Specifications/Technical Information
Application for evaluation machine
- FAQ
I tried to introduce Prisma Cloud's CSPM Part 1: Cloud account registration

In recent years, the use of the cloud has progressed, and most companies have come to use the cloud as a matter of course. On the other hand, there are also many incidents caused by misconfiguration of the cloud. There is a solution called CSPM to prevent such misconfigurations, but I have never actually used it myself, so this time I used a product called Prisma Cloud to actually implement it in my environment.
In this article, I would like to introduce the series of steps up to the introduction of Prisma Cloud's CSPM, divided into Part 1 and Part 2. Prisma Cloud supports multiple platforms such as AWS, GCP, and Azure, and this time we will introduce CSPM for AWS accounts.
In Part 1, I will introduce Prisma Cloud and the cloud service that my team is actually using for verification, and how to visualize the security status of the cloud being used on Prisma Cloud.
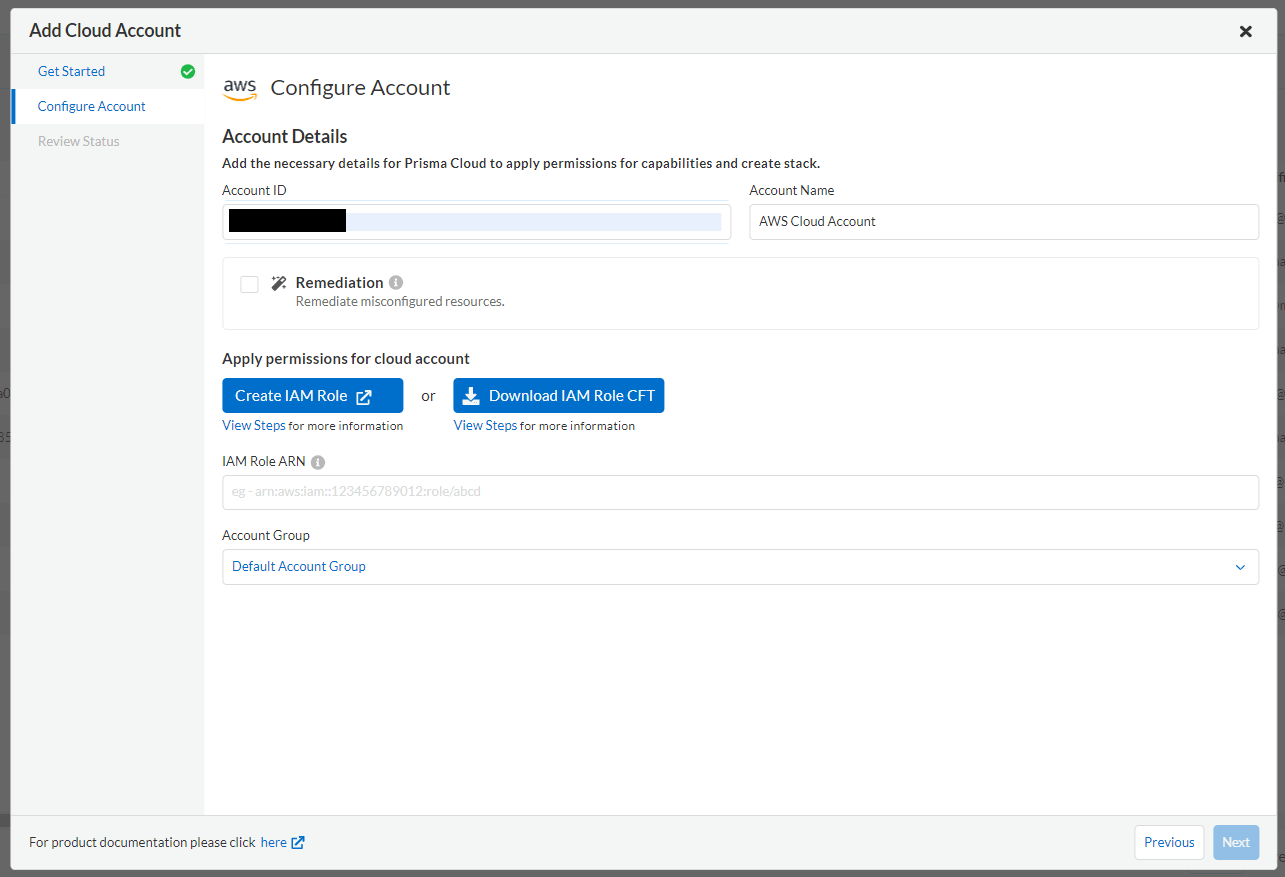
In order to monitor configuration errors with the CSPM function, it is necessary to obtain information from Prisma Cloud to AWS using an API. Therefore, it is necessary to create an IAM role for executing the API on the AWS side and register it on the Prisma Cloud console. I would like to actually try it.
