XDR
Document request
If you would like the following materials, please proceed to the application form.
| Document content | |
| white paper |
Pitfalls of Zero Trust - New Security Countermeasures against Identity Threats ITDR - PDF NEW  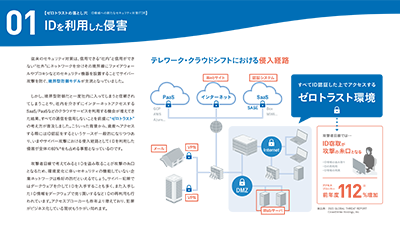 Information that identifies and identifies an individual, such as an ID, user name, PIN, and password, is called a “credential”. In this white paper, we will explain in detail how to protect important IDs linked to those assets and what security measures should be taken. |
|
Why can XDR improve security maturity? PDF   In this white paper, in addition to the definition and components of XDR, we will introduce a wide range of differences between existing solutions and XDR, and the verification results of actual XDR effects. |
|
|
What is "XDR" PDF   Advanced threat detection for businesses without security experts Cyberattacks are becoming more sophisticated and sophisticated every year. Despite implementing various measures such as multi-layered defense with anti-virus products and perimeter defense, threat detection with EDR and NDR, etc. In addition, there are many issues such as the increasing burden of security operations. In light of these issues, "XDR" is a solution that utilizes machine learning technology to realize advanced threat detection while reducing the operational burden, such as handling over-detection. This white paper focuses on such XDR and explains it in detail. |
|
|
Advanced security operations become a reality with XDR! ? From chasing operation to improvement-oriented aggressive operationPDF   "XDR" is a solution that achieves advanced threat detection while reducing the operational load, such as handling over-detection. In this white paper, we explain the operational issues that XDR can specifically solve, divided into "collection", "detection", and "analysis/response". |
|
| application form | |
Inquiry/Document request
In charge of Macnica XDR Co., Ltd.
- TEL:045-476-2010
- E-mail:XDR@macnica.co.jp
Weekdays: 9:00-17:00