
Imperva
Imperva
Thorough explanation! Trends in "Web skimming" attacks targeting e-commerce sites and correct countermeasures
Introduction
PCI DSS v4.0, released in April 2022, has new requirements against “web skimming” attacks. Web skimming is an attack that steals credit card information that is mainly entered for online shopping, etc. Currently, it is raging both in Japan and overseas. The methods are becoming more sophisticated year by year, and now all websites are exposed to the threat of web skimming, such as even websites that do not retain card information, such as theft of card information.
Protecting customer information is a responsibility that businesses must fulfill in developing web businesses. However, the reality is that there is still a lot of misinformation about how to specifically take measures against web skimming.
Therefore, in this article, we will explain web skimming attacks and the latest trends in a way that anyone can understand, and introduce specific countermeasures.
What is the web skimming attack raging in Japan?
What is a web skimming attack? When we use online shopping sites, etc., we enter personal information such as names, addresses, and credit card numbers. In a web skimming attack, a website contains a script that steals personal information entered in a form, and when that script is executed, all the entered information is sent to the attacker's server. . This attack is characterized by the fact that the data is not stolen from the server, but sent directly from the user's browser to the attacker.
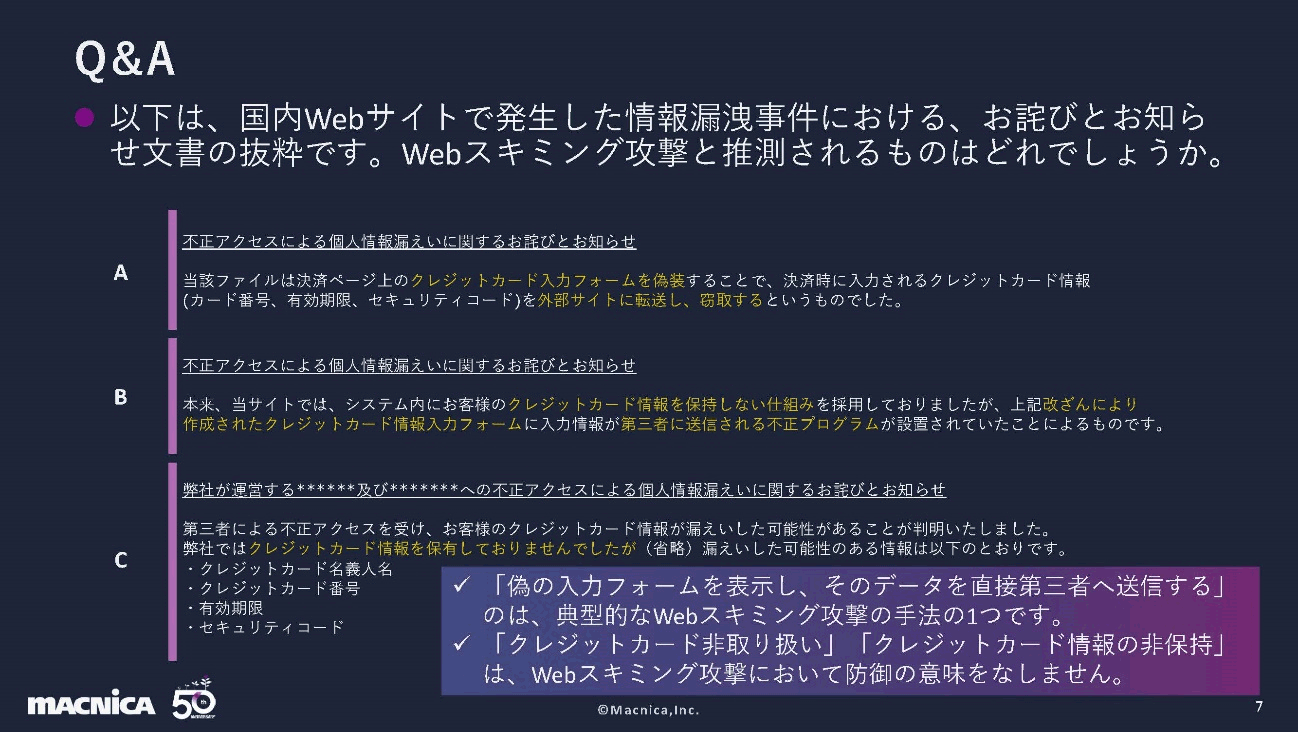
Here are three types of "apologies and notices" for information leakage incidents that occurred on domestic websites. It can be inferred that both are due to web skimming attacks. Web skimming attacks are commonly publicized as "unauthorized access". Contrary to the recognition of the word, it is clear that the threat is raging even in Japan.

