product
- Centralized Privileged Identity Management Solution - Privileged Access Manager
- Automated Certificate Management – CyberArk Certificate Manager (formerly Venafi)
- Endpoint Privileged Identity Protection - Endpoint Privilege Manager
- Zero Standing Privilege Solution - Secure Cloud Access/Secure Infrastructure Access

CyberArk
cyber arc
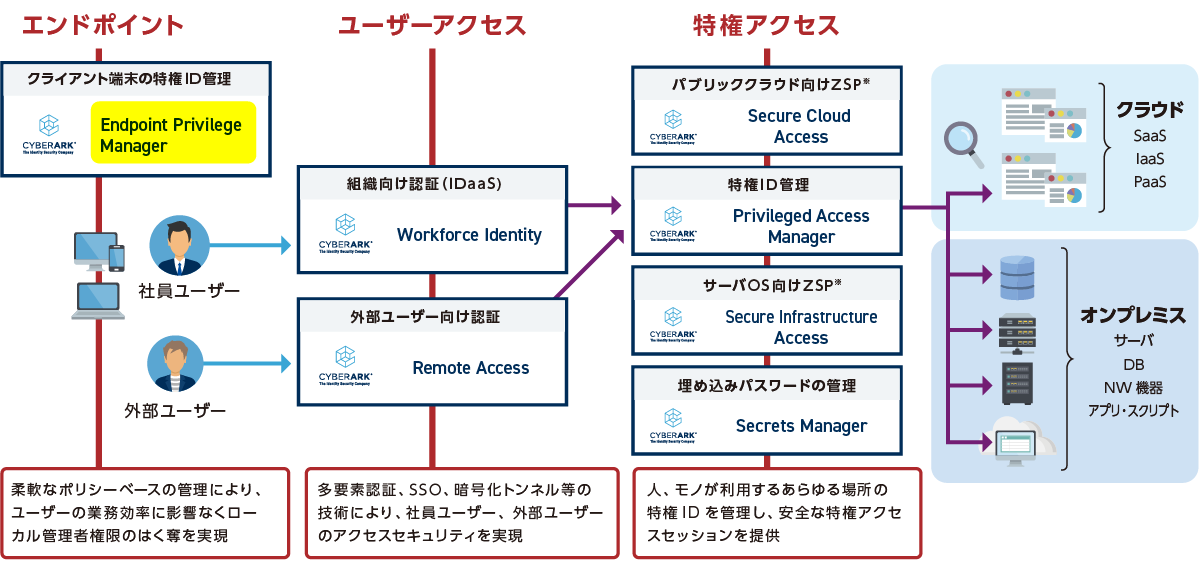
*Zero Standing Privilege: An approach to minimize attack vectors by having privileged IDs not exist on a system and only exist when a user uses them.
Endpoint admin privileges and security
Attackers use the intrusion of endpoint terminals as a foothold to expand their intrusion within the environment. In this case, if the compromised user has administrative privileges, the attacker can abuse those privileges.
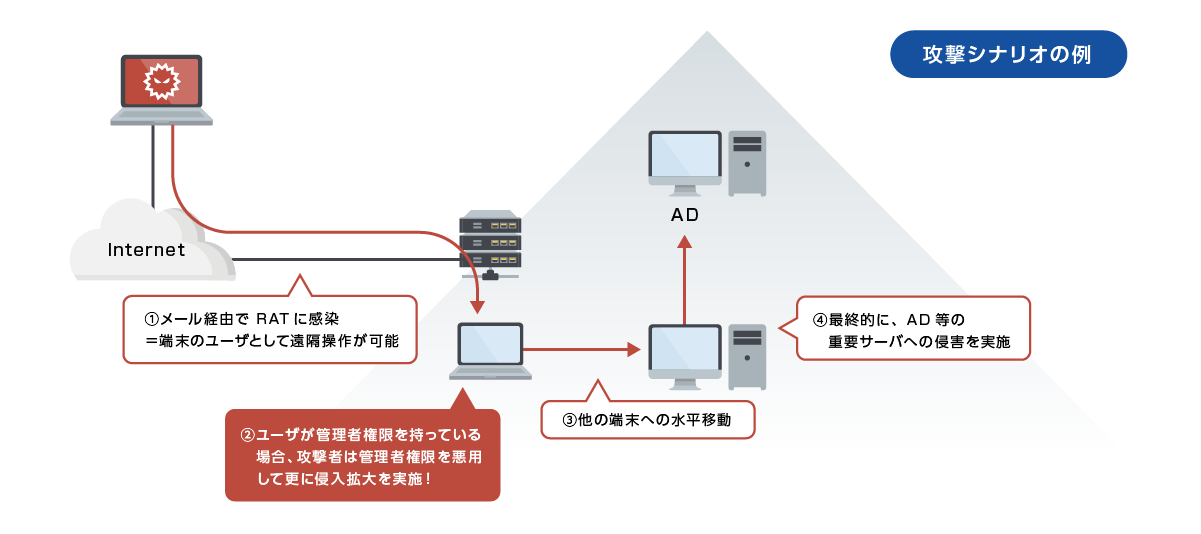
Risks of giving administrator privileges
An environment in which users are given administrator privileges has the following advantages from the attacker's point of view.
