
About reports
This report provides an analysis of attack campaigns that attempted to steal confidential information (personal information, policy-related information, manufacturing data, etc.) from Japanese organizations observed in fiscal year 2022 (April 2022 to March 2023). is described for the purpose of calling attention. It describes new attack methods and the detection of their threats, focusing on incidents using remote-controlled malware (RAT) with high stealth.
At the end of the report are the indicators used in the campaigns mentioned in the text.
攻撃のタイムラインと攻撃が観測された業種
In FY 2022, continuing from Observation 1 in FY 2021, attacks using the LODEINFO malware 2 of the APT10 attack group were actively observed in industries such as media and security as before. In the attacks using the LODEINFO malware, in addition to Office macro files, VHD format disk image files were used for the delivered files, the normal executable file used for DLL sideloading was changed, and the loader DLL was obfuscated. changes were confirmed. Compared to these, LODEINFO itself, which is a payload in memory, was only slightly updated. Also, as an attack that seems to be part of an ongoing attack campaign, an attack was observed that used a shortcut file as a download command targeting cryptocurrency-related organizations of the Lazarus attack group. This observation was almost unchanged from Method 3 reported around 2019. As newly observed attacks from 2022, we observed attack campaigns by Operation RestyLink 4 5, EneLink 6 7, and Earth Yako 8 attack groups at security-related organizations. In addition, as newly observed attacks from FY2022, attacks using FlowCloud malware910 and Pirate Panda (also known as Tropic Trooper, GouShe) 11 attacks by the TA410 attack group were observed. These two attack campaigns were observed at the Chinese bases of domestic manufacturing industries. Regarding the observation of these attacks, spear phishing emails and chat tool attachments were the main infection routes, except that the FlowCloud malware was infected from a USB memory. Until FY2021, there were attacks such as the A41APT attack campaign that exploited vulnerabilities in public systems such as VPN devices, but as a feature of FY2022, it was observed that the number of intrusions from public systems decreased. .
