Vectra AI
ベクトラエーアイ
攻撃者侵入経路の多様化とNDR(Network Detection and Response)の必要性
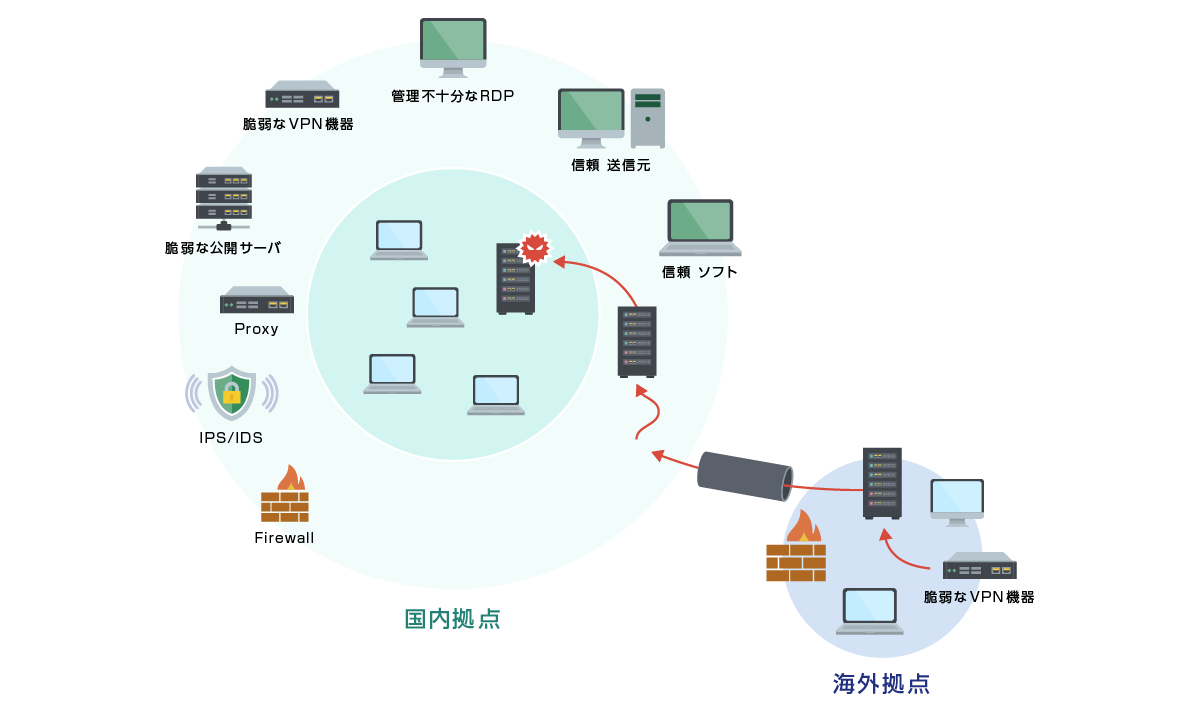
今日、攻撃者の侵入経路は多様化しています。下記は一例に過ぎず、境界防御を用いて攻撃者の侵入を全て防ぐことは不可能だという考え方が浸透しています。このため、境界防御製品に加え、内部へ侵入してくる攻撃者を検知する製品が必要だと考えるユーザがNDRの導入を進めています。
- VPN装置の脆弱性を悪用した侵入
攻撃者が直接的に社内ネットワークへアクセスします。EDRなどの最新の対策も効果を発揮しにくいという課題があります。 - リモートアクセス経路
攻撃者が何等かの方法で認証情報を入手し、端末へログインして社内ネットワークへアクセスします。通常利用においても必要な経路であるため、穴を閉じるという対策が取れないという課題があります。
NDRは、社内ネットワークを監視することで不審な振る舞いをいち早く検知し、攻撃者が目的を達成する前に脅威を封じ込めることができます。
Vectra AI NDRの特徴
