
Matter (*1) was released on October 4, 2022 as a new common standard for smart homes. The ability to seamlessly link different devices and platforms is expected to further improve the user experience. On the other hand, companies involved in the manufacture of smart home devices need to keep various points in mind when implementing this standard.
In this article, we will explore the potential of Matter and explain the points that companies should understand in order to increase their competitiveness in the smart home market.
*1: A new common IoT standard for smart homes developed by the Connectivity Standards Alliance, a wireless communication standards organization that includes over 500 American companies including Apple, Google, and Amazon. By making smart home appliances from different manufacturers compatible, it enables seamless device integration and unified control, contributing to further improvements in the convenience of smart homes.
The future of smart home with Matter
Matter version 1.0 was released (*2) about a year ago in October 2022. In addition, version 1.2, which is scheduled to be applied to air conditioners, air conditioning equipment, cleaning robots, etc., will be released one year later, and it is receiving even more attention from the market.
Meanwhile, some companies overseas have started releasing products compatible with Matter version 1.0 (smart switches, smart lighting) in advance. On the other hand, there are cases where companies are taking a cautious stance toward investment, considering the value they provide and the state of their business.
Improving the user experience value that Matter brings will be important in the future in Japan as well. In order to understand the convenience of smart homes and make effective use of them, it is necessary to actually experience them and constantly monitor trends. However, the truth is that the benefits of smart homes more than make up for the pain.
For example, for married couples raising children, nursing care facilities, or households with people in need of care, the cooperative operation of devices can be expected to reduce the burden on users. Depending on how it is used, it could also be a solution to the social issue of labor shortages. Additionally, for real estate developers, if they can provide properties that have smart homes installed in advance, this will be a major point of differentiation from other companies.
In the future, by actively using products with the Matter logo, we believe that the success rate of funding will increase and opportunities will arise to build an ecosystem with service providers aiming to provide new user experience value. If the importance of Matter increases, companies involved in the manufacture of smart home devices will need to accelerate their investment decisions and PoC cycles for Matter adaptation more than ever before.
* 2: Published by CSA (Connectivity Standards Alliance), a wireless communication standardization organization, on October 4, 2022.
Four challenges and solution approaches in implementing Matter
From here, we will explain four important points to avoid incurring rework costs when applying Matter, mainly for companies involved in the manufacture of smart home devices (see ① to ④ in the diagram below).
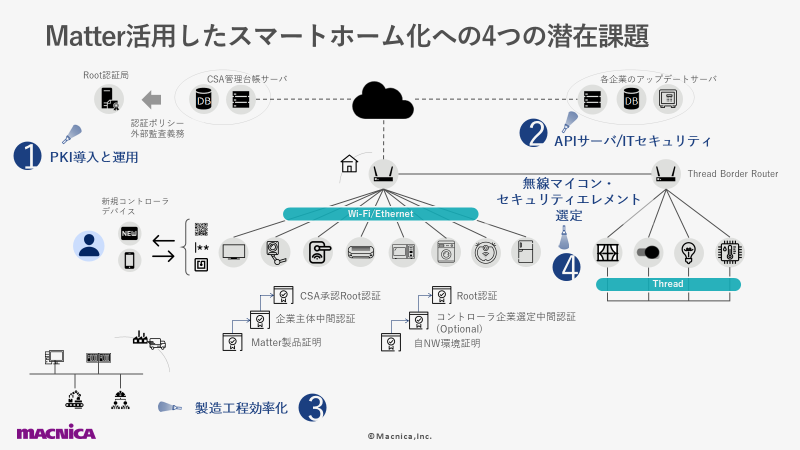
① PKI introduction and operation
In a multi-vendor environment, establishing mechanisms to trust third parties and implementing interoperable PKIs can be extremely time consuming. In fact, the reality is that there is a high possibility that this will not be achieved.
On the other hand, Matter is characterized by the fact that the content of the certificate usage within the standard is discussed by PKI and security experts before being incorporated into the standard. We have also established a Certificate Policy for PAA (Product Attestation Authority) approved by CSA and PAI (Product Attestation Intermediate) that smart home equipment manufacturers are explicitly involved with.
In other words, Matter has established sufficient trust for smart home devices to interoperate with each other. In addition, DAC (Device Attestation Certificate) is responsible for remote attestation (does it operate reliably as a Matter device?), and NOC (Node Operation Certificate) is responsible for the reliability of the owner.
What manufacturers of smart home equipment, which is the main entity behind DAC, should focus on is ``how to implement secure certificate authority operations.''
