
Full IT support service
Full IT support service
A dedicated engineer explains the importance of identity protection for small and medium-sized businesses

point
- 1. Cloud Migration and AD Management Challenges
- Many SMEs are migrating to the cloud, but security risks are on the rise
- Lack of AD management engineers and operational risks cause business interruptions
- 2. The Need for Zero Trust Security
- The zero trust model, which verifies all access, is gaining attention
- Identity management and protection are key to zero trust security
- 3. Effectiveness of "Marugoto ID Security"
- "Marugoto ID Security," specializing in ID management, provides cloud-based solutions
- Specialized engineers will take over operations, reducing the burden and enhancing security
table of contents
- 1. Changes and challenges in the modern IT environment
- 2. Dedicated engineers explain the importance of ID protection for small and medium-sized enterprises
- 3. Summary
1. Changes and challenges in the modern IT environment
Digital transformation has become mainstream in companies, and cloud technology is being rapidly adopted, making security measures increasingly important. However, the issue of being unable to respond to new security risks while still relying on traditional on-premise systems has emerged. In particular, small and medium-sized enterprises, with limited resources, are finding security management to be a heavy burden.
In addition, many companies use Active Directory (AD) as the authentication infrastructure for their systems. AD is an important tool for centralizing user and computer management and providing authentication, but if it is not managed properly, it will increase security risks. In particular, many companies are troubled by the risks arising from a shortage of engineers and inadequate operational management. In addition, there are some aspects of the concept of "zero trust security (zero tra)" that has been attracting attention recently that AD cannot fully address, so many companies are unsure how to achieve zero trust. Zero trust security is a security model that verifies all access inside and outside the network and treats it as untrusted, and it is important to design and build an appropriate environment to adapt to it.
Against this background, we interviewed a Macnica engineer to find out more about how Macnica 's "Marugoto ID Security" helps to address the security challenges of small and medium-sized enterprises, and why it is necessary.
2. Dedicated Engineer Explains the Importance of ID Protection for Small and Medium-Sized Enterprises
interviewer:
First, please tell us about the challenges that medium-sized and small businesses face due to changes in the modern IT environment.
Engineer Kawaguchi:
Many small and medium-sized enterprises are currently migrating to the cloud. This migration has improved business flexibility and efficiency, but at the same time it has also created new security risks. In particular, many companies have issues with the operation and management of authentication infrastructure that relies on the traditional AD (Active Directory). There is a risk of business interruption due to a shortage of engineers and insufficient risk management in the event of AD outages. In addition, AD is an authentication infrastructure for on-premise systems and cannot be used to authenticate cloud systems, so support for cloud system authentication is also insufficient.
interviewer:
What are some of the specific risks and challenges associated with AD?
Engineer Kawaguchi:
If AD stops, access to all related systems will be impossible, and the entire business may be interrupted. In addition, small and medium-sized enterprises with poor operational management are often unable to respond to security threats and are unable to respond quickly when incidents occur. In such situations, security measures are urgently needed to continue business activities. As mentioned above, AD does not support authentication for cloud systems, so strengthening authentication for cloud systems tends to be neglected. As a result, the risk of unauthorized access to cloud systems increases.
interviewer:
As part of their security measures, many companies are interested in "zero trust security (zero trust)." What are your thoughts on the concept of zero trust?
Engineer Kawaguchi:
Unlike the traditional perimeter security model, zero trust security is based on the idea of always verifying all access. This is an important model for strengthening security without trusting either inside or outside the network. By shifting to this way of thinking, the security level of the entire company can be dramatically improved. In the zero trust concept that eliminates the network boundary, from the perspective of an attacker, it is often possible to gain unauthorized access to a system by compromising an ID, so protecting IDs is particularly important.
interviewer:
With many companies considering implementing zero trust security, how exactly are you providing support for them?
Engineer Kawaguchi:
To introduce zero trust security, it is necessary to consider what kind of security design to use and what solution to use, as well as build the environment and operate it. Macnica provides optimal design for zero trust security and takes on the entire process from building the environment to operation. This is based on the knowledge Macnica has gained while proposing zero trust security to many customers. This service enables customers to arrive at the optimal solution for zero trust security in the shortest possible time.
interviewer:
With such support being so important, how do you feel about the need for full identity security?
