Google Cloud
Google Cloud
SIEM that uses AI to reduce operational burden
Do you have a problem like this?
- The quality of operations is unstable due to differences in response depending on the operator's experience.
- Too many detection alerts
- It is difficult to check security logs and consider how to respond.
- There is a lot of personnel turnover, and training security personnel is difficult.
- Learn the tool commands required for SIEM operation
- Learn security terminology and attacker information
- SIEM operation is complicated due to the need to use multiple products
- Operation of multiple products from log collection to response
Google Security Operations: Easy-to-use next-generation SIEM
In response to cyber attacks that are becoming more sophisticated every day, there are many cases where multiple products such as SIEM, SOAR, and ITSM are used. As a result, security operations inevitably require knowledge and experience, making it difficult to secure highly skilled security personnel.
Google Security Operations contributes to the efficiency and sophistication of security operations by utilizing Gemini (AI).
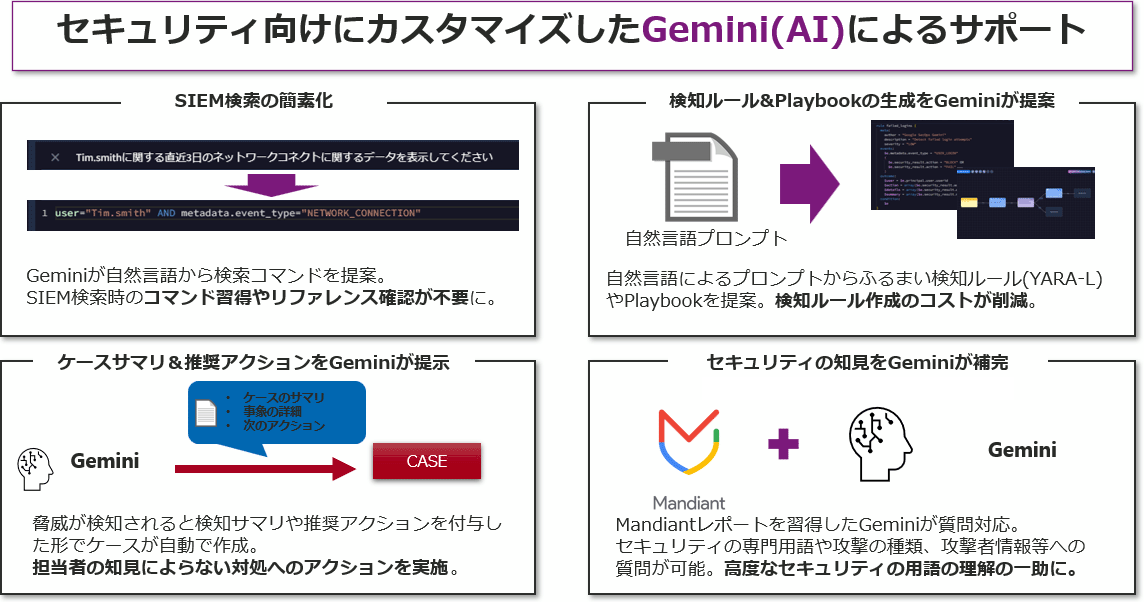
[Point 1] Simplifying SIEM searches
Gemini suggests search commands using natural language.
This helps reduce the burden on operations personnel as it eliminates the need to learn commands or check references when searching SIEM.
[Point 2] Make the most of Google Threat Intelligence security insights (Mandiant/Virustotal)
Threat detection rules operated by Google Cloud's security team are automatically applied to SIEM detection rules. By leveraging the comprehensive threat intelligence of Google Threat Intelligence, you can operate your SIEM using the latest threat detection rules.
[Point 3] Gemini complements security knowledge and supports the creation of investigation results reports and the implementation of countermeasures
Gemini provides comprehensive information on attackers, including an overview of targeted attacks, past activity, malware, countermeasure rules, TTPs, and IOCs, and supports the creation of investigation results reports and the implementation of countermeasures.
Seminar
これから開催 開催終了 {{ item.title }}
{{ item.seminar_start_date__display_1 }} {{ item.seminar_place__display_1 }}
video on demand
Inquiry/Document request
Macnica Google Cloud
- TEL:045-476-2010
- E-mail:google-sales@reseller.macnica.co.jp
Weekdays: 9:00-17:00