Island
island
How to prevent information leaks by outsourcing companies? ~Introducing a new approach using an enterprise browser~
Introduction
Are you aware of security in supply chains and outsourcing companies?
According to the Ministry of Economy, Trade and Industry's "Cybersecurity Management Guidelines," "In order to fulfill our responsibility for ensuring cybersecurity, we must implement cybersecurity measures not only for our own company but also for the entire supply chain, including domestic and overseas bases, business partners and subcontractors. It is written that it is necessary to take care of the Nowadays, it is required not only to strengthen security measures of the company, but also to strengthen security measures including the supply chain.
table of contents
1. Do you have such a situation?
2. Challenges in contractor management
2-1. Transactions with multiple companies
2-2. Difficulty in distinguishing between work and private life
2-3. Governance Issues
2-4. Balancing Security and Convenience
2-5. Lack of Last Mile Visibility and Control
3. Conventional countermeasure method
3-1. VPN
3-2. For VDI
4. What is the new countermeasure "enterprise browser"?
4-1. Differences from conventional browsers
4-2. Manage subcontractors using an enterprise browser
4-3. Subcontractor = Apply your company's security requirements without interfering too much with other companies
1. Do you have such a situation?
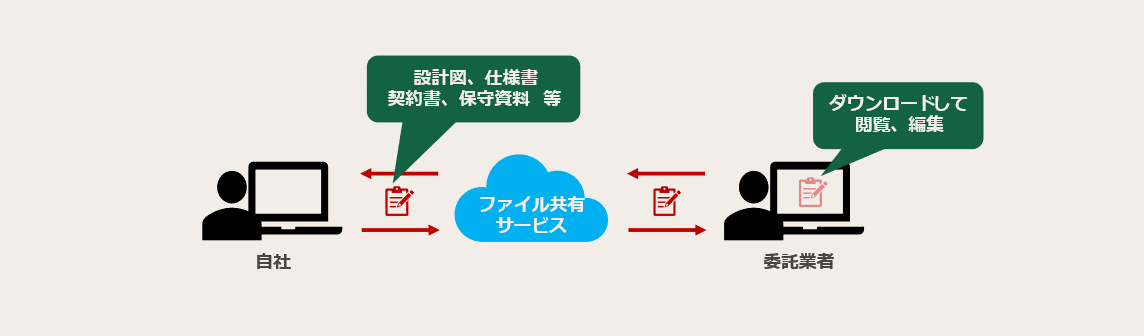
Have you ever used a file-sharing service to share some kind of document with a subcontractor? Depending on the company, there may be cases where a paid contract is used for a specific service, but there may be cases where some departments or individuals use free services.
In the above case, it is necessary to visualize the usage status of file sharing services in the first place, and take measures such as preventing the use of services that are not officially approved by the company. Isn't there a lot of companies that have it?
In order to develop such an environment, it is necessary to implement measures to secure access from contractors and a mechanism to monitor the movement of data on their terminals.
2. Challenges in contractor management
Even if you want to implement the measures mentioned above, the contractor is just another company, and there are various issues to control in-house.
2-1. Transactions with multiple companies
Outsourcers often work with multiple companies, may use multiple VPNs, and may have mixed data. Also, you may have tools from multiple companies with different requirements on a single PC, or you may not want to have multiple Agents installed. It is also important to be able to visualize and control the access and operation of contractors as much as possible when doing business with your company on terminals in such an environment.
2-2. Difficulty in distinguishing between work and private life
There may be cases where one PC is shared between personal and work. Even if it's not as much as BYOD, it is necessary to respect privacy when using a business terminal that uses the Internet in a nearly private manner, or when accessing or operating other than business with your company in the first place.
However, if any confidential data downloaded from the web application that the outsourcer communicates with the company can be stored on their PC, and if it can be edited and manipulated freely, it can be a security risk, so the outsourcer is also accepted. We need tools that allow us to visualize and control to the extent we need with such an approach.