"Display a fake input form and send the data directly to a third party" in the sentence is one of the typical techniques of web skimming attacks. "Non-introduction of credit card payment" and "non-retention of credit card information" are not defenses against web skimming attacks.
In April 2022, measures against web skimming were specified as a requirement in PCI DSS v4.0, an international common standard for card information security. Web skimming countermeasures should be taken by website operators without relying on user-side endpoint security. Protecting customer information with correct web skimming measures will also protect your business.
Flow of Web Skimming Attacks and the Need for Web Skimming Countermeasures
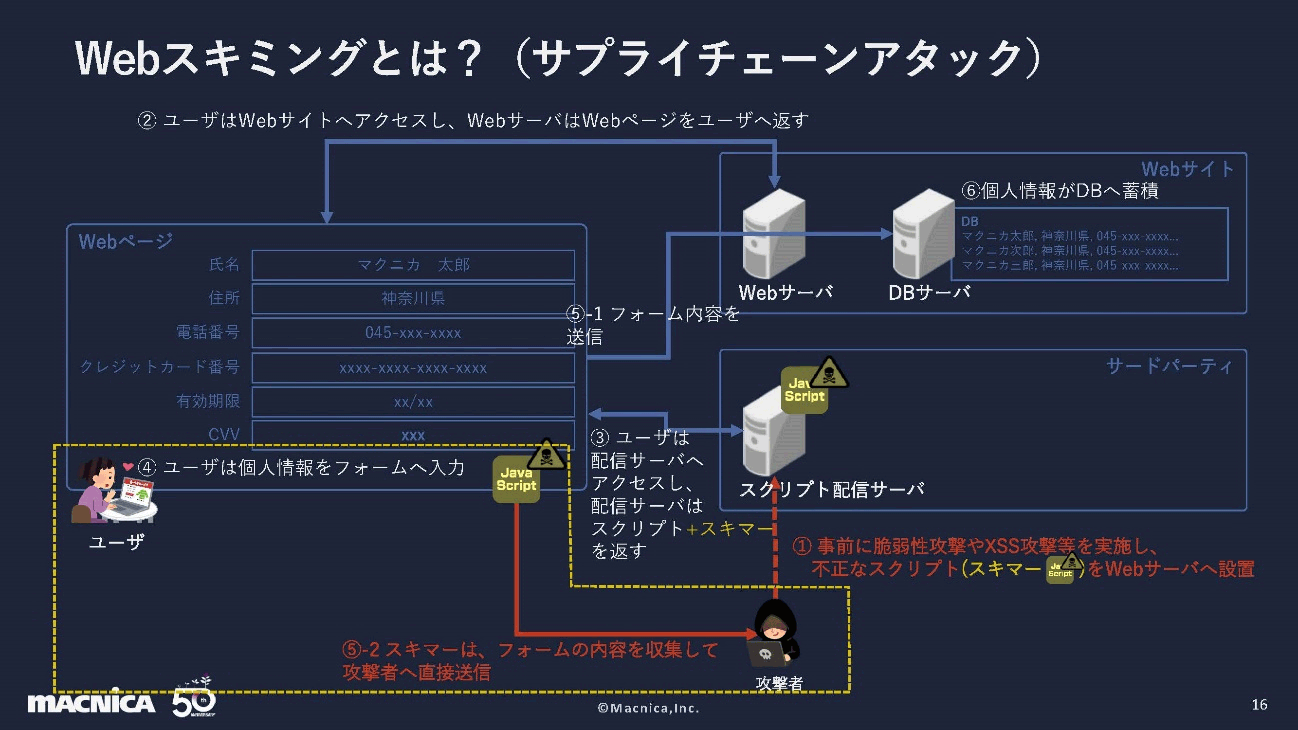
Let's take a look at the flow of web skimming attacks. Attackers perform tampering attacks and vulnerability attacks in advance, and install dangerous scripts called skimmers on Web servers. When a user accesses in this state, the web server returns a response containing the skimmer. When a user enters personal information into a form and submits it, the skimmer collects the form content and sends it directly to the attacker.
Web skimming attacks are difficult for websites to detect because data is sent directly from the user to the attacker. In many cases, the damage is discovered by contacting the credit card company.
