solution
Application for evaluation machine
"Ransomware execution demo!" Emotet / ransomware countermeasures with cloud storage! ?
Emotet/ransomware is spreading damage even in Japan, but did you know that cloud storage can be used as a countermeasure? Based on actual ransomware samples, we found that cloud storage is effective as a recovery measure against Emotet/ransomware. Therefore, this time, we will look at how to use cloud storage, which is attracting attention as a countermeasure against Emotet/ransomware.
table of contents
- In Japan, the possibility of being exploited by Emotet is expanding
- Details of damage caused by Emotet and route of infection
- More and more companies are quitting PPAP, what is the reason?
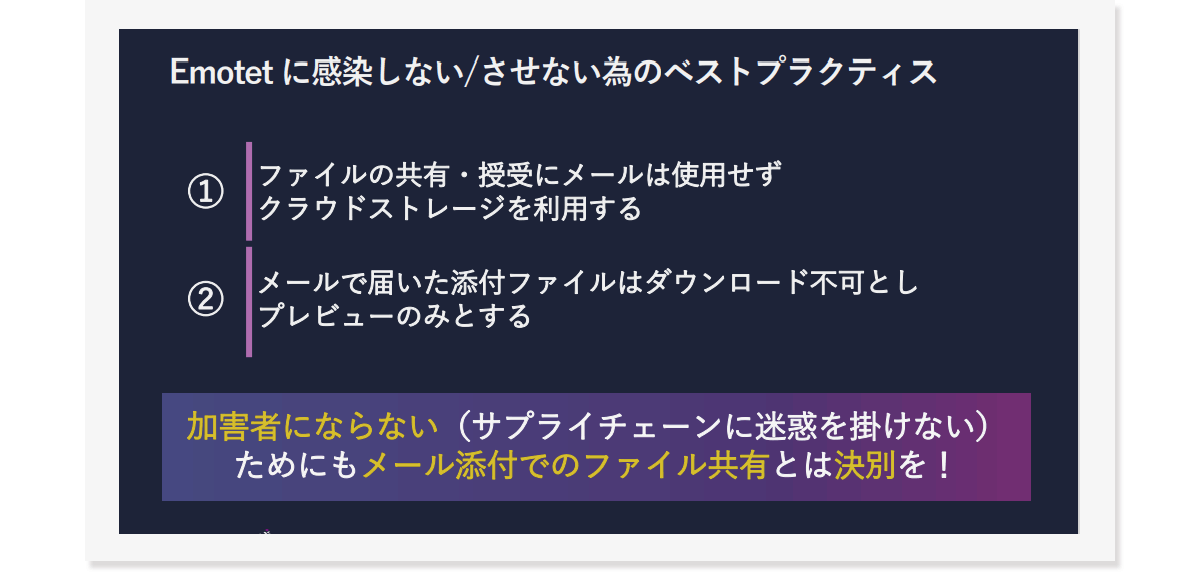
- Three points to reduce the risk of Emotet infection
- Flow to Emotet infection
- How to use cloud storage
- How to use cloud storage as a recovery solution
- Why cloud storage is effective for recovery from ransomware damage
- summary
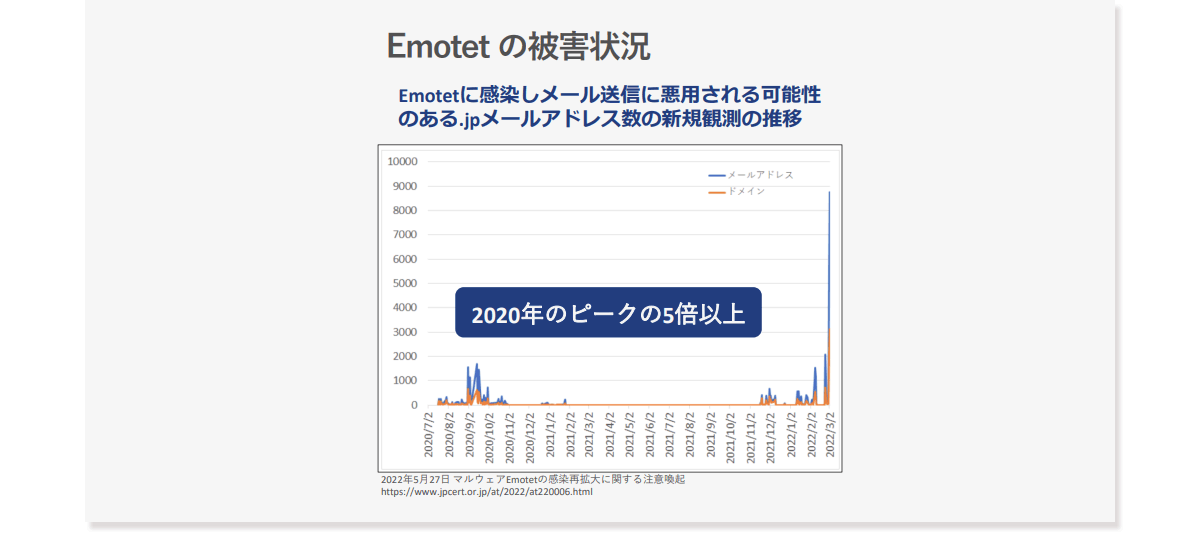
In Japan, the possibility of being exploited by Emotet is expanding
Many people are aware that the damage caused by Emotet has been increasing in Japan. According to a JPCERT study, the number of .jp email addresses that can be infected with Emotet and misused to send emails has increased by more than five times as of March 2022 compared to the peak infection period in 2020. This is clear from the survey data. In addition, there is no end to press releases from companies that have been affected by the infection, and many companies are experiencing damage from Emote. As Macnica handles many security solutions, many companies have decided to adopt cloud storage in the wake of the damage caused by Emotet, and I have the impression that more and more companies are considering cloud storage from a security perspective.