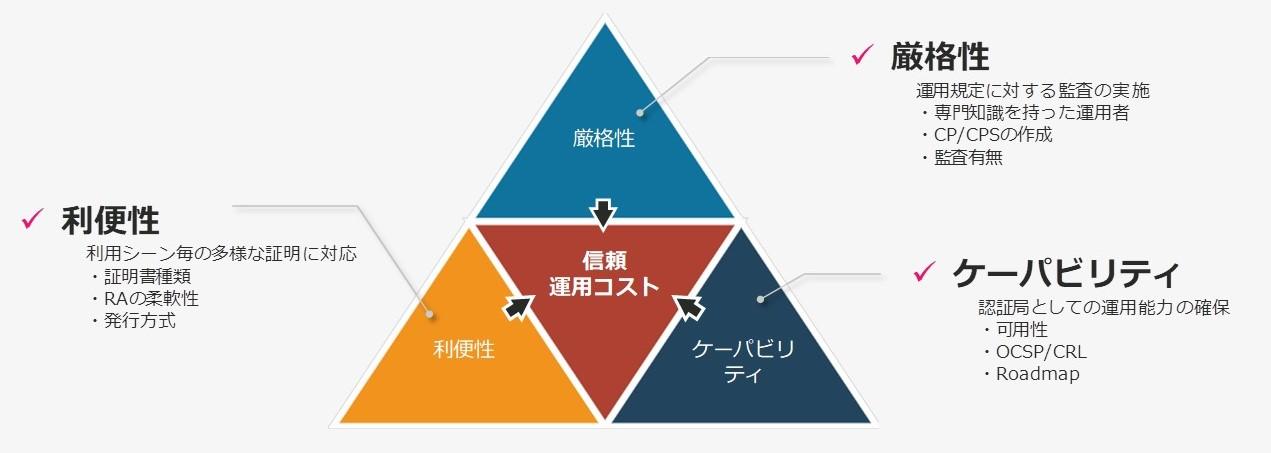
As of the end of September 2023, many PAA-approved certificate authority vendors are providing PAI solutions (* 3). However, without proper selection criteria, research costs are high, and there is also the risk of ultimately selecting a vendor that is not the best fit for your company.
Points to consider include the convenience of the certificate authority system, vendor support system, and investment in the data center where the certificate authority is operated. Furthermore, human error is one of the factors that requires special attention when operating a certificate authority. Vendors with a strong track record often work to improve system convenience based on their past track record and experience, and tend to implement designs that prevent human error, so use this as a reference. .
Also, check whether your company's requirements can be met for certificate management and operation throughout the life cycle, incorporate the uniqueness of certificates, and check whether your company's ID management for linking with products or authentication when realizing synchronized issuance from factory processes. Another issue that needs to be cleared is a close examination of the station's ability to provide information.
First, understand the gap with the current situation in terms of ``optimal solution for certificate issuance/approval (obtainment) flow = life cycle design'' and ``how to manage certificates.'' From there, it is a good idea to look for the optimal digital trust partner for your company, taking into account the necessary balance between cost, convenience, and strictness.
②API server/corporate server side security
Many IoT devices have an update function after release to fix vulnerabilities or add functionality. New firmware is distributed from the update server, but if an attacker infiltrates it, there is a risk that the tampered firmware will be applied to all products. For this reason, it can be said that security measures for update servers are a high priority.
Additionally, many IoT devices communicate with API servers on the cloud, allowing data storage and remote control. It depends on the type of IoT, but if a server on the cloud is infiltrated, there is a risk that personal information and private information (location information, medical information), etc. will be stolen or manipulated without permission. there is.
These public servers can be attacked from anywhere on the internet, making them more vulnerable than local IoT devices that require physical access.
Black Hat USA 2023 Then, via the cloud NAS Lecture on hacking (※ Four) had. The researcher who discovered the vulnerability NAS and cloud communication, and GUID We discovered that this is used as authentication. Furthermore, those GUID was found published on the Internet and collected GUID other people's information via the cloud using NAS We have proven that we can access.
There are several methods and points to prevent attacks on public servers.
- Manage vulnerabilities in the same way as general public servers
- Make sure you know the operating versions, including the OS and middleware, and perform regular maintenance.
- Obtain information on new vulnerabilities, and if a high-severity vulnerability is discovered, perform emergency maintenance (this applies not only to the production environment but also to the staging environment).
- Enhanced authentication
- Use tokens and IDs used for device authentication that cannot be guessed and that are not made public anywhere.
- Server authentication from the device's perspective is also important. In the past, motherboard firmware update servers used HTTP, and there were cases where the firmware was tampered with along the way because server authentication was not possible.
- API security measures
- OWASP has released the OWASP API Security Top 2023 edition (*5), which announces risks to be aware of when implementing APIs. The Black Hat example above can be considered a vulnerability to Broken Object Level Authorization.
