
Skyhigh Security
sky high security
Skyhigh CASB (formerly McAfee MVISION Cloud)
Solutions provided by Skyhigh CASB
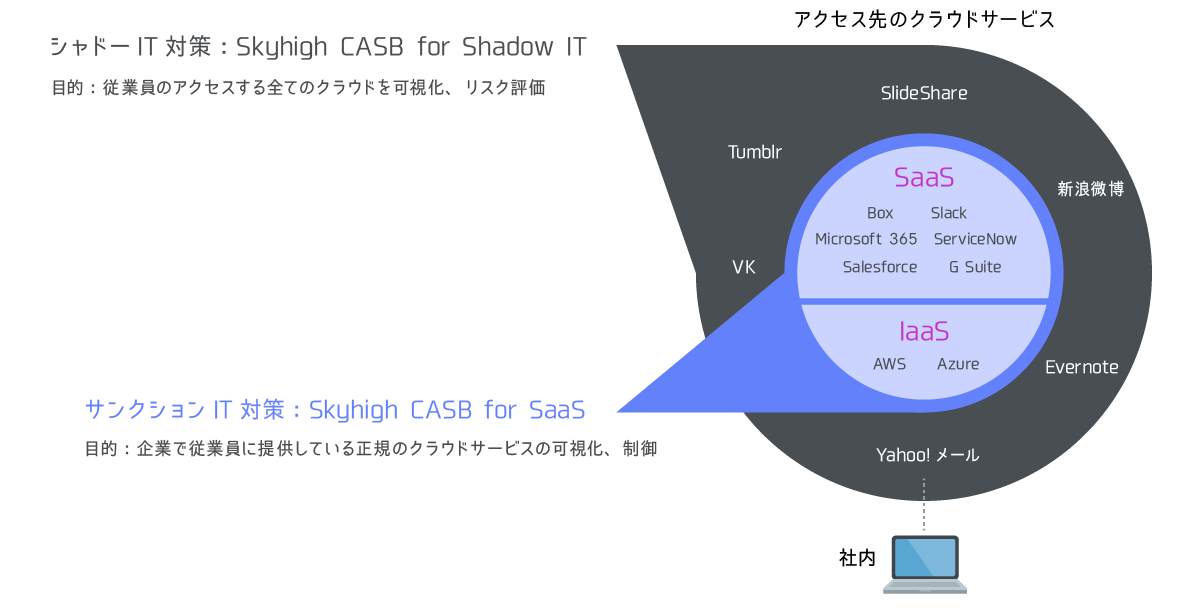
"Skyhigh CASB" provided by Skyhigh Security realizes cloud visualization and control from two approaches: shadow IT measures and Sanctioned IT measures. Even companies that have been hesitant to introduce cloud services due to concerns about cloud security can now use the cloud with peace of mind.
- Shadow IT countermeasures
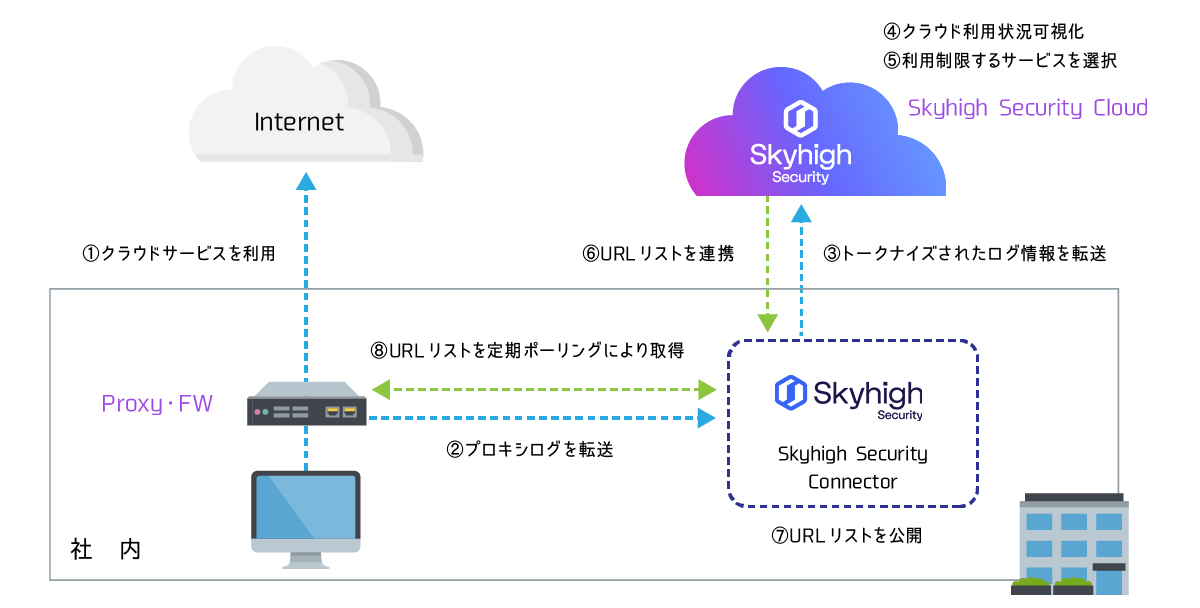
Based on the access log of Proxy/FireWall, we match with Skyhigh CASB's cloud risk DB to visualize cloud access and perform risk assessment. - Sanctioned IT measures
Acquire the logs of regular cloud services with API and visualize the usage status. You can define common policies across multiple cloud services, and control uploading of confidential information to cloud services and external file sharing.