As an advanced form of web skimming attack, there is an attack form called supply chain attack. The difference from a basic web skimming attack is that the skimmer is set on the third party that the website refers to rather than the website itself. It is common to reference resources such as HTML, images, and stylesheets from external third parties when constructing web pages. Placing a skimmer here is a supply chain attack.
Other attacks are the same. Skimmers come in when users visit your website and access third parties as additional resources. Once the information is entered in the form and the skimmer is run, the data is submitted. This is also difficult to notice because the data is directly leaked from the user to the attacker.
In 2021, there will be supply chain attacks in Japan as well. Web skimming attack by third party acquisition of tag-type access analysis domain. When using the tag-type access analysis service, embed the script for downloading the access analysis script as a Loader in the web page. When the user accesses the website, Loader is executed and the access analysis script is downloaded.
In this case, the access analysis service was terminated and the domain was released. Originally, you have to turn off the Loader on the website side. However, a malicious third party acquired this domain while it was left undeleted. The skimmer was delivered. The web page itself has not been attacked or tampered with by anyone. In this way, in a supply chain attack, damage is caused in a chain reaction from parts other than the company.
Server-side security that protects against web application attacks such as WAF (Web Application Firewall) and tampering detection cannot protect against web skimming attacks. Any website can be subject to web skimming attacks, and countermeasures are required. Whether it's a supply chain attack or an attack on your own website, it's important to have an approach that prevents skimmers from coming in from anywhere.
To protect your site from web skimming. How to think about correct web skimming countermeasures
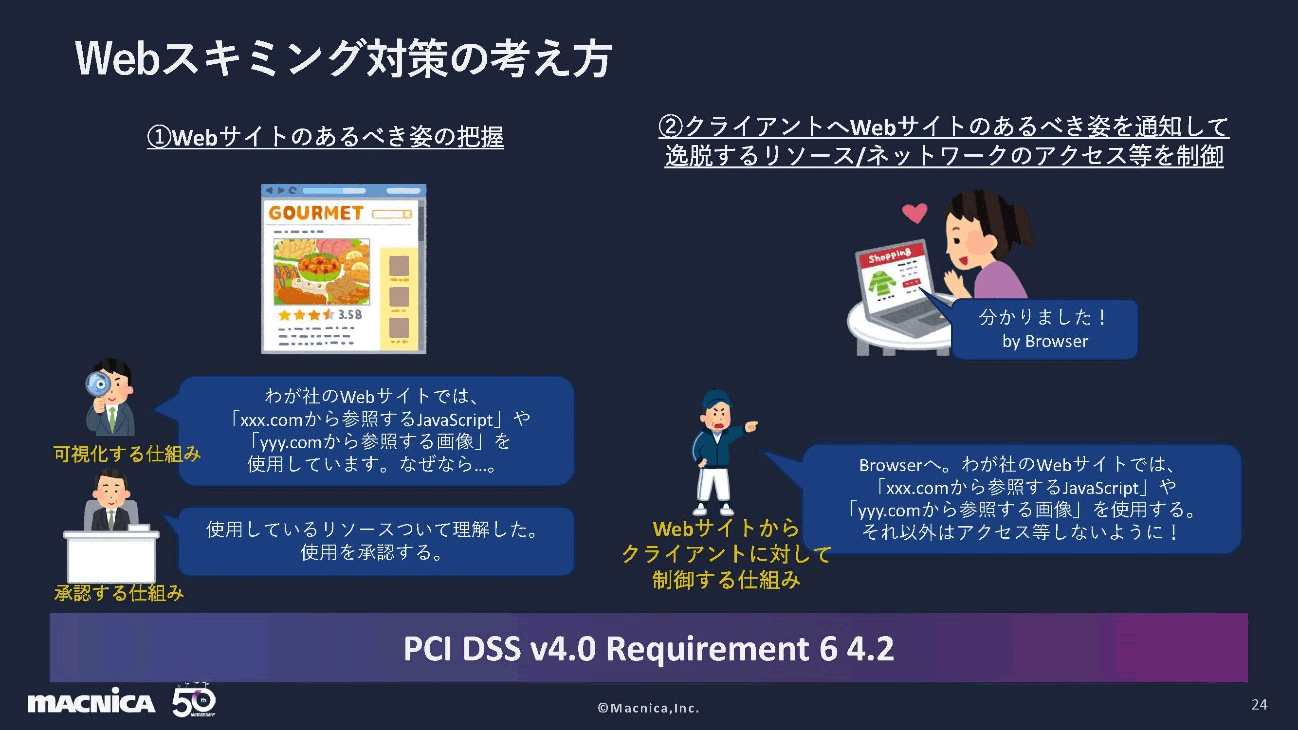
So, what kind of concrete approach should we take? As a way of thinking about web skimming countermeasures, the flow of attacks can be divided into two stages. The stage of setting up the skimmer as a preliminary preparation and the stage of collecting data with the skimmer. You can think of countermeasures at each stage, but the important thing is to prevent web skimming from succeeding. In other words, you need a defense to keep the skimmer from running and data from being sent out.
