
About reports
This report aims to raise awareness about the results of an analysis of attack campaigns observed in fiscal year 2023 (April 2023 to March 2024) that attempted to steal confidential information (personal information, policy-related information, manufacturing data, etc.) from Japanese organizations.
攻撃のタイムラインと攻撃が観測された業種
In 2023, many new attack groups have appeared compared to attacks up until last year. These are the UNC48412 attack group, which infiltrated organizations by attacking the Barracuda ESG CVE-2023-2868 vulnerability, the TELEBOYi attack group4, which attacked infrastructure-related organizations with RatelS3 remote control malware, the Vapor Panda attack group7, which attacked manufacturing-related organizations with BLOODALCHEMY56 remote control malware, and the UNC52218 attack group, which attacked academic and manufacturing industries by attacking Ivanti's CVE-2023-46805/CVE-2024-21887 vulnerability. On the other hand, attack groups targeting Japan in 2022 and before were observed, including attacks using the LODEINFO malware 9 by the APT10 attack group, attacks using the EntryShell 10 malware by the Tropic Trooper attack group, attacks using PlugX 11 and PUBLOAD 12 13 malware by the Mustang Panda attack group, and attacks exploiting the open source Stowaway, which has been reported to be used by Chinese attack groups, although the attackers are still under analysis.
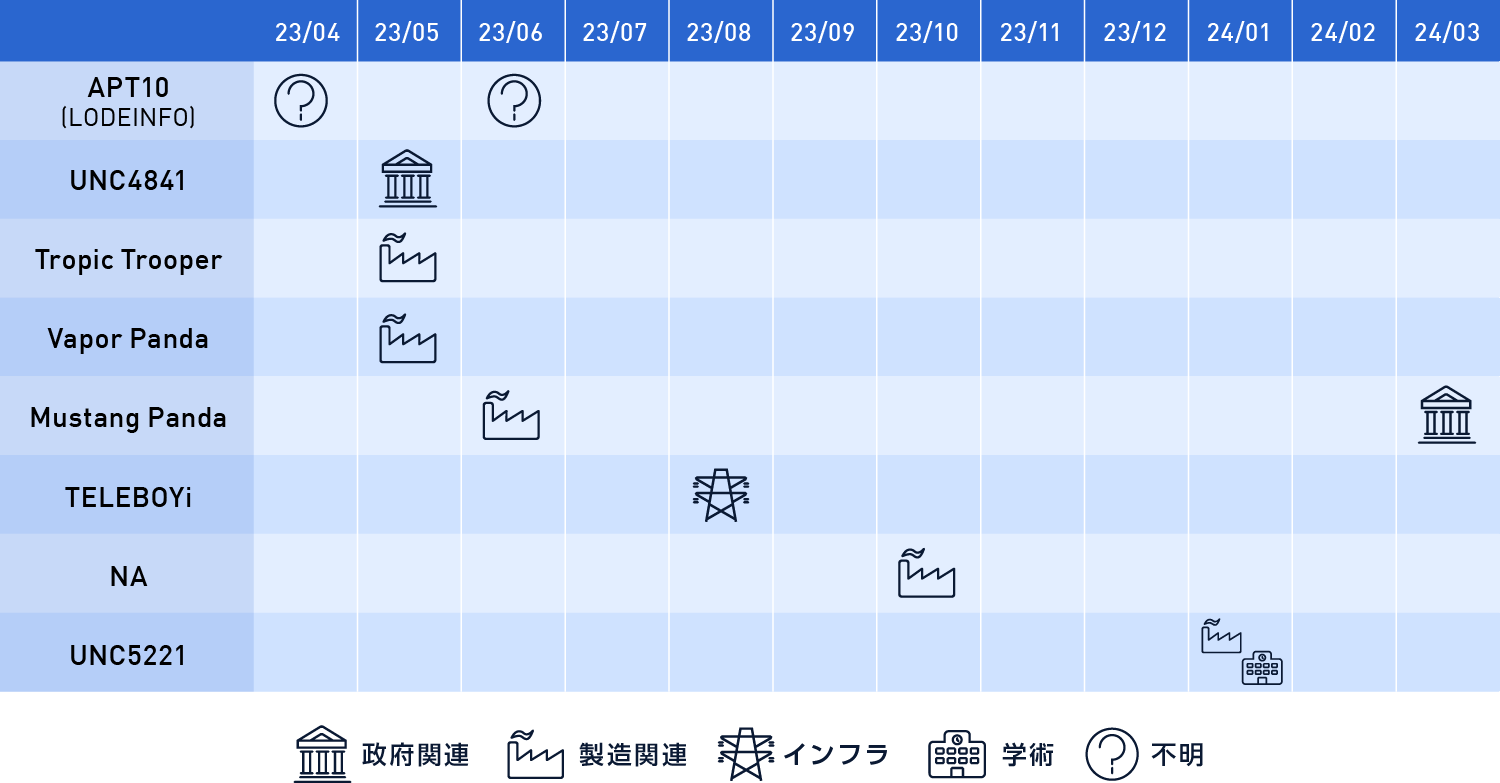
Table 1. Time chart
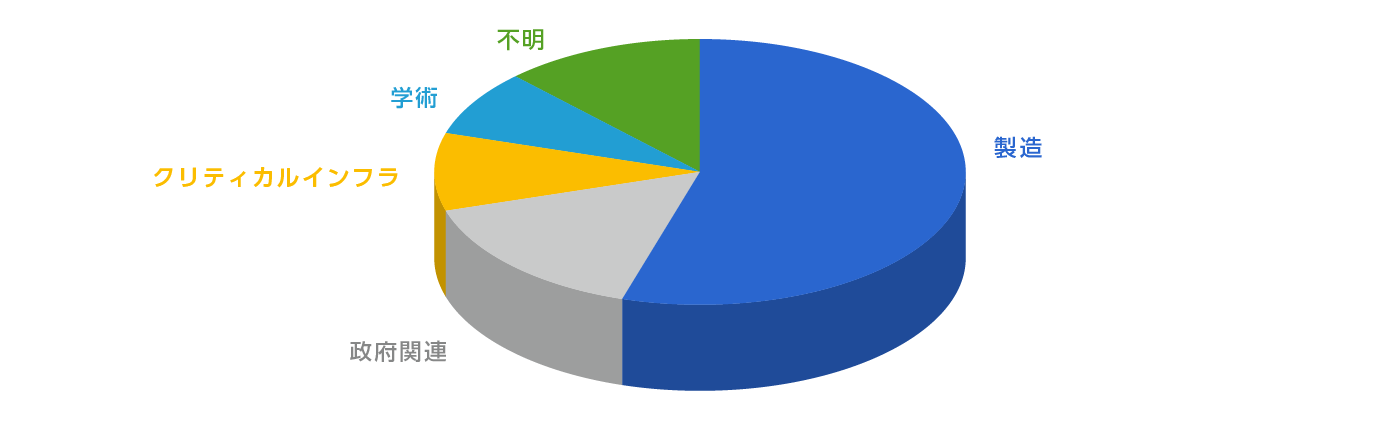
Figure 1. Proportion of target industries (FY2023)
In the past, spear phishing was the most commonly observed intrusion pattern for targeted attacks, but in 2023, the most common method of intrusion was through attacks on vulnerabilities in publicly available assets. In addition, methods such as exploiting Wi-Fi access points near the overseas bases of manufacturing-related organizations to infiltrate organizations and infecting malware through USB devices have also been observed.
