
Okta
Octa
Introduction
The number of unauthorized accesses to web services is increasing year by year, and even in the "Top 10 Information Security Threats 2022" announced by IPA, "theft of personal information" and "unauthorized use of credit card information" are ranked. doing. Attacks that exploit or target web services can take many forms, from small manually-operated attempts to large-scale brute-force and password-spray attacks. Service providers will be required to take countermeasures against various security attacks while ensuring the convenience of web services.
Auth0 provides various functions to prevent unauthorized logins as countermeasures against security attacks, making it easy to implement countermeasures against unauthorized logins in web services.
On this page, we will introduce the functions, settings, and behavior upon detection of four unauthorized login countermeasures (Attack Protection) provided by Auth0.
premise
The information on functions and settings described on this page is current as of August 2023.
Unauthorized login countermeasure function (Attack Protection) provided by Auth0
Auth0 has the following unauthorized login countermeasures called “Attack Protection”.
| Function name | Overview |
| Bot Detection |
Detect bot attacks (determined by Auth0 's knowledge) Conditions and examples of countermeasures Condition: A bot attempts to login/sign up/reset password Action: Additional request for CAPTCHA authentication (*) *You can use Auth challenge and Simple CAPTCHA provided by Auth0, or Google reCAPTCHA v2, reCAPTCHA enterprise, hCaptcha, Friendly Captcha, and Arkose Labs provided by other vendors. |
| Brute force protection |
Detecting repeated attempts to log in to a user Conditions and examples of countermeasures Condition: Consecutive login failures exceeding the threshold for the same user from a certain IP address Action: Block login for the user from the IP address + notify the user |
| Suspicious IP Throttling |
Detect frequent logins and sign-ups Conditions and examples of countermeasures Condition: Login failure exceeding the threshold occurs from a certain IP address within a certain period of time Action: Block login from the IP address for a certain period + notify the administrator |
| Breached Password Detection |
Detect logins and sign-ups for users who may have leaked information (determined by Auth0) ・ Breached Password Protection (no responsiveness) ・ Credential Guard (with responsiveness) Conditions and examples of countermeasures Condition: Login from a user who may have leaked information Action: Block login for the user + notify user / administrator |
*Available functions vary depending on the plan and options used.
Configuration example: Bot Detection
1. On the Auth0 admin screen, click Security > Attack Protection
2. Click Bot Detection
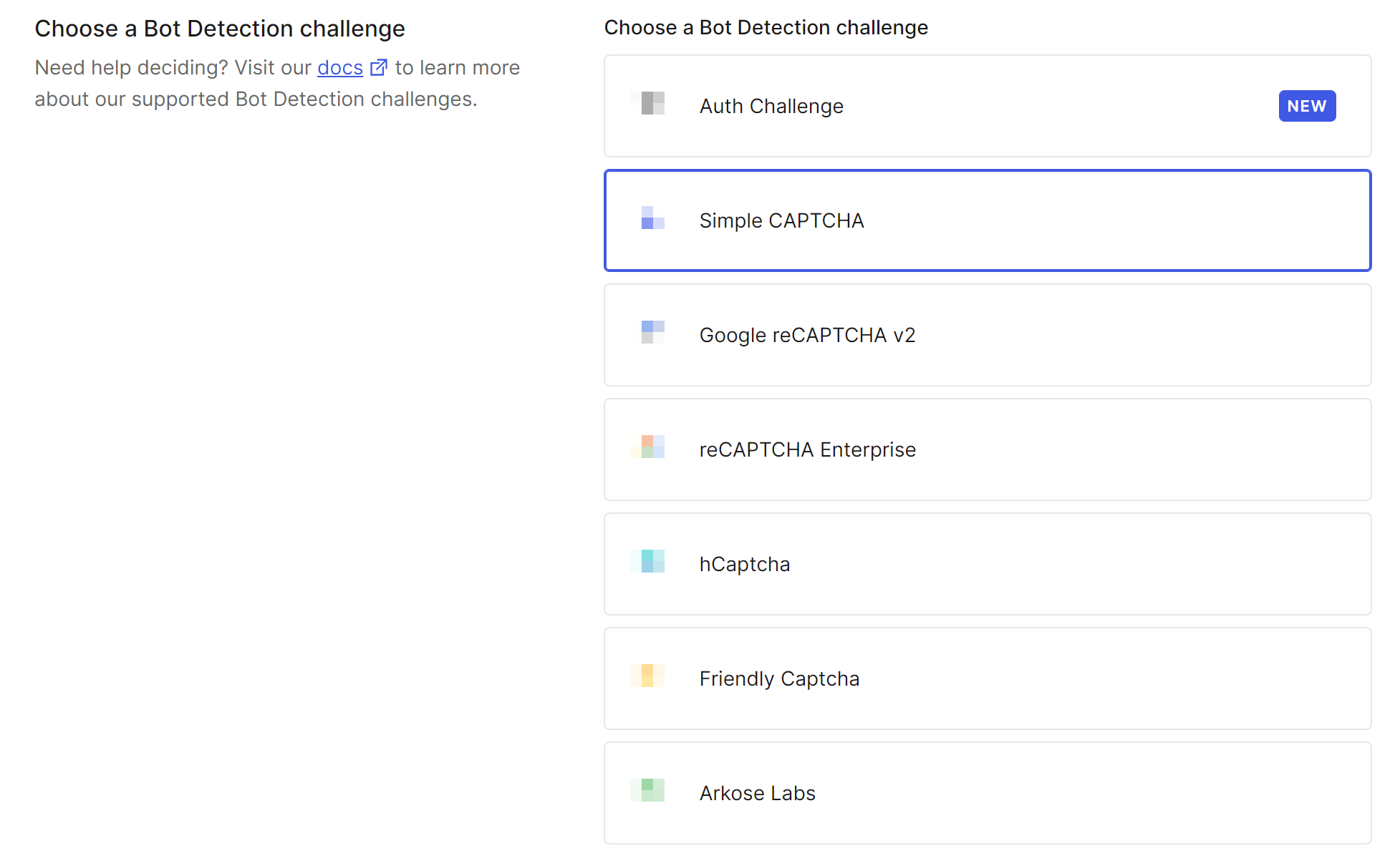
3. In the Choose a Bot Detection challenge section, select the CAPTCHA you want to use.
You can use Auth challenge (※1) and Simple CAPTCHA (※2) provided by Auth0, or Google reCAPTCHA v2, reCAPTCHA enterprise, hCaptcha, Friendly Captcha, and Arkose Labs provided by other vendors (separate registration with the vendor is required, and site key and secret, etc. must be set).
