Symantec製品
シマンテック製品
SSL Visibility Appliance

HTTPSに代表されるSSL通信は年々増え続けているものの、通信の中身が暗号化されているために十分なセキュリティ対策を実施することが困難な状況です。次世代ファイアウォールやIPS、セキュアゲートウェイ(プロキシ)などの一部の製品は、SSLを復号化する機能があるものの、専用アプライアンスでないためにパフォーマンスが低下してしまい実運用での導入が難しいケースも少なくありません。特にSSLの鍵長が512bit, 1024bit, 2048bit と大きくなるにつれてパフォーマンスが大きく低下してしまうケースが多く見られます。
また、逆に標的型攻撃に代表されるサイバーアタックでは、ファイアウォールやサンドボックス、フォレンジックなどのセキュリティ対策を回避するためにSSLを利用して実行されるケースが増えてきているため、SSL通信に対するセキュリティ対策が急務となっています。
既存のネットワーク構成を変更することなく、透過的にSSLの復号化が可能!
特徴
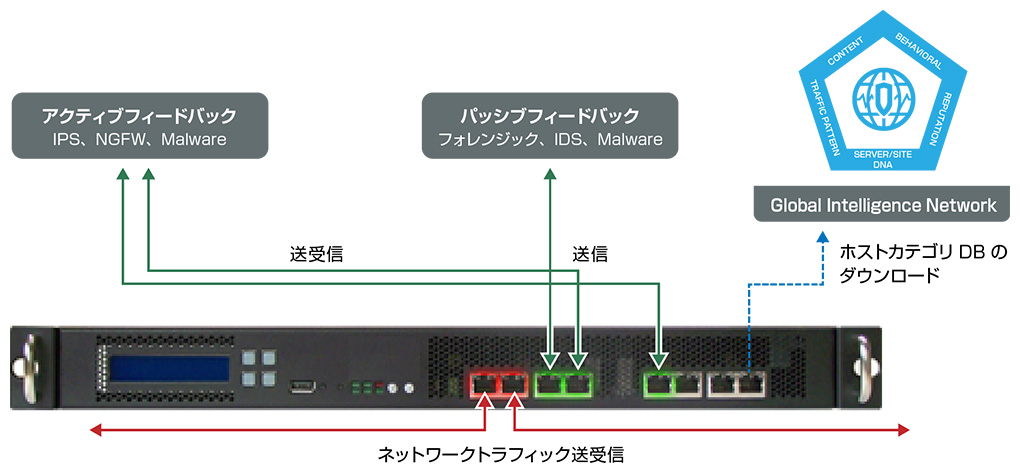
- 透過型で動作しSSL通信を復号する専用アプライアンス
- 復号したSSL通信とその他の通信を合わせて、外部機器へデータを受け渡す
- 1度の復号で、多数のデバイスに対してデータを提供可能
- インラインおよびパッシブの様々なセキュリティアプライアンス/アプリケーションをサポート
- URLがカテゴリデータベースに対応 Global Intelligence Networkに対応し、SSLデコード対象をカテゴリ単位で制御が可能
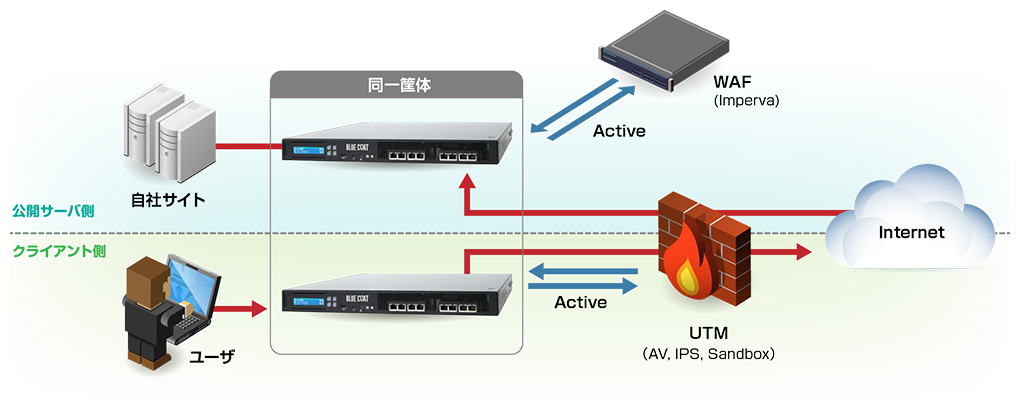
連携デバイス事例

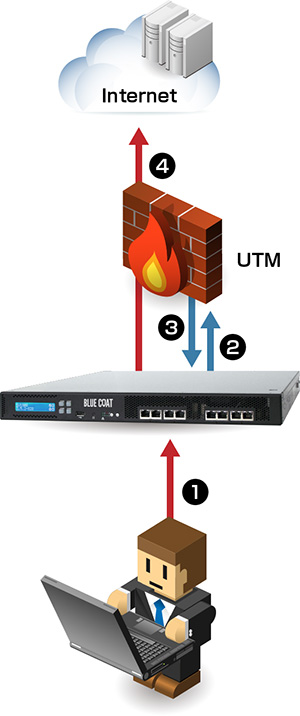
UTM / IPS連携
Active Inline構成
UTM製品のうち、AV, IPS, URL Filter, Sandbox等に、
SSL通信も検査をさせる
検知対象の拡大、詳細ログの把握が可能
- SSLサイトにhttpsの状態で通信