The role of each license of Skyhigh CASB
| Shadow IT Countermeasures: Skyhigh CASB for Shadow IT | Sanctioned IT measures: Skyhigh CASB for SaaS | |
|
definition |
Cloud services that employees use without realizing it *Including safe/dangerous services |
Cloud services contracted and used as a company *Confirmed safety |
|
Task |
The administrator cannot grasp the usage status of the cloud service | The default administrative functions of the service are not secure enough |
|
Response by CASB |
||
|
Visualization |
|
|
|
control |
|
|
For Shadow IT
What is Shadow IT
- Shadow IT refers to cloud applications that are used by employees without permission from the company.
- Enterprises use more cloud services than IT admins realize
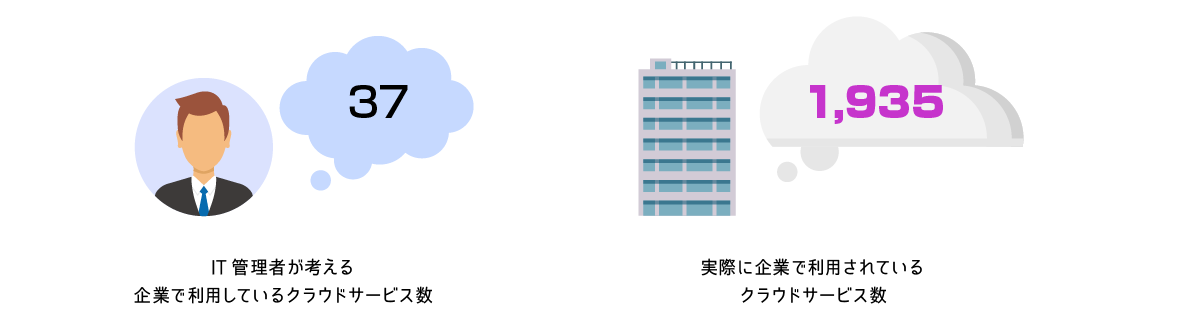
Risks of not knowing shadow IT
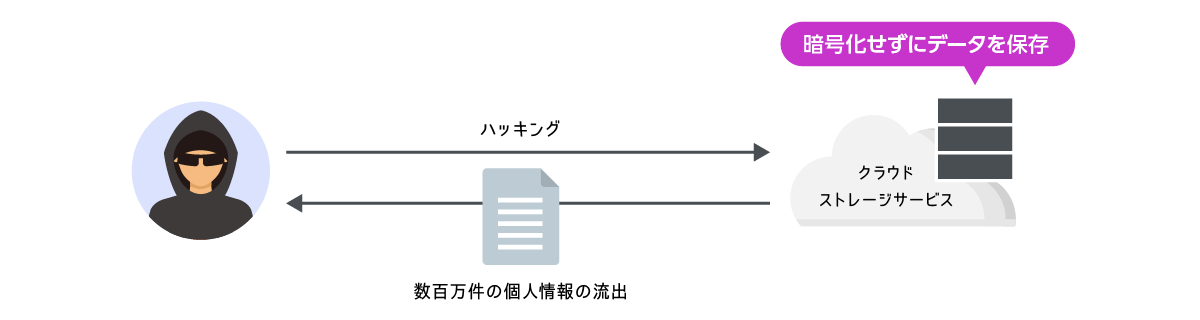
Information leak from domestic cloud storage
problem
- I didn't understand the security of the service (data was stored unencrypted)