*1: A non-interactive verification method that distinguishes between humans and bots based on browser session data.
*2: An interactive verification method that has users input distorted characters to determine whether they are human or a bot.
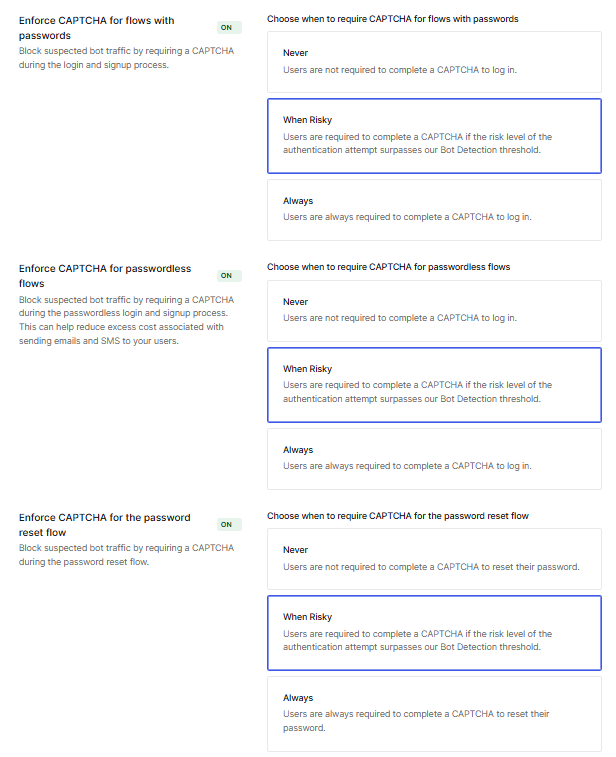
4. In the Enforce CAPTCHA section, select [When Risky] (this will require CAPTCHA authentication only if Auth0 determines that the access is from a bot).
*The top row is for password authentication, the middle row is for passwordless authentication, and the bottom row is for password reset.
5. Click [Save]
Example of detection operation: Bot Detection
If Auth0 determines access by a bot, additional CAPTCHA authentication will be required when logging in/signing up.
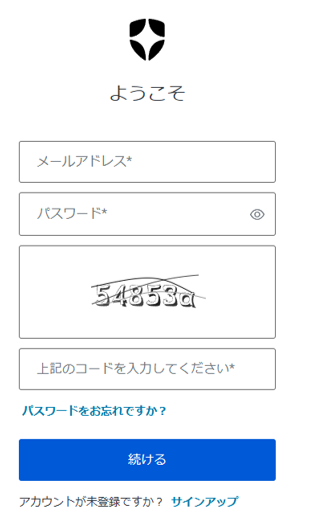
When using Simple CAPTCHA
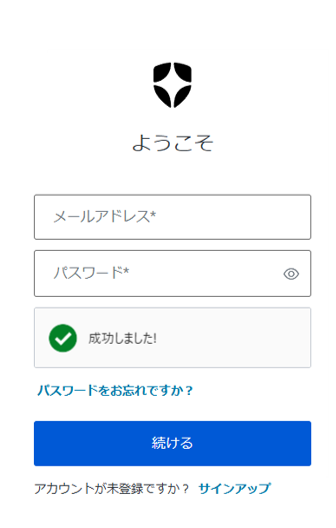
When using Auth Challenge
Configuration example: Brute-Force Protection
1.In the Auth0 admin screen, click Security > Attack Protection.
2. Click [Brute-force Protection]
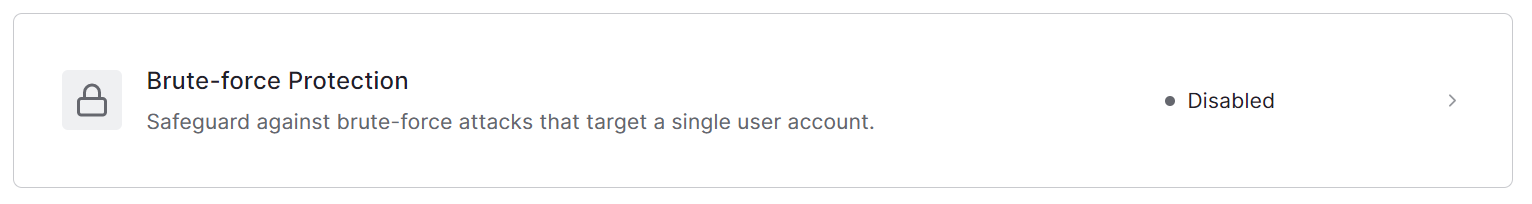
3. Enable Brute-Force Protection function
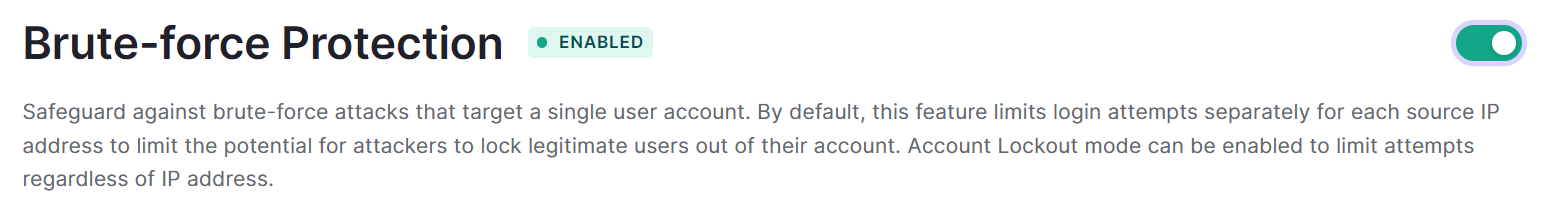
4.In the Detection and Response items, set the threshold for the number of consecutive unsuccessful attempts, networks not subject to detection, and actions and notifications when detected.