Change system configuration
Attackers can freely change the settings to make it easier for them to attack
・Service installation and execution
・Installation of malicious software
・Disable antivirus, uninstall, etc.
Steal password information
Credential theft, including access to password hashes that remain in memory
Create or modify user accounts
Create a backdoor account and use it for persistent infiltration
CHALLENGES IN ENDPOINT PRIVILEGE MANAGEMENT
The biggest challenge is how to balance convenience and security.
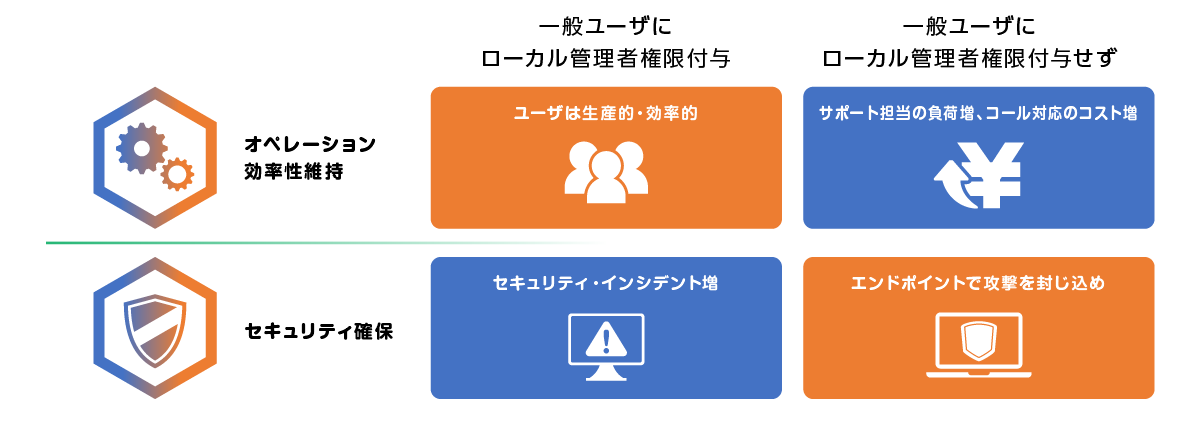
CyberArk solves your endpoint privilege management headaches! !
Endpoint Privilege Manager (EPM) Functional Overview
- Revoking administrator privileges from user terminals
- Users can use privileges only for necessary operations according to pre-defined policies
- Monitoring privileged behavior
- Set application execution permission or prohibition
- Applications not present in the rules can be allowed to run in restricted mode
example)
・Allows the execution of applications, but does not allow operations that require administrator privileges.
