Akamai
Akamai
Zero Trust Security & Microsegmentation
Based on zero trust security, it implements ransomware countermeasures through user authentication and authorization and network micro-segmentation
Providing secure access for businesses
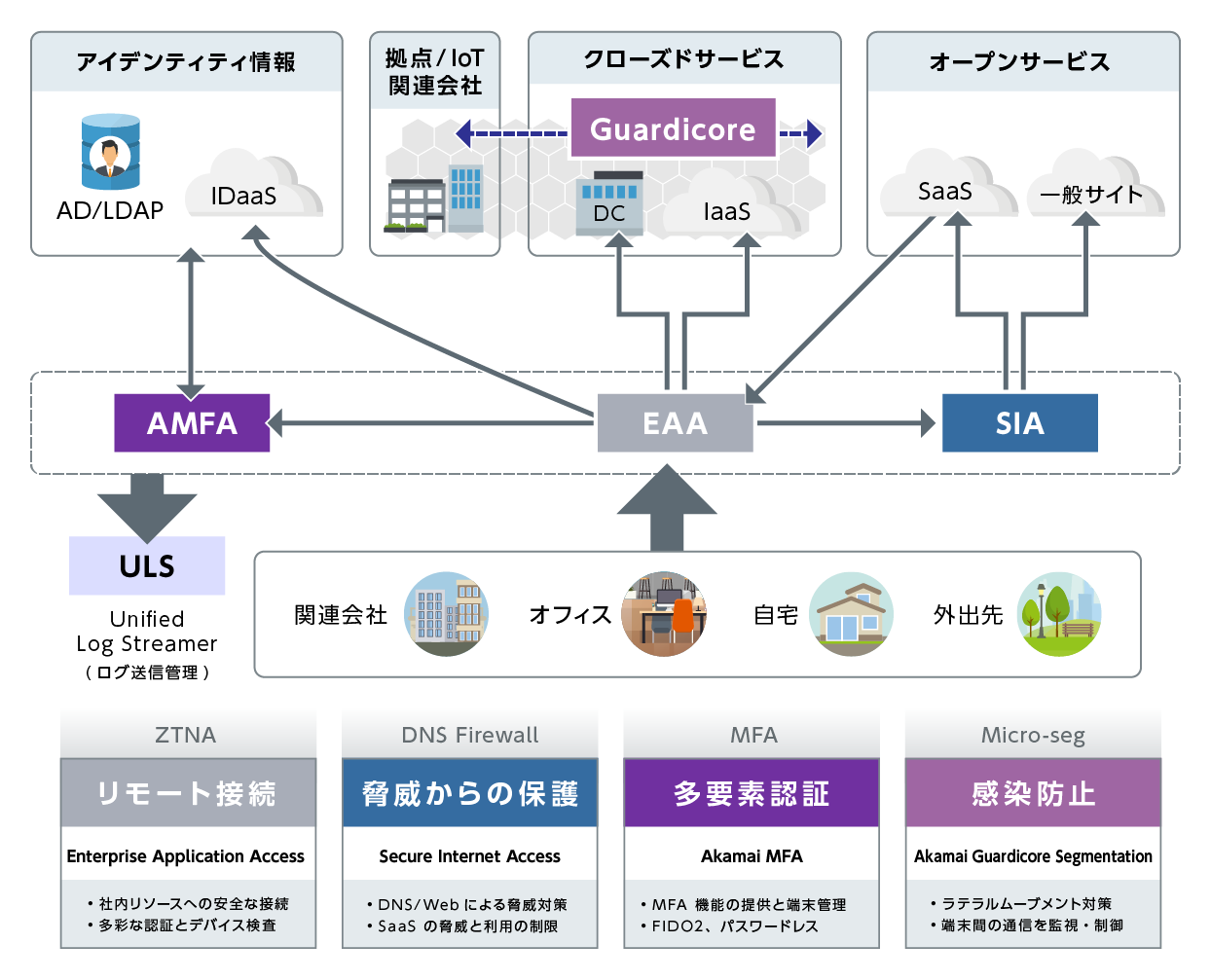
- Akamai Guardicore Segmentation (AGS)
Granular and flexible microsegmentation mitigates network risks and provides proactive and reactive defense against ransomware - Enterprise Application Access (EAA)