- Didn't realize employees were using cloud storage services for business
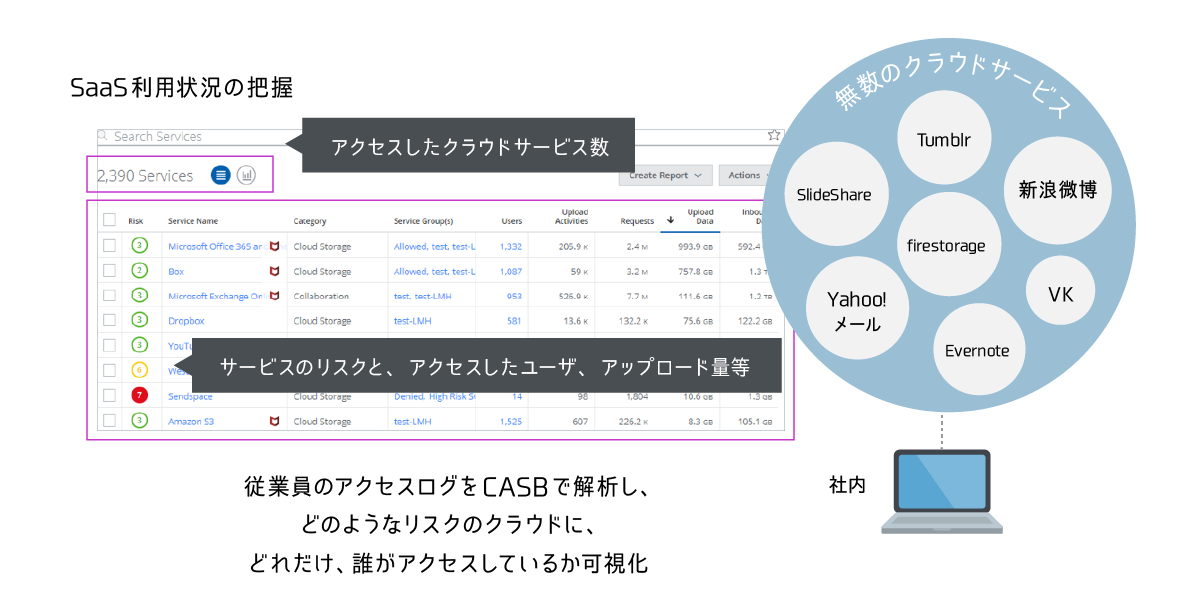
Configuration image of Skyhigh CASB for Shadow IT
Determine the risk of cloud services based on CSA
- Cloud service risks are quantified using approximately 50 items based on CSA (Cloud Security Alliance) guidelines
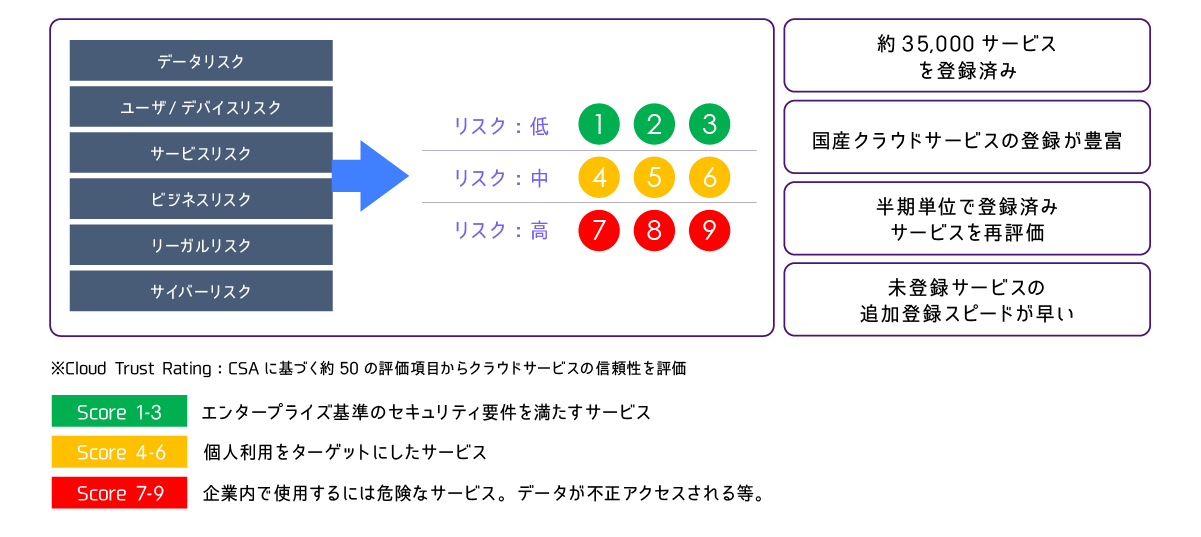
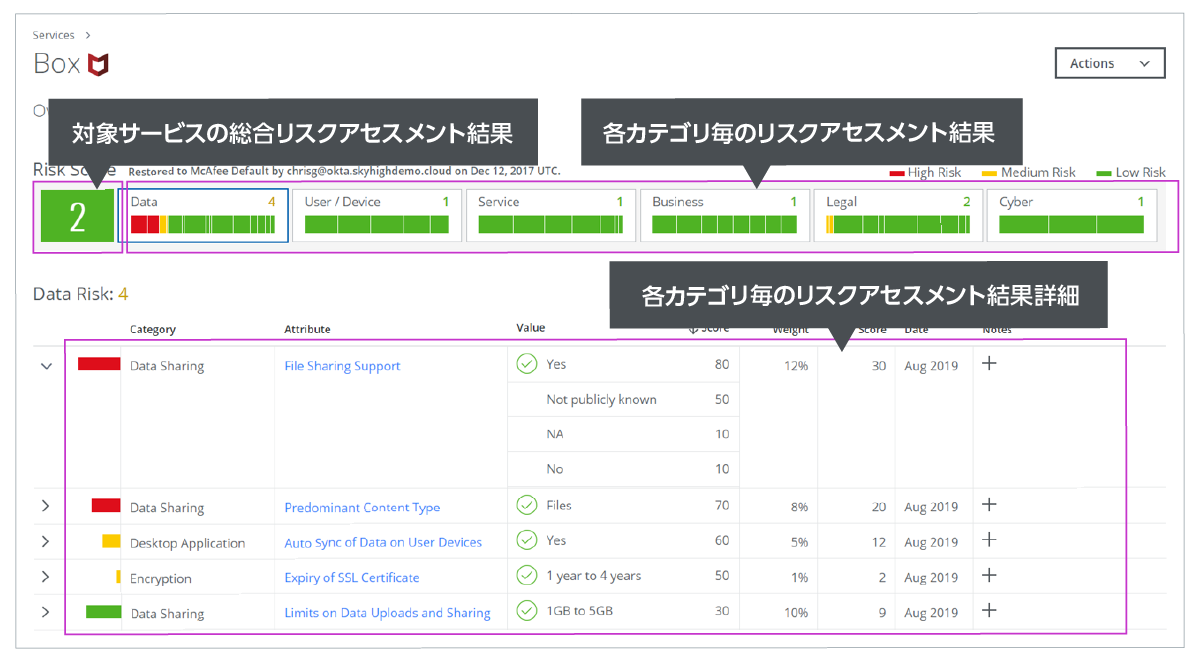
Reduces man-hours for responding to questionnaires and confirming agreements related to cloud service risk assessment
