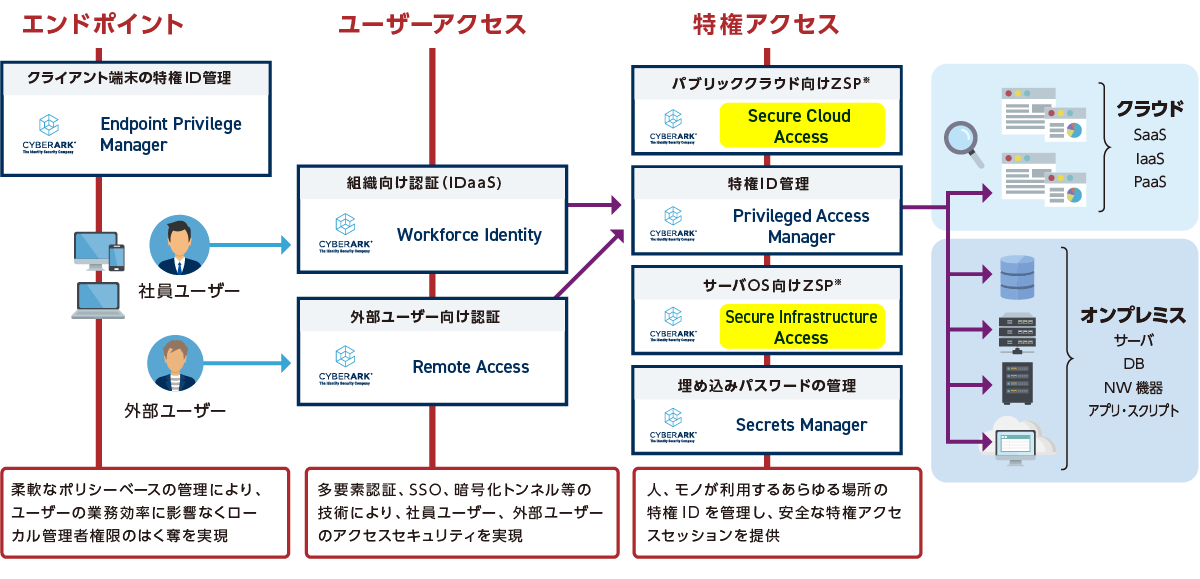
Products/Services
product
- Centralized Privileged Identity Management Solution - Privileged Access Manager
- Automated Certificate Management – CyberArk Certificate Manager (formerly Venafi)
- Endpoint Privileged Identity Protection - Endpoint Privilege Manager
- Zero Standing Privilege Solution - Secure Cloud Access/Secure Infrastructure Access

CyberArk
cyber arc
*Zero Standing Privilege: An approach to minimize attack vectors by having privileged IDs not exist on a system and only exist when a user uses them.