*CSPM stands for Cloud Security Posture Management. It identifies security risks such as configuration errors and compliance violations when using cloud services such as AWS and GCP, and visualizes and implements countermeasures.
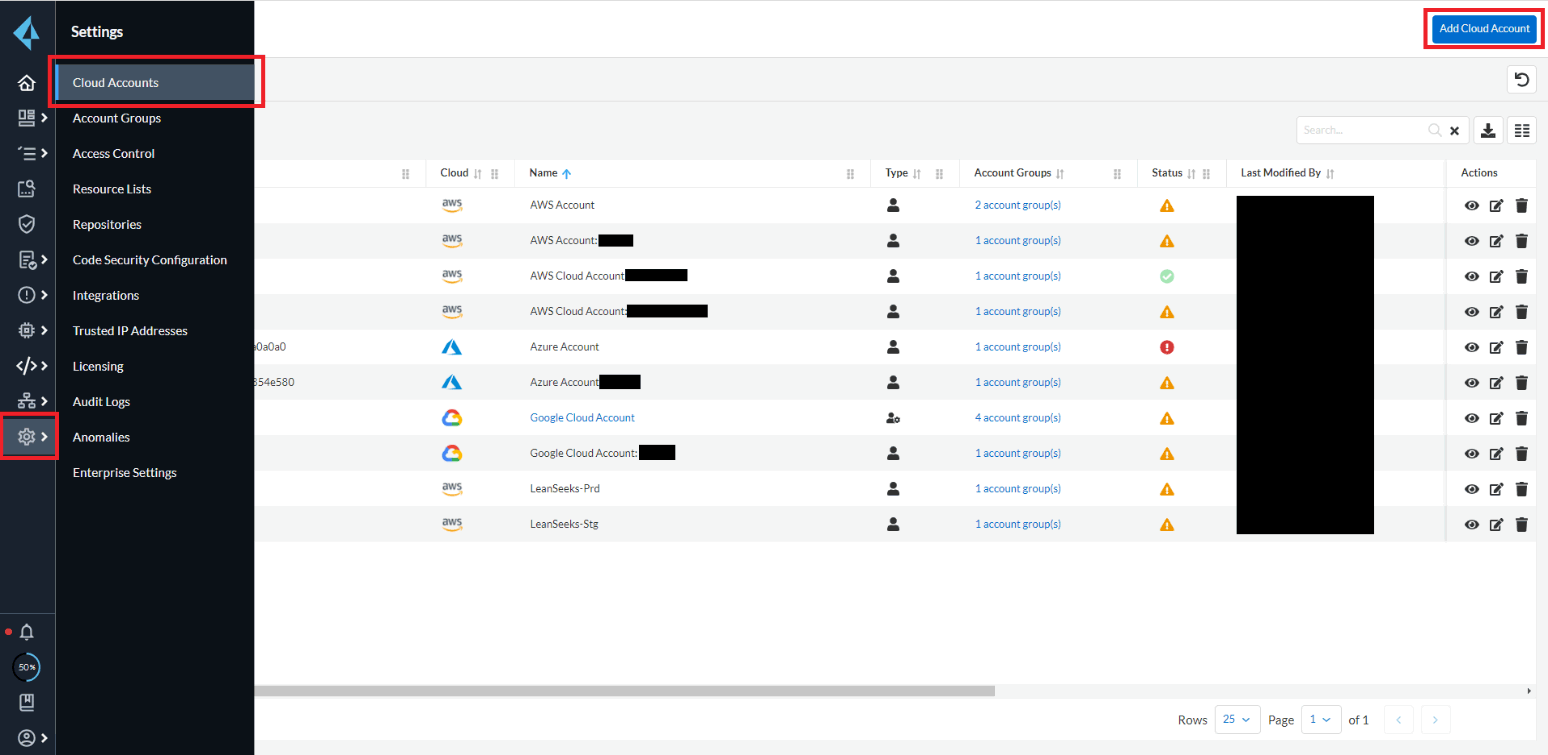
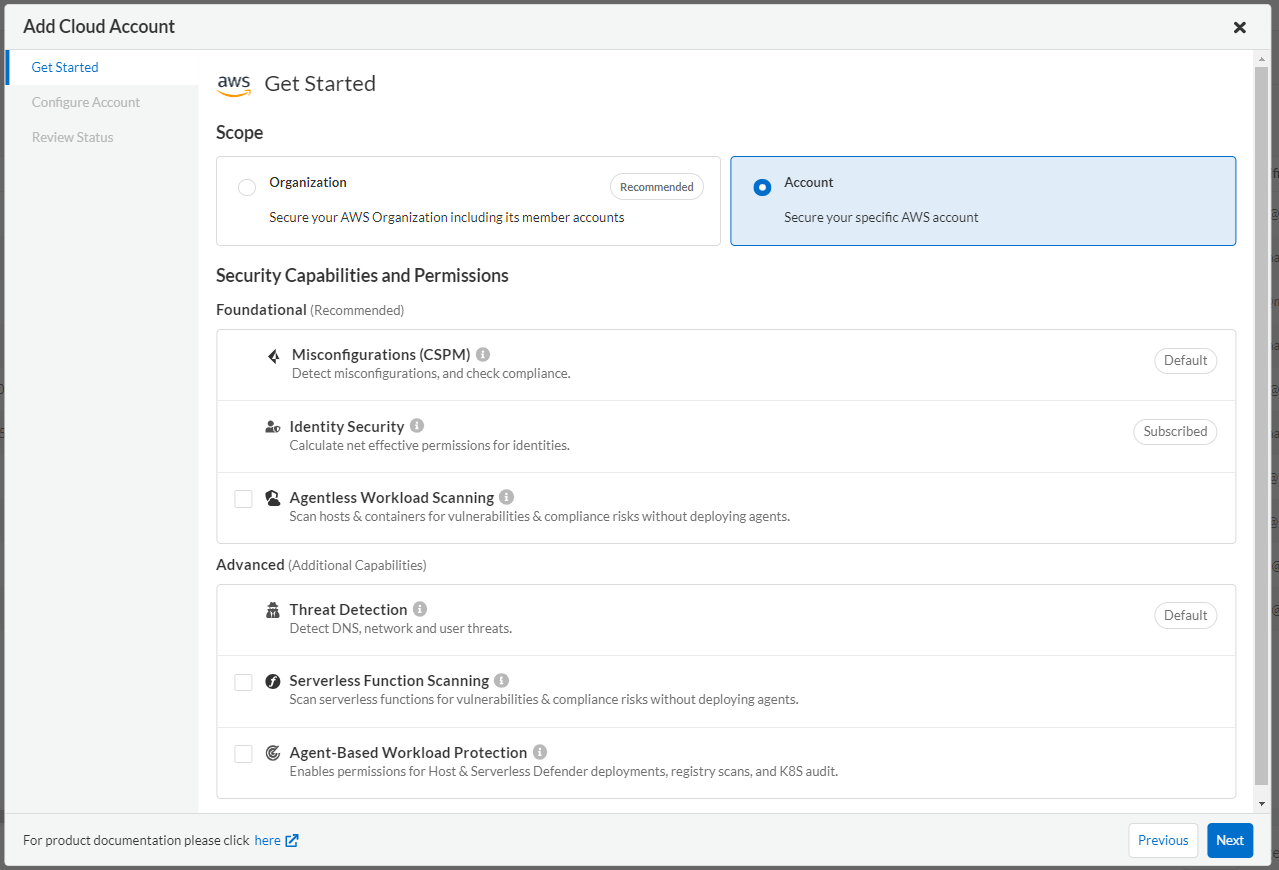
- Log in to AWS.
- Check 'I acknowledge that AWS CloudFormation may create IAM resources with custom names.' and click 'Create Stack'.
- Copy the PrismaCloudRoleARN.
