
Wiz
With
Wiz Defend
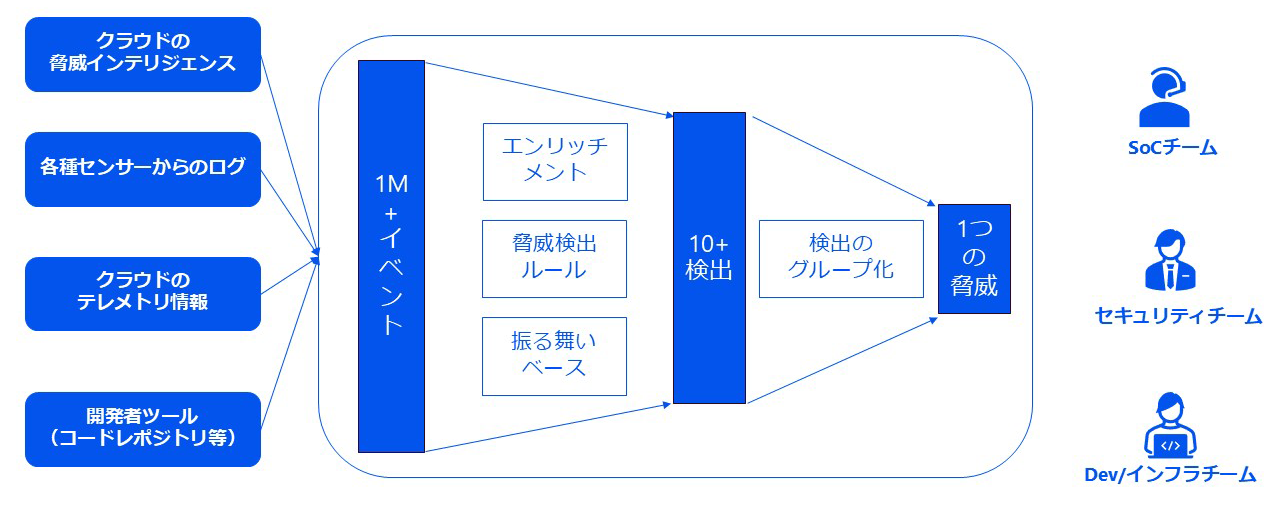
- Correlation analysis of cloud threat intelligence, information from various sensors, and cloud telemetry information
- Multiple detection results can be grouped together to identify a single threat