- SSL-VAにてSSLデコードし、UTMに展開
- UTMで検査後、通信を折り返し
- 再暗号化後、httpsでSSLサイトに接続
各業種別 利用事例
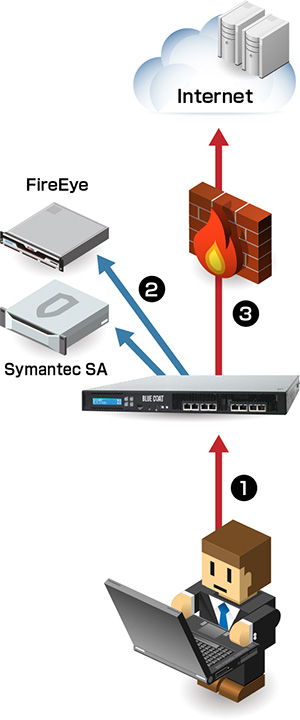
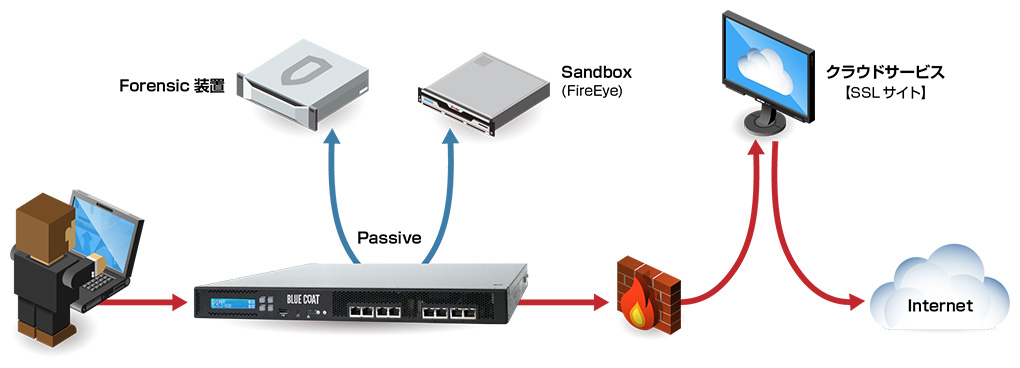
事例① 金融業界【サンドボックス・フォレンジック連携】
- 背景
- セキュリティ意識の高さから、サンドボックス(FireEye)が導入済み
- 官公庁からの指針もあり、フォレンジック(パケットキャプチャ)も実施済み
- 今後Webクラウドサービスの導入予定もあり、クライアントとWebクラウドサービス間がSSL通信になることにより、既存環境にてできている機能を今後も維持する為、SSL Visibility Applianceを導入※導入されるクラウドサービスにより要検証
事例② 公共業界【UTM・WAF連携】
- 背景
- 大規模なセキュリティ製品一括導入の際、増加しているSSL通信への対策を無視できなかった
- コストの関係もあり、UTMにて多くのセキュリティ機能をカバーしたが、SSL通信対策までをUTMで行うにはパフォーマンスが足りなかった
- SSL Visibility Applianceを導入することで、コストを抑えつつ多くのアウトバウンドセキュリティ機能(AV, IPS, Sandbox)だけでなく、インバウンドセキュリティのWAF(Imperva)までもを、1台にてSSL通信検査対象にすることが実現できた
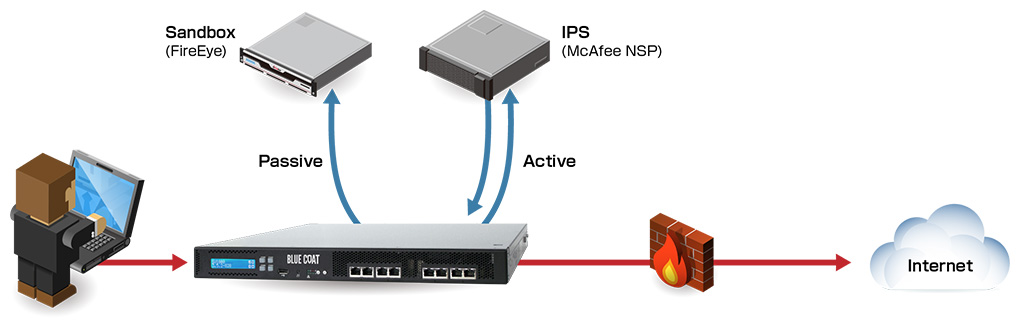
事例③ 製造業界【IPS・サンドボックス連携】
- 背景
- FireEyeを導入するも、SSL通信の中身が見れないことを導入直前まで気づいてなかった
- 社内全通信の40%以上がSSL化されていることには気づいていた為、早急な対応が求められた
- FireEyeとSSL Visibility Applianceの連携導入実績がマクニカにてあった為、安心して製品を選定
- 今後は既存IPS製品にも、同時連携を行う予定
