
In Japan, the number of fraud victims who may be triggered by smishing is on the rise, and has become a serious social problem. Smishing fraud is not limited to Japan. Phishing is also occurring overseas, taking advantage of the convenience of SMS, and each country is working on countermeasures against it. In this column, we will summarize and compare the smishing countermeasures being promoted in various countries. First, we will introduce the common smishing reporting hotline "7726".
What is Spam Reporting Service?
The Spam Reporting Service is a service used worldwide as a common system for reporting smishing among telecommunications carriers.
Overview of Spam Reporting Service (7726 Service)
When users receive a smishing message, they forward the message to "7726". In some cases, they may be asked to provide the sender's phone number later. The forwarded messages are then aggregated and analyzed for message patterns and senders.
The GSMA[1] launched a pilot of the Spam Reporting Service in 2010, and it is now implemented by individual carriers, industry associations and regulators.
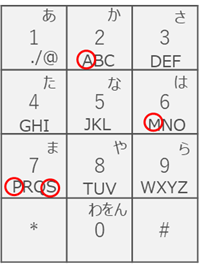
The forwarding destination number "7726" comes from the fact that it corresponds to SPAM on a smartphone keyboard.
Hereafter, Spam Reporting Service will be referred to as the "7726 Service."
[1] The GSMA (GSM Association) is an industry group consisting of mobile communications operators and related companies. Its members include nearly 800 mobile communications operators as well as terminal vendors, network vendors, and software companies.
Benefits and challenges of the 7726 service
There are three possible benefits to each supply chain from implementing the 7726 service.
1. Visualization of damage
The first benefit is that it visualizes the overall picture of smishing damage. Each telecommunications carrier can grasp the smishing that passes through their own SMS server, but to obtain data such as the overall volume of smishing being sent, whether it has increased compared to the past, and whether there are differences between carriers, a system that crosses carriers is necessary. The 7726 service is able to provide such basic data, and it is expected that it can be used not only by telecommunications carriers, but also by companies and government agencies whose brands are being deceived, to decide on countermeasures to be implemented.
2. Improving the efficiency of countermeasures
Second, by conducting cross-service analysis, it will become possible to implement more efficient measures against smishing. Based on analytical data on smishing senders and sending patterns, it will be possible to strengthen filtering and user education measures.
3. Improved reliability
The third benefit is that it leads to improved reliability of the entire system. Efficient blocking not only reduces the percentage of smishing messages that reach users, but also gives users a sense of security by visualizing the damage and sharing the status of countermeasures being implemented.
In addition to the benefits mentioned here, other benefits for users include the fact that transfer can be done with simple and common operations, which saves time and makes filing easier.
On the other hand, one issue is that SMS contains confidential communication and personal information, so service providers need to handle it with care.
(For more information on the secrecy of communications and the progress of domestic telecommunications carriers in taking measures against smishing, please see the following page: https://www.macnica.co.jp/business/consulting/columns/145451/)
Non-SMS Phishing Reports
Phishing is the practice of scams that impersonate real organizations to steal personal information such as user names, passwords, account IDs, ATM PINs, and credit card numbers.[1] In addition to email-based phishing, there are other types of phishing, such as SMS-based smishing (SMS+Phishing) and voice-based vishing (Vishing=Voice+Phshing).
The 7726 service is a reporting window for SMS smishing, but there are also cases where a general reporting window for all phishing, including email, is published on the Web. Because the delivery mechanisms for SMS and email are different, it is common to have a common initial reporting window page and then provide reporting methods according to the delivery method.
One of the benefits of setting up a central reporting desk is that it will help prioritize countermeasures by making the overall damage caused by phishing visible, such as which methods are causing the most damage and where measures should begin.
Next, we will explain the status of phishing reports including 7726 services in each country. Depending on the country or organization, actions equivalent to phishing may be expressed as "spam" or "scam." In this column, we will standardize the term "phishing" to mean any action that steals personal information, and use the terms "smishing" and "vishing" when specifying that it is SMS/Voice, and "email phishing" when distinguishing email.
Spam Reporting Service (7726 Service) Implementation Status in Each Country
The 7726 service has expanded since the GSMA launched a pilot service in 2010, and is currently available in the United States, Canada, the United Kingdom, Australia, New Zealand, Singapore, etc. Since each operator introduces it at their own discretion, there is no official information showing the worldwide adoption status.
The 7726 service is operated in a variety of ways, including by telecommunications industry associations (USA) and government agencies (New Zealand and the UK).
