
Imperva
Imperva
How to protect users and brands from unauthorized use of your service
Summary of this article
With phishing attacks on the rise, how can you protect your legitimate users and your brand from criminal abuse of your services? In this article, we will look at trends in phishing crimes and countermeasures against fraudulent use, and introduce a framework of measures that companies that have been deceived about their services should take.
Summary of this article in 3 lines
- In phishing scams, users are directed to fake sites through SMS and emails, and personal information is stolen.
- By deepening our understanding and consideration of the crime ecosystem, it is possible to take measures in line with the overall picture of crime.
- Yahoo, which operates Yahoo! Shopping, utilizes a real-time fraud detection system operated by a dedicated monitoring team.
table of contents
- Unauthorized use
- Framework of measures
- Anti-fraud measures as seen in the example of Yahoo!
- Effective technology to combat fraud
- What companies should do when their company name/service is deceived
*You can see the contents of this article in the video.
Unauthorized use
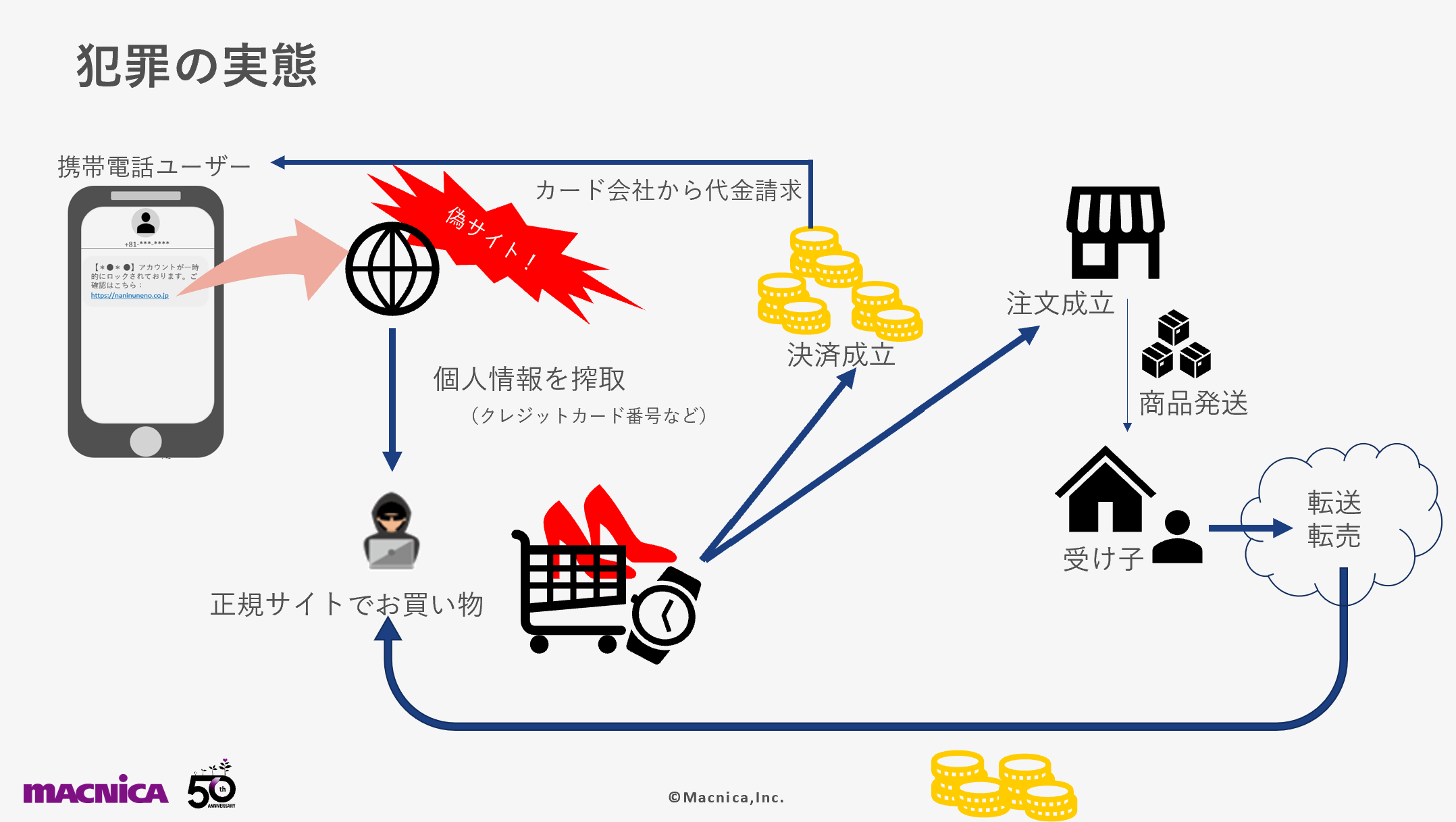
First, let's take a look back at the flow of fraudulent use by phishing scams, using an EC site as a typical example. What often happens is that a short message masquerading as a legitimate service is delivered to the SMS of a smartphone, and by tapping the URL in it, you are guided to a fake site, and by entering your ID and password, your information is stolen by criminals. It will end up. And it is a series of flows that the criminal who impersonates the person purchases the product on the genuine site and suffers financial damage.