An identity-aware proxy that provides a strong and secure authentication foundation for in-house and external applications - Secure Internet Access (SIA)
DNS Firewall prevents access to dangerous sites and protects employees from the risk of phishing and malware infection
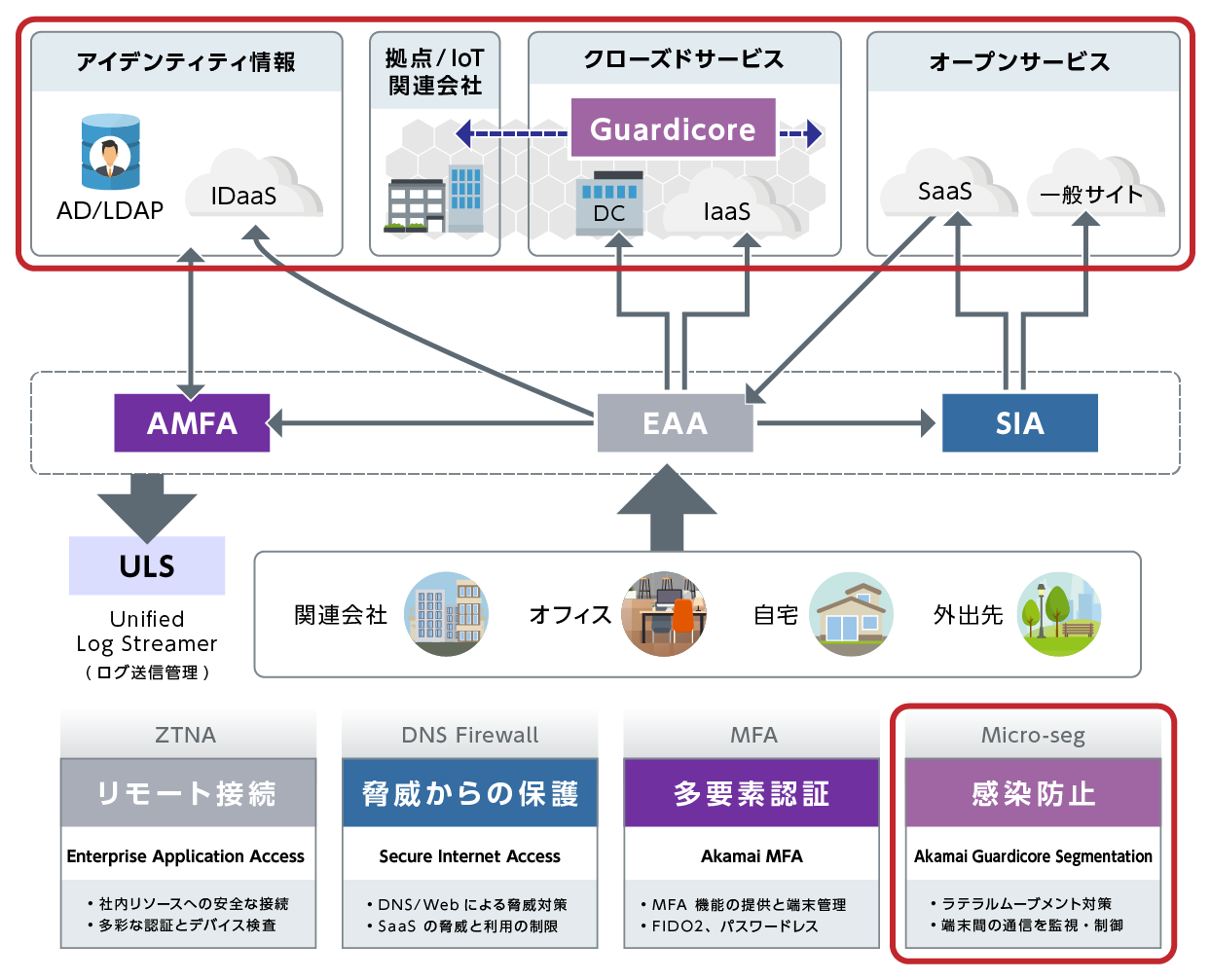
Akamai Guardicore Segmentation(AGS)
Microsegmentation to prevent ransomware from spreading
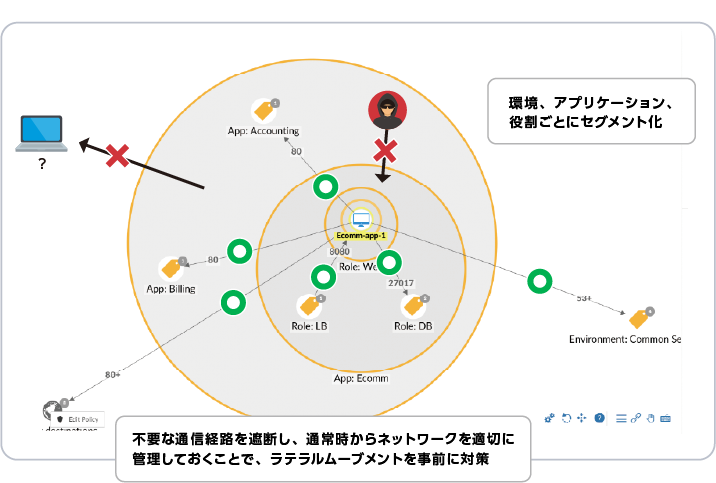
What is microsegmentation?