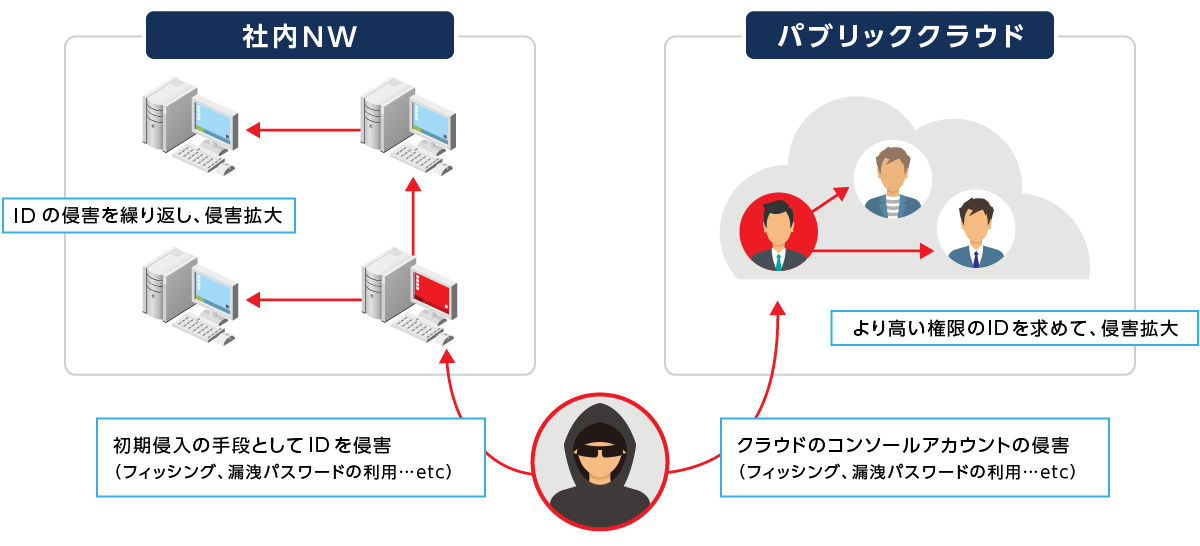
Zero Standing Privilege (ZSP): Minimize identity-based attack vectors
ID = “attack route” for the attacker
- "ID infringement" is a shortcut for attackers to expand infringement and achieve their goals
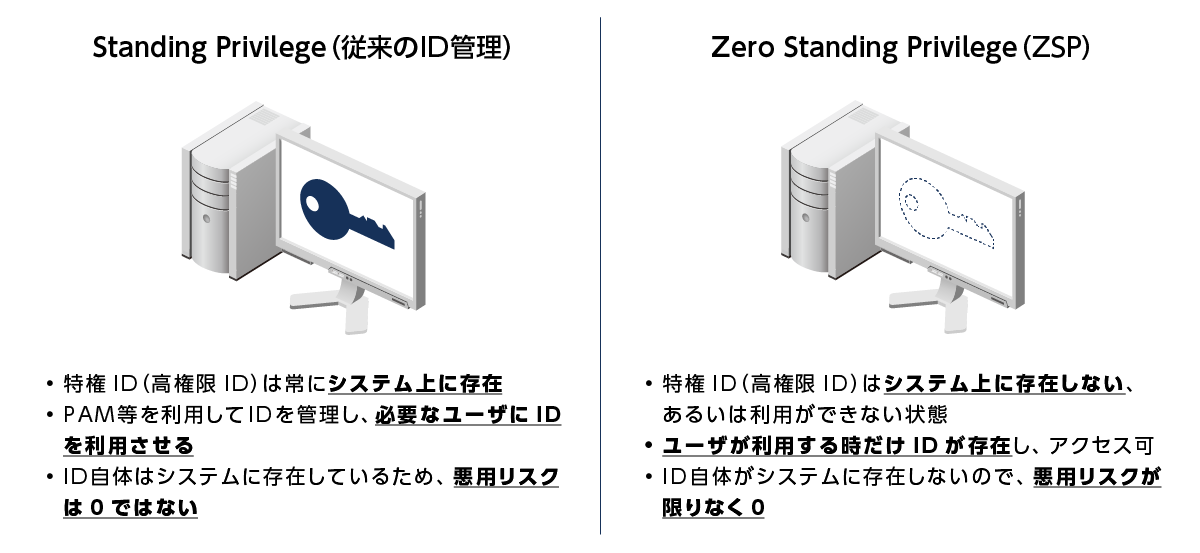
What is Zero Standing Privilege (ZSP)?