Skyhigh CASB risk judgment screen
Evaluate similar cloud services side by side
- View risk assessment items for each service side by side
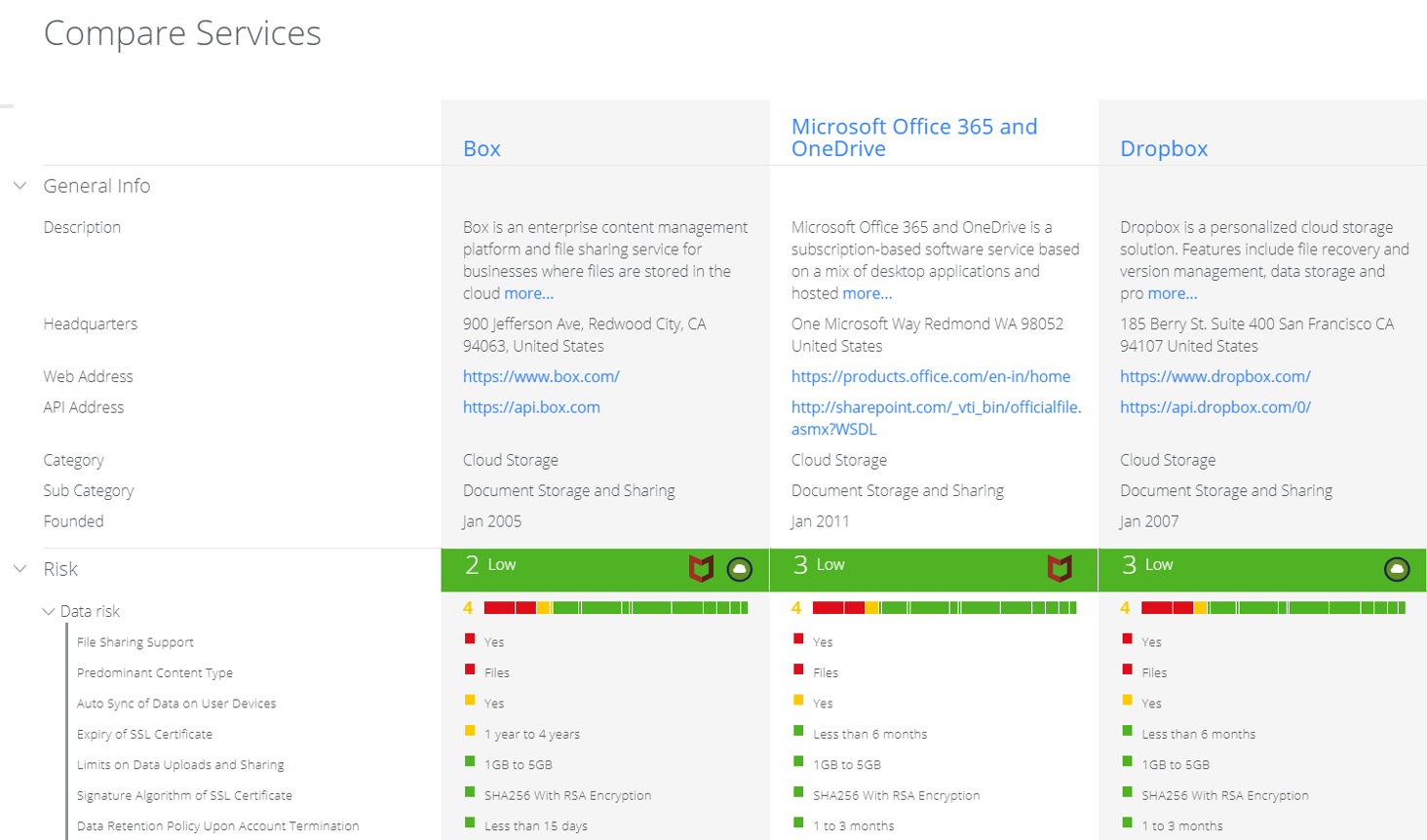
You can use it to consider introducing services to your company and to guide users who have applied for use of alternative services.
For Sanctioned IT
Sanctioned IT and risk
- What is Sanctioned IT IT?
Cloud services contracted and used by companies, authorized cloud services (Microsoft 365, box, Slack, etc.)
