
Imperva
Imperva
Dangers lurking on e-commerce sites
As shopping on e-commerce sites has become easier, online payments are on the rise. This is also accompanied by an increase in damage caused by "Web skimming attacks," which steal credit card information directly from payment pages.
"Web skimming attacks" are carried out by tampering with the script on a payment page so that payment information is sent not only to the web server but also to the attacker.
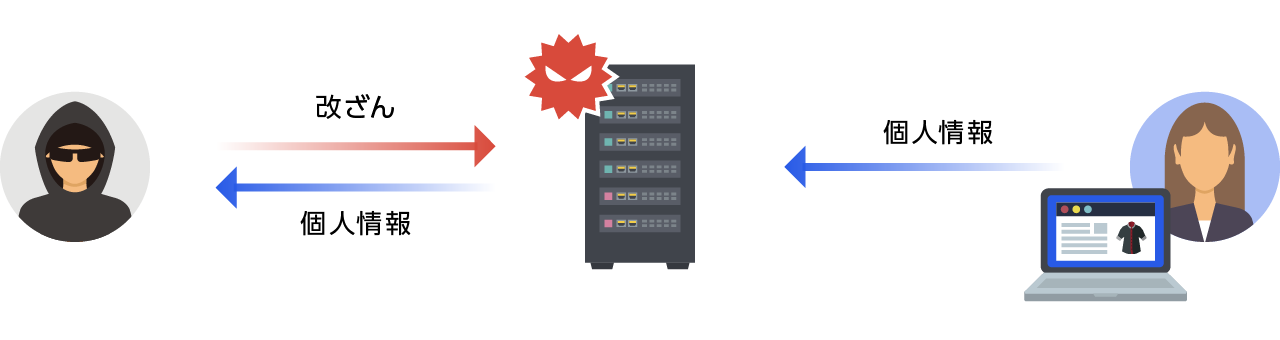
A suspected web skimming attack
①Leaking of personal information and credit card information of customers who used Company A's EC site
- The incident was discovered after an external party contacted us regarding concerns about information leakage.
- Leaked from around July 2021 to May 2024
② Personal information leaks due to unauthorized access to B Union's online shopping site
- It was discovered after receiving a report from an outside source that some of the programs on the site may have been illegally tampered with.
- Leaked from around April 2021 to May 2024
→ There are many cases of information leaks over a long period of time
One reason for this is that script tampering is done in a way that makes the website look and function normally, making it difficult for users and operators to notice.
Therefore, special measures are required
How to protect against web skimming attacks
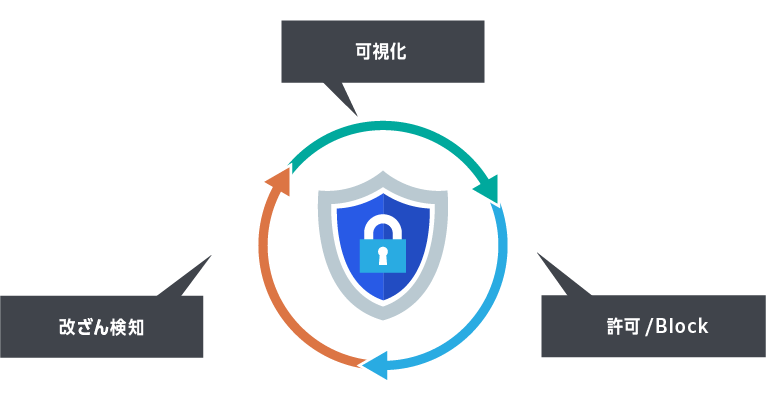
A list of scripts used on the payment page is visualized and their contents are examined. The payment page is then corrected by "allowing normal script execution" and "blocking suspicious/unnecessary script execution." This is carried out periodically, and if script tampering is confirmed, action is taken immediately. This maintains the integrity of the payment page and protects against web skimming attacks.