※4:https://i.blackhat.com/BH-US-23/Presentations/US-23-MOSHE-Pain-in-the-NAS.pdf
※5:https://owasp.org/API-Security/editions/2023/en/0x00-header/
③Need for preliminary verification due to manufacturing process changes
When writing highly confidential information during the manufacturing process, process changes occur. In that case, you can reduce waste by digitally verifying the problem in advance and confirming that there are no problems before applying it to the actual factory.
In the past, when there was a change in the process or some change point, it was often necessary to solve the problem based on the experience and intuition of the individual. Moreover, no one can prove whether the solution is really appropriate.
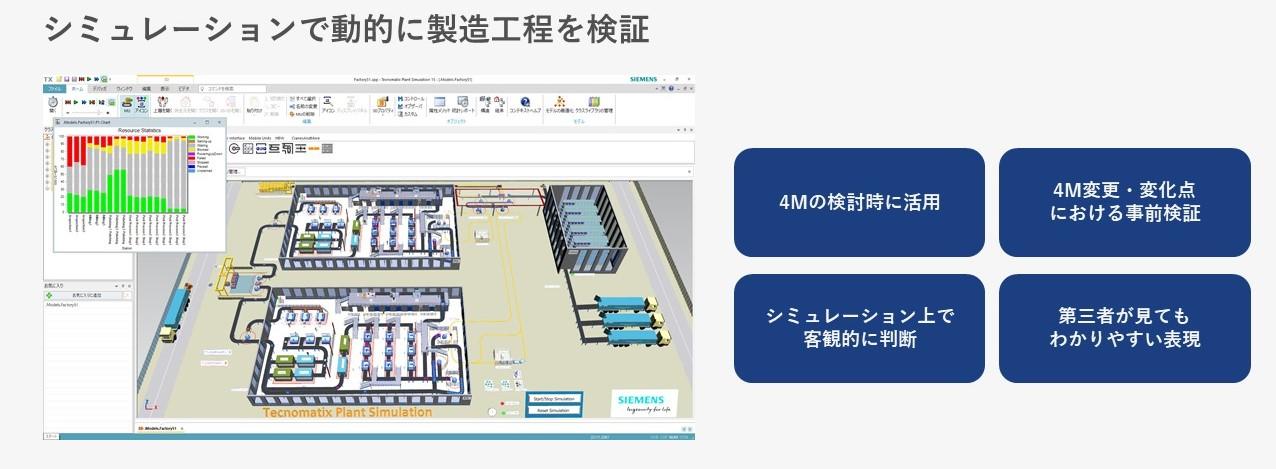
In such cases, simulation can be a very effective tool. For example, when a process change like the one mentioned above occurs, it is possible to verify various proposed changes by dynamically reproducing a factory exactly like the actual site in advance digitally. Everything from verifying the equipment layout, number of equipment, and number of workers to verifying the manufacturing order can be objectively verified using data.
Furthermore, by reproducing the factory conditions in a form that closely resembles the actual situation, it is possible to consider sudden changes and ways to avoid problems. The simulated factory is also useful for collaboration with other departments because it is possible to see what the interior looks like at a glance.
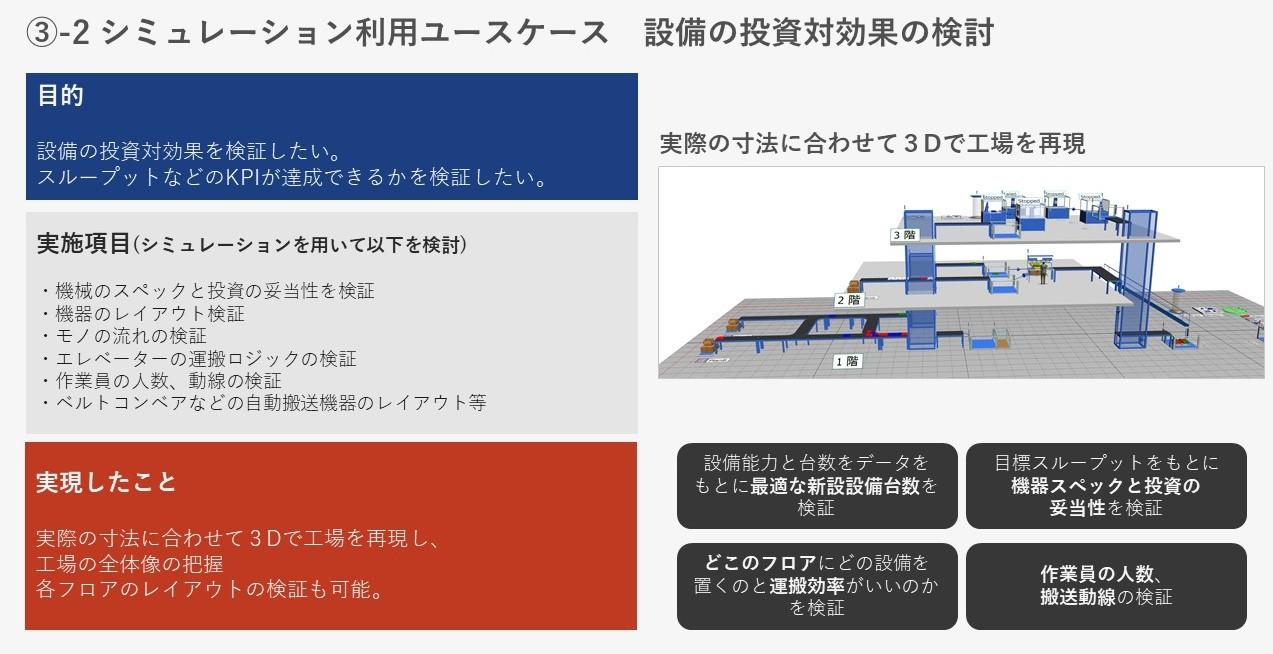
Simulation use case: Examining the return on investment of equipment
④Wireless/security semiconductor selection
WLAN The module has an encryption method WPA (Wi-Fi Protected Access) is the latest standard for WPA3 The one that is compatible with this is suitable. Because the conventional WPA2 In the method KRACKs(※ 6) A vulnerability in encryption called ” was discovered, WLAN This is because the danger of wiretapping and interception of communications has been pointed out.