Microsegmentation is a solution that allows you to freely and flexibly segment networks based on roles such as applications, and restrict unnecessary communications.
It is effective in strengthening measures against ransomware and simplifying network management.
Three main features
- Allow only the minimum amount of communication necessary
The network is divided into small sections and managed to ensure only the minimum amount of communication is carried out.
A proactive measure against ransomware that blocks unnecessary communications and prevents damage from spreading through lateral movement. - Flexible Network Management
Agents (software) logically segment networks and control communications more flexibly than hardware implementations. - Reduce the operational burden of network management
Easy control by simply operating the management screen.
The visualized communication information is visually easy to understand.
Akamai Guardicore Segmentation (AGS) Features
①Easy operation
The basic operation of Akamai Guardicore Segmentation (AGS) mainly consists of the following three steps.
There are also convenient functions to reduce operational burden.
- Visualize the entire network based on communication data collected by agents installed on each device
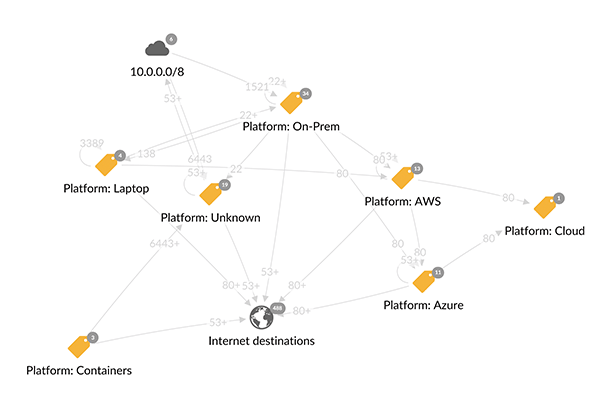
- Create labels* for each role, such as application, and map (label) devices
- Reduce the burden with the convenient function of setting up IP addresses (CIDR) and other information all at once
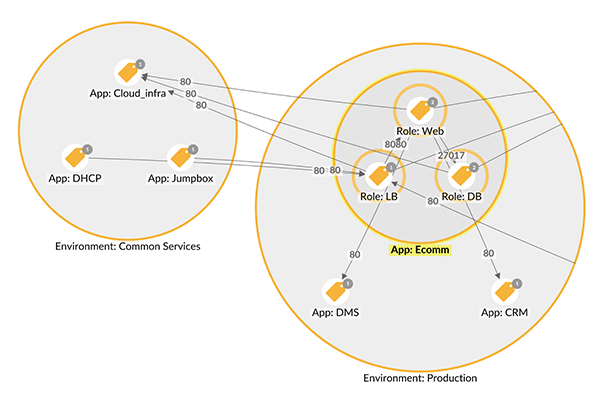
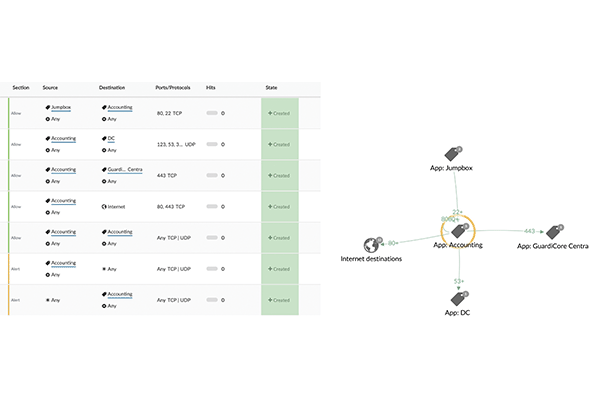
- Based on the mapped information, a policy** is created that defines the source and destination.
