Infoblox
infoblocks
Cloud-based Protective DNS "Infoblox Threat Defense"
What is Infoblox Threat Defense?
Cloud service of "DNS Firewall" provided by Infoblox. Block outbound DNS-based communication by malware to prevent connections with botnets and C&C servers.
Infoblox Threat Defense Key Features
- Monitor and block DNS queries to malicious domains
- Block malicious DNS queries (DNS tunneling) with behavioral detection
- Obtain IP address, MAC address, user name, and device information as user information
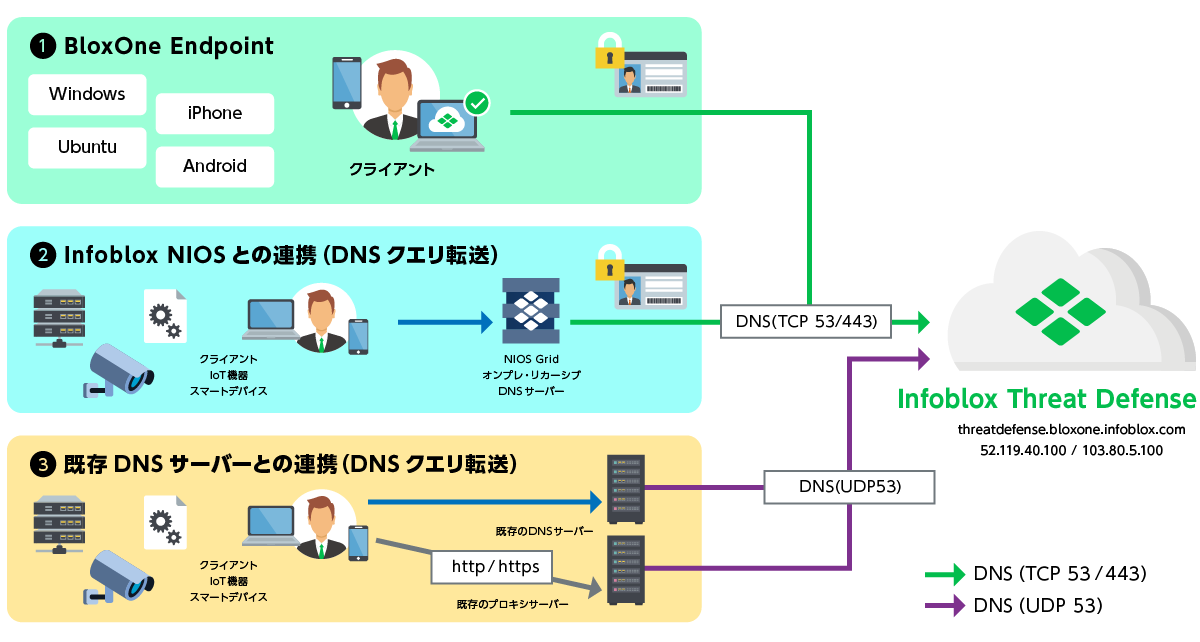
Three deployment models
Defense with 14 different feeds
| feed name | detail |
|---|---|
| Base (base.rpz.infoblox.local) |
A blacklist consisting of host names (FQDN) of malicious sites such as APTs, botnets, infected hosts/domains, exploit kits, abused DNS servers, bogon IP address sinkholes, etc. |
| Anti-Malware (antimalware.rpz.infoblox.local) |
A blacklist consisting of host names (FQDN) of threatened servers such as C&C servers, malware distribution sites, and active phishing sites |
| Ransomeware (ransomware.rpz.infoblox.local) |
A blacklist consisting of the host name (FQDN) of the ransomware (ransomware) connection destination or distribution site |
| Bogon (bogon.rpz.infoblox.local) |
In Internet routing control, route information that should not appear in the blacklist* routing table consisting of address blocks (IP addresses/subnets) that are not registered as advertiseable addresses is called a "bogon route." It includes unallocated IP addresses that have not been allocated by IANA, private IP addresses, and IP addresses reserved by IANA. |
| DHS_AIS_IP (dhs-ais-ip.rpz.infoblox.local) |
A blacklist composed of IPs shared with participating partners as cyber threat information in the U.S. Department of Homeland Security (DHS) AIS (Automated Indicator Sharing) program |
| DHS_AIS_Domain (dhs-ais-domain.rpz.infoblox.local) |
A blacklist consisting of host names (FQDN) shared as cyber threat information with partners participating in the U.S. Department of Homeland Security (DHS) AIS (Automated Indicator Sharing) program |
| AntiMalware_IP (antimalware-ip.rpz.infoblox.local) |
A blacklist consisting of IP addresses of threatening servers such as C&C servers, malware distribution sites, and active phishing sites |