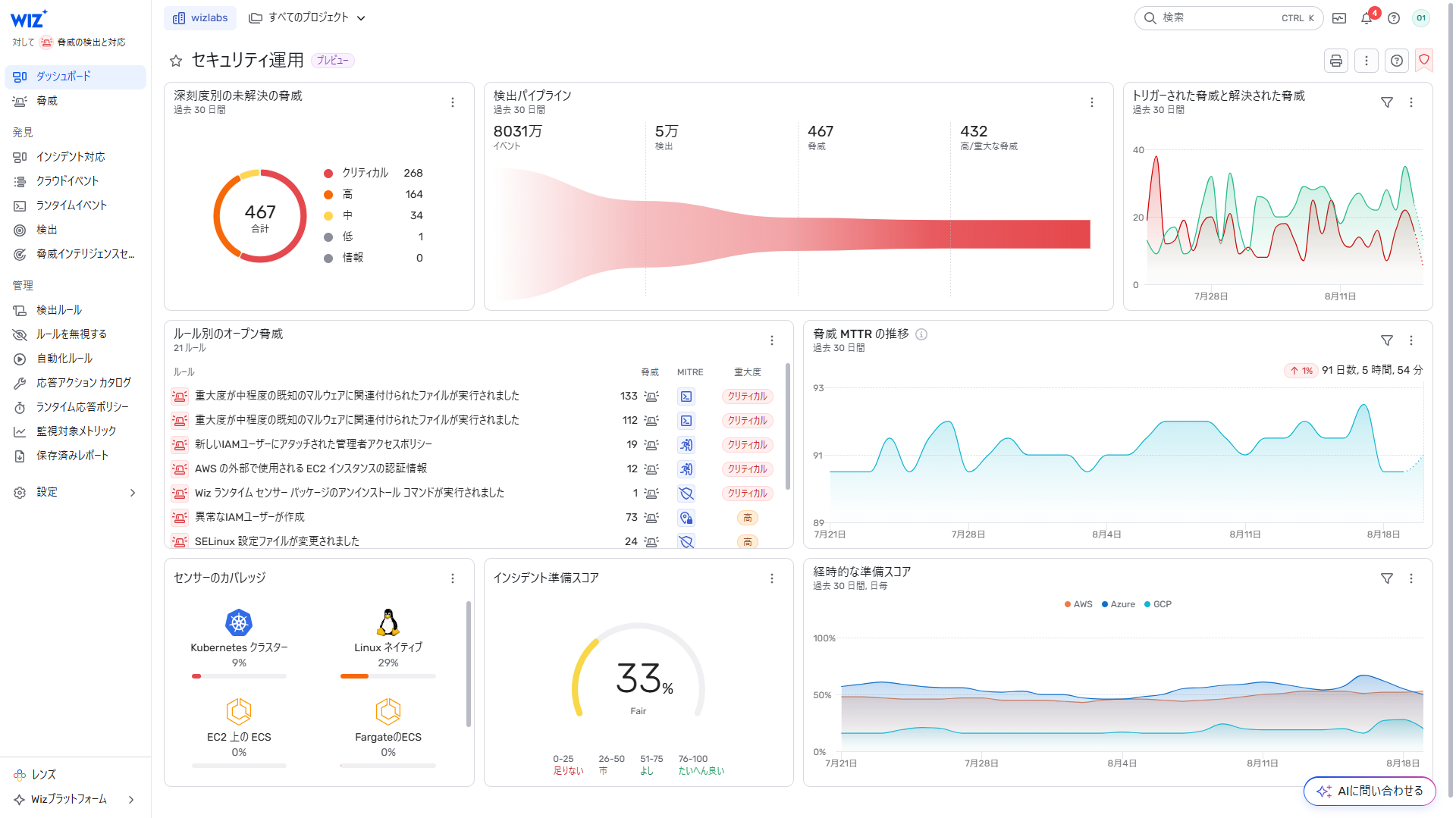
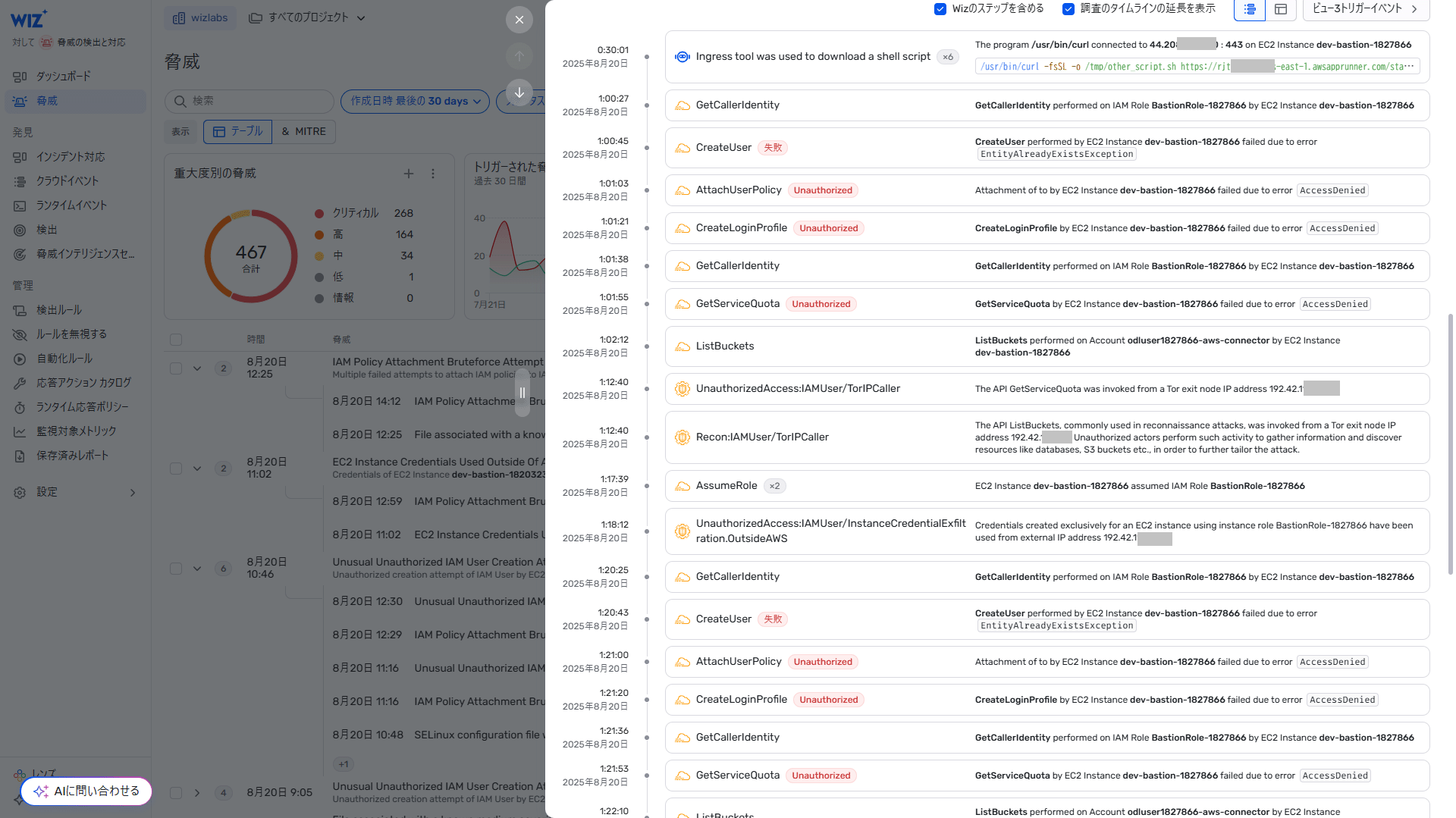
- Security Operations Dashboard
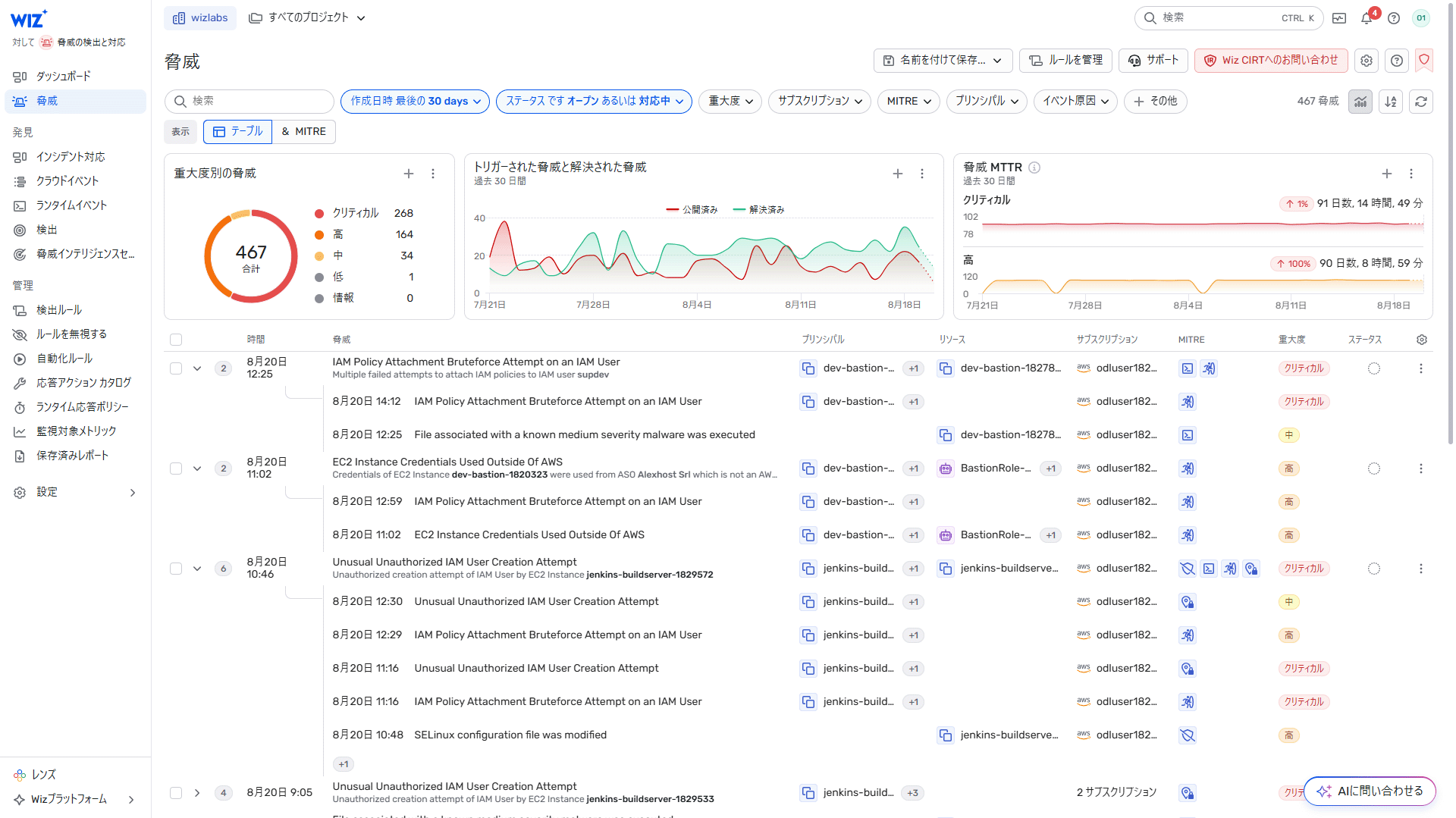
- Threats (multiple detections grouped together)