Next, we will explain how criminals are exploiting fraudulent use after exploiting legitimate user login information by phishing.
When criminals impersonate themselves and make purchases on legitimate sites, the money is billed to them (the phishing victims). The product is set to be delivered to the location specified by the criminal, not the person's home. When the product is shipped from the shop, another member called the receiver receives the product and resells it, or the receiver receives the product after transferring it to another place and resells it.
Framework of measures
In order to eradicate the damage caused by phishing, it is possible to take countermeasures in line with the overall picture of crime by deepening our understanding and consideration of the criminal ecosystem. Until now, phishing countermeasures have centered on early detection and takedown of phishing sites (or de facto harmlessness through access blocking). These measures will continue to be effective in the future, but it is also important to combine upstream and downstream measures against crime to break the chain of criminal activity.
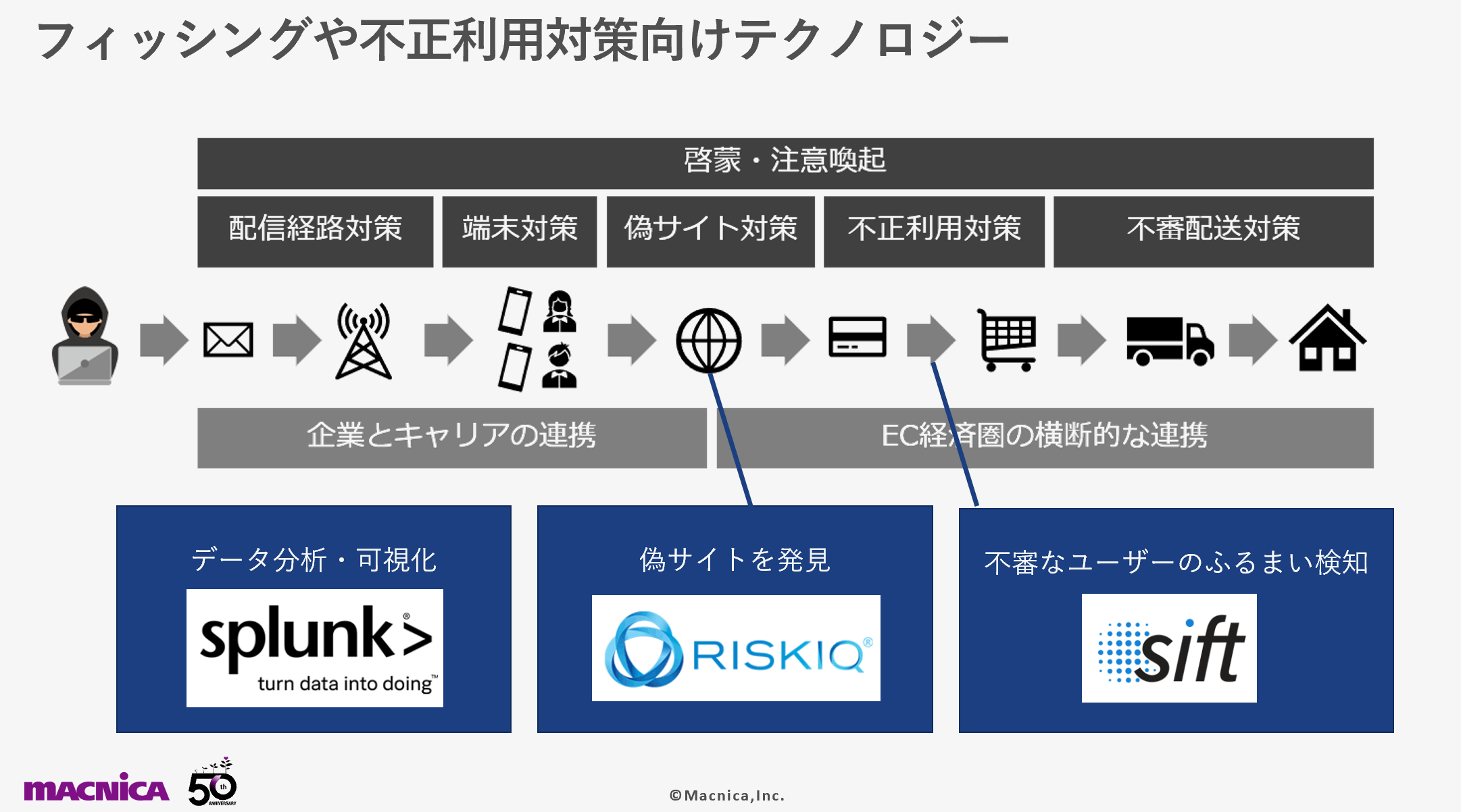
When considering countermeasures, define a framework that follows the flow of phishing.
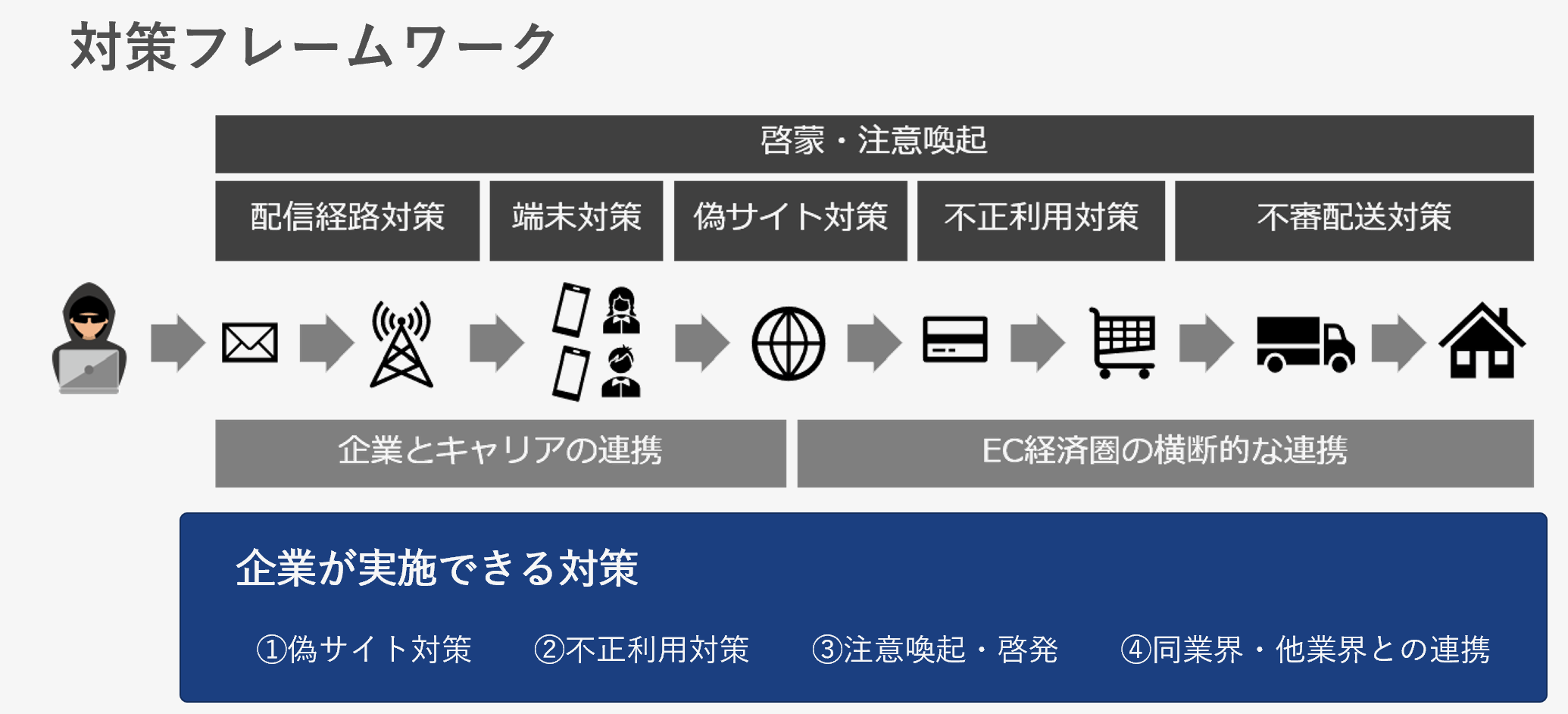
The diagram above shows the order of crimes from left to right. Some of these measures are implemented by each company, but it is also important to have horizontal cooperation across the industry, such as cooperation between SMS delivery companies, e-commerce sites, and home delivery companies. In this article, we will delve into the “anti-abuse” part in more detail.