Details of damage caused by Emotet and route of infection
The damage caused by Emotet can be roughly divided into three categories. Specifically, the company's information is extracted, it becomes the sender of Emotet emails, and other malware is loaded as a downloader. Concerning the infection route, in the case of Emotet, in many cases, it originates from e-mail, and Excel and Word files containing macros for infecting Emotet, or those files encrypted with ZIP are sent to e-mails. Attached. By opening the file, it will be infected if macros are enabled. Email password files are difficult to detect and easy to bypass security, so the number of cases where they are used for attacks is increasing.
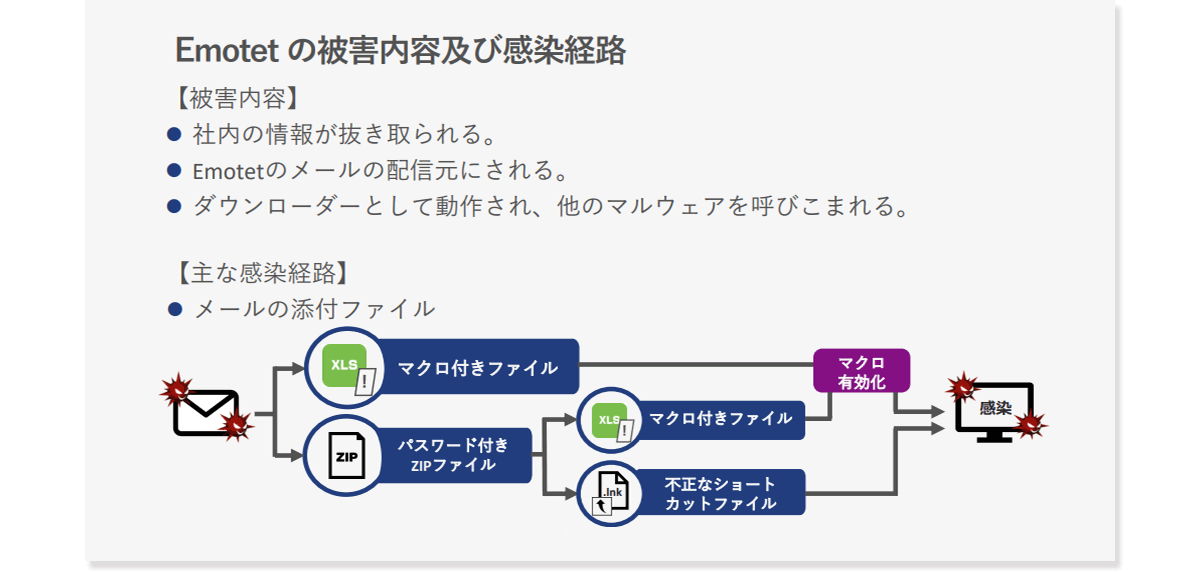
At that time, in April 2022, as part of Microsoft's security measures, we have begun to take measures such as forcibly disabling macros in Office files received via email or the web. However, in order to counteract this movement, the current situation is that the infection method is shifting from the method using Office files to the method of infecting password ZIP with an illegal shortcut file.
More and more companies are quitting PPAP, what is the reason?
For attachment encryption, PPAP should also be mentioned. PPAP means that when you attach a file to an e-mail and send it, the file is ZIP-encrypted and sent, and the password for decompression is sent in a separate e-mail. It is said that the reason behind this procedure was to prevent information leaks and erroneous transmission of attachments containing personal information when sending emails.
Originally, passwords were supposed to be communicated via other channels, such as oral communication over the phone or sending by fax, but due to the complexity of the operation method, the rule was changed that passwords could be sent by separate e-mail. It has been used by many companies. However, if the attached file and the password are sent through the same channel, the problem is that if the recipient is sent to the wrong address, the countermeasures will be meaningless.