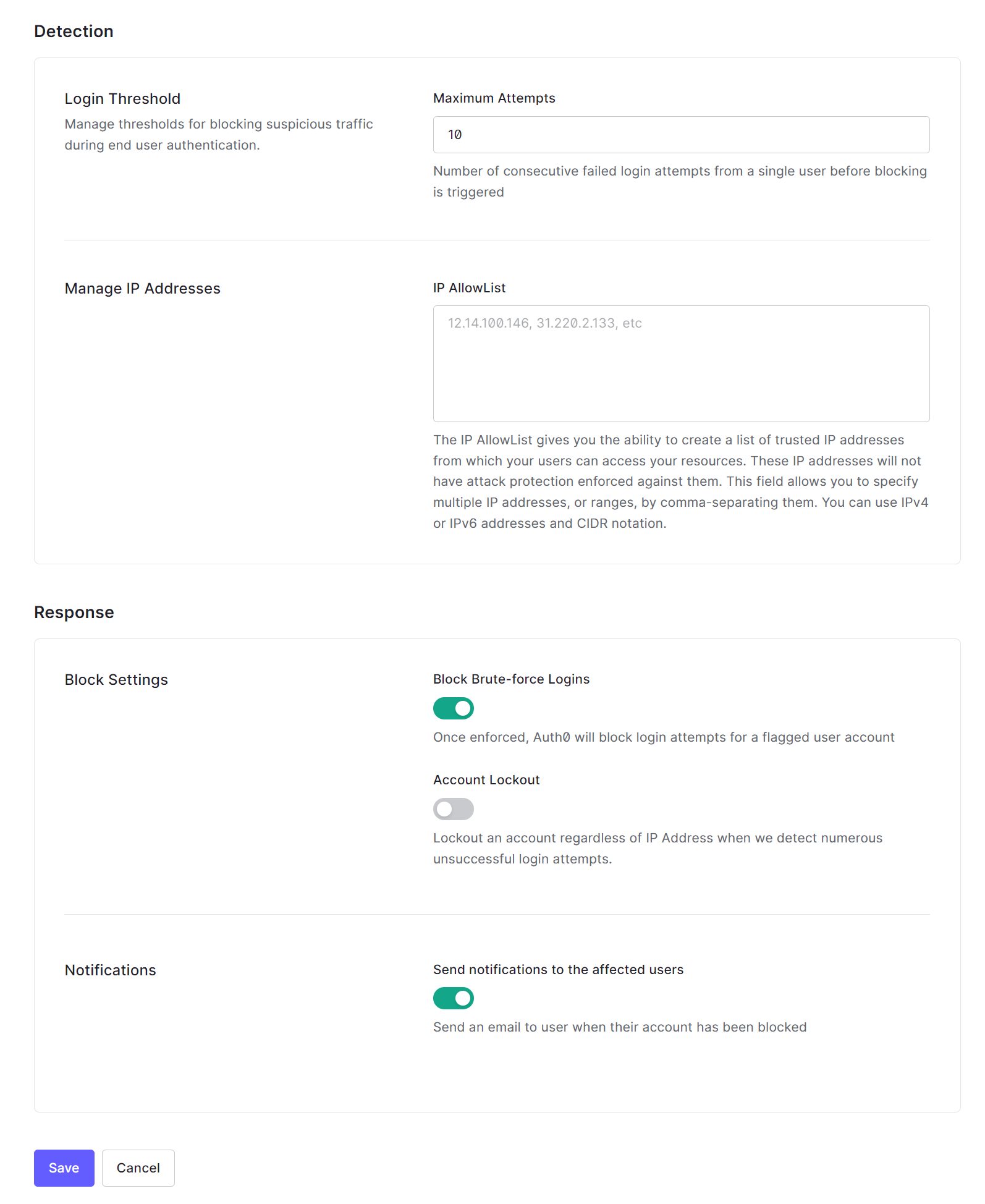
5. Click [Save]
Detection operation example: Brute-Force Protection
If consecutive login failures exceeding the set threshold occur for a certain user, a warning message will be displayed on the login screen when the user attempts to login. In addition, the user will be blocked or notified by email according to the detection action and notification settings.