America
In the United States, the 7726 service is provided by CTIA, a wireless communications industry association whose members include telecommunications carriers, communications equipment vendors, service providers, and content creators. The CTIA website explains how to report smishing if you receive it.
CTIA accepts reports of smishing, but does not provide a reporting desk for email phishing or vishing, and does not provide reports on the analysis of smishing reports it receives, nor does it publish regular reports.
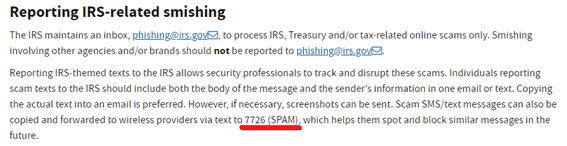
Figure 1 IRS [3]
Telecommunications companies recommend using the 7726 service as a contact point for filing smishing reports, but there are also government agencies that recommend using the 7726 service. Figure 1 shows the IRS (Internal Revenue Service) website, which lists forwarding to 7726 as a way to handle IRS-related smishing (the red text was added by the column author) [3]. The FTC (Federal Trade Commission) [4] and USPS (United States Postal Service) [5] also explain on their websites that forwarding to the 7726 service is a countermeasure when receiving smishing. By consolidating smishing messages impersonating these agencies into the 7726 service, it will be possible to comprehensively analyze and take countermeasures.
new zealand
In New Zealand, the government agency DIA (Department of Internal Affairs) operates the 7726 service [6]. Figure 3 shows the DIA spam reporting site, which is a general reception site for three types of phishing: Email, SMS, and fax. Selecting "Report TXT spam" takes you to the page in Figure 4, which explains how to report smishing, and shows videos explaining how to report spam to the 7726 service for both iOS and Android.
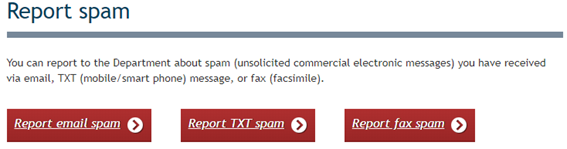
Figure 3 Report Spam[6]
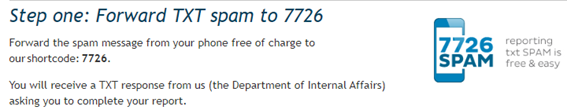
Figure 4 Report Text Spam to 7726[7]
DIA summarizes the status of phishing reports for both email and SMS in the "Digital Messaging Transparency Report" and publishes it as an annual report [8]. The first edition will be the 2022 edition. This is when the malware FluBot infection became a major problem, and it summarizes the history of countermeasures. The 2023 edition will be the second report.
Figure 5 2023 Digital Messaging Transparency Report [8]
The Digital Messaging Transparency Report provides some interesting data on the trend in the number of email/SMS reports.
![図6 Email/SMSフィッシングの申告数の推移[9]](/business/consulting/columns/145965_img06.png)
Figure 6. Trends in the number of reported email/SMS phishing attacks [9]
The graph shows that the number of SMS reports consistently exceeds the number of email reports, and that while the number of email reports is roughly constant, the number of SMS reports fluctuates greatly. This is a valuable report, as there is little data comparing the ratio of email/SMS phishing. However, it is important to note that the data is the number of reports submitted to the DIA, not the total number of phishing incidents.
England
In the UK, the regulator Ofcom runs the 7726 service [10]. Ofcom 's 7726 service accepts reports of scam calls (vishing) as well as scam texts (phishing), and provides a video on their website explaining how to make a report.
![図7 Ofcom 7726サービス [10]](/business/consulting/columns/145965_img07.png)
Figure 7 Ofcom 7726 service [10]
Figure 8 shows that the NCSC (National Cyber Security Centre) accepts various types of fraud reports, including email, SMS, and voice. [11] Figure 8 shows the NCSC 's fraud report acceptance methods. 7726 is presented as the number to report scam text messages.
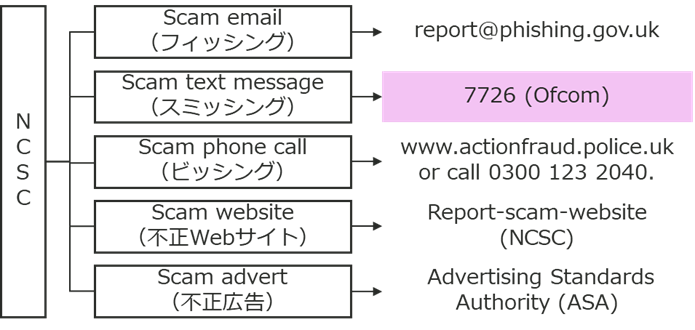
Figure 8 NCSC 's phishing measures
Japan
Although the 7726 service is not offered in Japan, several organizations other than telecommunications carriers will accept reports of smishing SMS.