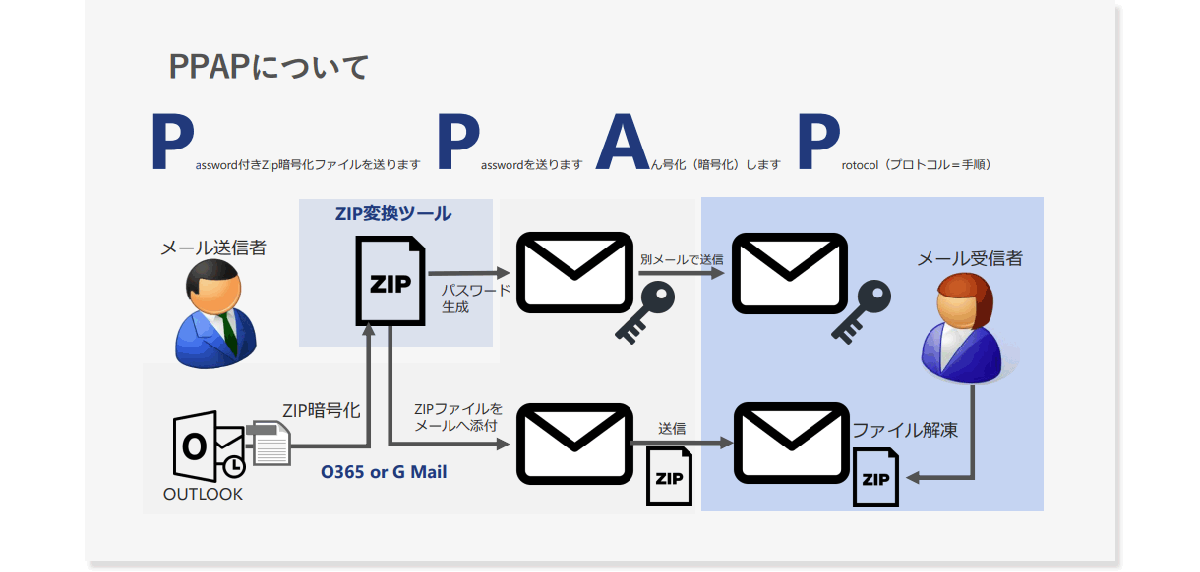
For this reason, the trend of moving away from PPAP is accelerating these days. The government's proposal to abolish password-protected ZIP files has become a hot topic because it has become a mere countermeasure against erroneous transmissions, and it also reduces work efficiency and productivity. In addition, considering the infection route of Emotet, it is difficult to perform virus checks on encrypted ZIPs during email security inspections. companies are also emerging.
Three points to reduce the risk of Emotet infection
Considering the risk of PPAP and the infection route of Emotet together, there are three main points to practice in order not to be infected with Emotet. First, do not unzip or open ZIP-encrypted attachments. It may contain files with malicious macros or shortcut links. Second, do not open suspicious attachments. Please note that plaintext Office files that have not been ZIP-encrypted may be directly attached and sent. And the third is disallowing enabling macros in attachments. If the user downloads the attachment locally and has macros enabled, any malicious file will be infected.
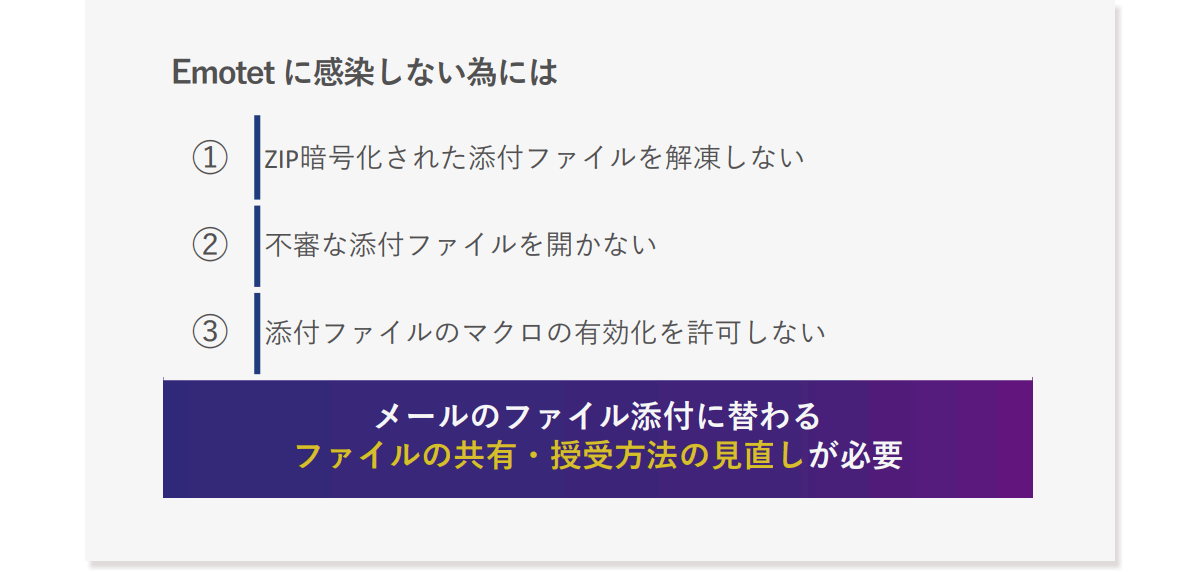
Based on these, you can understand that it is necessary to review the method of sharing and receiving files instead of attaching files to emails.
