
Tanium
タニウム
見えないものは守れない
こんな課題はありませんか?
絶えることのないエンドポイントセキュリティにおける各種課題
- 端末のOS/ソフトウェアの脆弱性有無が不明、端末OSも複数ある
- 端末の管理(全端末の把握)がしっかりできていない
- 海外・国内に拠点が多数あり、資産管理に工数がかかる
- 最新パッチの速やかな適用ができていない
エンドポイントのリアルタイム可視化、迅速なリスク対処を行うプラットフォーム
Taniumは全世界全数端末のPC・サーバにおけるリアルタイムの可視化と制御を叶える製品です。
サイバーハイジーンの徹底の為に必要な「網羅性」「確実性」「リアルタイム性」も持った資産情報の収集とパッチ配布、ソフトウェアアップデートが必要です。
Taniumでは特許技術を取得した独自のネットワーク構造を強みとし、①独自のプロトコルを用いた通信方式、②クライアント間でリニアチェーンを組みTaniumサーバとエンドポイントの通信を削減、③シャード分割・キャッシュ保持の機能を用いて、従来の課題であった「中継・分散サーバの存在」、「ネットワーク負荷」という根本的な課題を解決します。
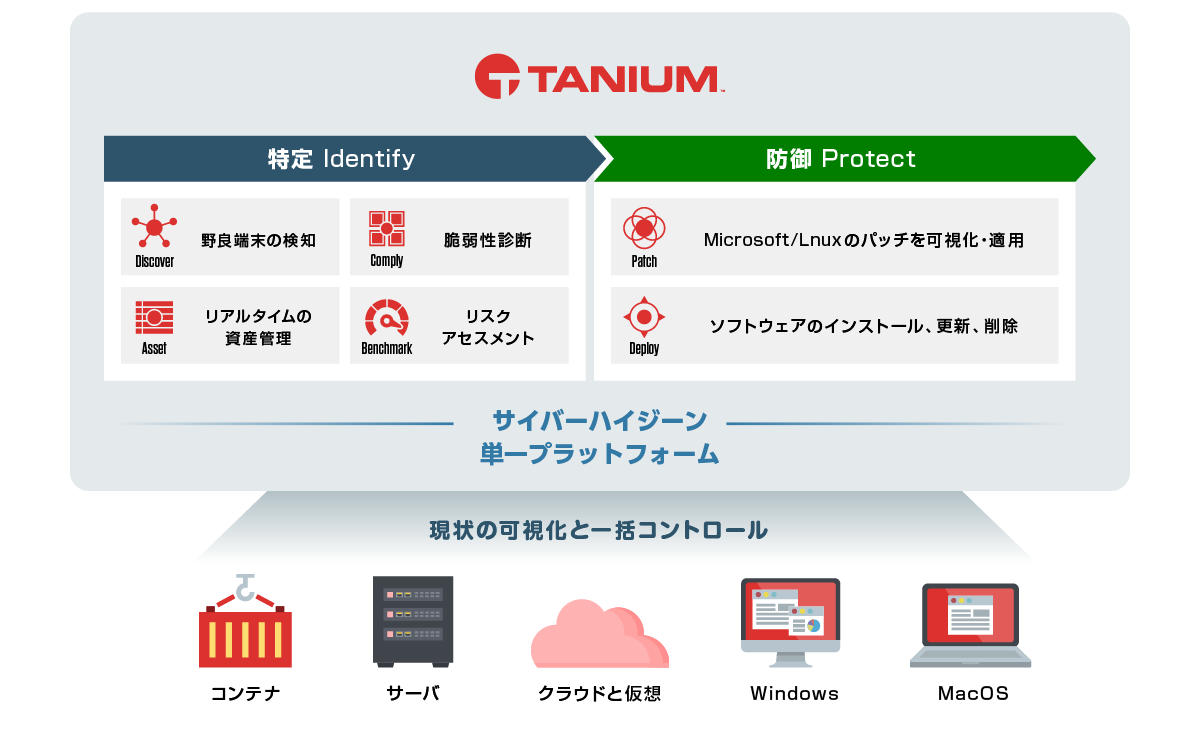
【Point1】リニアチェーンで大規模環境でも“リアルタイムなシステム管理”を実現
- 管理端末が数十万台でもリアルタイムに検索・対処
- 不許可/脆弱なアプリの使用規制
- Windows10以降の負荷軽減
【Point2】リアルタイムにエンドポイントを可視化・コントロール
- 社内に潜む非管理端末を可視化
- 違反端末の発見・修正
- Windowsパッチやインストーラは自動分割し、低帯域でも確実に配信