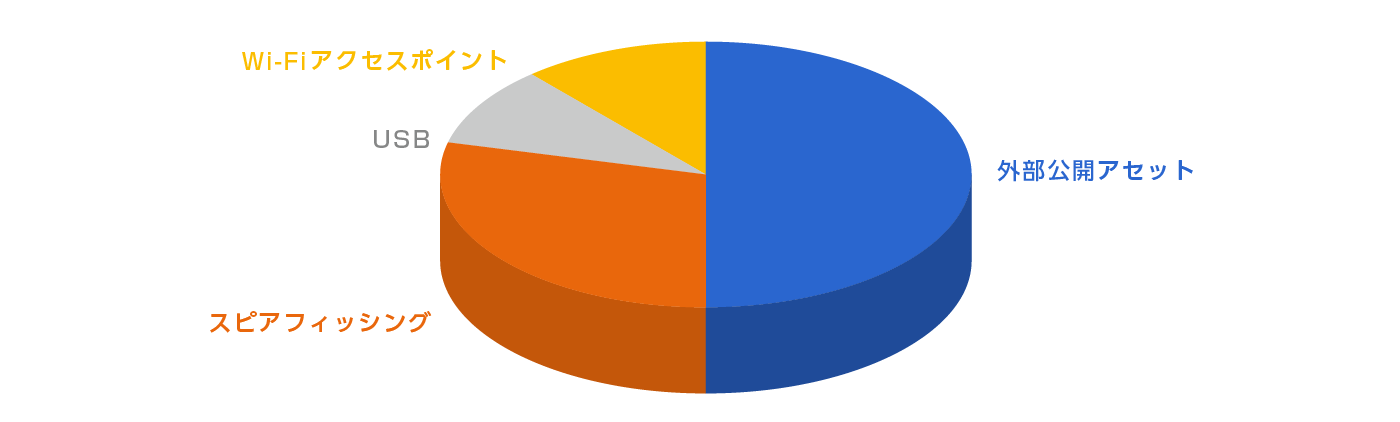
Figure 2. Attack surface ratio (2023)
- Introduction
- 攻撃のタイムラインと攻撃が観測された業種
- Attack summary
- April 2023
- May 2023
- June 2023
- July 2023
- October 2023
- January 2024
- March 2024
- New TTPs, RATs, etc.
- Mustang Panda (PUBLOAD)
・Outline of the attack campaign
Mustang Panda attack campaign characteristics and detection - Mustang Panda (PlugDisk attacks observed in Southeast Asia)
・Outline of the attack campaign
Infection flow
・Detailed analysis of PlugDisk ・Consideration of infection via PlugDisk USB - Attack campaign exploiting vulnerabilities in Ivanti products
・Outline of the attack campaign
・Abuse cases observed in Japan ・Passive backdoor ProxDoor
- Mustang Panda (PUBLOAD)
- TTPs (tactics, techniques, procedures) by attack group
- Threat Detection and Mitigation Considered from TTPs
- Malware Delivery/Attack
- Installed RAT, remote control (for C2 server)
- indicator of detection
- https://www.macnica.co.jp/business/security/security-reports/pdf/cyberespionage_report_2022.pdf
- https://www.mandiant.com/resources/blog/barracuda-esg-exploited-globally
- https://www.lac.co.jp/lacwatch/report/20230914_003513.html
- https://jsac.jpcert.or.jp/archive/2024/pdf/JSAC2024_1_8_yi-chin_yu-tung_en.pdf
- https://www.elastic.co/security-labs/disclosing-the-bloodalchemy-backdoor
- https://www.botconf.eu/botconf-presentation-or-article/into-the-vapor-to-tracking-down-unknown-pandas-claw-marks/
- https://www.crowdstrike.com/adversaries/vapor-panda/
- https://www.mandiant.jp/resources/blog/investigating-ivanti-zero-day-exploitation
- https://blogs.jpcert.or.jp/ja/tags/lodeinfo/
- https://www.virusbulletin.com/uploads/pdf/conference/vb2023/slides/Slides-Unveiling-Activities-of-Tropic-Trooper.pdf
- https://unit42.paloaltonetworks.jp/plugx-variants-in-usbs/
- https://csirt-cti.net/2024/01/23/stately-taurus-targets-myanmar/
- https://unit42.paloaltonetworks.jp/chinese-apts-target-asean-entities/