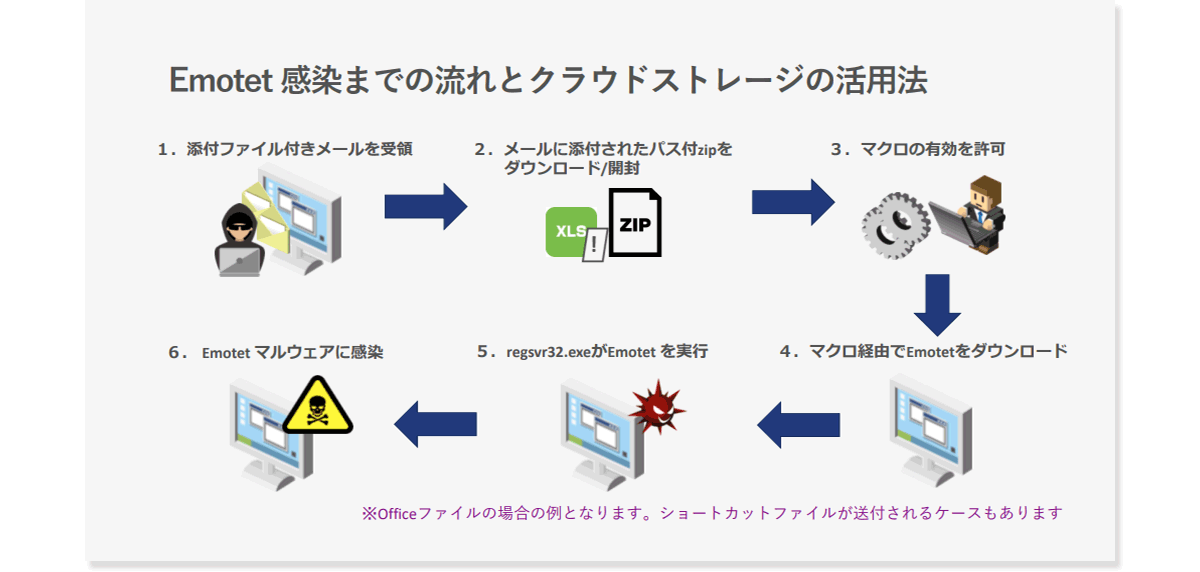
Flow to Emotet infection
Here, we will look at how cloud storage should be used, along with the flow leading up to the Emotet infection.
An Emotet infection begins when a user receives an email with an attachment, then downloads/opens the attached Excel file or password-protected ZIP file.
As a point of caution, in the case of password-protected ZIP files, the contents cannot be scanned except for some products. Also, if an Office document is directly attached, it may evade detection immediately after the attacker changes their tactics. Also, even if you are isolated by security products, if you allow users to release emails, it is possible that users will release emails themselves by means of social engineering and reach Box.
Next comes the stage where the user allows macros to be enabled. Remember, opening a file will not infect Emotet unless macros are enabled. However, in many cases, a message prompting you to enable macros is displayed when you open the file, and if you allow this, the download of Emotet will start, which is the general flow until infection.
How to use cloud storage
In any case, in order to prevent Emotet infection, it will be effective to share files in other ways instead of email, which is the source of infection. Cloud storage is attracting attention as a way to share such files.
Usage method 1
When you need to share files, it is an approach to ask the other party to use cloud storage. In other words, file sharing with trusted business partners is a method of creating a shared folder in cloud storage and storing and exchanging files there so as not to receive email attachments. For example, in the case of Box, when sharing files, you can set detailed access rights for business partners, such as file upload and editing rights, and preview only rights.
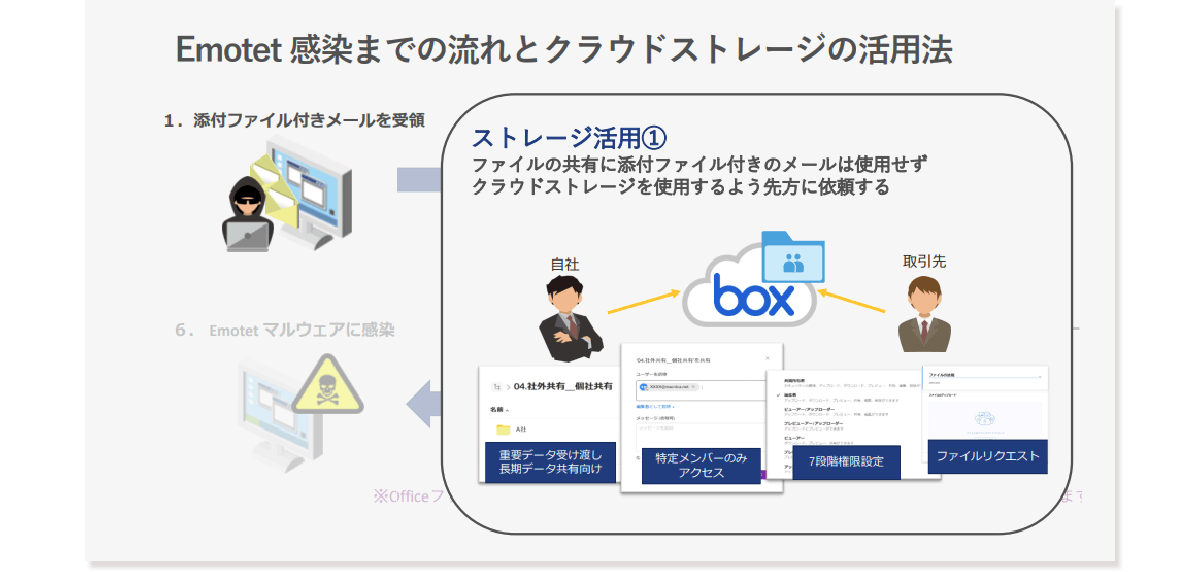
However, there are cases where this method does not gain understanding for file sharing in cloud storage depending on the internal policy of the other party and the level of IT literacy.