- 感染端末をリアルタイムに検索し複数台へ一斉対処
【Point3】コマンドラインで実行できることはすべて可能
- 500種類以上のSensor(情報を取得できるスクリプト)保有
- 全オンライン端末の取得したい情報を収集・表示
- スクリプトのカスタマイズ可能
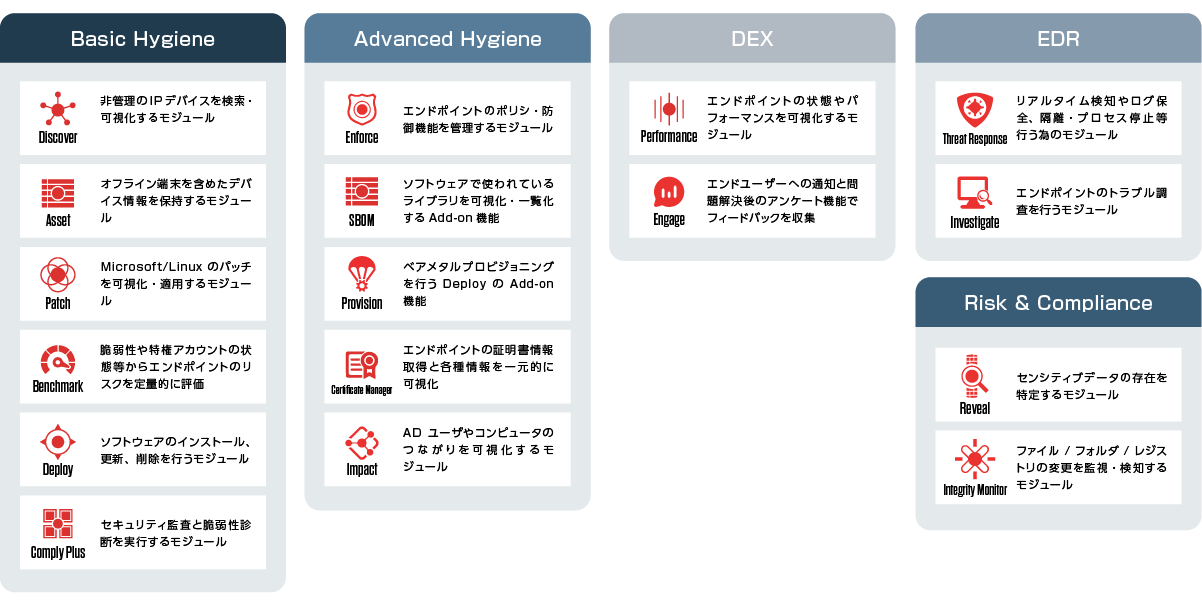
【Point4】プラットフォーム上で選択可能な拡張モジュール
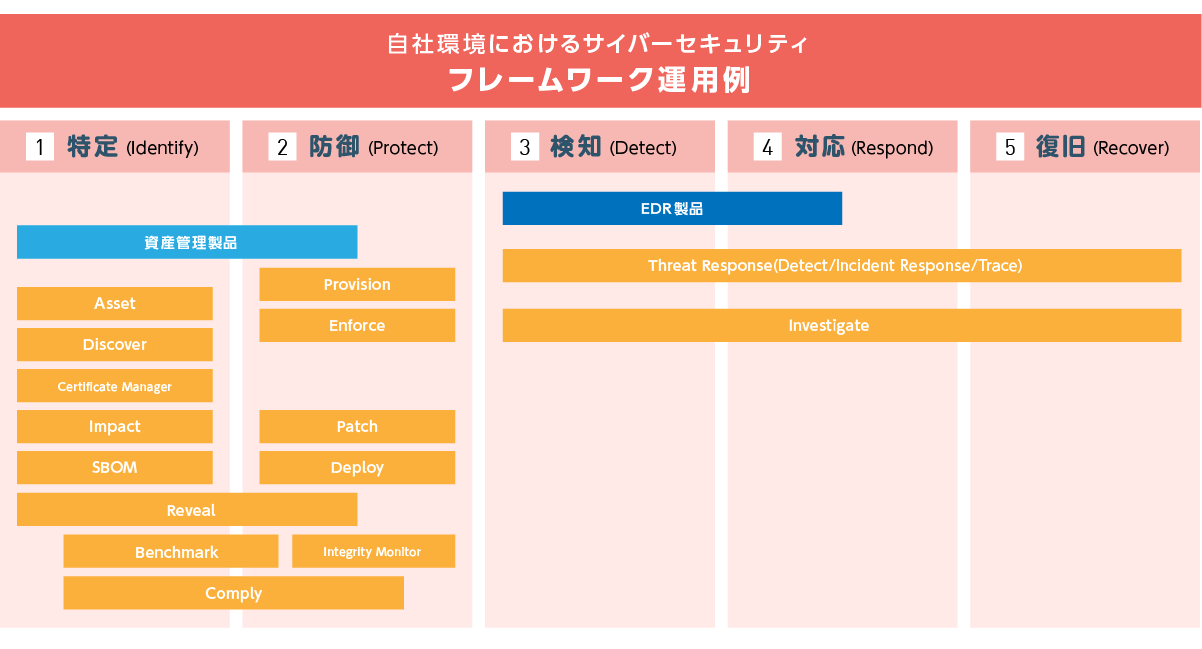
【Point5】自社環境におけるサイバーセキュリティフレームワーク運用例
導入事例
セミナー
これから開催 開催終了 {{ item.title }}
{{ item.seminarClass }}
{{ cat }}
{{ item.makerName }}
開催終了
開催前
開催中
開催中
開催終了
{{ item.seminar_start_date__display_1 }} {{ item.seminar_place__display_1 }}
オンデマンド動画
会社説明
| 会社名 | Tanium Inc. |
|---|---|
| 設立 | 2007年 |
| 所在地 | 米国カリフォルニア州エメリービル |
| 代表者 | Dan Streetman |
| ウェブサイト | https://www.tanium.com/ |
お問い合わせ・資料請求
株式会社マクニカ Tanium 担当
- TEL:045-476-2010
- E-mail:tanium_sales@macnica.co.jp
平日 9:00~17:00