- Threat detection example (two detection results from a sensor and AWS CloudTrail logs are correlated and analyzed to identify a single threat)
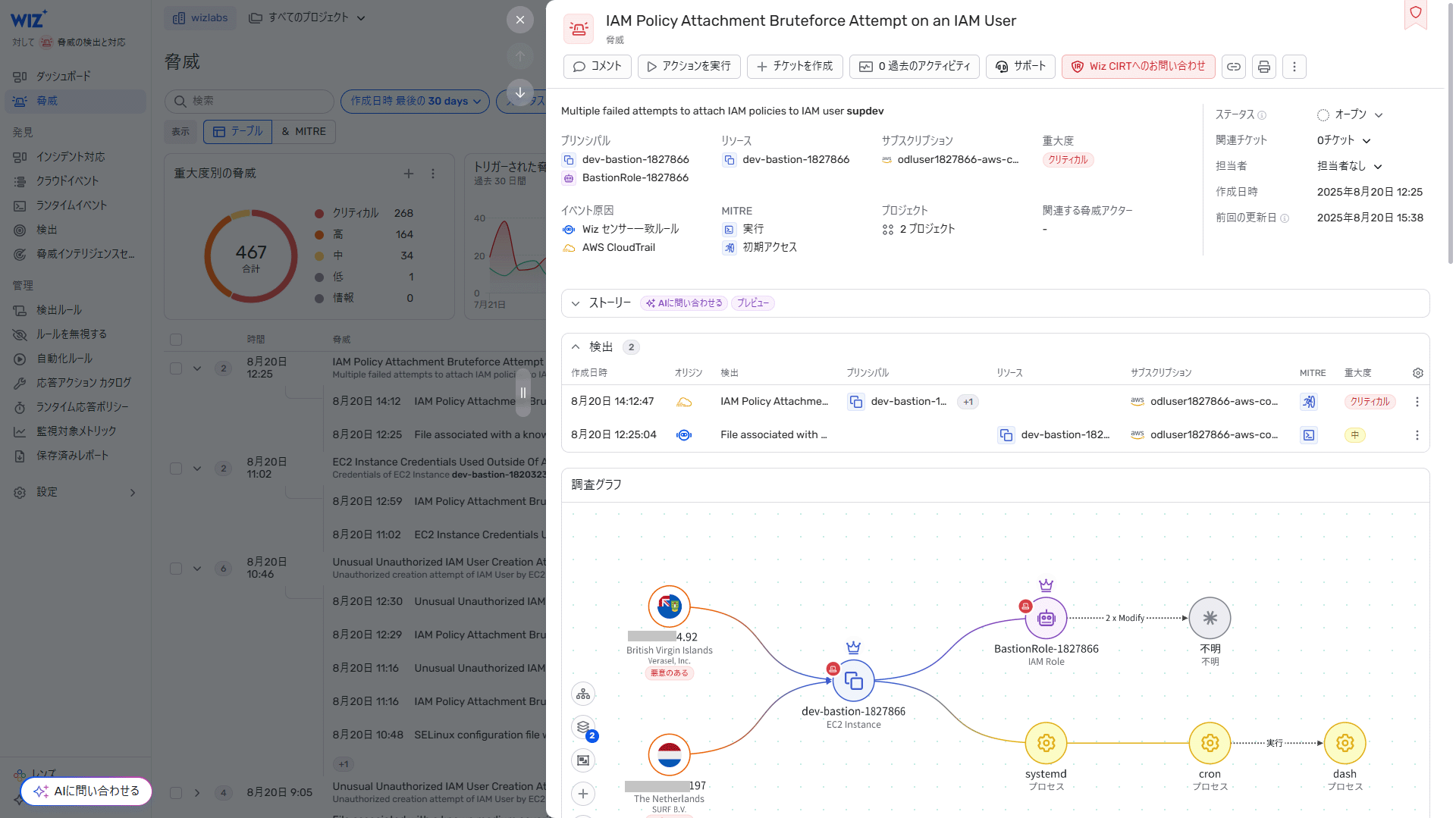
- Also displays a timeline of events for each cloud