Imperva Client-Side Protection
Imperva Client-Side Protection is a solution that provides script management and tamper detection to ensure the integrity of scripts used on payment pages.
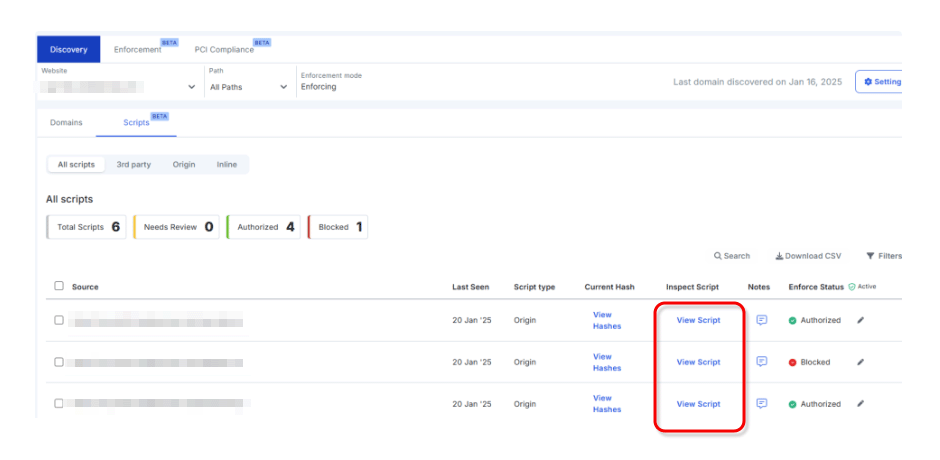
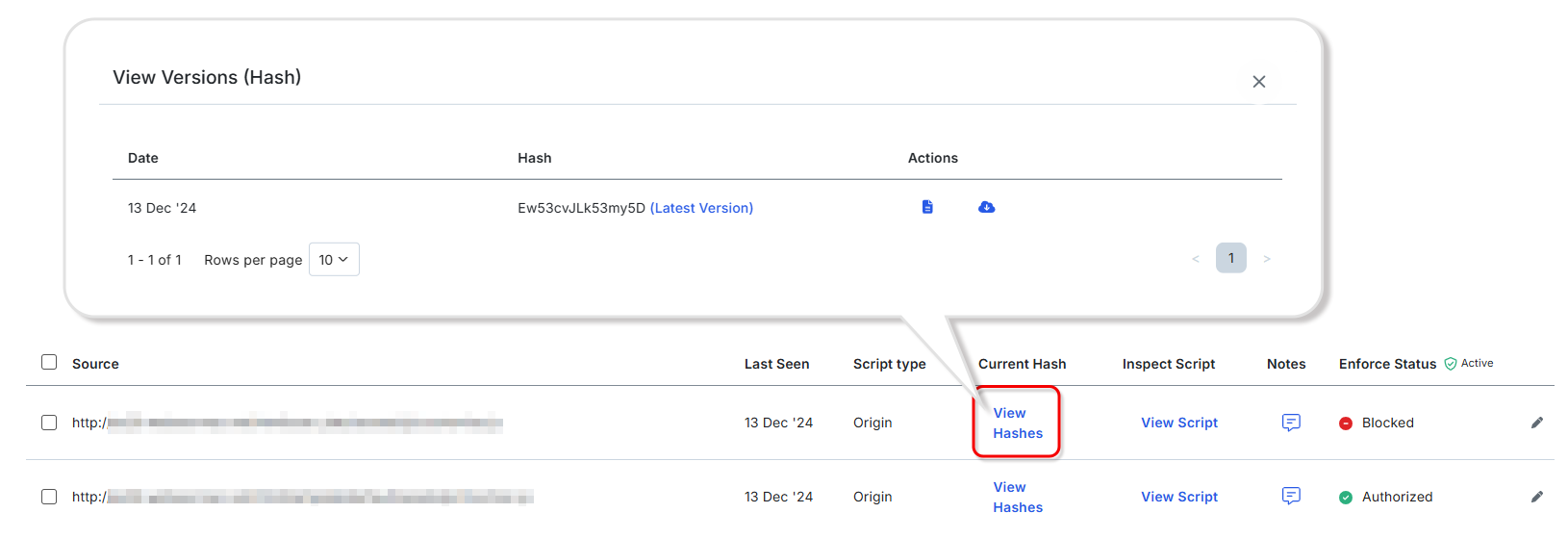
View Script (Visualization)
It is possible to detect the list of scripts running on the payment page and check their contents on the GUI. It is also possible to scan the scripts using AI and summarize their contents.