Anti-fraud measures as seen in the example of Yahoo!
In this article, we will introduce measures against fraudulent use of credit cards that Yahoo!
Yahoo! Shopping, which operates Yahoo! Also, at Yahoo! One of the biggest factors in reducing fraud since 2019 is the introduction of fraud detection systems.
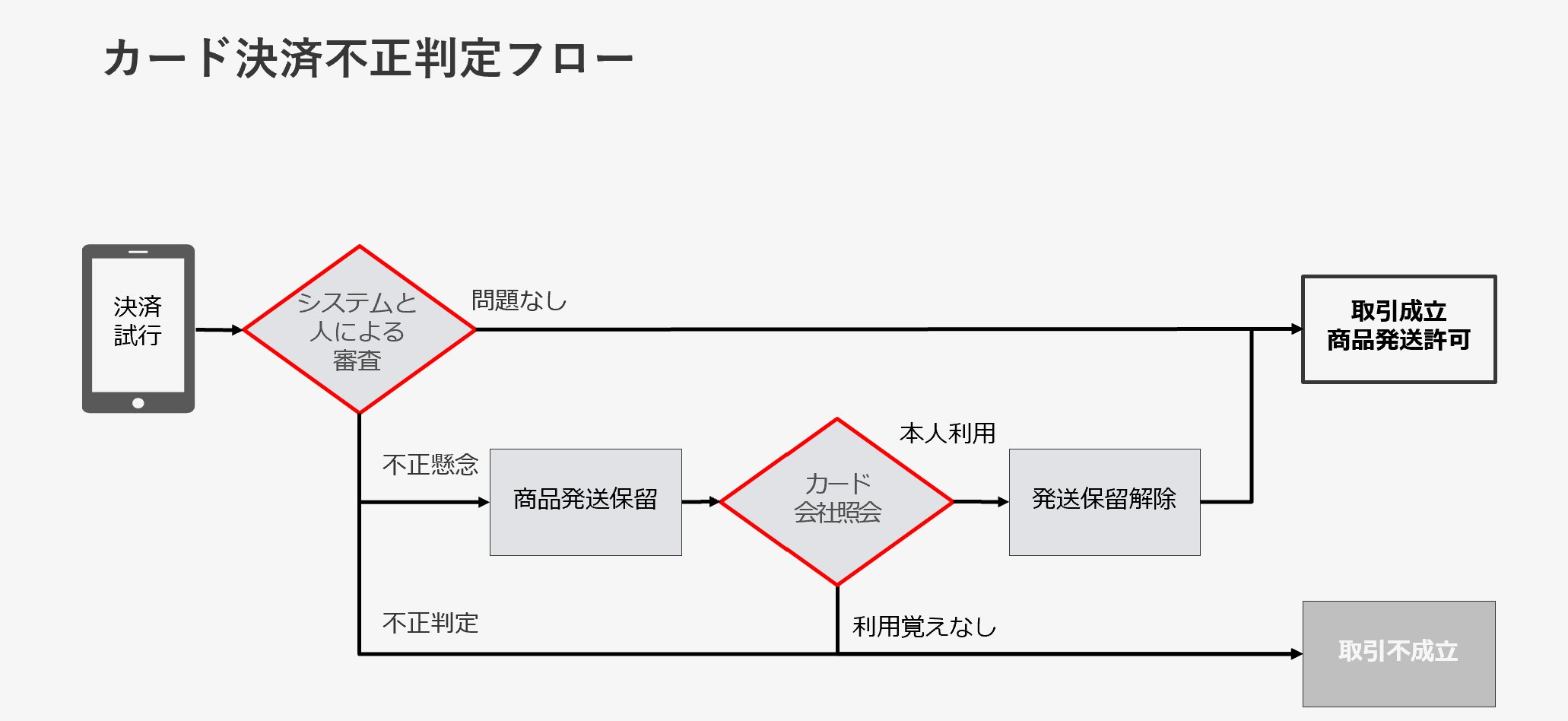
The system itself is based on Yahoo! All payment transactions pass through this fraud detection system to determine in real time whether it is fraudulent, whether there is a problem, or whether there is any concern about fraud. If there is a concern about fraud, we ask the store to hold the shipment of the product, check with the card company, and if there is no problem, we will ship it. Inquiries to the card company are made in two ways: attribute inquiry and identity verification. Regarding attributes, it is the process of querying the shipping information on the order and checking whether that information matches the cardholder information. (From August 17, 2022, Yahoo! Shopping has introduced EMV3D Secure for some transactions determined to be fraudulent.)
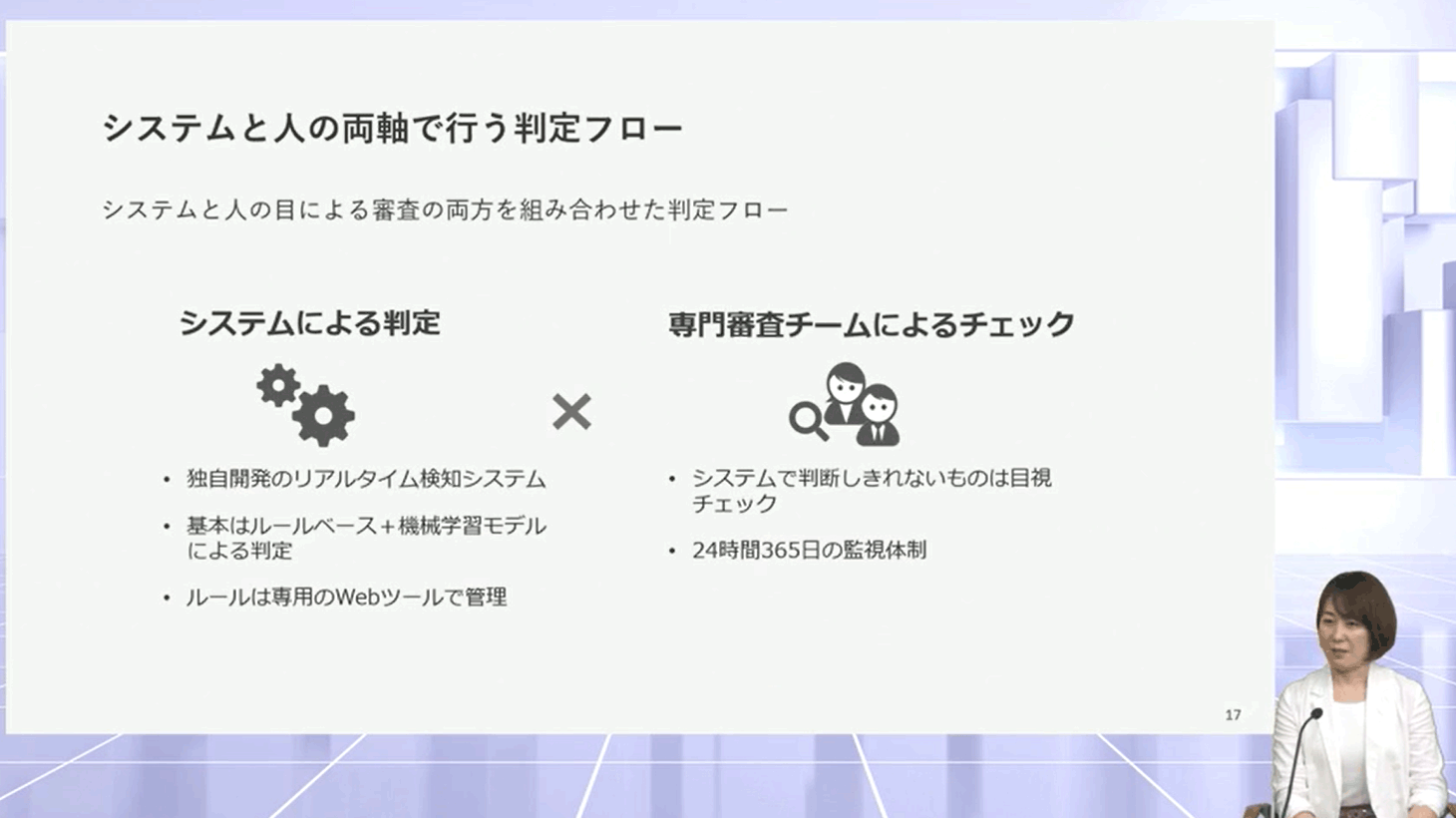
The basis is rule-based judgment, and a machine learning model is also used. Rule making is managed by our own web tool. If fraud occurs, the corresponding rules are immediately created to detect and prevent it, but in some cases, it is also possible to proactively set rules in advance by using prediction models based on machine learning. going. In addition, as a human system, checks are also performed by a specialized review team, and unauthorized use is thoroughly monitored by a monitoring system 24 hours a day, 365 days a year.
Effective technology to combat fraud