| Bot_IP (bot-ip.rpz.infoblox.local) |
A blacklist consisting of IP addresses of bots used by malware to spread infection |
| Exploit Kit_IP (exploitkit-ip.rpz.infoblox.local) |
A blacklist consisting of IP addresses of malware distribution sites containing malicious programs to infect |
| Malware_DGA (malware-dga.rpz.infoblox.local) |
A blacklist consisting of domain names that can be used as C&C servers generated by the malware's Domain Generation Algorithm (DGA) |
| TOR_Exit_Node_IP (tor-exit-node-ip.rpz.infoblox.local) |
Blacklist configured by Tor exit node IP addresses *Tor exit nodes are gateways through which encrypted Tor traffic is routed to the Internet. |
| SURBL_Multi (multi-domain.surbl.rpz.infoblox.local) |
Malicious domain blacklist with up-to-date information on active malware, phishing, botnets and spam domains provided by partner company SURBL |
| SURBL_Fresh (fresh-domain.surbl.rpz.infoblox.local) |
Blacklist of newly observed domains with malicious activity provided by partner company SURBL |
| SURBL_Multi_Lite (surbl-lite.rpz.infoblox.local) |
A blacklist focused on only the latest and completely malicious sites so that the SURBL_Multi feed can be used on a low spec model |
Behavior detection function -Threat Insight-based defense
Infoblox Threat Defense Features
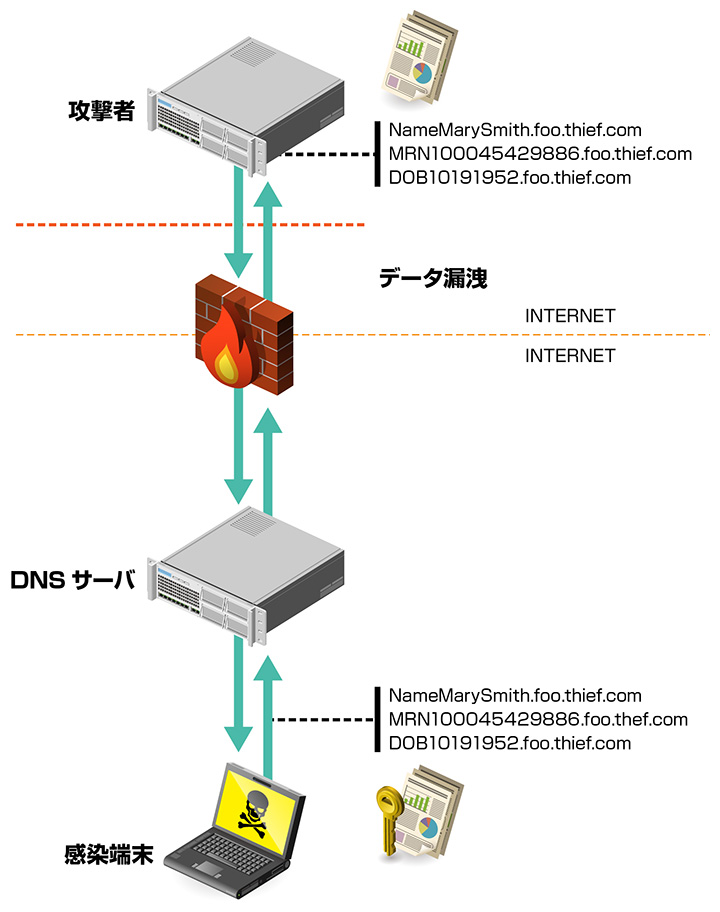
1. Block DNS-based malware
By exploiting name resolution and using DNS cache servers as stepping stones, malware bypasses the defense-in-depth of existing security measures. By blocking malicious DNS queries against these attacks, it is possible to block information leaks due to targeted attacks on a DNS basis.
2. Immediate use by simply installing an agent on the client
You can use the service without changing the existing network configuration. In addition, by installing an agent, it becomes possible to identify the terminal, and centrally manage the client's activity from the web GUI management screen.
3. Enhanced security in remote access environments
Even if your company has thorough security measures in place, it's often the case that you are not fully prepared to protect against access from devices taken outside the company. Infoblox Threat Defense blocks unauthorized communications outside the company that were previously uncontrollable.