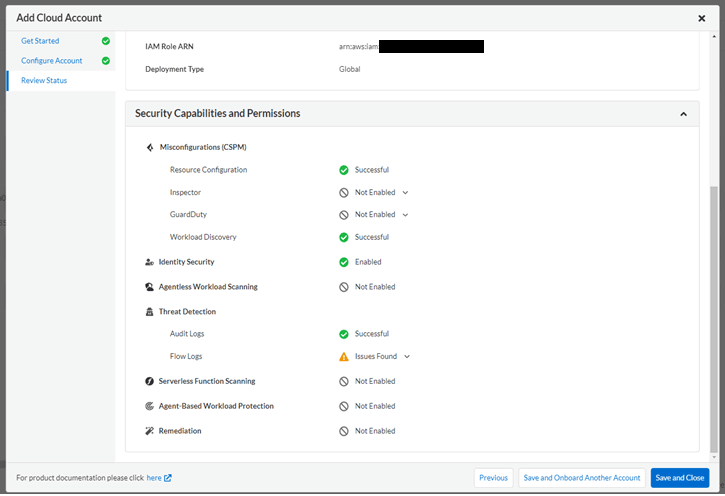
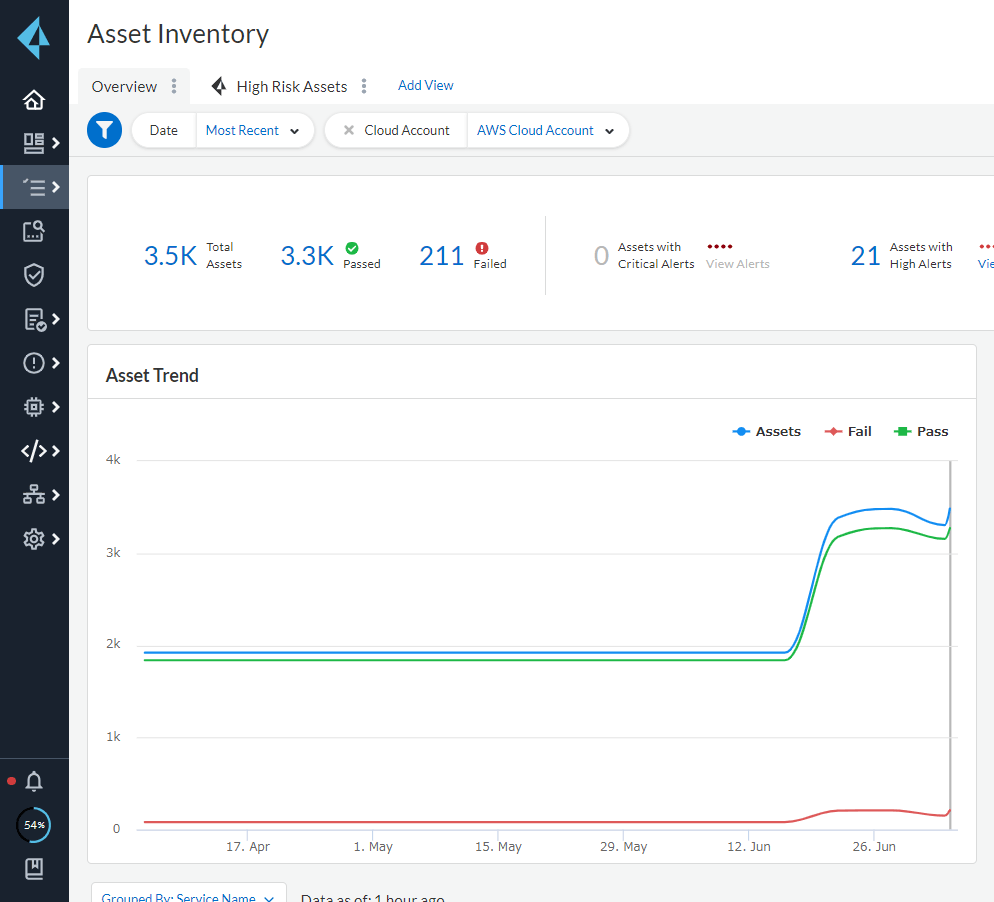
- Select "Inventory" > "Assets" on the left side of the console screen.
- Let's filter by the Cloud Account registered this time.
- Since it is a verification environment, there are some Failed items. In the next blog, we will introduce how to check the details of the specific problem.