2-3. Governance Issues
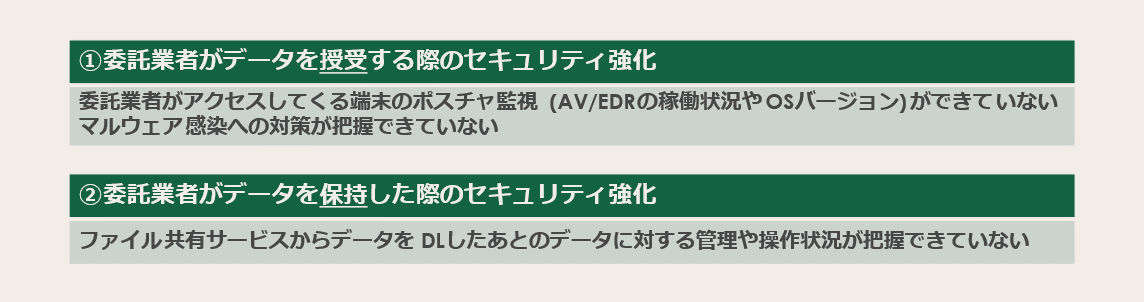
Policy management is driven by user identity and device type is often not considered. Even if an authorized user accesses the site, if the device being used is vulnerable, it becomes a security risk, so device status monitoring (device posture monitoring) is important.
Organizations can also apply role-based access controls to restrict access to different apps, but they may not have adequate policy controls for their high turnover contractors. By setting and controlling the application of policies in more detail for actions (data operation history, etc.) after granting access to an application, security is enhanced while allowing flexible work without sacrificing convenience. That's what's important.
2-4. Balancing Security and Convenience
Data redaction for critical pieces may require application code changes or complex tokenization.
Don't you think about the security of external access and enable excessive security functions that impair convenience, or, conversely, do you disable the originally necessary security functions to prioritize convenience?
2-5. Lack of Last Mile Visibility and Control
The last mile here refers to the "browser", the first and last point at which data can be exfiltrated from a web application. For example, there is no way to prevent contractors from accessing web applications shared with your company and copying and pasting sensitive information or taking screenshots. This is one of the important measures from the viewpoint of data protection in contractor management.
3. Conventional countermeasure method
3-1. VPN
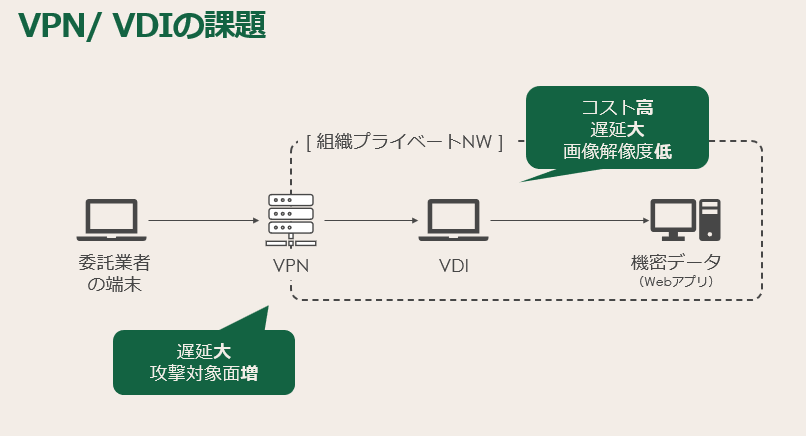
One traditional countermeasure is to provide the outsourcer with a virtual private network (VPN) client to access the environment. This way, you can control your merchant traffic and what you touch.
However, since you will be accessing websites and web applications frequently by connecting to the VPN, business will be affected by communication delays due to multi-stage access, and additional costs will be incurred due to the strain on the line due to the increase in access. may be affected.
In addition, VPNs themselves increase the attack surface where network resources can be accessed.
3-2. For VDI
The second traditional mitigation approach is to provide virtual desktop infrastructure (VDI) to outsourcers. In this scenario, the contractor is given his or her own virtual PC, which launches and uses a web browser as soon as they log into the OS.
