on version information.
Environment-dependent and configuration-dependent vulnerabilities
In addition to OS-dependent CVE, it is also possible to discover vulnerabilities that depend on the creation of web applications and the environment, such as SSRF and XSS. By automatically repeating scans every day, the health of your assets is always guaranteed.
rescan
Discovered vulnerabilities can be rescanned at any time. This eliminates the hassle of checking evidence after corrections and prevents incorrect corrections.
Providing priority
Provides response priority for discovered vulnerabilities. Prioritize not only by general indicators such as CVSS score, but also by ease of execution in the real environment (authentication, etc.) and impact if executed (data visibility, tamperability).
Inquiry/Document request
Macnica ULTRA RED
- TEL:045-476-2010
- E-mail:ULR-info@macnica.co.jp
Weekdays: 9:00-17:00