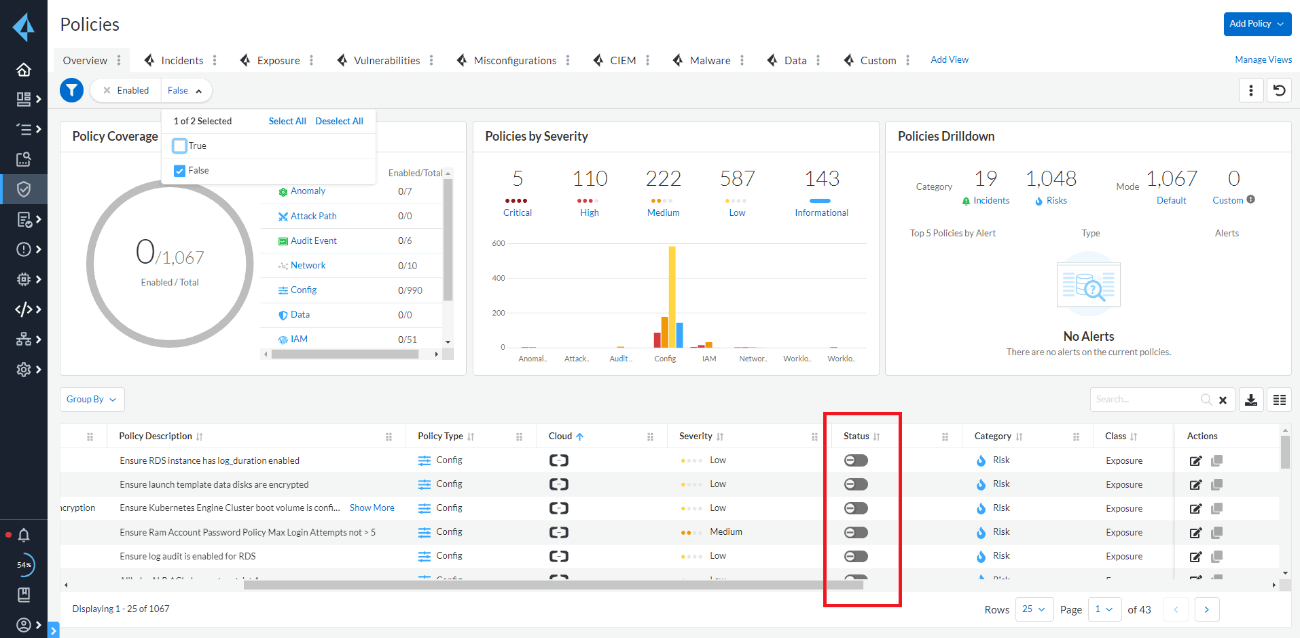
- Finally, when adding a Cloud Account for the first time, you need to change the Status of the policy you want to apply from Policies to Enabled.
Summary
This time, I tried to implement Prisma Cloud's CSPM function by myself, but it was easy to set up with easy-to-understand guidance on documents such as procedure manuals and GUI. In particular, the access rights on the AWS side were automatically created by AWS CloudFormation without having to set them myself, so the settings were completed just by clicking. Depending on the organization, there may be a lead time for procedures that require certain privileges, such as creating an IAM role, but in my environment, I was able to implement it in about 10 minutes while reading the documentation. . As mentioned at the end of the setting procedure, as a sticking point, in order to raise an alert, it is necessary to activate each policy you want to visualize, so please be careful.
In the second part, we will identify the cause and take countermeasures while looking at the alerts visualized on Prisma Cloud.
Related video: "Achieving Secure Application Development -Improving Security Baselines with Posture Management-"
Providing a secure work environment for employees is a common challenge for all businesses. Suppression of security incidents is also recognized as a major issue in application development sites, but there are situations in which developers have to lower the priority of security due to unique reasons, and the importance of security is neglected. is not uncommon. In this session, we will explain Posture Management, a preventive solution for implementing the minimum mechanism necessary to reduce the probability of security incidents in the development environment and significantly improving the security baseline.
Inquiry/Document request
In charge of Macnica DevOps
- TEL:045-476-1972
- E-mail:twistlock@macnica.co.jp
Weekdays: 9:00-17:00