Anti-Phishing Council
The Japan Anti-Phishing Working Group was established in April 2005 and is responsible for collecting and providing case information, materials, and news about phishing scams, raising awareness, and conducting technical and institutional studies. As part of these activities, the Japan Anti-Phishing Working Group accepts reports of phishing scams. [12]
![図9 フィッシングの報告(フィッシング対策協議会)[12]](/business/consulting/columns/145965_img09.png)
Figure 9 Phishing report (Anti-Phishing Working Group) [12]
To distinguish between email and SMS, when reporting, there is a field to enter the receiving method, and you can select email, SMS, advertisement, SNS, unknown, or other. Phishing reports are not made through the 7726 service, but through the web, where you can enter the sender, message body, etc.
The Japan Anti-Phishing Working Group analyzes the reports and publishes a monthly report showing trends in the total number of reports, number of URLs, number of brands, etc., but does not publish totals for email/SMS.
Spam Consultation Center
The Spam Consultation Center, a general incorporated foundation run by the Japan Data Communications Association and commissioned by the Ministry of Internal Affairs and Communications, accepts reports of spam emails and SMS that are believed to violate the Specified Commercial Email Act. [13] To report an SMS, enter the date and time the smishing message was received, the phone number of the device that received it, the carrier, the device OS, the sender (phone number or display name), and the text of the message into the web form.
![図10 迷惑メール情報提供のお願い(一般財団法人日本データ通信協会)[13]](/business/consulting/columns/145965_img10.png)
Figure 10: Request for information on spam emails (Japan Data Communications Association) [13]
The Spam Center publishes the number of spam emails reported, but does not report the total number of emails/SMS.
Summary of phishing reporting desks
Table 1 summarizes the status of phishing reporting desks in each country, including those other than 7726.
|
England |
America |
new zealand |
Japan |
|
|
7726 |
Already provided |
Already provided |
Already provided |
Not yet provided |
|
7726 |
Ofcom (Ministry of Communications) |
CTIA (wireless communications industry association) |
DIA (Department of the Interior) |
|
|
Phishing Report Hotline (including numbers other than 7726) |
SMS, Voice |
CTIA: SMS only |
Email, SMS, FAX |
Anti-Phishing Council: Email, SMS, etc. |
Table 1. Status of phishing reporting desks
at the end
This article provided an overview of the smishing reporting service "Spam Reporting Service (7726 Service)"and the current status of its implementation in various countries. Although the damage caused by smishing has become a social issue, there have been almost no reports that quantitatively analyze the current status of smishing. Therefore, by introducing the 7726 Service, it will be possible to visualize the distribution status of smishing from the perspective of reporting, and it is expected that by reporting the distribution status as in New Zealand, telecommunications carriers, regulatory authorities, and victim companies will be able to widely share basic data to consider countermeasures from their respective positions.
reference
[1] https://www.antiphishing.jp/consumer/abt_phishing.html
[2] https://www.ctia.org/protecting-yourself-from-spam-text-messages
[3] https://www.irs.gov/newsroom/irs-reports-significant-increase-in-texting-scams-warns-taxpayers-to-remain-vigilant
[4] https://consumer.ftc.gov/articles/how-recognize-and-report-spam-text-messages
[5] https://www.uspis.gov/news/scam-article/smishing-package-tracking-text-scams
[6] https://www.dia.govt.nz/Spam-Report-Spam
[7] https://www.dia.govt.nz/Spam-Report-TXT-Spam
[8] https://www.dia.govt.nz/Spam-Transparency-reports
[9]https://app.powerbi.com/view?r=eyJrIjoiZmM0ZWJmYzItZTA1ZC00ODMzLWEyZGItNmU0MTlmZjdmZmRlIiwidCI6ImY2NTljYTVjLWZjNDctNGU5Ni1iMjRkLTE0Yzk1ZGYxM2FjYiJ9
[10] https://www.ofcom.org.uk/phones-and-broadband/scam-calls-and-messages/7726-reporting-scam-texts-and-calls/
[11] https://www.ncsc.gov.uk/collection/phishing-scams
[12] https://www.antiphishing.jp/registration.html
[13] https://www.dekyo.or.jp/soudan/contents/ihan/index.html