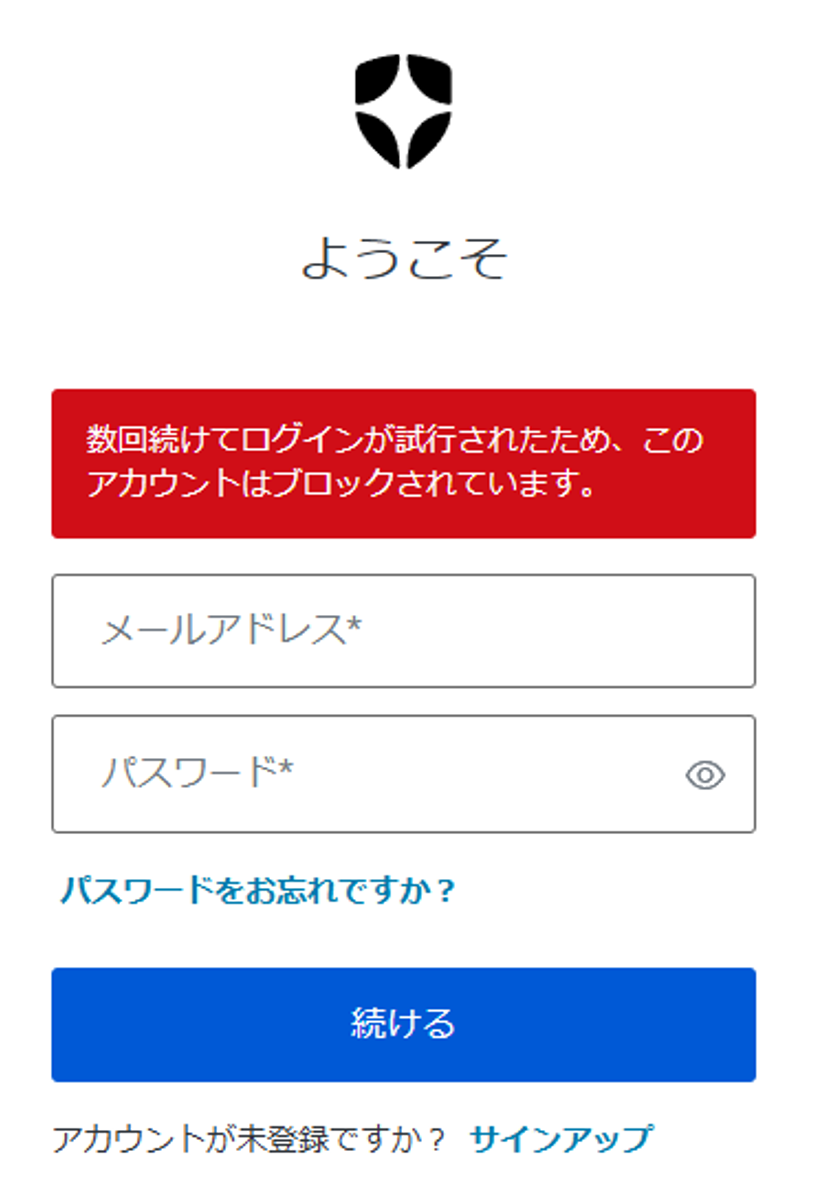
Login screen when Brute-force is detected
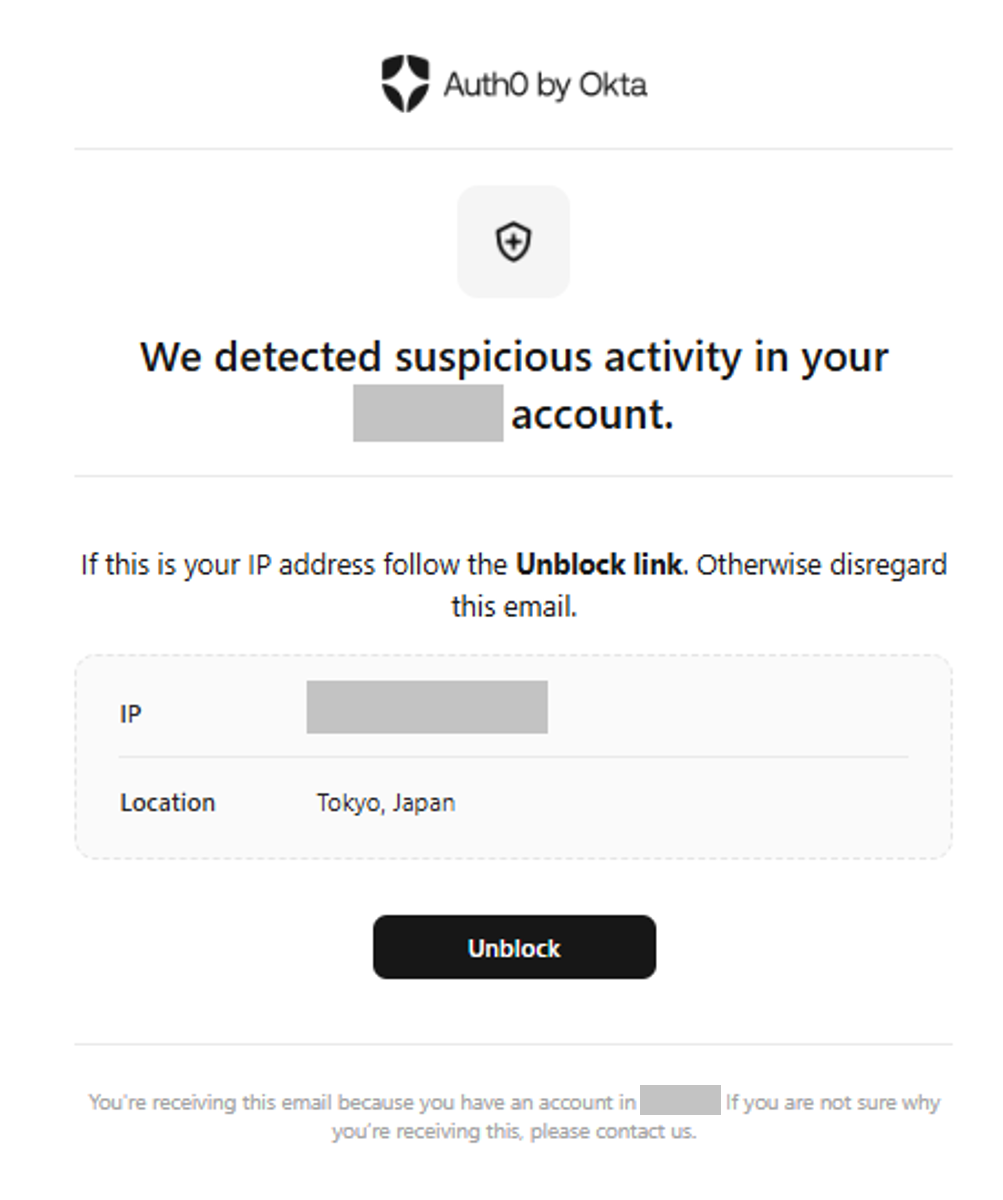
Block notification email to user
Configuration example: Suspicious IP Throttling
1.On the Auth0 administration screen, click [Security] > [Attack Protection]
2. Click Suspicious IP Throttling