- Reduces the burden by creating policies based on actual communication data
*Label: Indicates the attribute information of a device. Multiple labels can be created for each application or environment, making it easier to classify and manage devices by role.
**Policy: Define the source and destination to control communication. Labels can be used for efficient configuration and detailed control according to use.
②Advanced security features
Akamai Guardicore Segmentation (AGS) provides threat detection and analysis using threat intelligence collected from around the world.
It has advanced security features, including proactive investigation (Hunt) by expert security engineers.
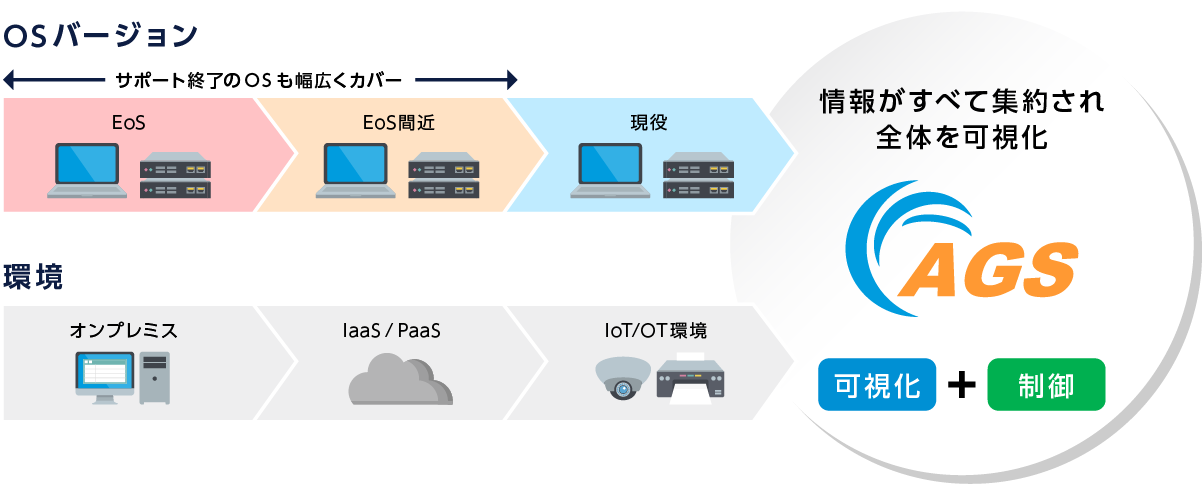
3. Covers a wide range of operating systems and environments
Akamai Guardicore Segmentation (AGS) agents support a wide range of operating systems, including those that are no longer supported, and can be deployed in a variety of environments.
Even in IoT/OT environments and cloud managed services where agents cannot be installed, communications can be visualized agentlessly by linking with switch and cloud functions.