- Approaches to Minimizing "Identity"-Based Attack Surfaces
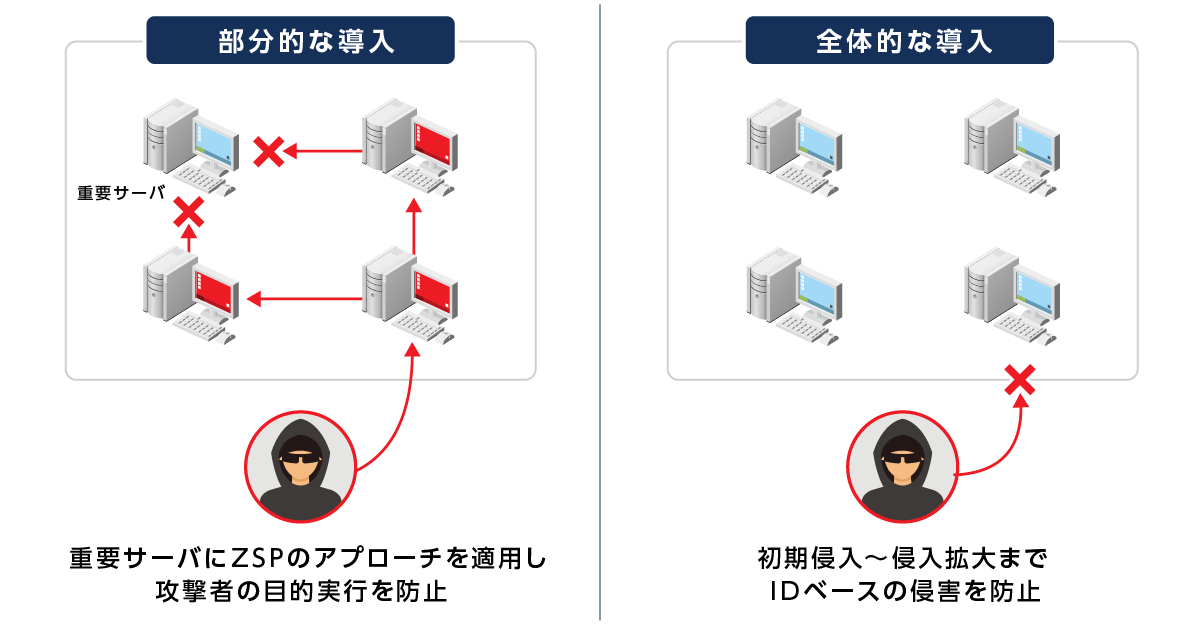
Advantages of ZSP introduction ① Security measures
- Prevent attackers from committing identity-based breaches
- By focusing on protecting important servers, even partial implementation is highly effective.
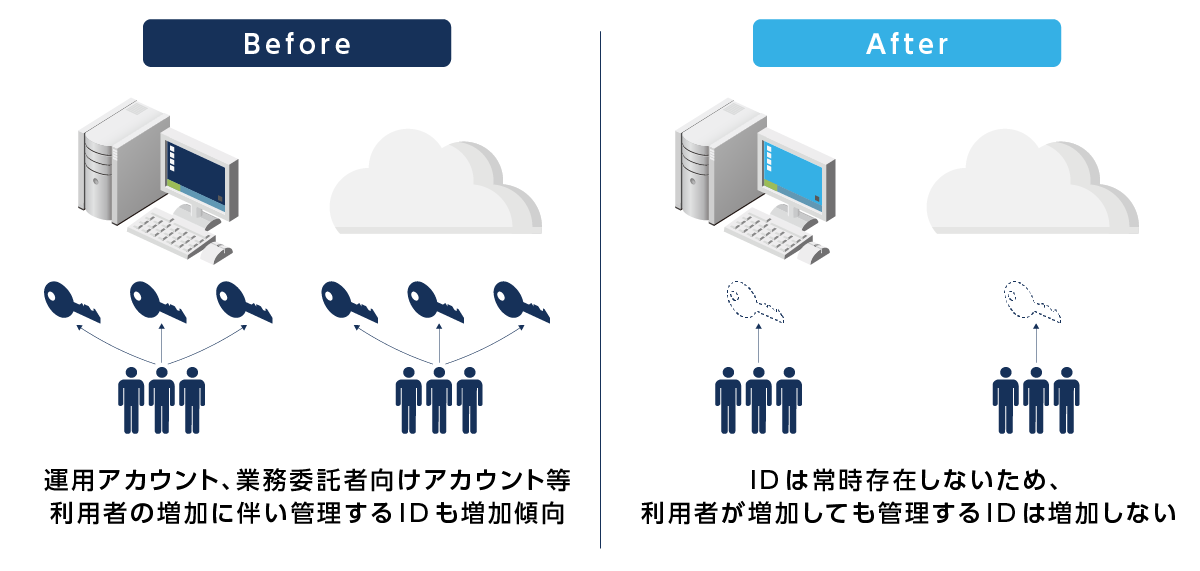
Advantages of ZSP introduction ② Preventing complexity of ID management