Yahoo operates its own system, but not all companies can prepare their own environment. Effective anti-fraud tools for businesses include:
- Splunk: Integrated aggregation, analysis, judgment, and visualization of transactions and various logs
- RiskIQ: Identify websites of your company and affiliated companies, collect and visualize information such as server certificates and IP addresses of discovered fake sites
- Sift: Detects suspicious user behavior and prevents spoofing and fraudulent payments
What companies should do when their company name/service is deceived
In the first place, how should I notice that my company name and company service have been deceived? In fact, there are many patterns that users who discover fake sites notice when they contact companies.
(1) Develop internal systems
First of all, it is important to improve the system within the company. If the scale of the EC site operated by the company grows, it is possible to set up a system to set up a dedicated department, but in general, the point of contact for customer service will be the center, and there will be no choice but to respond on a case-by-case basis. In doing so, it is essential that the department that normally serves as the point of contact and the department in charge of security within the company work closely together.
② Alert
What's even more important is getting the user's attention. The biggest victims of unauthorized use are users, and it is necessary to consider that it is the responsibility of companies to promptly provide accurate information to users.
In the event of a phishing attack, it is important to convey correct information to users quickly, accurately, and safely.

For example, you should avoid asking the user to "make sure the URL is correct". Criminals make full use of URLs that appear to be correct, so it is honestly extremely difficult for users to determine whether the URL is correct.
You should also avoid messages asking you to confirm that your email address or sender is correct. This is because email addresses and senders can be easily spoofed, so users cannot determine whether they are correct.
In addition, we should avoid messages that say that it is safe if the URL starts from the correct domain, and in actual examples, there are fake site URLs that use the same domain as the legitimate domain until the middle. Avoid encouraging people to make judgments based solely on domains.
And the URL of the phishing site, which is a fake site, should not be posted as it is. This is because if you post it as text as it is, you may access it and cause secondary damage. When posting, use detoxified items or images to call attention.
As you can see from the above points, it is important to call attention to the basic premise that it is difficult for users to distinguish whether it is a phishing site or not.
In addition, when calling attention, its ability to transmit is also important. Of course, you can send information on company websites and SNS, but if you use the emergency information notification provided by the Anti-Phishing Council, there are cases where many media will pick up on it. It is effective to make good use of external mechanisms.
\You can watch the contents of this article in the video/
Available immediately after registration
Inquiry/Document request
In charge of Macnica Imperva Co., Ltd.
- TEL:045-476-2010
- E-mail:imperva-info@macnica.co.jp
Weekdays: 9:00-17:00