Enterprise Application Access(EAA)
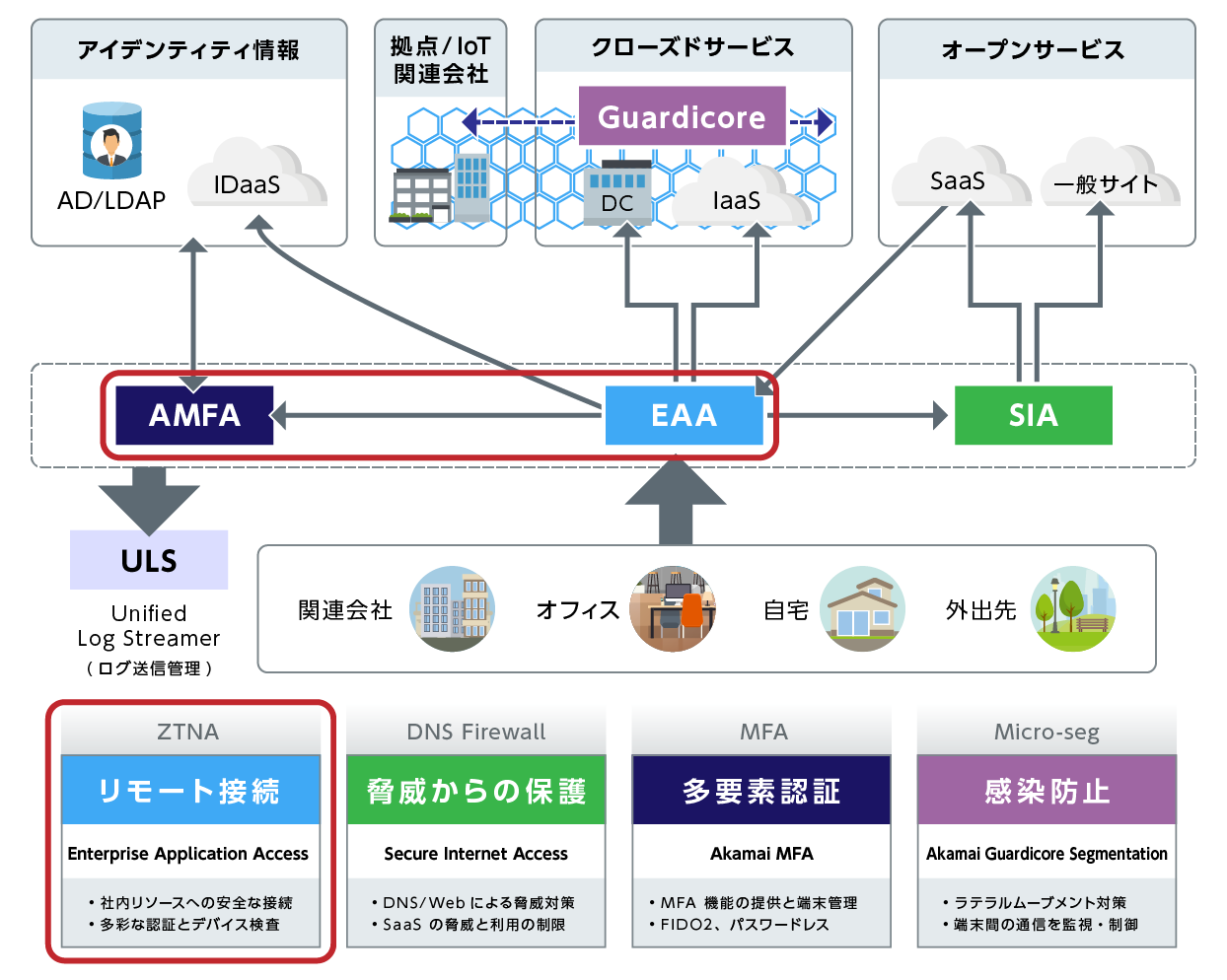
Enterprise Application Access (EAA) Features
Enterprise Application Access (EAA) is based on a zero trust model, tightly controls user access, improves security across your network, and is easy to manage thanks to seamless integration with your existing identity management systems and security tools.
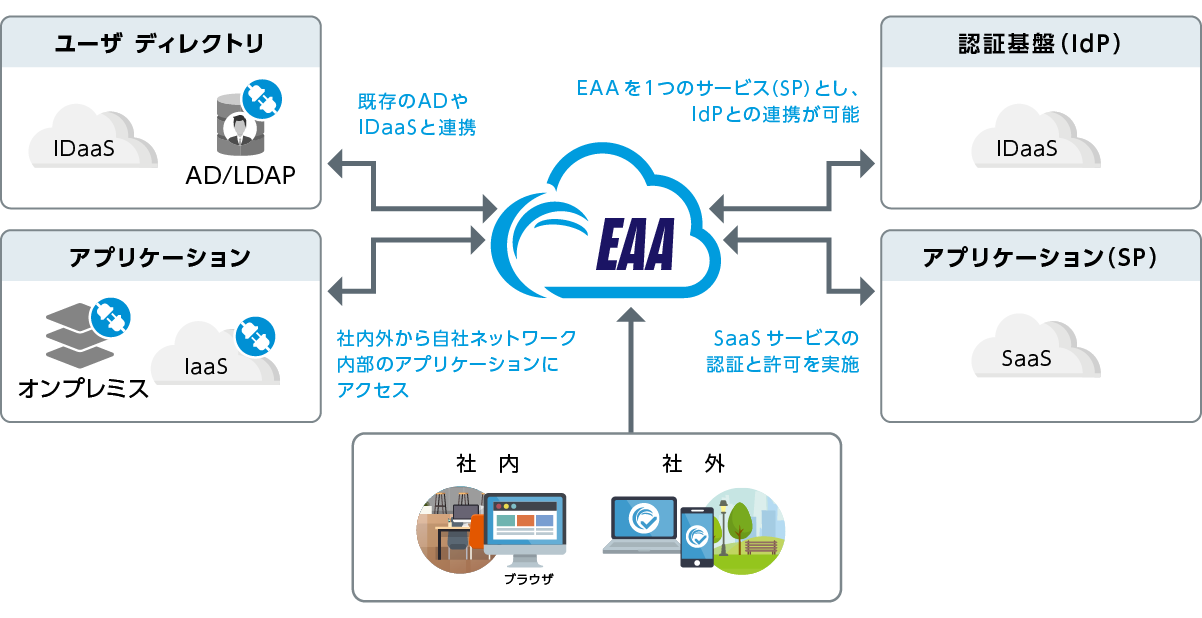
- Strong Authentication
- MFA can be easily achieved with various elements
- Integration with various IdPs (AD, SAML, OIDC, etc.) and SSO functionality
