product
- Web Protection Suite(SWG)
- Symantec Cloud SOC (CASB)
- Symantec Zero Trust Network Access(ZTNA)
- Symantec Endpoint Security(EPP・EDR)
- Symantec Email Security.cloud (Email Security)
- Symantec Ghost Solution Suite (kitting tool)
- SSL Visibility Appliance (SSL Composite)
- Macnica Cloud Security Security Package
- Other services/product information
Specifications/Technical Information

Symantec products
symantec products
Symantec Web Isolation
Required network isolation and web security issues
Possible threats from using the Internet
- Malvertisements
- coined from malicious or malware advertising
- Malicious Internet Ads Infecting Your PC
- Infected just by viewing ads
- watering hole attack
- A method of tampering with websites that are frequently visited by the target of the attack and installing malware by visiting them.
- Execution of exploitation and destruction of confidential information by remotely controlling infected terminals
- ransomware
- Malware Takes Data Hostage, Forces Data Encryption
- Not only one infected PC but also a shared file server on the network is encrypted, so it is easy to affect the business of corporations.

While maintaining user convenience, security measures have become an urgent issue.
Cyber security incidents continue to occur frequently
- Damage caused by cyber attacks via the web in Japan and overseas
- October 2016 Leak of personal information of 1,466 students at a certain private university
⇒It started when an employee mistakenly entered an ID and password on a phishing site that was guided by e-mail. - February 2017 Large-scale watering hole attacks overseas
⇒The website of the Polish financial regulator was defaced, and the computers of each industry organization selected as targets were infected with the malware "RATANKBA."
- October 2016 Leak of personal information of 1,466 students at a certain private university
- The second most common threat to organizations is “damage from ransomware”
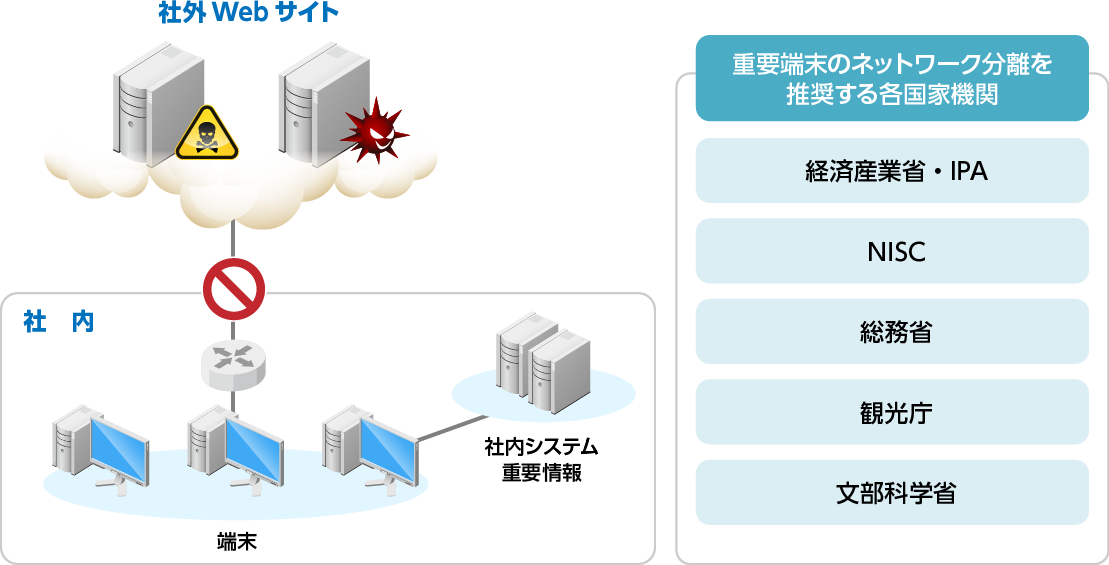
- IPA recommends network separation as a countermeasure against ransomware damage, ranked second in the 2018 Top 10 Information Security Threats*.
* We have a wealth of experience in dealing with malware that is often used by attack groups targeting Japan.
Desired web isolation
In the wake of the 2015 security incident at a public entity, the guidelines of the Ministry of Internal Affairs and Communications, the Ministry of Economy, Trade and Industry, etc. strongly recommend separating the networks of important business terminals.