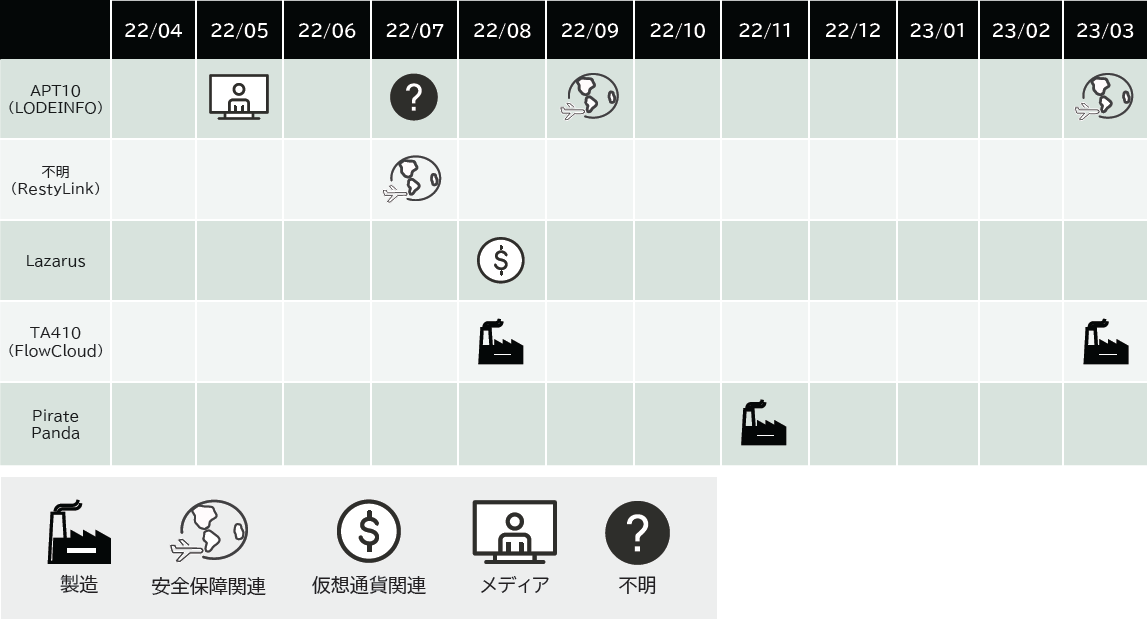
Table 1. Time chart
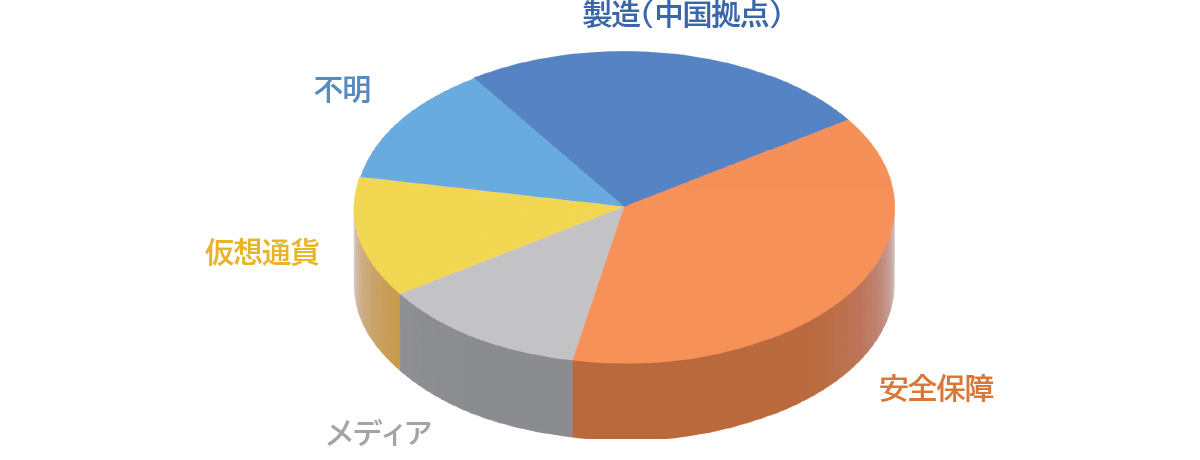
Figure 1. Pie chart of target organizations (FY2022)
In 2022, we observed many attacks on security-related organizations as targets of the LODEINFO malware and Operation RestyLink attack campaigns. In addition, although the attack campaign using the LODEINFO malware was not observed once in FY2021, it was observed again in the media industry, where attacks had been observed until FY2020. Regarding the detection of attacks on domestic organizations in the manufacturing industry, there have been observations of concentrated attacks on bases in China. I would appreciate it if you could refer to the measures.
- Introduction
- 攻撃のタイムラインと攻撃が観測された業種
- Attack summary
- May 2022
- July 2022
- August 2022
- September 2022
- November 2022
- March 2023
- New TTPs, RATs, etc.
- Pirate Panda China-Based Spear Phishing Attack
・Delivered macro file and EntryShell RAT
- Executable file of WORD icon and Cobalt Strike Beacon
・Pirate Panda network infrastructure
・Characteristics and detection of the Pirate Panda attack campaign - Attack campaign using LODEINFO
・v0.6.6
・v0.6.8
・Characteristics and detection of the LODEINFO attack campaign
- Pirate Panda China-Based Spear Phishing Attack
- TTPs (tactics, techniques, procedures) by attack group
- Threat Detection and Mitigation Considered from TTPs
- Malware Delivery/Attack
- Installed RAT, remote control (for C2 server)
- indicator of detection
- https://www.macnica.co.jp/business/security/cyberespionage_report_2021_6.pdf
- https://blogs.jpcert.or.jp/ja/tags/lodeinfo/
- https://blogs.jpcert.or.jp/ja/2019/07/shorten_url_lnk.html
- https://security.macnica.co.jp/blog/2022/05/iso.html
- https://insight-jp.nttsecurity.com/post/102ho8o/operation-restylink
- https://www.ipa.go.jp/security/j-crat/ug65p9000000nks8-att/000099786.pdf
- https://www.ipa.go.jp/security/j-crat/ug65p9000000nks8-att/000106897.pdf
- https://www.trendmicro.com/ja_jp/research/23/a/targeted-attack-campaign-earth-yako.html
- https://www.eset.com/jp/blog/welivesecurity/lookback-ta410-umbrella-cyberespionage-ttps-activity/
- https://insight-jp.nttsecurity.com/post/102id0t/usbflowcloud
- https://attack.mitre.org/groups/G0081/