- ID-free operation prevents management complexity
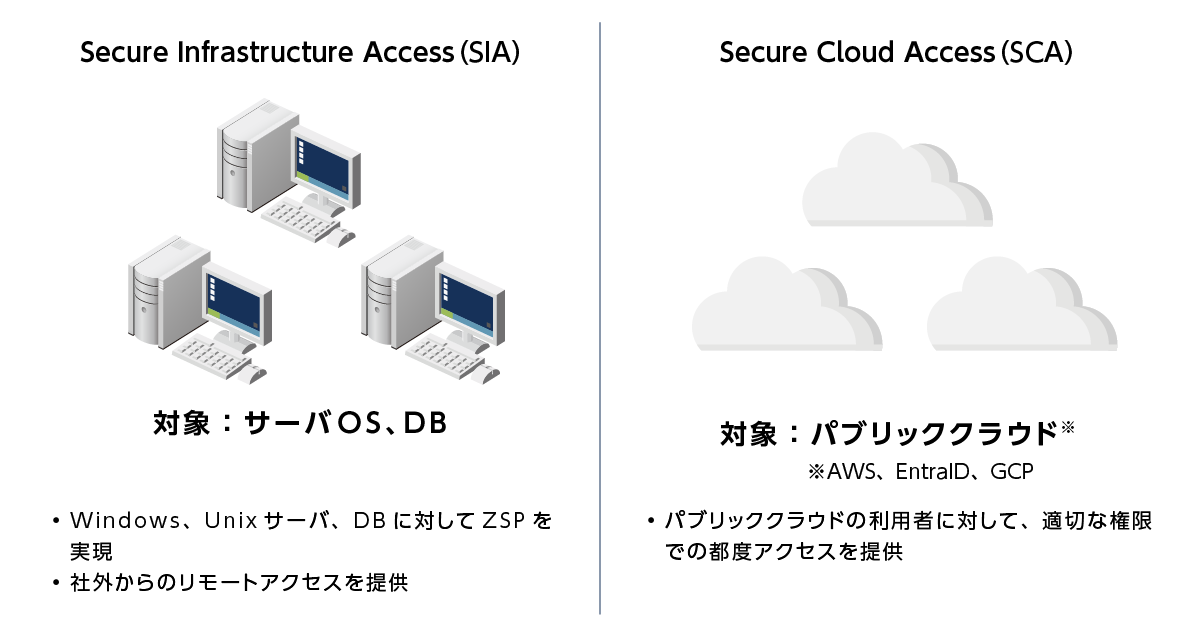
ZSP realization solution by CyberArk
- Providing solutions for server OS, DB and public cloud
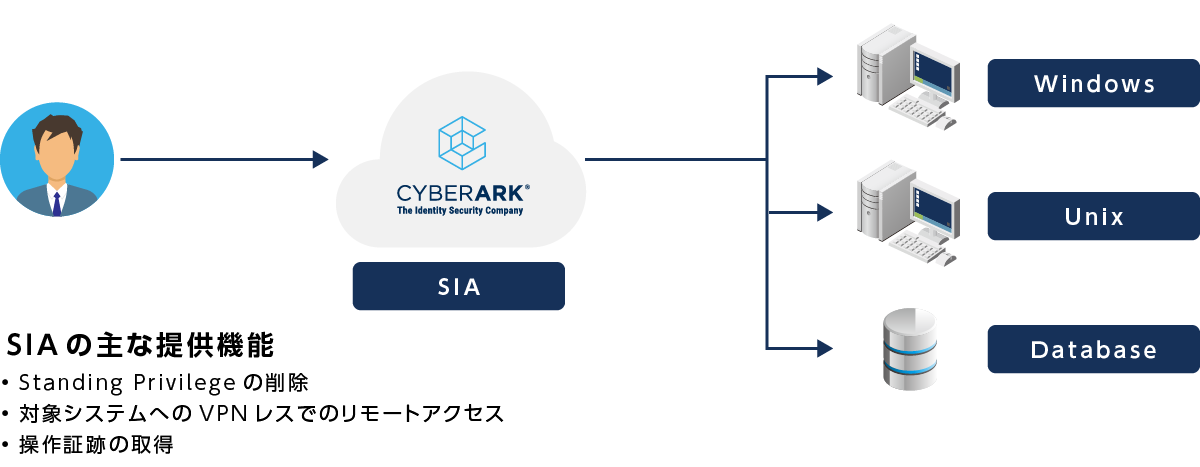
Secure Infrastructure Access (SIA) - Product Overview -
- Provides ZSP access to server OS and DB
- Allow temporary access to target systems according to predefined policies