Usage method 2
In addition, we can introduce an advanced usage method, which is to create a mechanism to aggregate email attachments in cloud storage, which can be realized by combining cloud storage and email security products. For example, a solution called mxHERO peels off email attachments, uploads them to cloud storage, and delivers a link to the file instead. By using this solution, attachment files can be forcibly aggregated in cloud storage, and the sender does not have to change the conventional method of attaching files to emails, making it possible to achieve both security and convenience. It can be said that it is a mechanism.
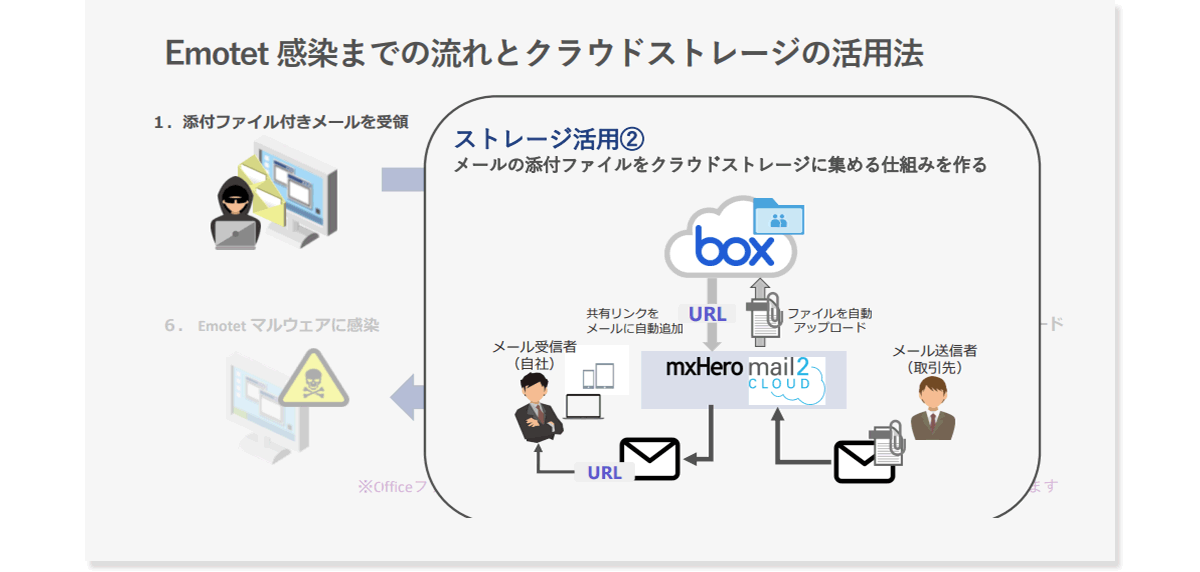
However, Office files attached in plain text can be previewed on cloud storage, but ZIP-encrypted files are uploaded to cloud storage as they are, so when checking the contents, download them locally and enter the password. Input required. In that case, if Emotet is planted in the file, it is impossible to escape from the conventional infection flow of prompting the activation of macros.
Usage method 3
The third way to use it is to disable file downloads and check with the cloud storage preview function. This is an approach that disables downloads by controlling the cloud storage side for the above-mentioned utilization method. Roughly speaking, the option is to give up downloading. Of course, if it is plaintext, you can preview it on the cloud storage side, but you cannot check the contents of the ZIP file. The point of this method is not to download files attached to e-mails, and the use of ZIP files is contrary to PPAP and Emotet countermeasures in the first place. Many companies are moving away from PPAP, and it is quite possible that ZIP-encrypted files will eventually be eliminated.
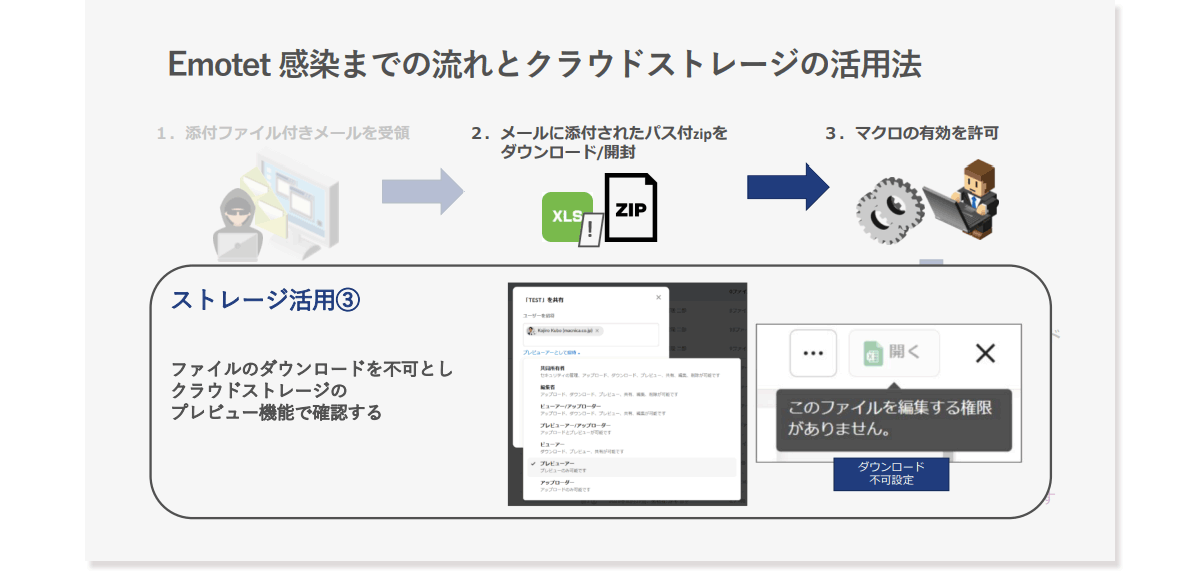
In addition, recently, attack methods such as opening Word or rich text files attached to e-mails have been introduced, so the importance of using the preview function of cloud storage will continue to increase in the future. The possibilities are quite conceivable.