telemetry and sensor related to the threat.
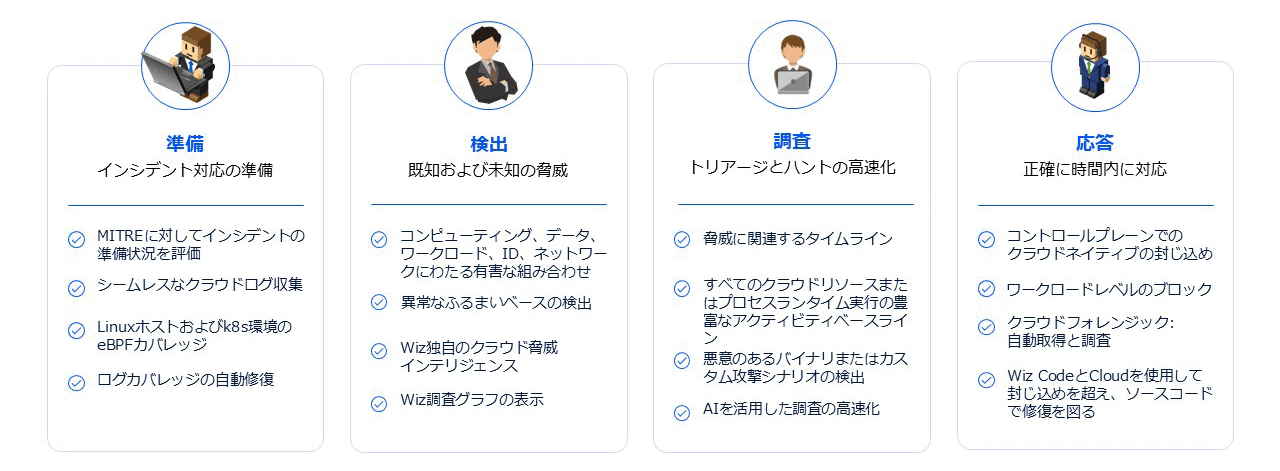
Threat Detection Pillars
- From a preparation perspective, it is also possible to evaluate the necessary log acquisition status in preparation for incidents.
- In terms of response, it is also possible to delete excessive IAM Role permissions from the Wiz management screen.
Inquiry/Document request
Macnica Wiz Inc.
- TEL:045-476-2010
- E-mail:wiz@macnica.co.jp
Weekdays: 9:00-17:00