- Once access is terminated, no privileged ID remains on the target system
SIA Use Cases

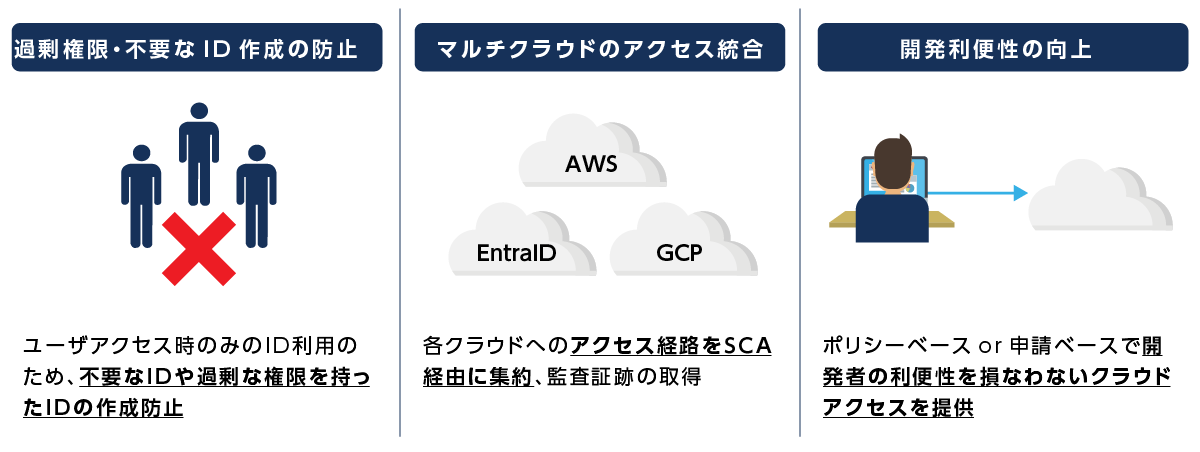
Secure Cloud Access (SCA) - Product Overview -
- Providing ZSP access to public cloud users
- Allow temporary access to target clouds according to predefined policies
- After the access ends, the user does not remain in the target cloud.