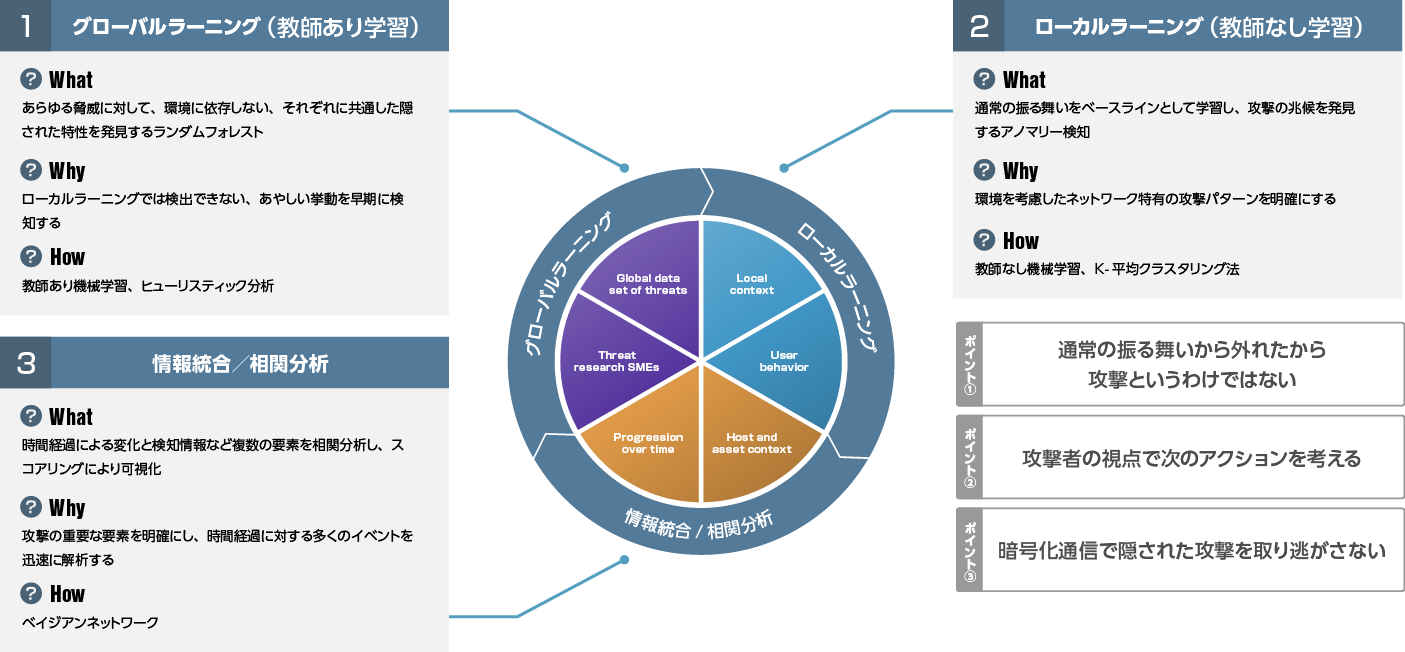
高度な検知機能
教師あり学習・教師なし学習・相関分析といった3つの検知ロジックを組み合わせることで、より精度の高い検知を提供します。
導入構成イメージ
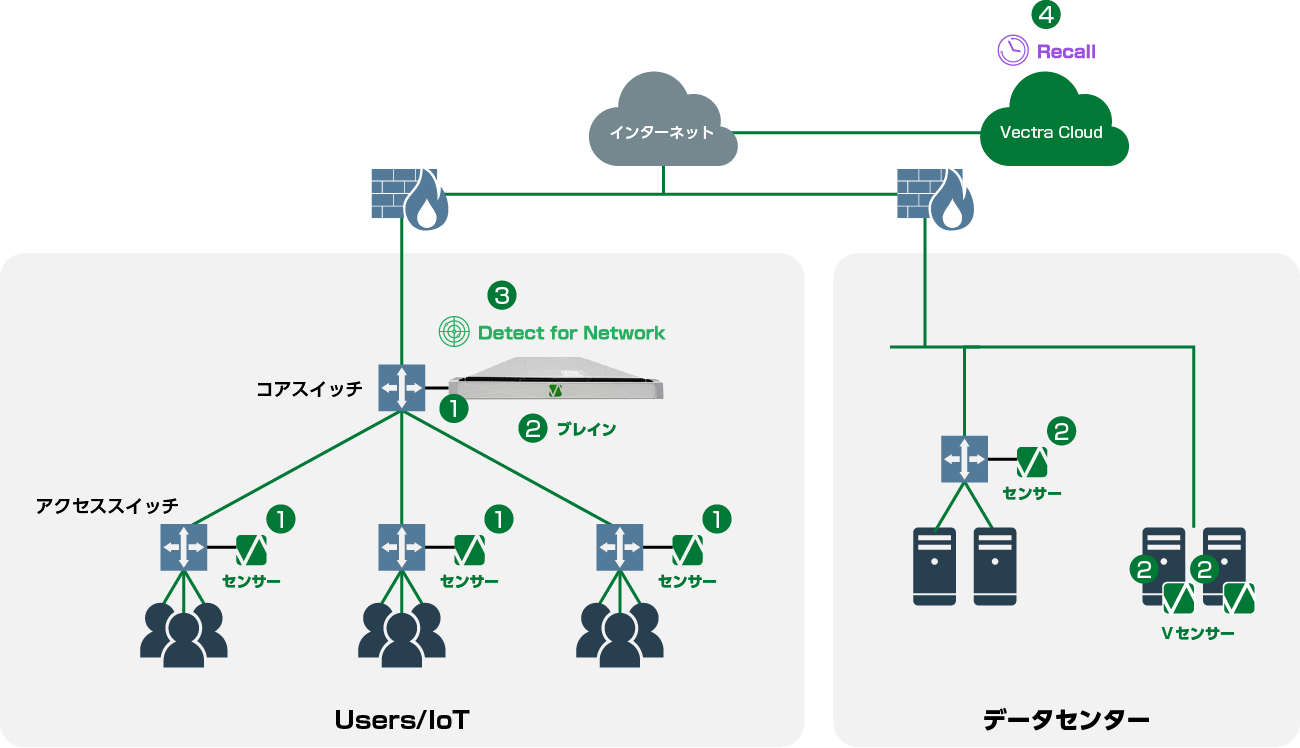
- データのキャプチャー
コアスイッチからミラートラフィックを生成し、ブレインにすべてのトラフィックをパッシブに取り込みます。 - 複数拠点監視
データセンター、リモートロケーション等、セグメントが分離している場合はセンサーを設置し、ブレインにメタデータを転送することで、複数拠点の可視化を実現。 - データ収集/検知(Detect)
ブレインに収集された情報は重複排除され、独自のエンジンが脅威を検出 - 収集データの可視化(Recall)
センサーが収集したネットワークメタデータをクラウド上の基盤で可視化
プラットフォーム
お問い合わせ・資料請求
株式会社マクニカ Vectra AI 担当
- TEL:045-476-2010
- E-mail:vectra-ai-sales@macnica.co.jp
平日 9:00~17:00