3. Enable Suspicious IP Throttling function
4.In the Detection item, set the detection threshold and the IP network not to be detected. Any detection threshold can be set by selecting Custom for Suspicious IP Thresholds
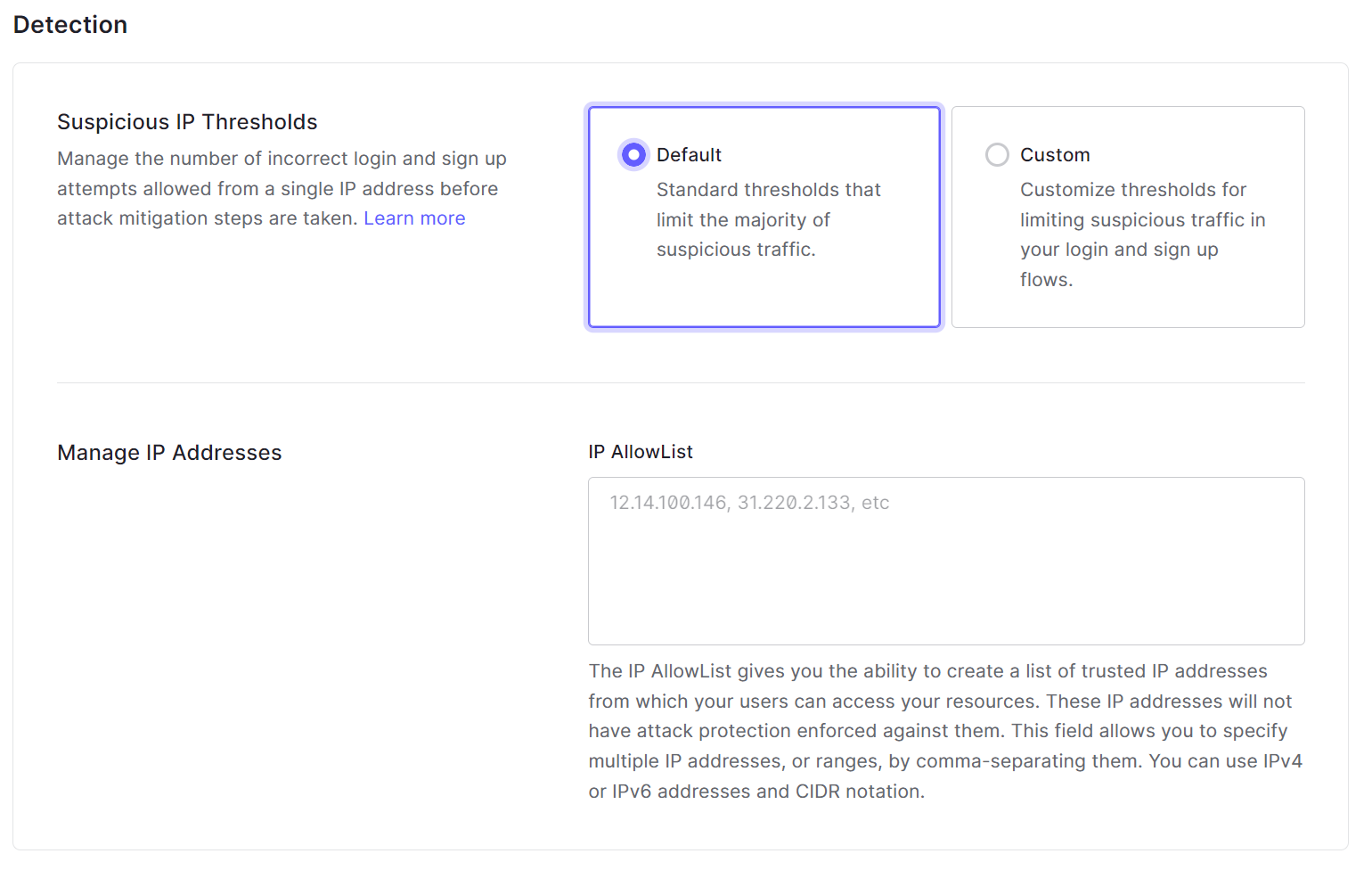
5.In the Response item, set whether to handle detection and whether to notify the administrator.