Safe as a service, but not all security is guaranteed by the service provider
The following risks must be addressed by the user


User abuse


account takeover


Data sharing with external parties
Shared Responsibility Model and CASB (Sanctioned IT) Visibility and Control Range
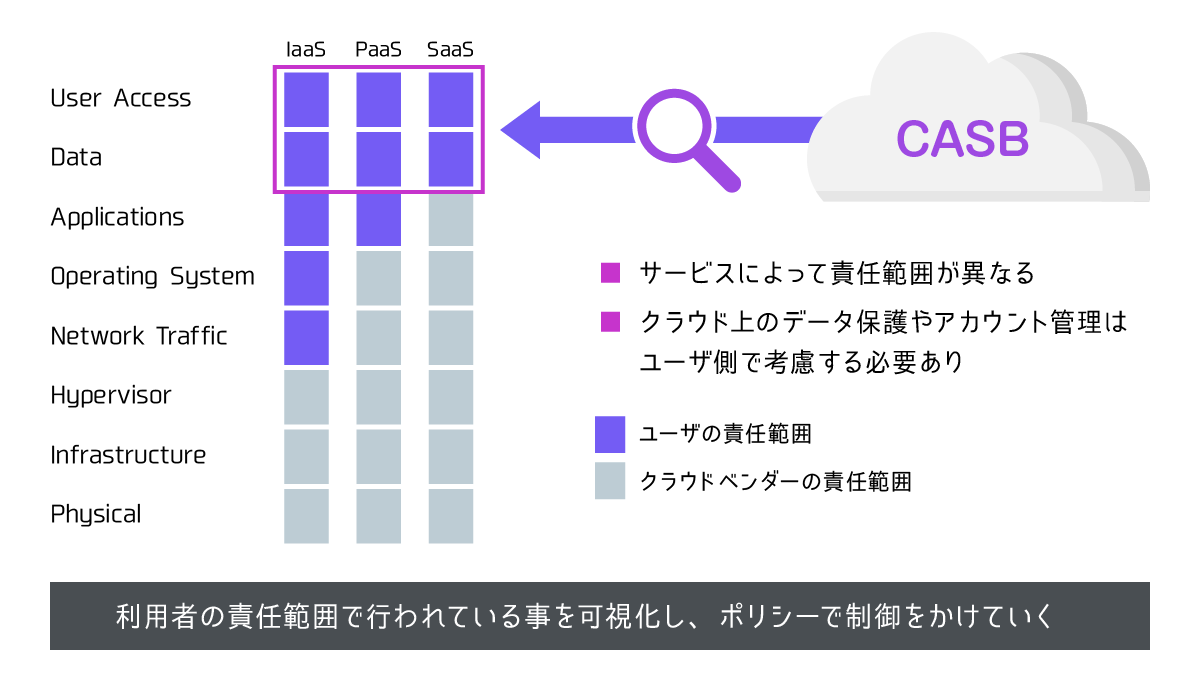
Support for IaaS
- Check logs and configuration information using API to detect account compromise and vulnerable settings
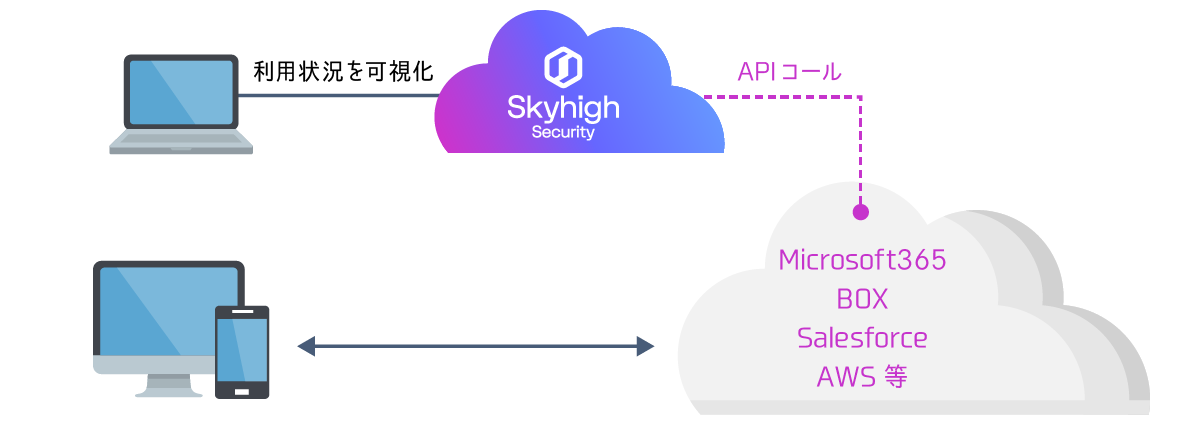
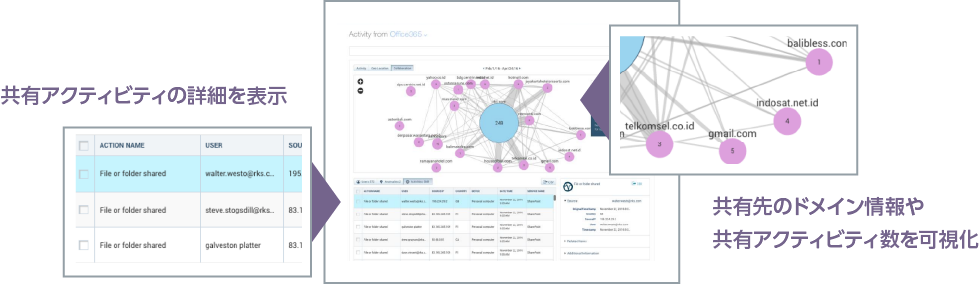
Skyhigh CASB makes API calls directly to the target SaaS and visualizes the sharing status of user activity files.
