Specifications/Technical Information
Specifications/Technical Information
solution
solution
- Pulse Secure Manga, Secure Access Story - Zero Trust/SSL-VPN/Remote Access Solutions
- Pulse Secure Secure Access Story through Manga - Episode 1 Remote Work
- Pulse Secure Secure Access Story through Manga - Episode 2 MDM Introduction
- Pulse Secure Secure Access Story through Manga - Episode 3 Ransomware Countermeasures
- Pulse Secure Secure Access Story Learned from Manga - Episode 4 University Information System
- Connect Secure Series Solutions - Zero Trust/SSL-VPN/Remote Access Solutions
- Connect Secure Series Solutions - PulseSecure SDP for Zero Trust Model

Pulse Secure
pulse secure
Important [Regarding Vulnerability Fix Version]
A vulnerability affecting Pulse Secure products has been confirmed. For each vulnerability, countermeasures have already been implemented depending on the specific version, so please be sure to upgrade to the vulnerability fixed version.
Click here for details
Episode 3 Ransomware Countermeasures
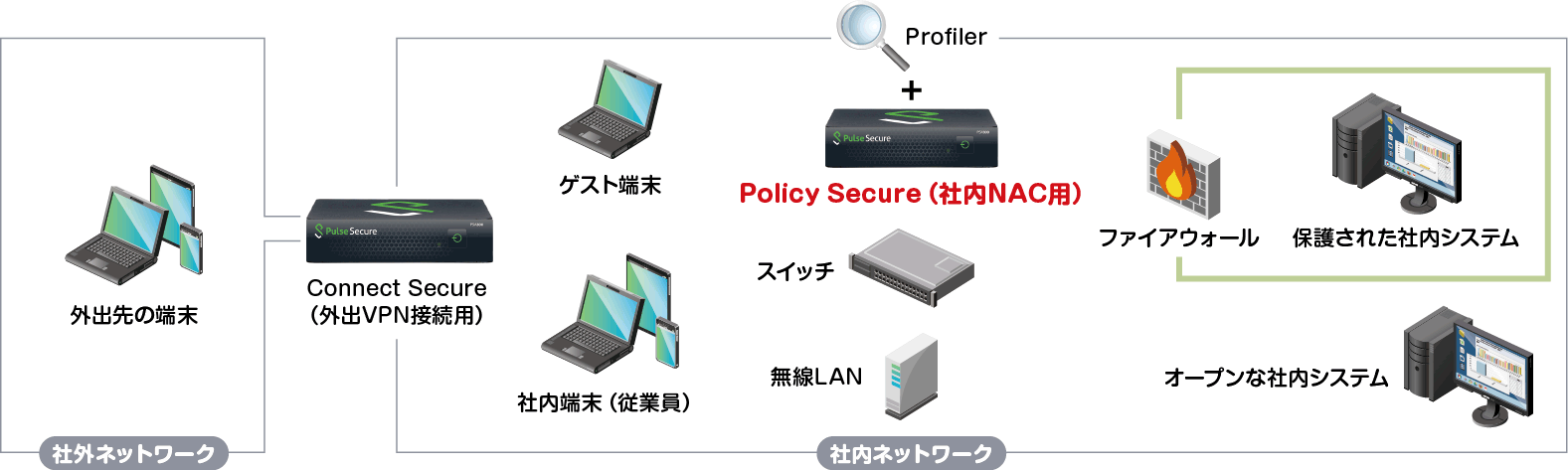
With Pulse Secure, computers that may be infected with ransomware cannot be connected to the company.
Solution brief
- An authentication solution that checks the device when accessing the company LAN and allows only healthy devices to use company resources.
- As a countermeasure against ransomware such as "WannaCrypt0r", it is possible to prevent the spread of infection by setting a policy that does not allow access to the internal network for terminals that do not have the latest Windows Update applied to the terminal.
- Seamless integration with third-party user authentication, firewalls, switches, wireless LANs, etc.
| Diverse check items | |
|---|---|
| predefined rule (antivirus software) |
Supports more than 600 types of anti-virus software from about 140 companies (including each version). It is possible to check the operating status and definition file status, and forcibly update the definition file depending on the software. |
| predefined rule (personal firewall) |
It is possible to check the operation status of personal firewall products from about 100 companies and more than 500 types (including each version). |
| predefined rule (anti-spyware) |
It is possible to check the operation status of about 120 companies' anti-spyware products and more than 800 types (including each version). |
| predefined rule (OS, service pack) |
Client OS and Service Package can be checked |
| Hard disk encryption check | Check whether the hard disk of the terminal of the connection source is encrypted |
| computer certificate check | Host Checker can check even if the computer certificate is installed on the terminal itself instead of importing the certificate into a normal browser. |
| MAC address check | Check the MAC address active on the device |
| custom rule (port) |
Check if a specific port is free on your device |
| custom rule (File) |
Check the existence of the specified file, file version, update date, MD5 hash value, etc. |
| custom rule (process) |
Check if a specific process is running |
| custom rule (registry) |
It is possible to check the existence and value of the Windows registry |
| NetBIOS name check | Check Windows machine name |