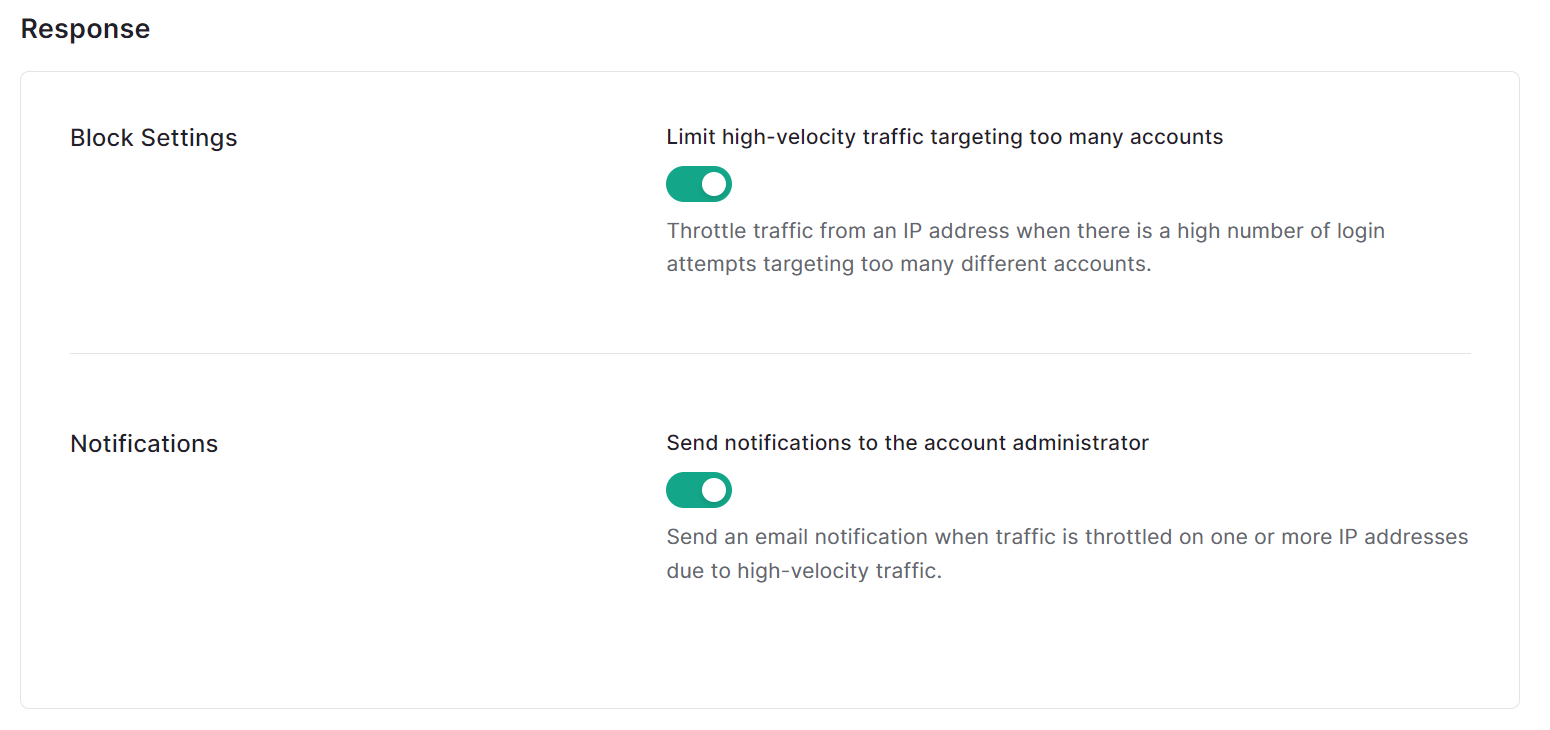
6. Click [Save]
Detection operation example: Suspicious IP Throttling
If login/signup failures from a certain IP address exceed the threshold within a certain period of time, a warning message will be displayed on the login screen when accessing from that IP address. In addition, access from the IP address will be blocked and an email notification will be sent to the administrator according to the response and notification settings at the time of detection.
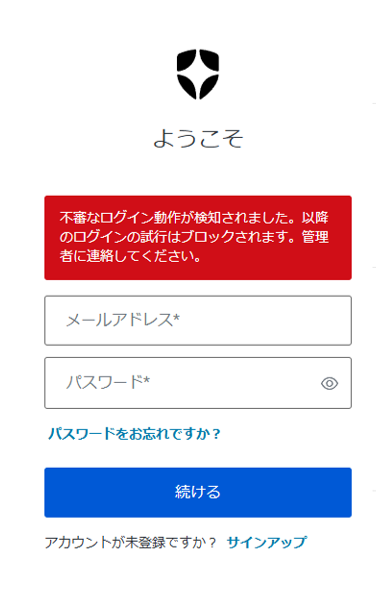
Suspicious IP Throttling
Login screen when detected
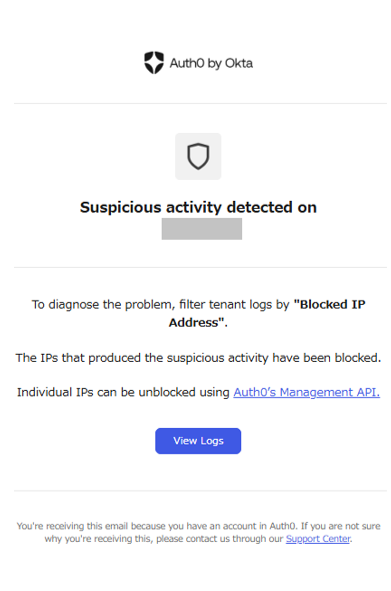
Detection notification email to administrator
Configuration example: Breached Password Detection
1.On the Auth0 administration screen, click [Security] > [Attack Protection]
2. Click [Breached Password Detection]