・Do not allow applications to communicate with the Internet
・Do not allow applications to access other files
- Detects and blocks access to credentials that remain in memory or browsers
- Detect and block file access by ransomware
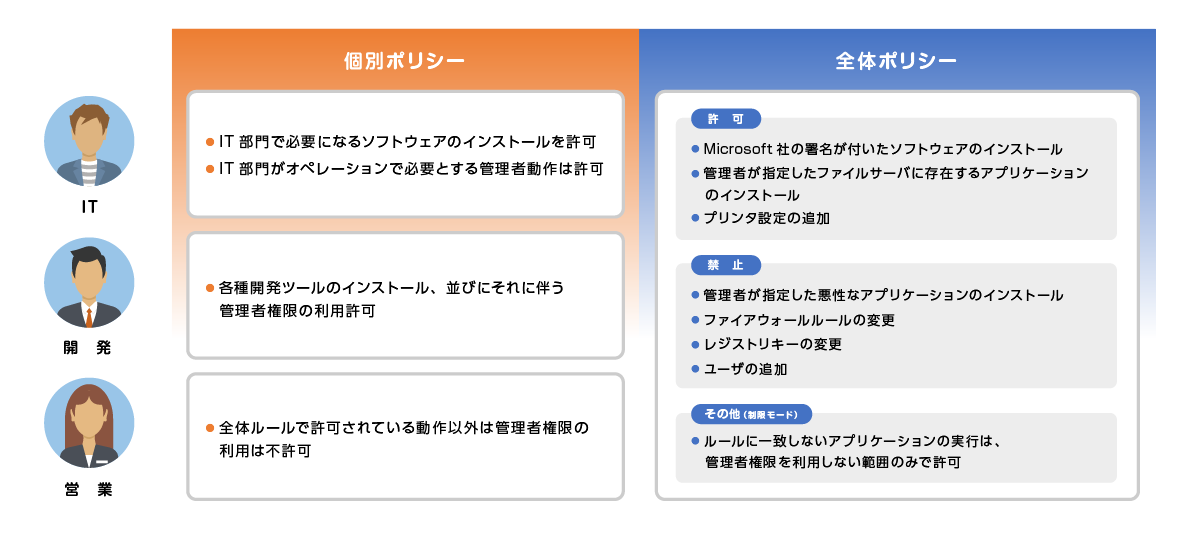
Usage image
By creating a policy, it is possible to control permission/non-permission for operations involving administrator privileges.
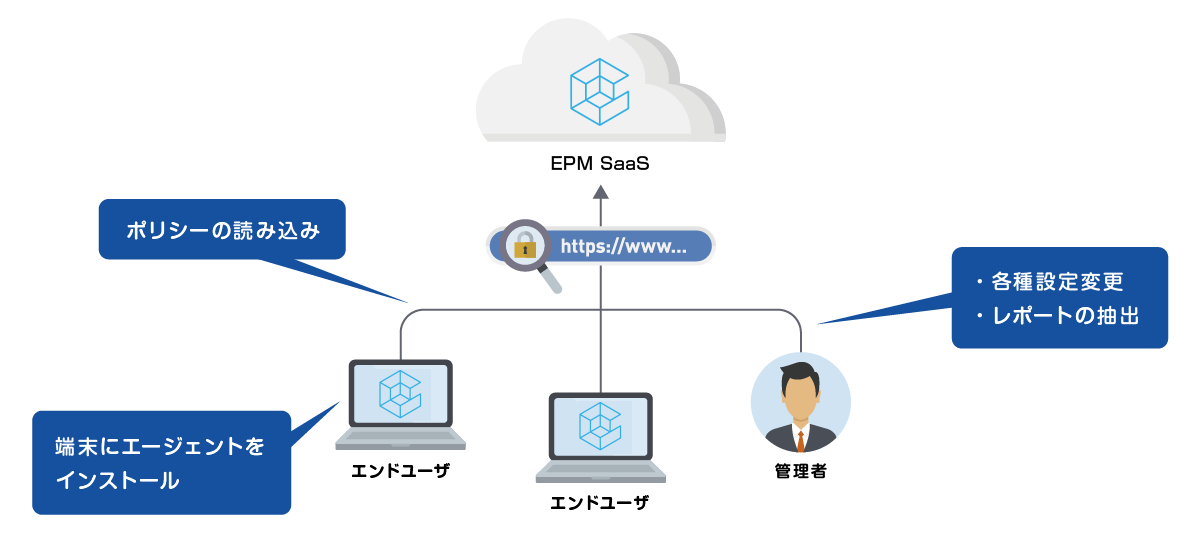
architecture
- The management console and policy server are provided on SaaS.
- Install the EPM agent on the customer terminal.
Features of EPM Agent
- It is very lightweight and uses less than 1% CPU on average.
- It supports Windows OS and MacOS.
- HTTPS/443 communication to the Internet is required from the EPM Agent installation terminal.
- Installation does not require OS reboot.
Inquiry/Document request
Macnica CyberArk
- TEL:045-476-2010
- E-mail:macnica-cyberark-sales@macnica.co.jp
Weekdays: 9:00-17:00