Symantec Web Isolation Overview
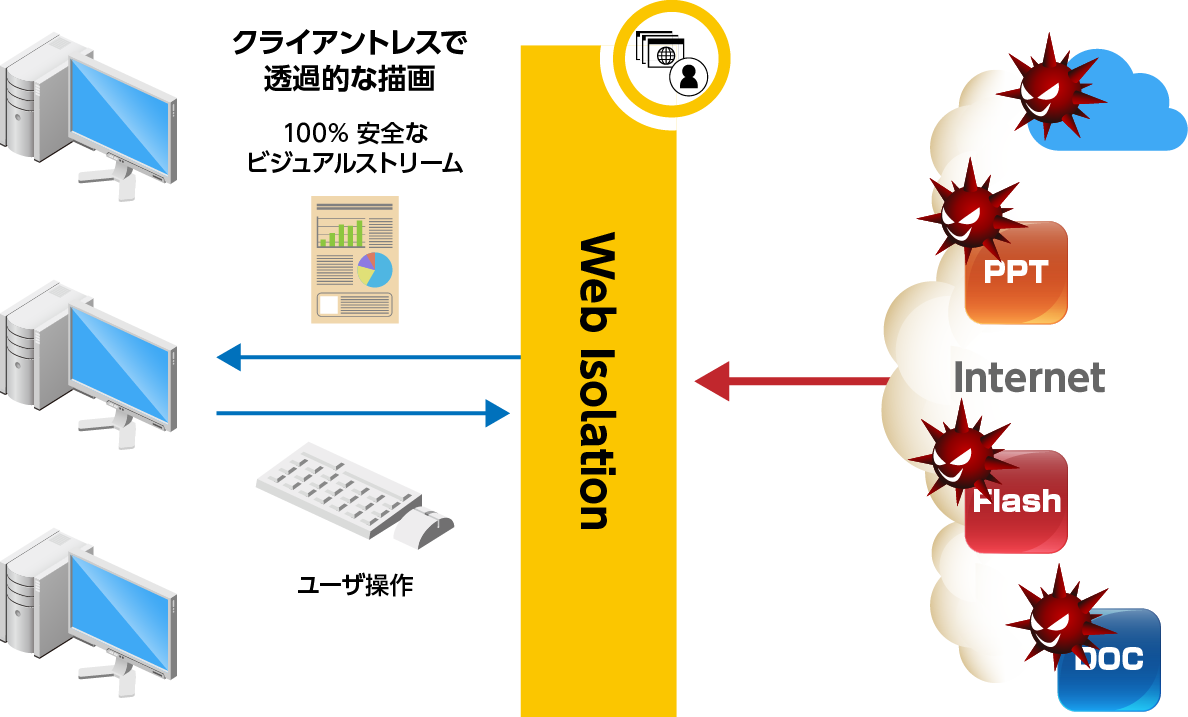
- Transmit only visual stream to user without active content
- Original web content is isolated in Web Isolation's secure container All web content is destroyed after the session ends
- No need to install agents on clients
- Compatible with various browsers, no change in operation content
Function introduction
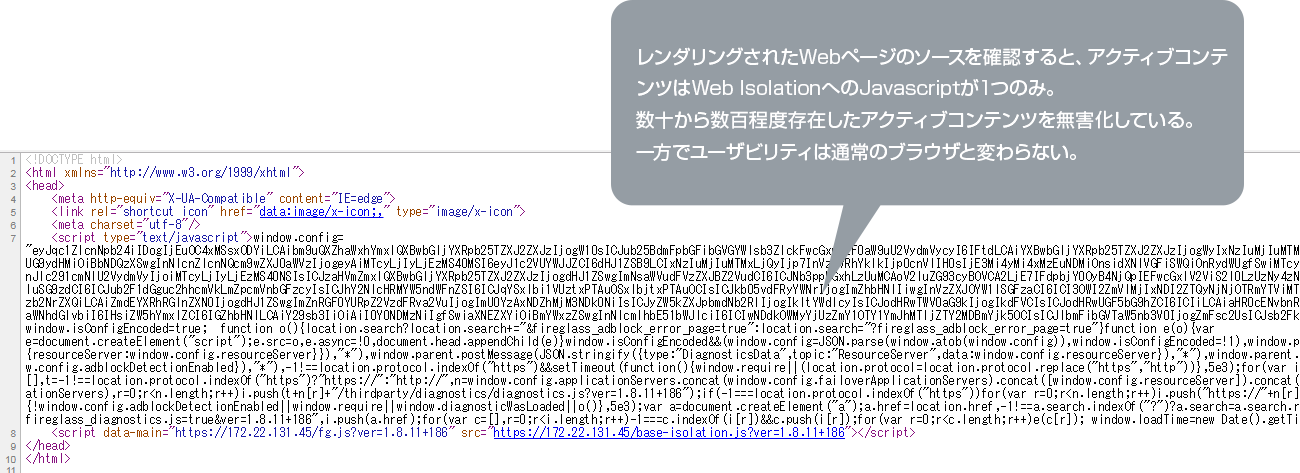
Isolation / Active Content Sanitization
before rendering
After rendering
Isolation/secure document viewing