3. Enable Breached Password Detection function
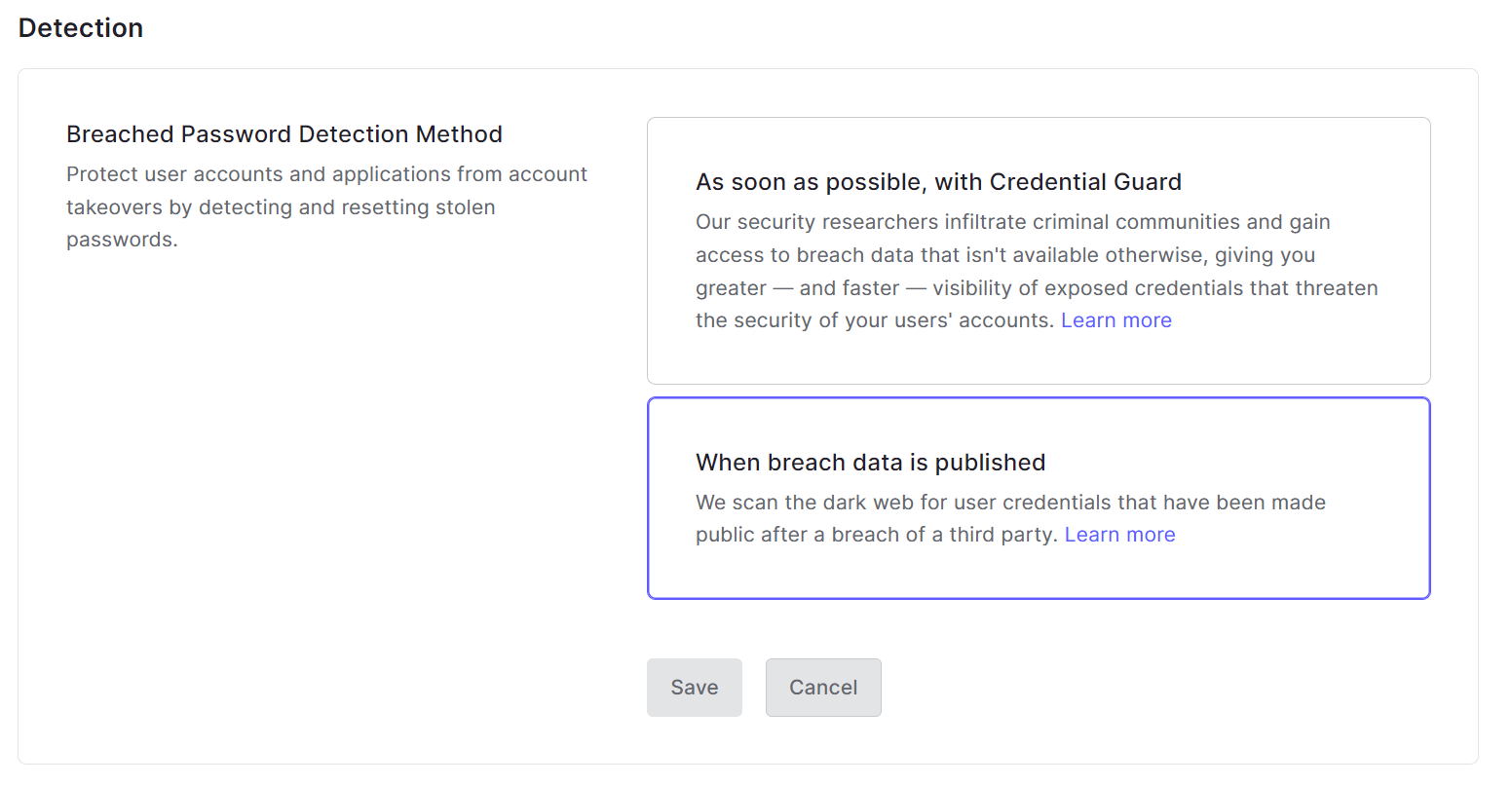
4. Select the usage method of Breached Password Detection in the Detection item. Click [Save]
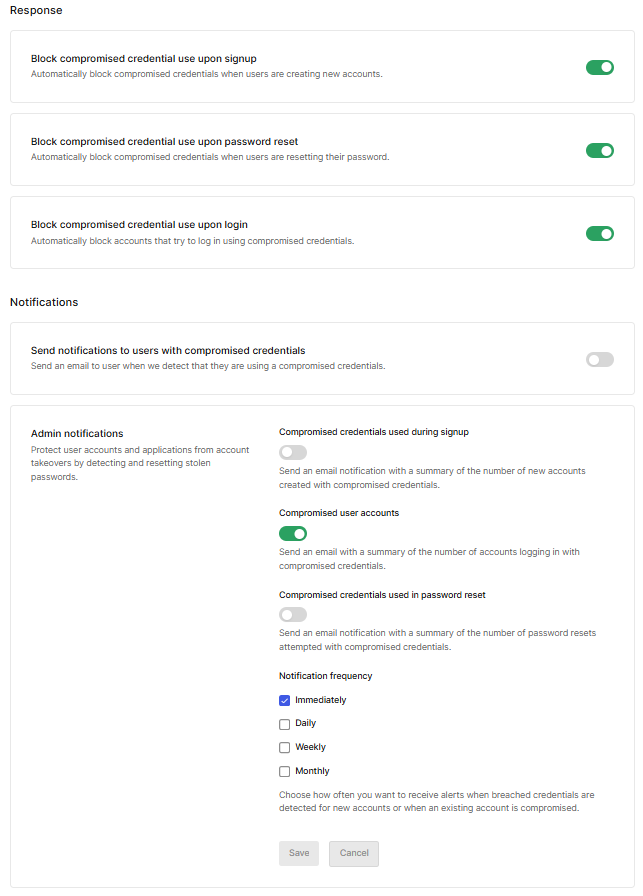
5.In the Response and Notifications items, set the rejection of sign-up upon detection, whether or not to block users, and the timing of email notification to the administrator. Click Save if you have changed your notification settings
Detection operation example: Breached Password Detection
If a user whose password information has been leaked is logged in by a user on the Auth0 side, a warning message will be displayed on the user's login screen. In addition, according to the countermeasures and notification settings at the time of detection, login restrictions for the user and email notification to the administrator will be performed.