As we have seen so far, the best practice to prevent Emotet infection is to use cloud storage instead of email for file sharing and transfer, and make sure that attachments sent by email cannot be downloaded. The point is that it should only be a preview. In order not to cause a horrific incident in which sending an attached file unwittingly becomes a perpetrator and has an impact on the entire supply chain, please stop sharing files as email attachments and try sharing them in cloud storage. .
How to use cloud storage as a recovery solution
Next, I will introduce how cloud storage can be used as a recovery solution against ransomware. As a definition of the term, backup means to duplicate the contents of data and save it on another storage device or medium in preparation for data corruption, and recovery means to restore data in the event of a failure. increase. Backup is one way of recovery.
In the first place, do you know how successful the companies that were actually damaged by ransomware have been in recovery? In fact, data shows that one-third of companies that have been hit by ransomware have failed to restore their data. In addition, 52% of respondents said they had paid the ransom in response to the ransomware demands, and 24% said they had paid but were unable to recover.
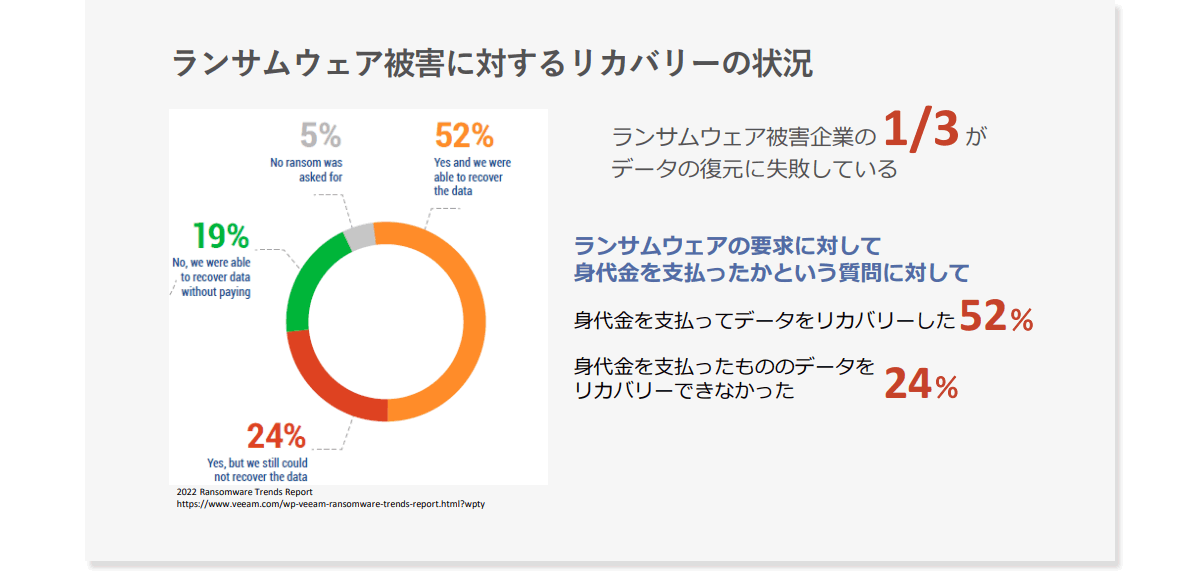
Many ransomwares tend to steal data first and then encrypt it, and the data tends to be passed to the attacker. As a result, it is no longer a matter of paying the ransom because not only can you not obtain the key for decryption without paying the ransom, but there is also the possibility of double extortion such as being threatened to reveal the stolen confidential information to the world. The reality is that 80% of companies have succumbed to attackers. On the flip side, it is also a sign that ransomware is having a tremendous impact on business.
Therefore, it is important to keep backups firmly, but there are cases where the attacker deletes the backup data before encrypting the PC or makes the backup server unrestorable. is also actually happening. As a result, there is no end to the number of companies that have backups but fail to recover. There are still many issues remaining when backing up, such as the complexity of backup rules and the difficulty of determining when to restore data, and we believe that many companies find it difficult to deal with them.