No network changes or agent installation required.
Feature 1: Activity Monitoring
- Collect logs via API and detect suspicious events using machine learning
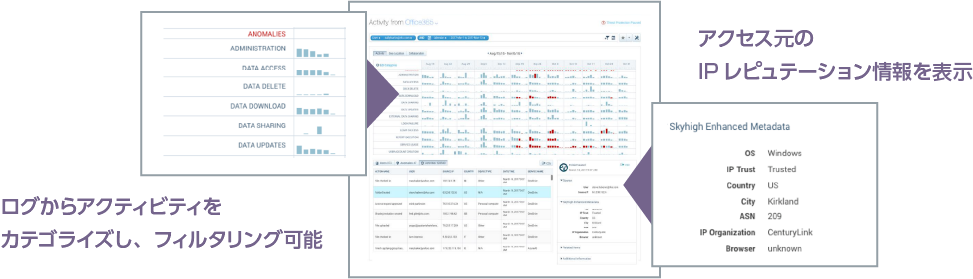
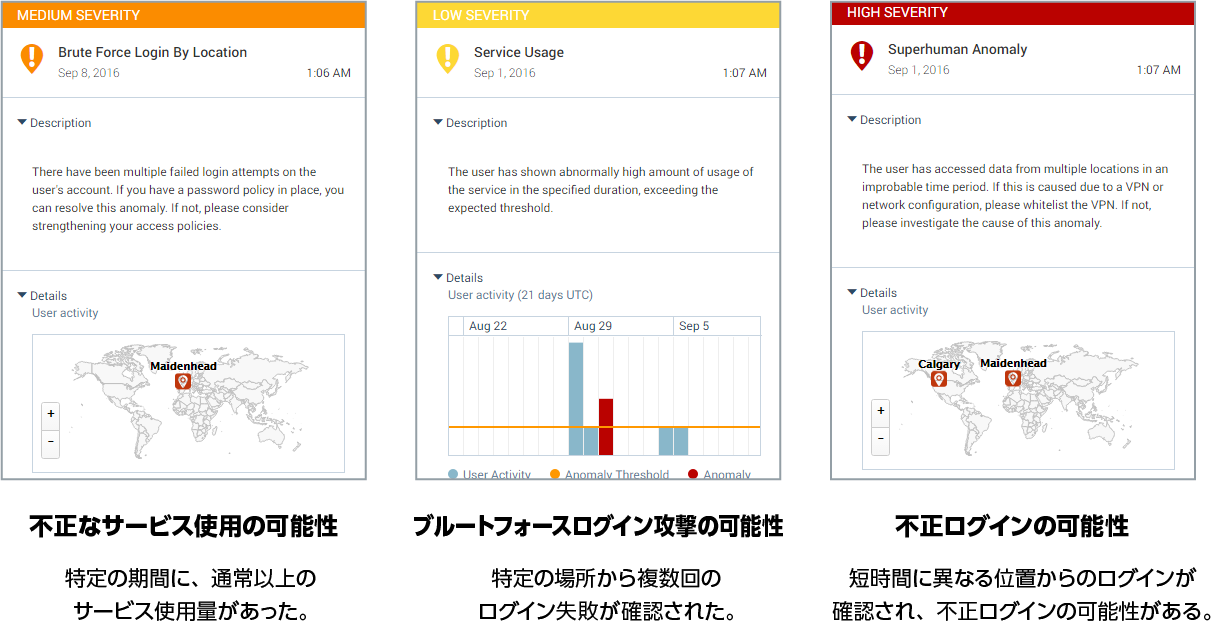
Feature 2: UEBA
- Detect unusual and suspicious events as anomalies and classify their severities
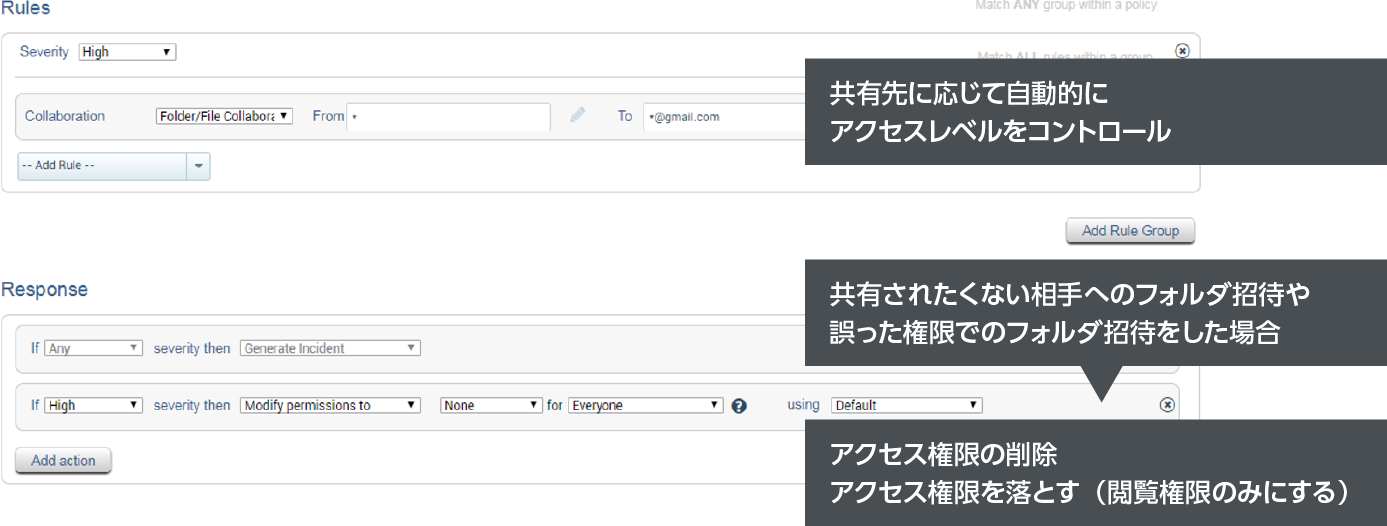
Feature 3: Collaboration Control
- Visibility of internal and external collaborators within the managed tenant
- Analysis of external collaborators' access to critical information
license
License lineup list
| License type | Billing target | ||
| Skyhigh CASB for | Shadow IT | - | Number of Employees |
| SaaS Unlimited | Supported SaaS Unlimited | Number of SaaS contract users | |
| Microsoft365 | Onedrive/Sharepoint | ||
| Teams | |||
| Mail/Onedrive/Sharepoint | |||
| Shadow IT/Mail/Onedrive/Sharepoint | |||
| Mail/Onedrive/Sharepoint/Teams | |||
| Shadow IT/Mail/Onedrive/Sharepoint/Teams | |||
| BOX | - | ||
| Dropbox | - | ||
| SLACK | - | ||
| drive | |||
| Salesforce | Sales Cloud | ||
| Service Cloud | |||
- Shadow IT
- The log retention period on the GUI is 1 year.
- Sanctioned IT
- The standard log retention period on the GUI is 100 days.
As an option, it is possible to extend the storage period to 1 year (365 days) for each regular price license + 10% fee.
- The standard log retention period on the GUI is 100 days.
remarks
- Only major services are listed for Sanctioned IT licenses. Please inquire about each optional license separately.
- Please inquire separately about other supported services.
Inquiry/Document request
In charge of Macnica Skyhigh Security
- TEL:045-476-2010
- E-mail:mfe-info@macnica.co.jp
Weekdays: 9:00-17:00