- You can view documents such as Word and Excel without saving them locally
- Realize safe document browsing by converting to static content
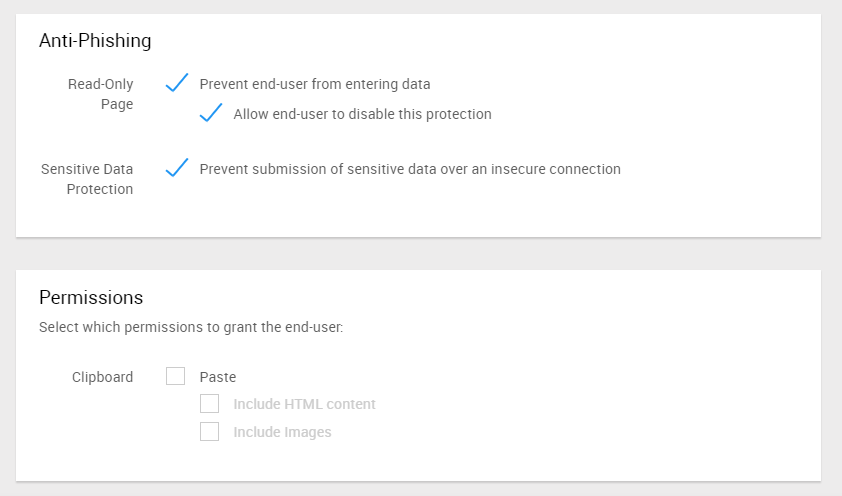
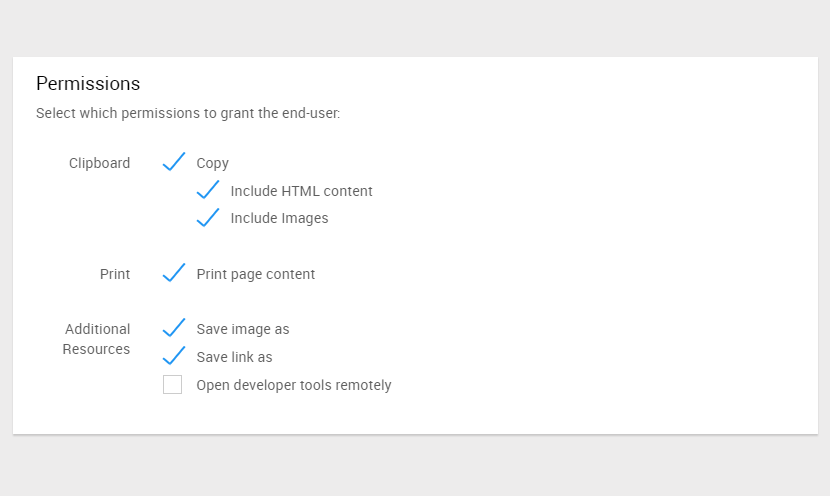
Operation restrictions within the Isolation/Rendering page
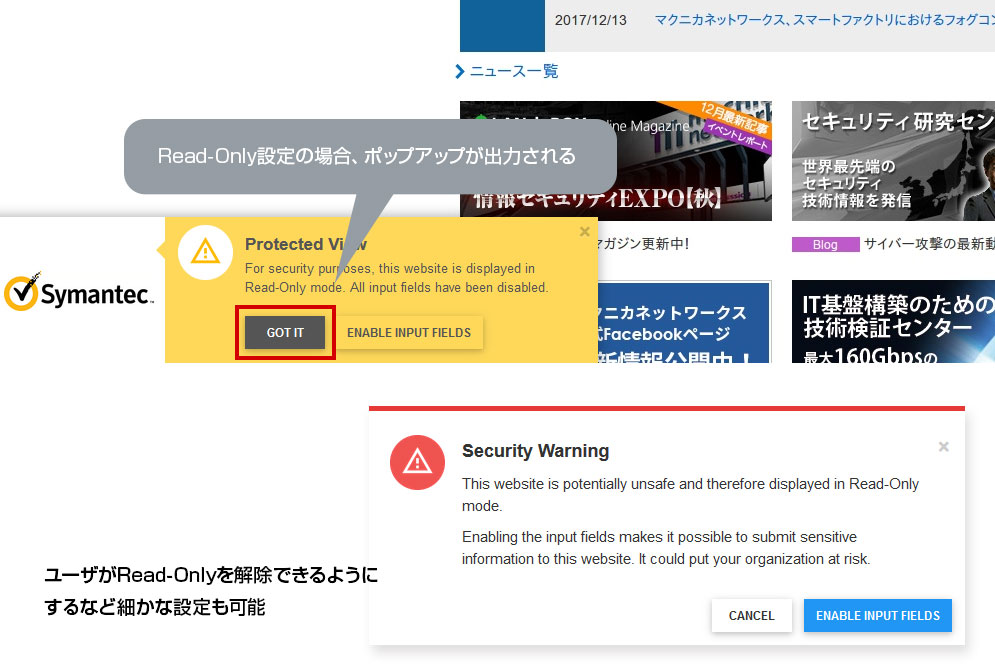
With Web Isolation, it is possible to flexibly set read-only (employees cannot enter characters) within the rendered page, copy and paste restrictions, etc. according to the user and risk level.