- Dynamic Authorization
- Determines access to resources based on device posture information from EAA clients and security products (EDR)
- Secure connection
- On the Internet, IP addresses/ports of protected resources are limited by encryption.
- Communication originating from DC eliminates connections from outside
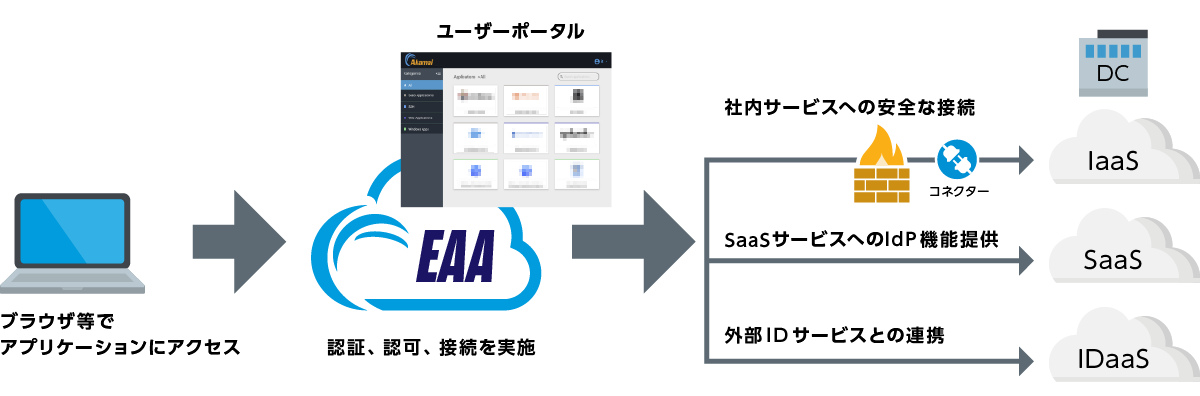
Operation image
EAA's strong authentication infrastructure enables secure access to a variety of applications. In addition, by linking with Akamai MFA, strong security is realized using multi-factor authentication.
