Specifications/Technical Information
Specifications/Technical Information
solution
solution
- Pulse Secure Manga, Secure Access Story - Zero Trust/SSL-VPN/Remote Access Solutions
- Pulse Secure Secure Access Story through Manga - Episode 1 Remote Work
- Pulse Secure Secure Access Story through Manga - Episode 2 MDM Introduction
- Pulse Secure Secure Access Story through Manga - Episode 3 Ransomware Countermeasures
- Pulse Secure Secure Access Story Learned from Manga - Episode 4 University Information System
- Connect Secure Series Solutions - Zero Trust/SSL-VPN/Remote Access Solutions
- Connect Secure Series Solutions - PulseSecure SDP for Zero Trust Model

Pulse Secure
pulse secure
Important [Regarding Vulnerability Fix Version]
A vulnerability affecting Pulse Secure products has been confirmed. For each vulnerability, countermeasures have already been implemented depending on the specific version, so please be sure to upgrade to the vulnerability fixed version.
Click here for details
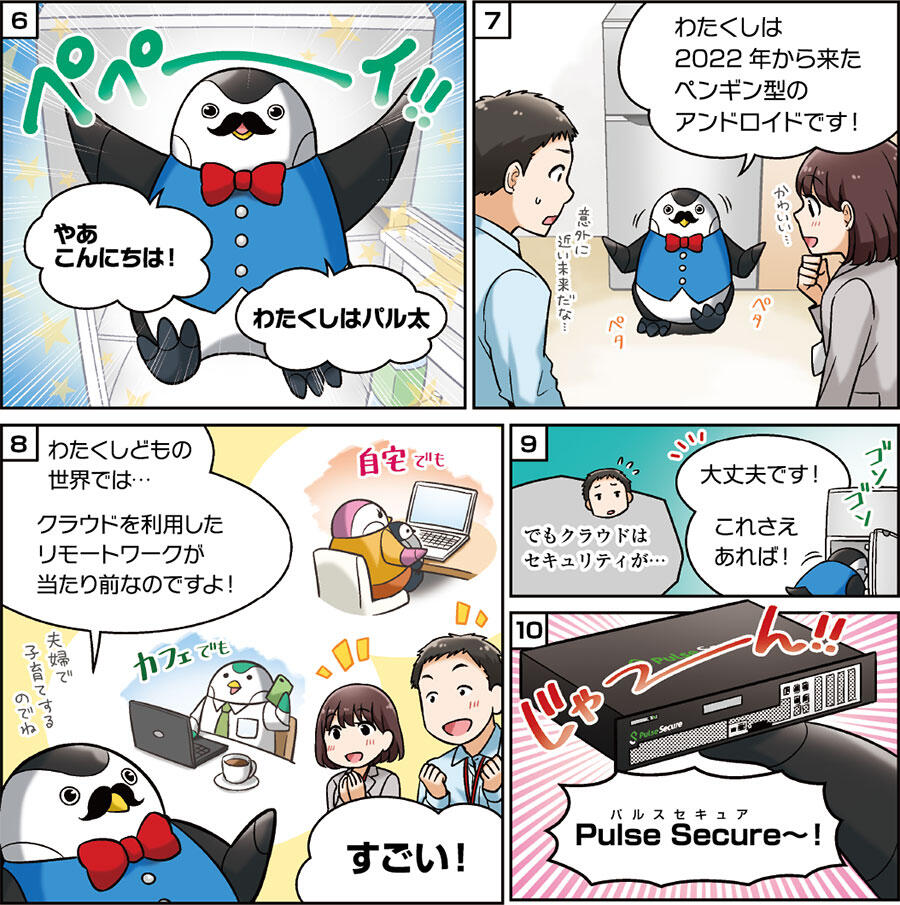
Episode 1 Remote work
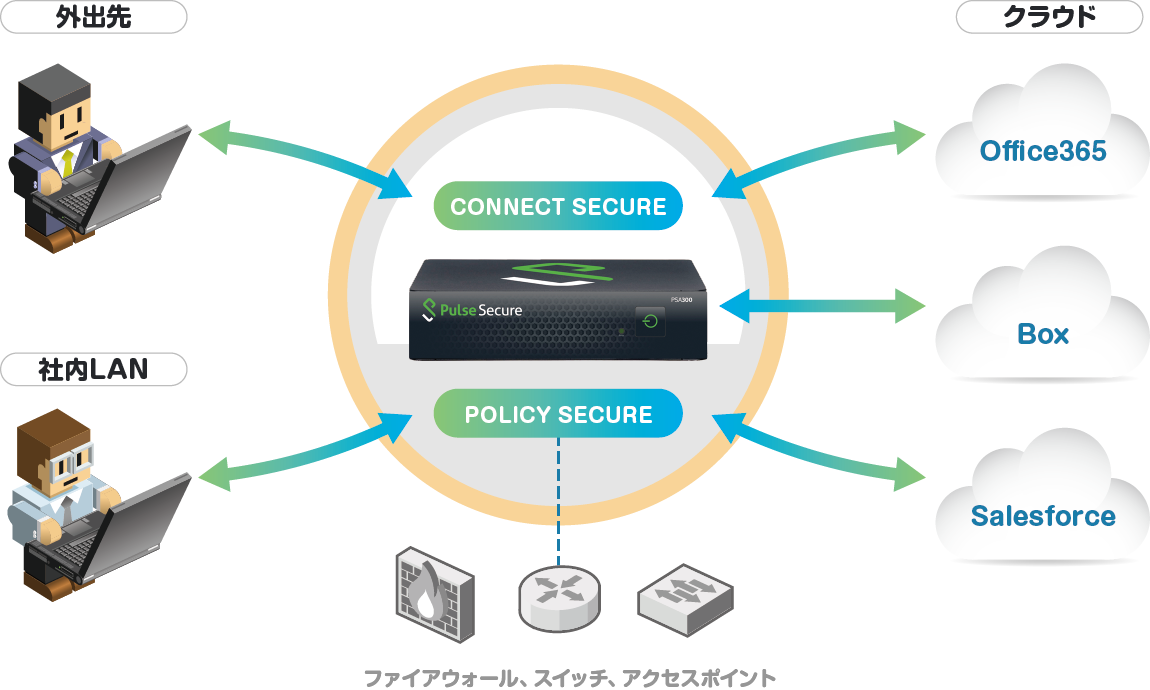
Pulse Secure centrally authenticates to cloud services for single sign-on
Solution brief
- Pulse Secure acts as SP or idP
- Integrates with the cloud via SAML. When the cloud receives a login request from a user, the cloud and Pulse Secure authenticate
- Check device security status by matching users against Active Directory. Subsequent traffic is sent and received directly between users and the cloud
Three Features of Pulse Secure
- More secure access to the cloud
In addition to certificates and ID/passwords, it is possible to check the health of the terminal (anti-virus software is running, the OS Ver is up to date, etc.) and then allow access only to healthy terminals. - Enables SSO for multiple cloud services with a single authentication
Enable SSO for any cloud service that supports SAML such as Exchange Online, Office 365, Salesforce, Box, Concur, etc. - Suppress bandwidth pressure in the internal environment
After being authenticated by Pulse Secure, remote access users can access cloud services directly without going through the company in a secure state. In-house bandwidth compression suppression achieved