Example) Behavior when Read-Only is set
Integration with Symantec products
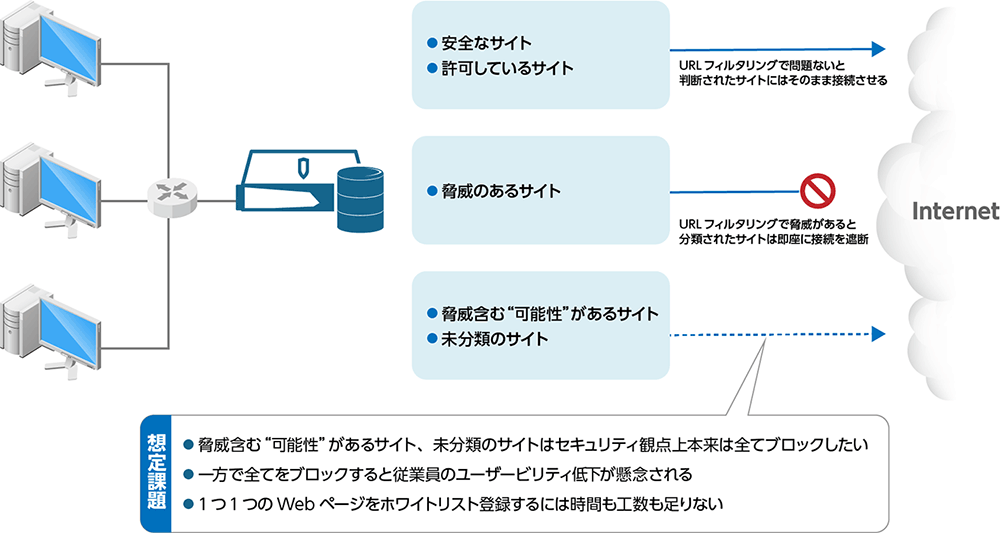
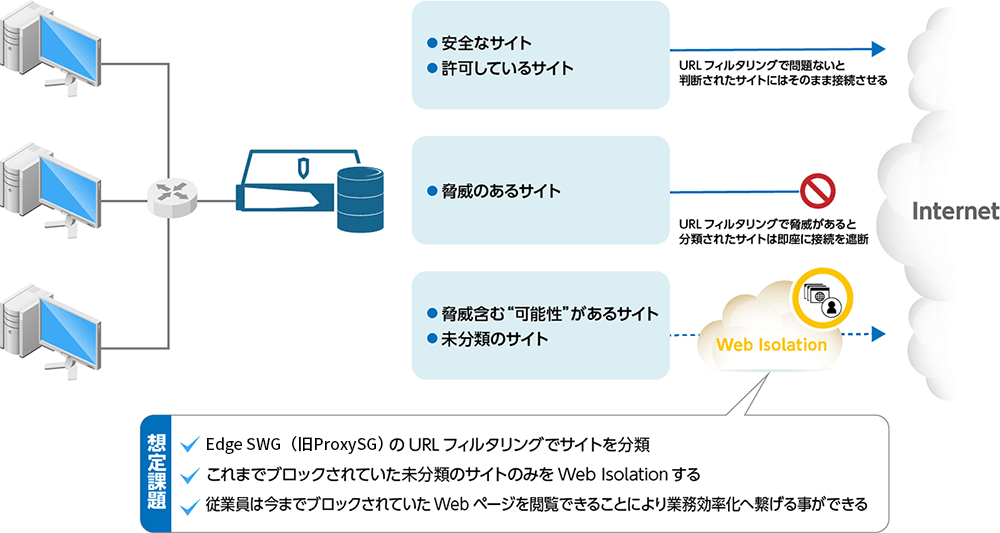
Coordination with Symantec Edge SWG (formerly ProxySG) (before introduction)
In URL filtering, operations occur for uncategorized sites that are potentially threatening sites
Coordination with Symantec Edge SWG (formerly ProxySG) (after introduction)
Sites with potential threats and uncategorized sites are dealt with by rendering them harmless without blocking.
Inquiry/Document request
In charge of Macnica Symantec Co., Ltd.
- TEL:045-476-2010
- E-mail:symantec-sales@macnica.co.jp
Weekdays: 9:00-17:00