Let's go into detail. First of all, the countermeasures start with “(1) Grasping the ideal form of the website”. Use visualizations of your website to identify the resources you are using and clarify the need for external scripts and images, if any. Then set up a mechanism to approve it. This is more of a development rule point of view than a technical point of view. In this way, you can establish what your website should look like, a kind of bill of materials that your site uses.
Next, “(2) Notify the client of the ideal website and control access to deviating resources and networks”. In other words, you tell your browser what scripts and images to use on your website, and what other resources to disallow access to. This makes it possible to prevent the execution of suspicious scripts and the transmission of data externally. As a requirement of PCI DSS v4.0, it is required to implement three such "visualization mechanism", "approval mechanism" and "control mechanism".
What kind of technology should I use? There are two possible ways to control browser behavior. One is to use CSP, SRI, Nonce, etc., which are installed in browsers as standard Web technologies. Another method is to embed an agent for monitoring Java Script behavior, including a skimmer, into a web page.
Let's take a look at how each technology works. Let's take CSP as an example of a web standard technology. Clearly indicate the resource access permission by Content-Security-Policy in the response returned from the server when the user accesses the website. The browser follows suit and only accesses permitted resources. This prevents unauthorized sites from downloading skimmers or sending personal information to attackers' websites.
Next is when using the JavaScript Agent. Skimmers use JavaScript web APIs such as XMLHTTPRequest to send personal information out. Therefore, create an extended type XMLHTTPRequest with a validation function and replace the original XMLHTTORequest. When the skimmer tries to send data, it runs the validation function of the extended XMLHTTPRequest, preventing data from being sent out.
Whether it's Web standard technology or JavaScript Agent technology, it's pointless if you don't set it up correctly. With both approaches, evasive behavior and evasive attacks by attackers have been observed. For example, in the JavaScript Agent-based case, if the skimmer is loaded first and a copy of the XMLHTTPRequest is made, then it is technically possible to send the data out because it can bypass the extended XMLHTTPRequest validation.
To prevent this, do not load any other resource before the JavaScript Agent has finished replacing the extended XMLHTTPRequest. However, in practice, there are cases of failures in which the rules are ignored and another resource is loaded first.
Next, we will introduce two typical technologies for understanding the ideal form of a website: the "crawling type" and the "telemetry type." The crawling type is a method of using an external crawling service to access a web server or website and check all the resources used. Since the file is actually read and analyzed, it is sometimes done in conjunction with detailed analysis using intelligence. While there is an advantage of being able to visualize automatically, it is necessary to be careful when dealing with login, two-factor authentication, CAPTCHA authentication, etc., and dealing with pre-publication pages.
Telemetry type is a method to grasp the structure of the website based on the actual access by using the reporting function of CSP and JavaScript Agent. Since it is based on human access, it is easy to handle login, two-factor authentication, CAPTCHA authentication, pre-publishing pages, etc. On the other hand, at the time of initial introduction, it is necessary to manually access all pages, which is time-consuming.
Comparing the crawling type and the telemetry type, the merits and demerits are contrasting. It is necessary to be aware of the characteristics of your company's website and select a solution that can be operated.
Summary
So far, we have introduced an overview of web skimming attacks, the necessity of countermeasures, and key points. In order to implement proper web skimming countermeasures, it is necessary to have knowledge about web skimming attacks themselves and countermeasures. I have heard of many cases where a lack of this led to wasted man-hours. At Macnica, we support our customers' web businesses with a variety of web security solutions, including web skimming countermeasures. If you are interested or have any questions, please feel free to contact us.
You can download web security-related materials from the following.
Inquiry/Document request
In charge of Macnica Imperva Co., Ltd.
- TEL:045-476-2010
- E-mail:imperva-info@macnica.co.jp
Weekdays: 9:00-17:00