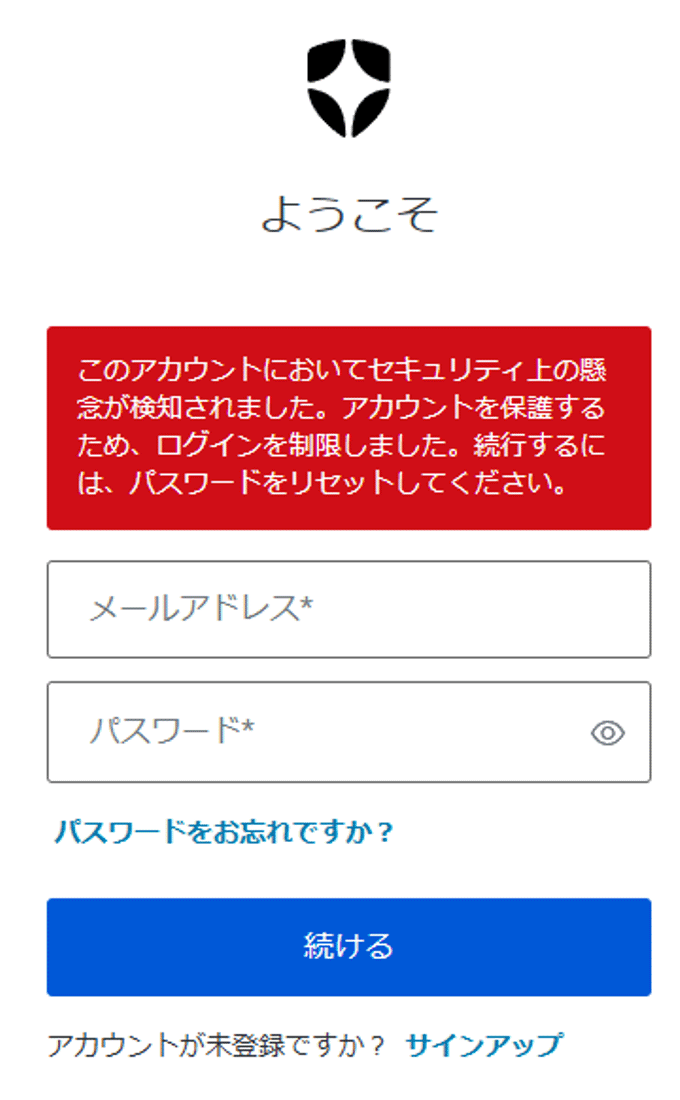
Breached Password
Login screen when detected
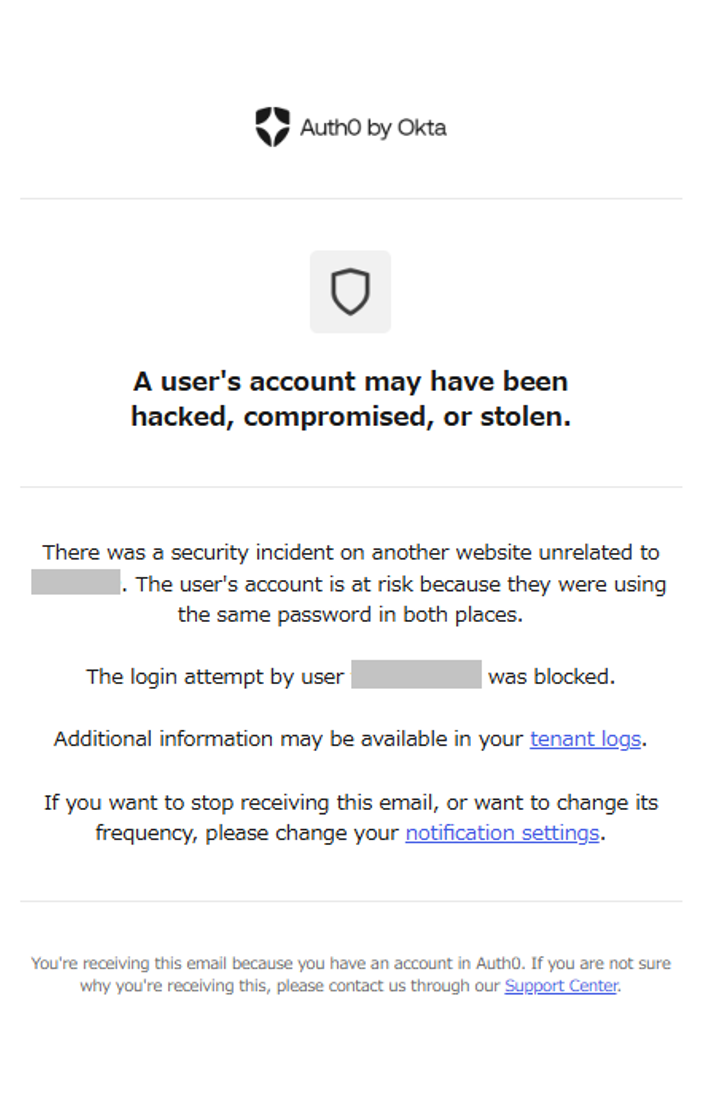
Detection notification email to administrator
In addition, the manufacturer has prepared a procedure for how to check the operation of Breached Password Detection. For details, please check the document below.
https://auth0.com/docs/secure/attack-protection/breached-password-detection#verify-detection-configuration
Summary
By using Auth0 in this way, you can easily implement countermeasures against unauthorized logins in web services. You can try the functions in the free Auth0 trial environment, so please feel free to experience it.
In addition to the functions introduced this time, Auth0 can implement measures against unauthorized login according to your requirements. If you are interested in the unauthorized login countermeasures implemented by Auth0, please contact us.
reference
Attack Protection – Auth0 docs
https://auth0.com/docs/secure/attack-protection
Top 10 Information Security Threats 2022 - IPA
https://www.ipa.go.jp/security/vuln/10threats2022.html
Inquiry/Document request
In charge of Macnica Okta Co., Ltd.
- TEL:045-476-2010
- E-mail:okta@macnica.co.jp
Weekdays: 9:00-17:00