WPA3 implements a handshake technology called SAE (Simultaneous Authentication of Equals) to overcome multiple security vulnerabilities found in the traditional WPA2. We have also implemented a mechanism to encrypt communications between individual users, even in environments where users do not use passwords.
The certification program (hereinafter referred to as Wi-Fi certification) provided by WFA (Wi-Fi Alliance) requires WPA3 compatibility. Therefore, by passing Wi-Fi certification with their products and acquiring the Wi-Fi logo, device manufacturers can demonstrate to the outside world that their products implement genuine WPA3.
Wi-Fi certification requires actual device testing at WFA 's Authorized Test Lab (ATL). If you fail the exam, you will have to improve the failed items and retake the exam, which will increase costs. Typical equipment manufacturers prepare for the ATL Wi-Fi certification test several months in advance, and in some cases conduct their own pre-tests if necessary. As described above, the costs associated with obtaining Wi-Fi certification, including human resources, time, and money, are an issue for device manufacturers.
After product mass production, wireless Chip There are cases where vulnerabilities have been found within mentioned earlier WPA3 Also in `` Dragonblood(※ 7) A vulnerability called `` has been announced. To address these vulnerabilities, WLAN A firmware update within the module is required. As a means of doing so, OTA (Over The Air) over-the-air updates, USB One example is the wired update method. In any case, it is necessary to install software to update the firmware on the device side in advance.
WLAN module firmware is generally provided by WLAN chip vendors, so device manufacturers want to be able to obtain firmware that addresses vulnerabilities as soon as possible. However, WLAN chip vendors with poor (or limited) support capabilities may find it difficult to provide firmware in a timely manner.
In other words, when selecting a WLAN module / chip, the technical support system of the chip vendor should also be carefully considered. By the way, Infineon has multiple WLAN application engineers stationed in Japan, and has a good reputation for its speedy and solid technical support system.
* 6: Abbreviation for Key Reinstallation Attacks. A type of attack that exploits vulnerabilities in WPA2 to steal data sent over the network.
* 7: A collective term for multiple vulnerabilities related to WPA3 's SAE (Simultaneous Authentication of Equals) handshake. An attacker within range of a password-protected Wi-Fi network could obtain the password and gain access to sensitive information.
Summary
This time, we have divided themes that are difficult to uncover into four areas and explained them, mainly for smart home equipment manufacturers.
Particularly in the area of ``digitalization of manufacturing processes,'' if Matter and in-house DX can be successfully synergized, the value of the initiative will increase. To achieve this, it is essential to efficiently grasp the overall picture while also adding external knowledge. However, there may be cases where it is difficult to allocate cost and man-hours to other areas because you are so focused on deepening your understanding of Matter and finding ways to implement it.
Macnica is close to our customers' issues and proposes comprehensive solutions that are immediately effective. If you have any problems, please feel free to contact us.
Writer
Toshihiro Kurosawa / Chief, CPS Innovation Center Macnica
Joined Macnica after developing consumer embedded devices. Since joining the company, he has been engaged in work related to security chips, IoT product device security, PKI /authentication, and provides comprehensive support from the initial stage of introduction consideration to the implementation level. In recent years, he has also been engaged in 5G security consulting for MNOs.
Related articles/solutions
PKI (Public Key Infrastructure): Digicert
Digital Twin Production Simulation Software: Siemens Plant Simulation
Wireless SoC (System on Chip): Silicon Labs / NXP
MCU, Connectivity, Secure Element:Infineon / MICROCHIP