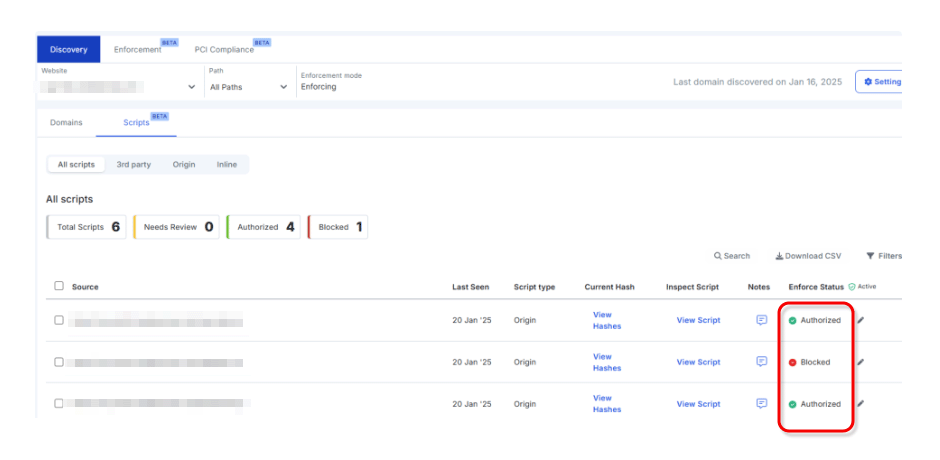
Enforce Status (Permit/Block)
You can manage script permissions from a central location.
If you set it to Block from the GUI, the script will stop running, allowing you to quickly respond to unauthorized scripts.
View Hashes (Script Tampering Detection)
You can check the modification date and time and hash value of each script, making it possible to detect unauthorized editing or tampering of scripts.
How to Deploy Imperva Client-Side Protection
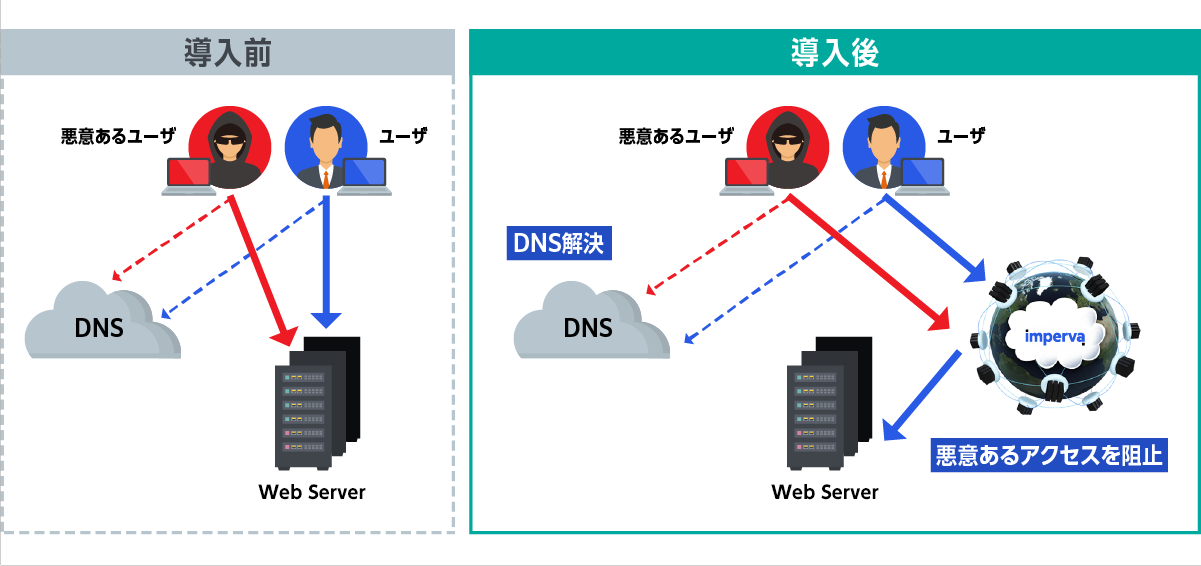
Available as an optional feature of Imperva Cloud WAF.