Engineer Kawaguchi:
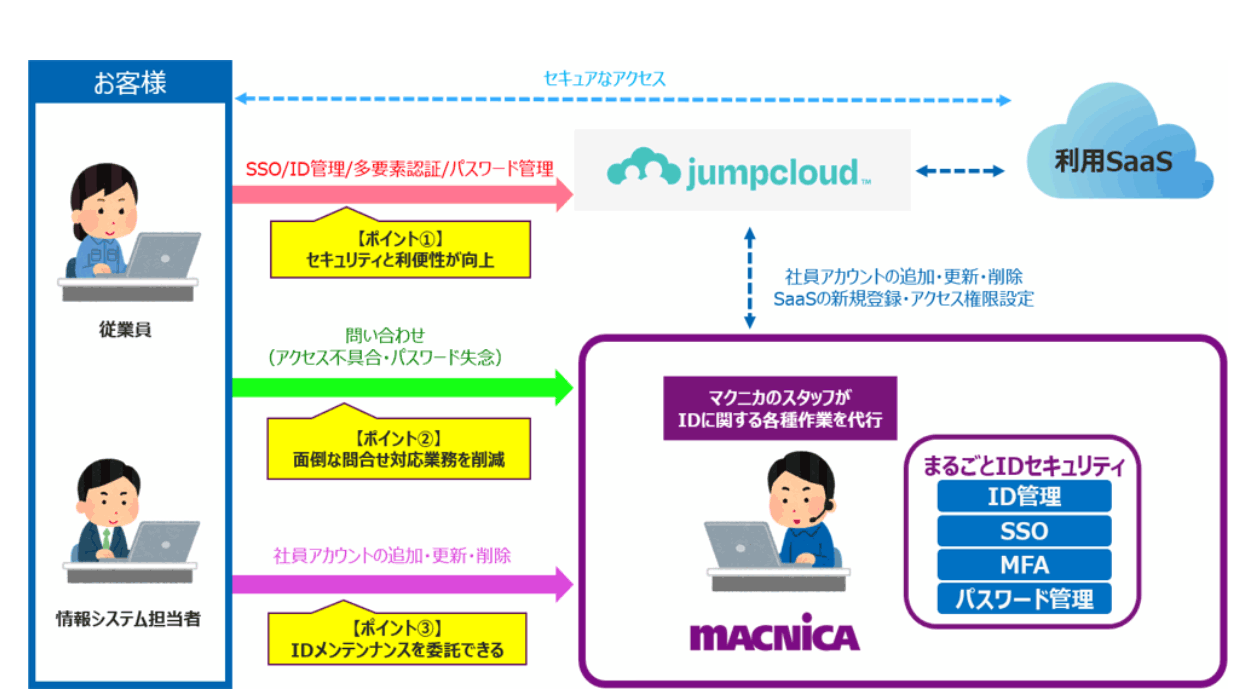
Marugoto ID Security is a service that specializes in IDs within the Zero Trust Security. As mentioned above, proper design of ID management is important in a Zero Trust environment. In addition, we believe that building and operating an ID management solution is a high hurdle for customers, so we will handle the building and operation within this service. This service provides a cloud-based ID management solution, reducing the dependency on AD in the customer's environment and realizing an environment that is more in line with the concept of Zero Trust.
interviewer:
What kind of support do you provide specifically?
Engineer Kawaguchi:
Our scope covers ID management and authentication for cloud systems, and we design, build and operate a cloud-based ID management infrastructure to suit your environment. In the design stage, we provide optimal solutions for ID management in zero trust. In the construction stage, we also integrate with the cloud systems used by our customers. In the operation stage, we provide a help desk for end users, handling tasks such as changing and abolishing IDs when employees join or leave the company. This allows us to achieve optimal ID management in zero trust without placing a burden on our customers.
interviewer:
Please share any feedback or success stories you have received from customers.
Engineer Kawaguchi:
One small and medium-sized enterprise had a problem where ID management work had become mundane, and ID management work would stop when the person in charge was on vacation. At the same time, as the number of cloud systems used increased, security concerns arose because logging into the cloud systems only required a simple ID/PW. After introducing Marugoto ID Security, the mundane nature of ID management work was resolved, and security was strengthened by using multi-factor authentication to log into cloud systems. The customer commented, "We were able to take the first step toward optimal zero trust."
interviewer:
Finally, do you have any message for companies considering using this service?
Engineer Kawaguchi:
To keep up with the rapid changes in the IT environment, you need a reliable partner. At Marugoto ID Security, our experts will provide full support to help small and medium-sized businesses carry out their work with peace of mind. Please feel free to contact us with any inquiries, no matter how trivial. Let's solve your problems together.
3. Summary
Marugoto ID Security is an ideal solution to resolve the issues that small and medium-sized enterprises face when implementing cloud-based ID management and zero trust security. By having specialized engineers handle operations on your behalf, we provide an environment in which companies can safely transition to the cloud and implement new security measures.
If you would like to consult with Macnica, please contact us through the Company website. Our dedicated engineers will propose the optimal solution based on your needs and help you create an environment where you can concentrate on your work with peace of mind.
Dedicated Engineer Profile

Macnica, Inc.
Security 3rd Business Division, 3rd Technology Department, 2nd Section
Koji Kawaguchi
\Related Content/
We have a variety of content for IT personnel at small and medium-sized enterprises!
Inquiry/Document request
Macnica IT Support Services
- TEL:045-476-2010
- E-mail:digital-it-sales@macnica.co.jp
Weekdays: 9:00-17:00