Why cloud storage is effective for recovery from ransomware damage
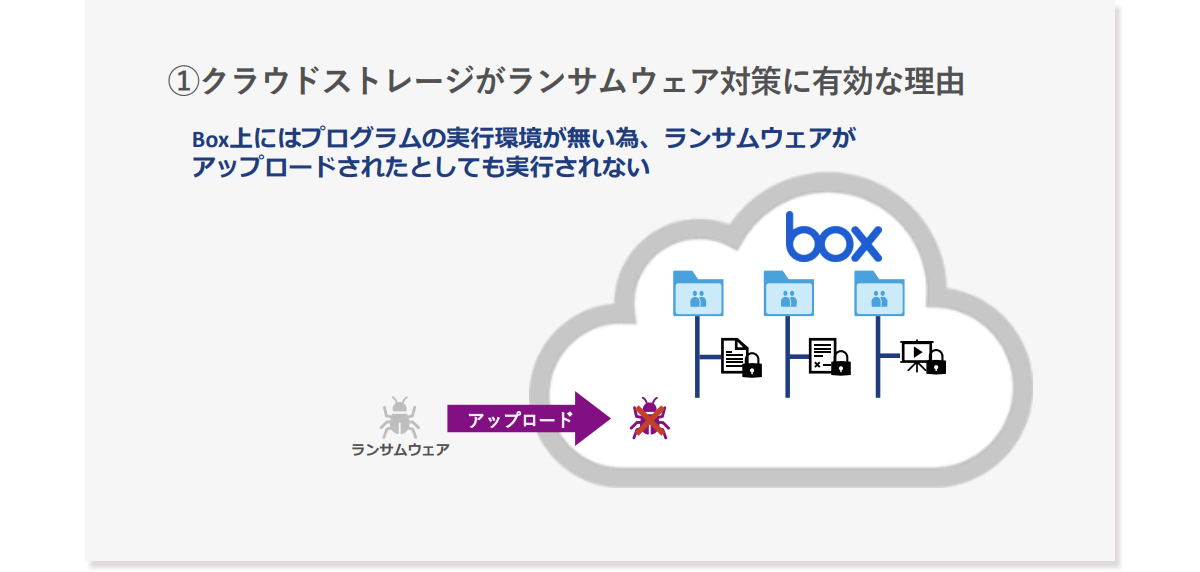
Cloud storage is also effective for such issues. Taking Box as an example, one of the big points is the stability of the infrastructure of Box itself. Even if ransomware is uploaded to Box, the files on Box will not be encrypted because there is no program execution environment on Box.
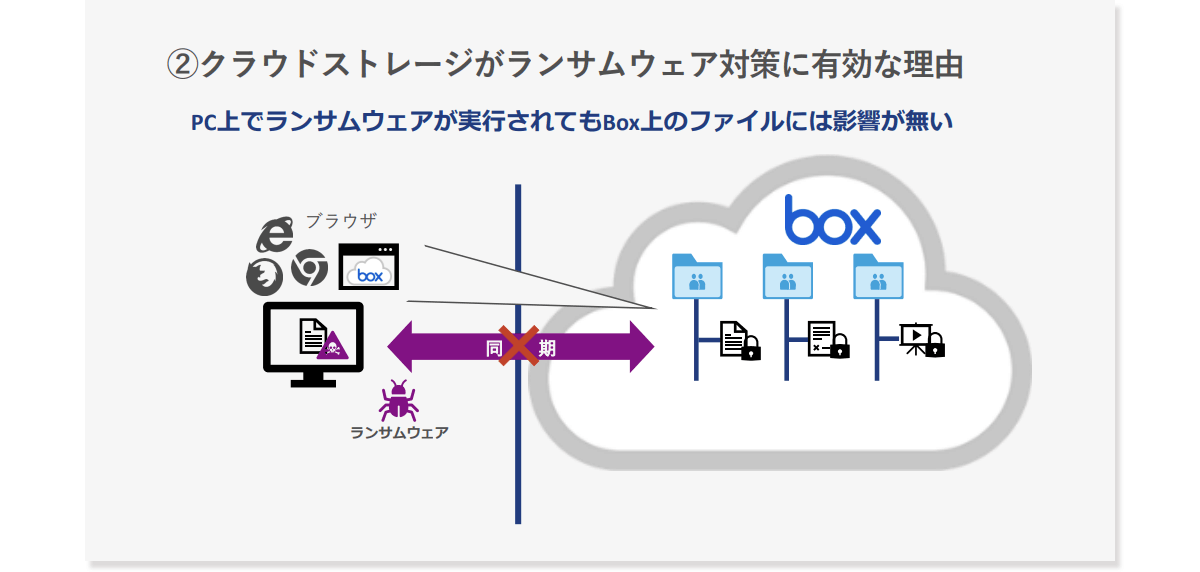
Also, if the ransomware is executed on the PC, although the files stored locally are encrypted, when the files on Box are browsed in the browser, they are not synchronized with the local files, which affects the Box side. does not affect In other words, if you use Box in your browser, you can prevent ransomware infection on Box.
On the other hand, if you use Box with File Explorer, the cloud storage side may also be encrypted by ransomware. Box has an application called BoxDrive, which synchronizes the local side and the Box side. If the local side is encrypted, the file on the Box side will also be encrypted, so be careful.
However, Box has a feature called version history that recovers files, so even if you were using File Explorer, you can recover to the state just before it was encrypted. And even with ransomware that deletes files, Box makes it easy to restore files from the Recycle Bin.