However, in general, VDI takes a long time to start up, has access delays, and has low screen resolution, so there are many cases where users feel work stress.
Additionally, VDI is very expensive, which is a challenge for IT administrators.
4. What is the new countermeasure "enterprise browser"?
Introducing a new approach to secure contractor access and data control "on the browser", traditionally done with VPN or VDI.
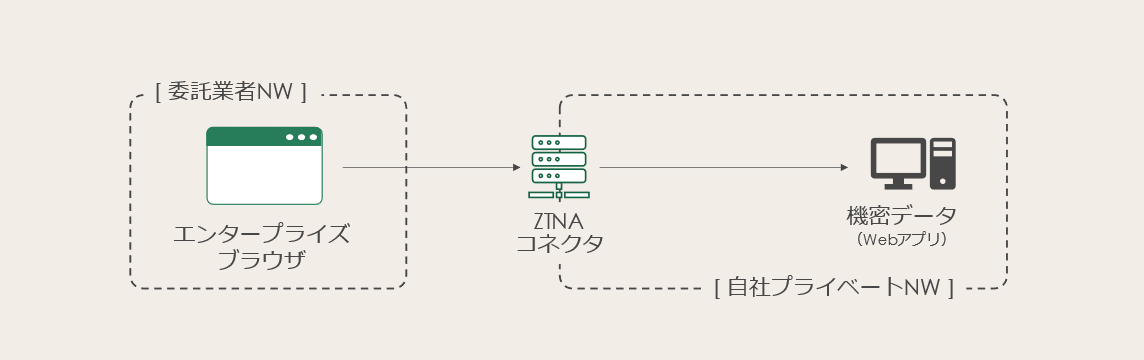
4-1. Differences from conventional browsers
What browser do you use at work?
Google Chrome, Microsoft Edge, etc. I think that many people use the same browsers that they use privately. Since these browsers are consumer browsers, they are not very conscious of the security features required for business use by enterprises.
However, if you use a browser to access file sharing services, and if you also browse and edit on the browser, the browser itself will check the device status at the time of access, monitor data operations, and control how it is handled. One of the best approaches is to use an "enterprise browser" where you can.
4-2. Manage subcontractors using an enterprise browser
Enterprise browsers allow you to:
- Checking whether the device of the outsourcer accessing the file sharing service is healthy (device posture)
- Is EDR up and running? Is the asset management tool process running? Is the OS the recommended version? etc - Allowing contractors to view and edit data without downloading it locally (in-browser storage)
-DL to local increases the risk of information leakage. It is important to have a mechanism that does not output from the browser as much as possible. - Control copy-paste and screenshots from transfer data to the outside, monitor actions such as keystrokes and mouse transitions (last mile control)
-It is possible to monitor and control the rendering information itself, which is invisible on the communication
4-3. Subcontractor = Apply your company's security requirements without interfering too much with other companies
Contractors are important business partners, but they are still other companies. Many companies must be faced with the dilemma that they have an obligation to ensure security, but cannot interfere excessively.
Such problems can be solved with an enterprise browser.
- All you need is a browser installation. no agent required
- Usage is the same as the conventional browser! No work stress for contractors due to tool changes
- Protect your privacy by using different browsers. If you use the enterprise browser only when doing business with your company, there is no need to interfere with other browser operations
in conclusion
Accelerating global business and expanding supply chains have made contractors more important than ever. However, there are limits to conventional methods for safe data exchange and data protection during these external collaborations, so a new approach suitable for the current environment is required.
Reduce complexity, lower costs, deploy faster, and protect critical data while protecting the privacy of everyone involved by bringing enterprise browsers to the challenges of contractor access and data transfer. can.
Inquiry/Document request
Macnica Island, Inc.
- TEL:045-476-2010
- E-mail:Island-sales-i@macnica.co.jp
Weekdays: 9:00-17:00