Secure Internet Access(SIA)
DNS Firewall
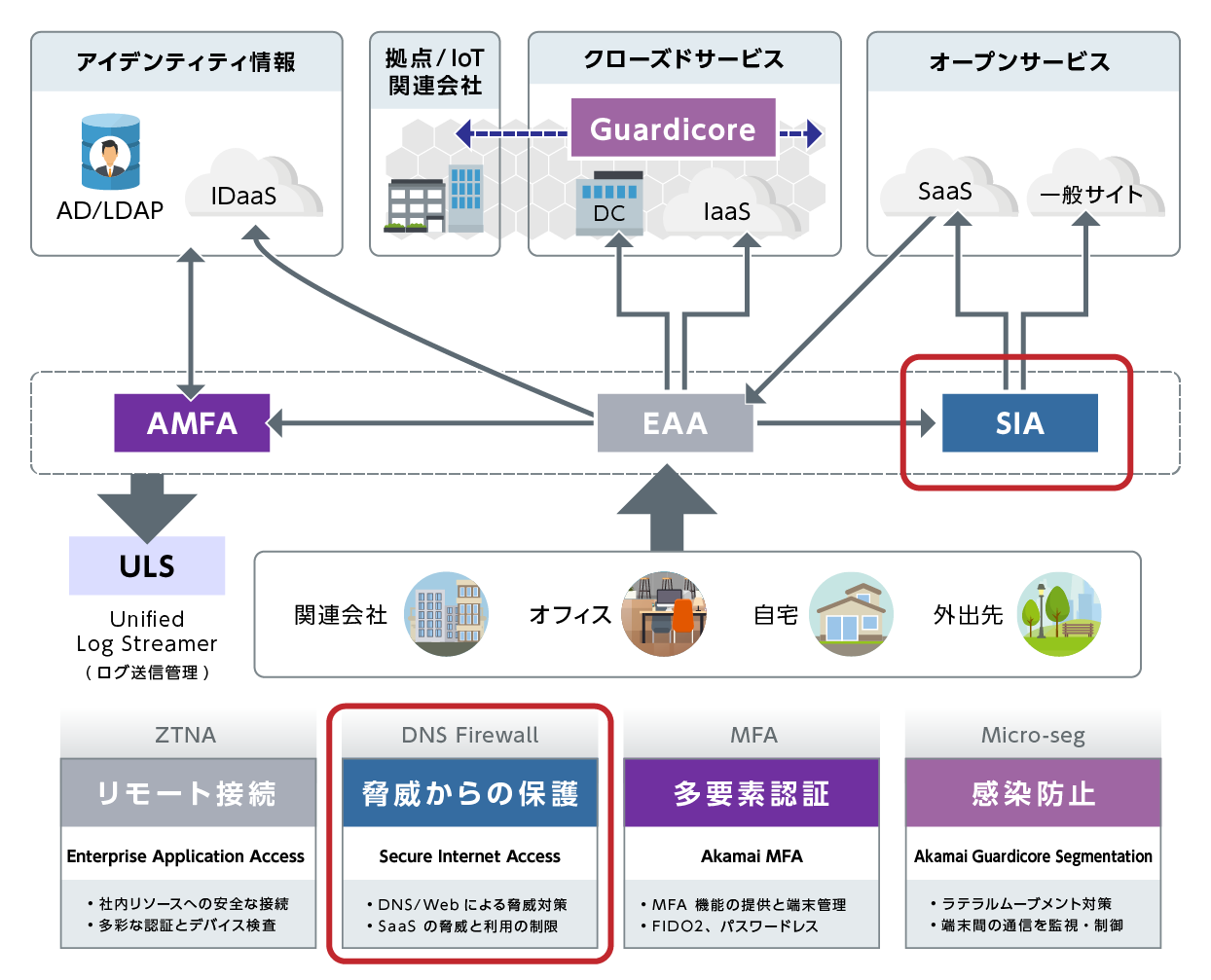
Features of Secure Internet Access (SIA)
Secure Internet Access (SIA) is a DNS firewall that identifies and blocks dangerous domains during the name resolution process, which is essential for web communication. This protects users from accessing dangerous sites. By utilizing the extensive reputation information collected by Akamai globally, we provide an environment that users can use with peace of mind without compromising user convenience.
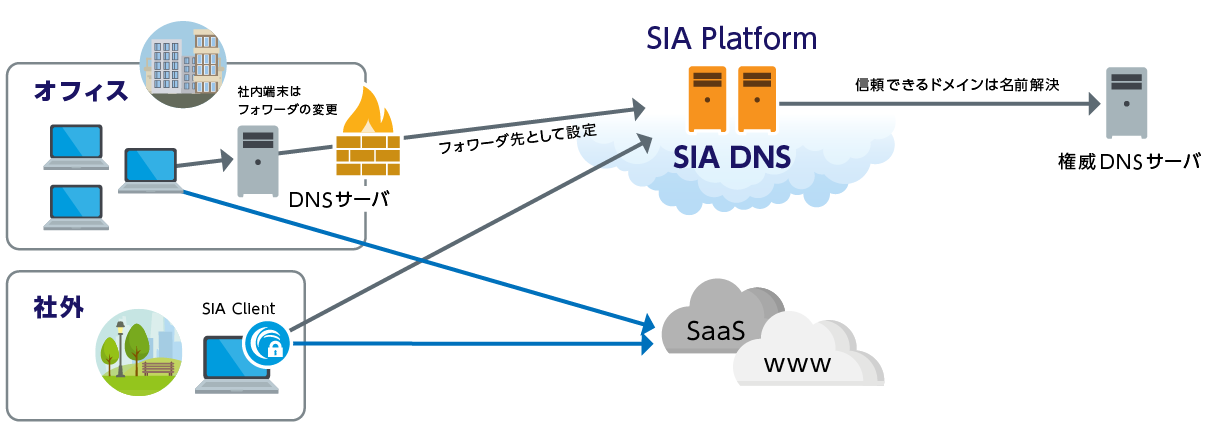
*If you want to identify devices in-house, you will need to install SIA Client or Security Connector.