Seamless integration with on-prem solutions
Integrated policy management, visualization, reporting and analysis
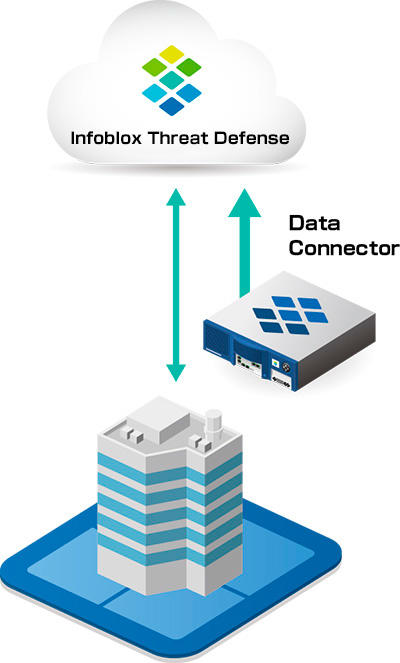
- Configurable individual or common policies for each on-prem and remote user
- Data Connector can be used to send on-premises Infoblox data to the Cloud for integrated analysis of DNS security.
- It is possible to check the history, etc., of each user/device's traffic between the on-premises LAN environment and the remote environment.
- Visualize user information such as MAC address, device information, DHCP lease history, and physical location (building, base)
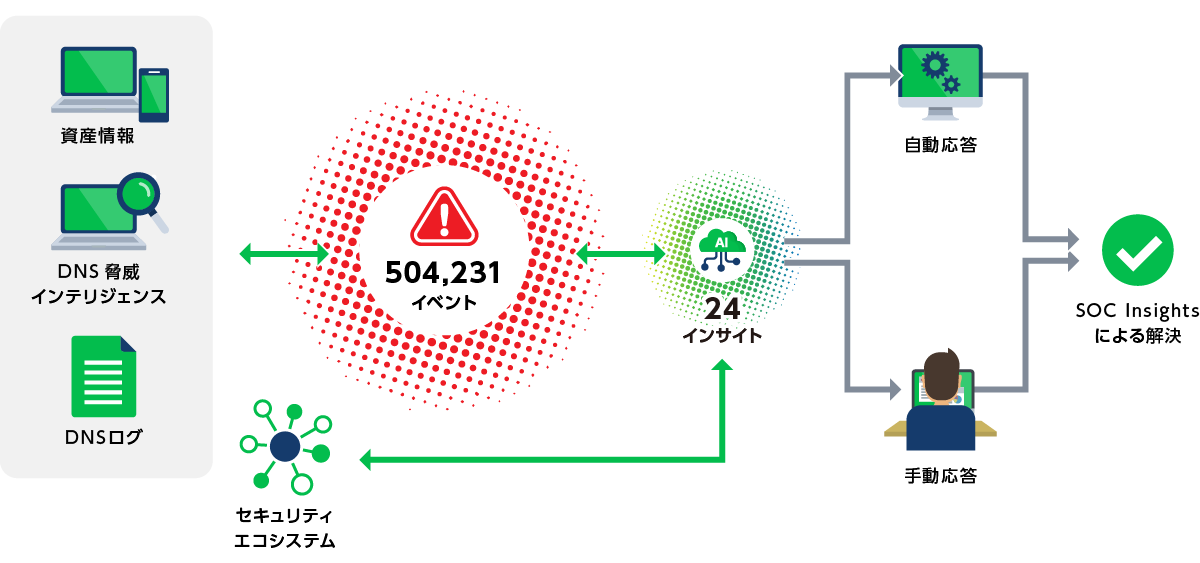
SOC Insights
Breakthrough AI-driven SOC operations tools integrated into Infoblox Threat Defense
- AI provides instant insights
It uses AI to analyze massive amounts of security event and network data and delivers immediate, actionable insights, dramatically reducing incident response times. - Identify and automate the threats that matter most
Leverage AI to analyze vast amounts of threat data and identify those that matter most, driving automation with the broader security ecosystem for rapid remediation and containment. - Reduce alert fatigue
Consolidate hundreds of thousands of security alerts into dramatically smaller, more manageable insights.
Example of implementation effect (reduced response time)
Eliminate alert fatigue and distill mountains of events into actionable insights
Inquiry/Document request
Macnica Infoblox
- TEL:045-476-2010
- E-mail:infoblox-sales@macnica.co.jp
Weekdays: 9:00-17:00