There is no need to change the configuration or modify the web server upon installation.
Imperva Cloud WAF
It can be implemented by changing the DNS name resolution destination to Cloud WAF, allowing for flexible implementation that is not dependent on your applications or deployment environment.
PCI DSS 4.0 Compliant
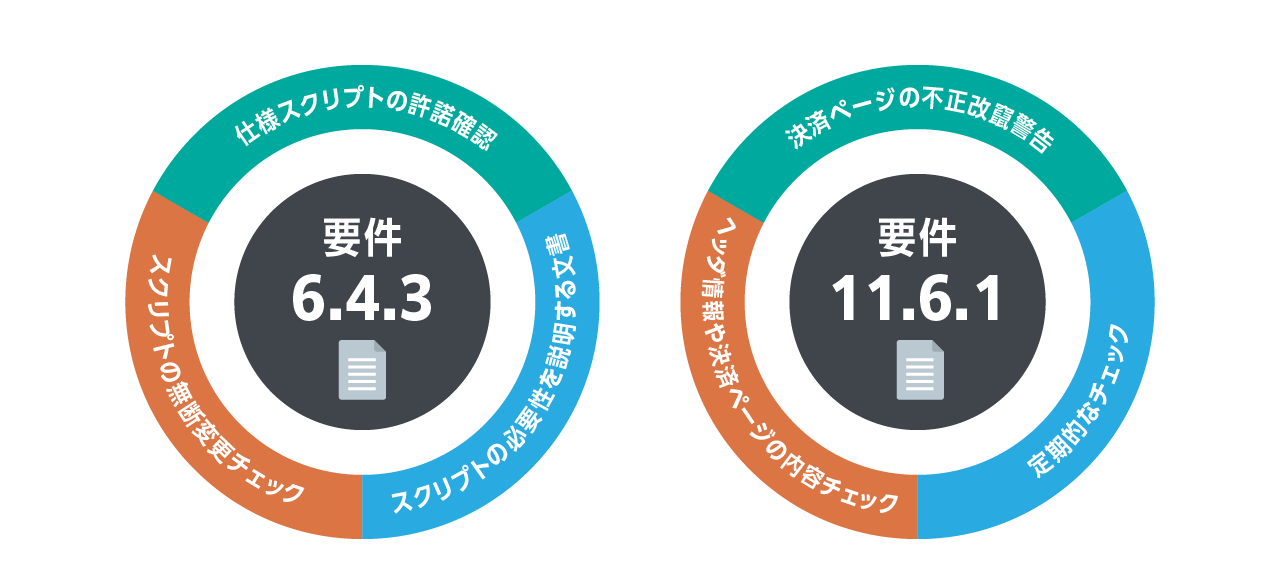
Businesses that handle credit card information must comply with an international security standard called "PCI DSS (Payment Card Industry Data Security Standard)".
Measures to prevent web skimming are specified in requirements 6.4.3 and 11.6.1.
Imperva Client Side Protection helps you achieve compliance.
Inquiry/Document request
In charge of Macnica Imperva Co., Ltd.
- TEL:045-476-2010
- E-mail:imperva-info@macnica.co.jp
Weekdays: 9:00-17:00