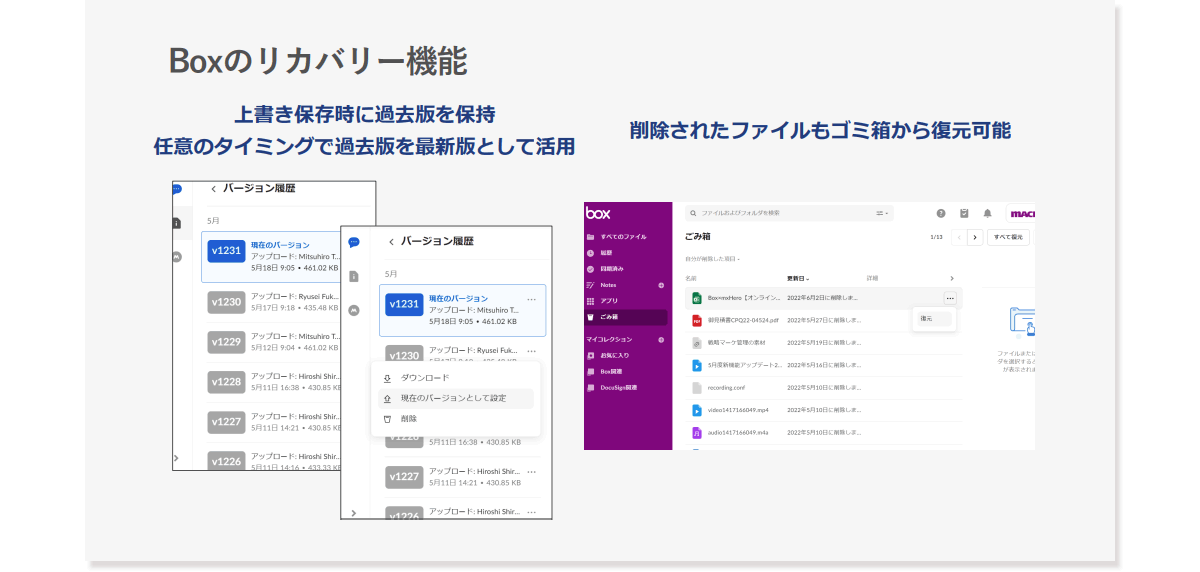
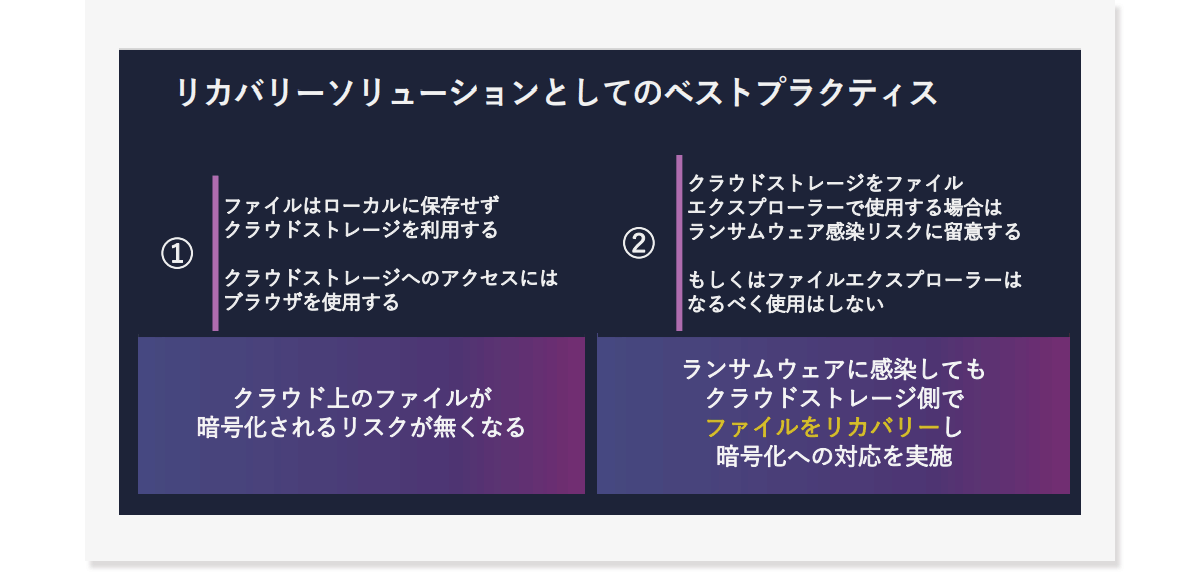
A best practice recovery solution is to simply use cloud storage instead of storing files locally, and use your browser to access cloud storage. Also, if you use cloud storage with File Explorer, you should be aware of the risk of ransomware infection and avoid using File Explorer if possible. However, with Box, you can easily restore to the state before it was overwritten, so you should be able to dispel the worry of recovery.
In addition, when investigating the extent of damage, Box allows you to ascertain the files that have been downloaded, making it easier to determine the risk of file leaks.
Summary
Recovery can be easily realized by using cloud storage, but the original purpose is not to recover, and the aim should be to avoid damage from ransomware. As a means to that end, by aggregating file sharing in cloud storage, attachment emails can be abolished and Emotet intrusion can be prevented. Also, even if you are infected with ransomware, depending on the cloud storage, you should be able to recover and think about your next move.
If all files exist on cloud storage in the first place, files can also be avoided from being damaged by ransomware. However, the reality is that there are many areas within companies where Box cannot be used as a recovery measure, such as business systems, and there is no doubt that individual measures must be taken. As ransomware evolves day by day, it is necessary to implement ransomware countermeasures from multiple perspectives. It is important to bear in mind that new attack methods targeting cloud storage may emerge in the future.
Still, for now, cloud storage can be one of the effective solutions for Emotet/ransomware protection.
Inquiry/Document request
Macnica Box Inc.
- TEL:045-476-2010
- E-mail:box-sales@macnica.co.jp
Weekdays: 9:00-17:00