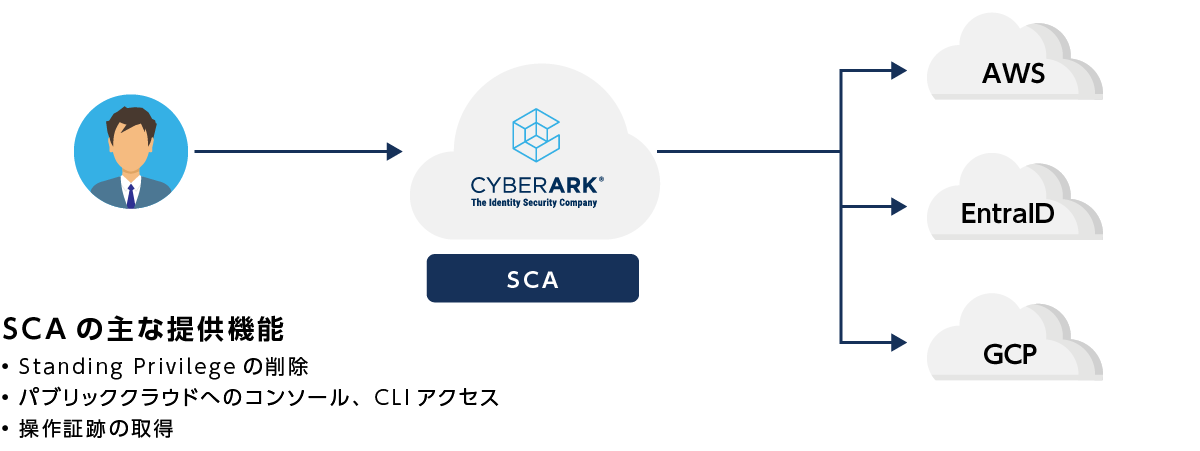
SCA use cases
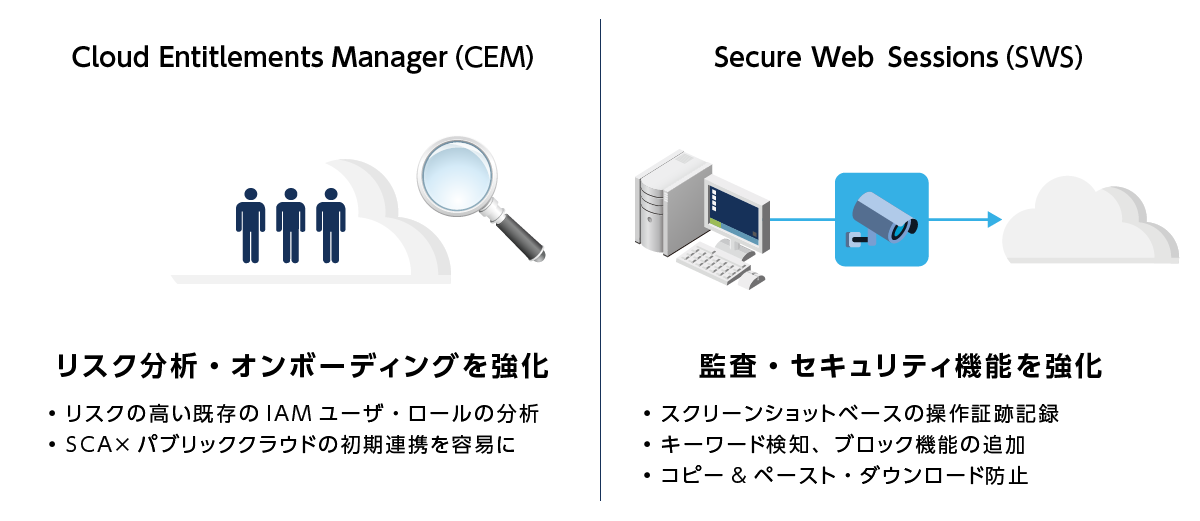
Integration with Cloud Entitlements Manager (CEM) and Secure Web Sessions (SWS)
- Enhance SCA functionality by integrating with other CyberArk products
Inquiry/Document request
Macnica CyberArk
- TEL:045-476-2010
- E-mail:macnica-cyberark-sales@macnica.co.jp
Weekdays: 9:00-17:00