ネットワーク構成例
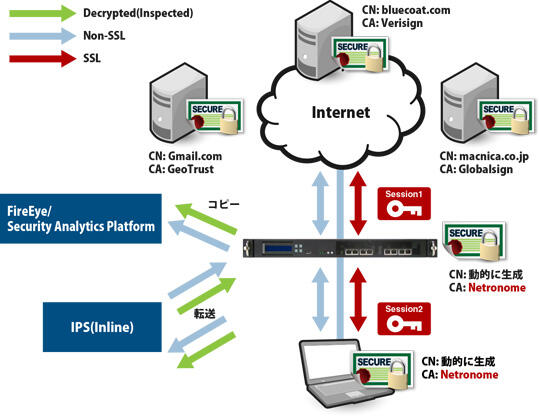
社内ネットワークに設置する場合(フォワード環境)
フォワードの環境では機器をInlineで導入してSSLを復号化し、Inline構成の機器にパケットを転送、及びSPAN/TAP構成で待ち受ける機器にコピーすることが可能です。この場合、機器がSSLのハンドシェイクを一旦終端し、SSLの証明書を動的に生成(Re-Sign)してクライアント側と通信を行いますので、クライアントには機器のCAの証明書を信頼されたルート証明機関として事前に登録しておく必要があります。
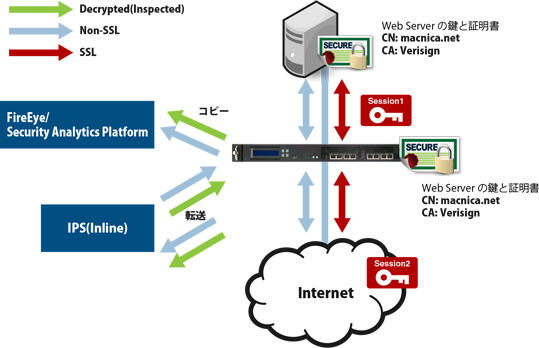
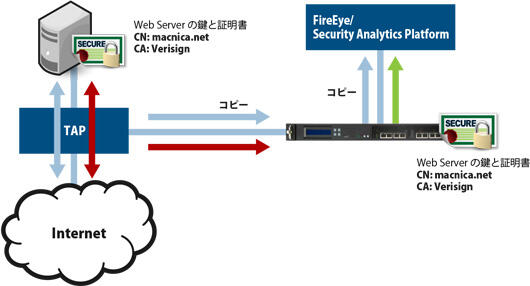
データセンターに設置する場合(リバース環境)
リバースの環境でWebサーバの鍵と証明書がある場合、TAPモードとInlineモードのどちらかの構成で導入します。
各構成比較一覧(インバウンド・アウトバウンド)
|
アウトバウンド構成 |
インバウンド構成 |
||
|---|---|---|---|
| SSL通信の方向 | インターネット向け | DMZ向け、内部向け | |
| 設置形態 | インライン | インライン | TAP |
| モード | パッシブインライン アクティブインライン |
パッシブインライン アクティブインライン |
パッシブタップ |
| 組み合わせ可能なデバイス | IPS、IDS、サンドボックス、フォレンジック | IPS、IDS、サンドボックス、フォレンジック | IPS、IDS、サンドボックス、フォレンジック |
| クライアントPCへのCA証明書配布 | 必要 | 不要 | |
| Webサーバの証明書と秘密鍵 | 不要 | 必要 | |
| SSLセッションの終端 | あり | あり | 無し |
お問い合わせ・資料請求
株式会社マクニカ Symantec 担当
- TEL:045-476-2010
- E-mail:symantec-sales@macnica.co.jp
平日 9:00~17:00