- Highly accurate identification and blocking of dangerous domains
- Leverages Akamai's global threat reputation data
- Simple deployment
- Change DNS request destination to SIA
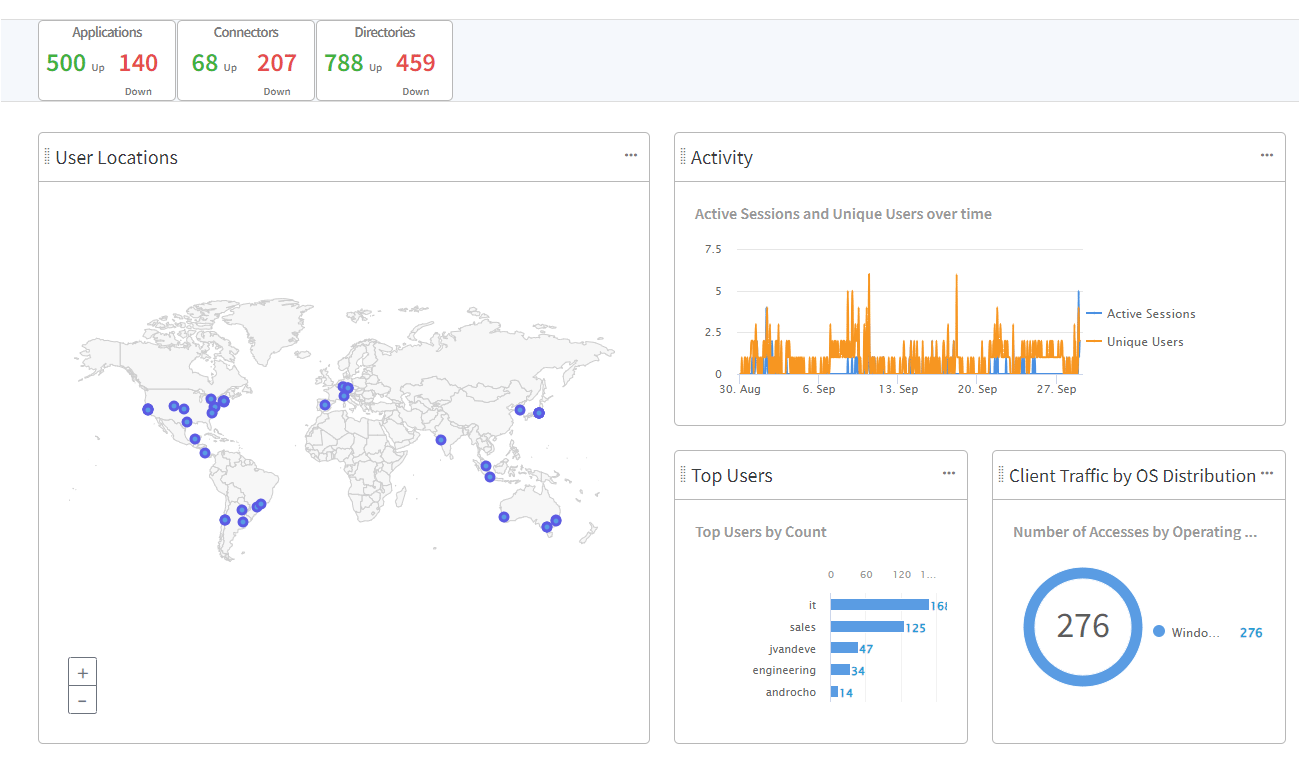
- Easy-to-read dashboard
- Check various information graphically in the Threat Overview dashboard