
Axonius
Axonius
Integrated threat exposure management for various environments – CAASM tools
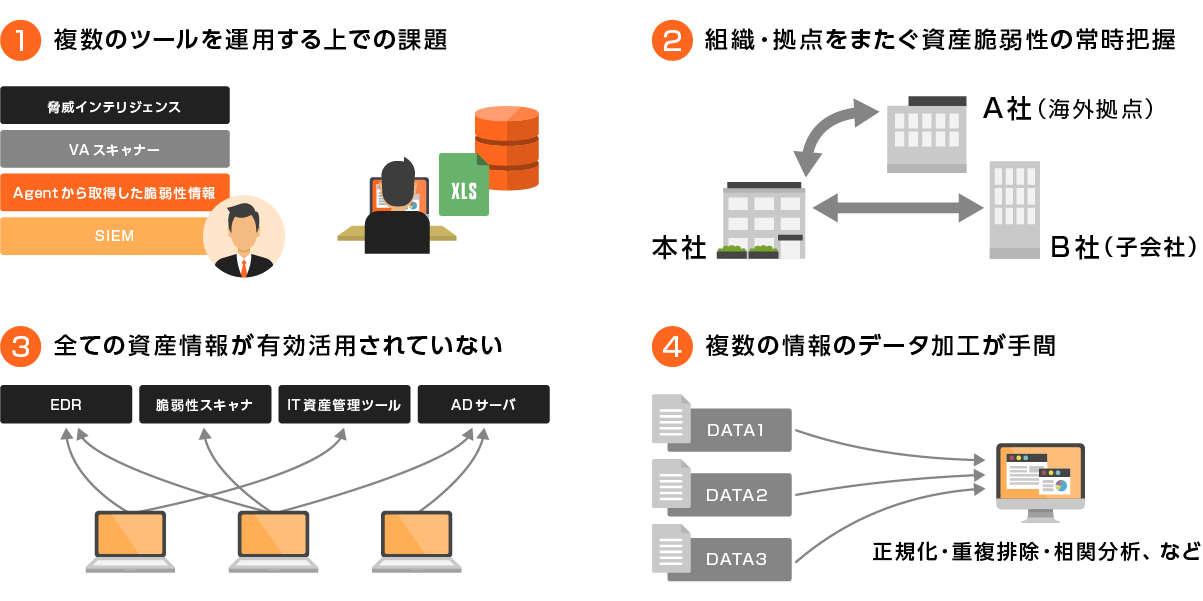
Do you have a problem like this?
- We have contracts for multiple products with similar functions for different purposes, and we can't keep up with managing them.
- Each department and location uses its own tools, making it impossible to keep track of company assets at all times.
- It is not clear which tools are included in which assets. Asset information is not being used effectively.
- It takes time to process data when managing multiple pieces of information in an integrated manner.
- We want to achieve cyber hygiene and reduce security operation man-hours.
Features of the CAASM tool, Axonius
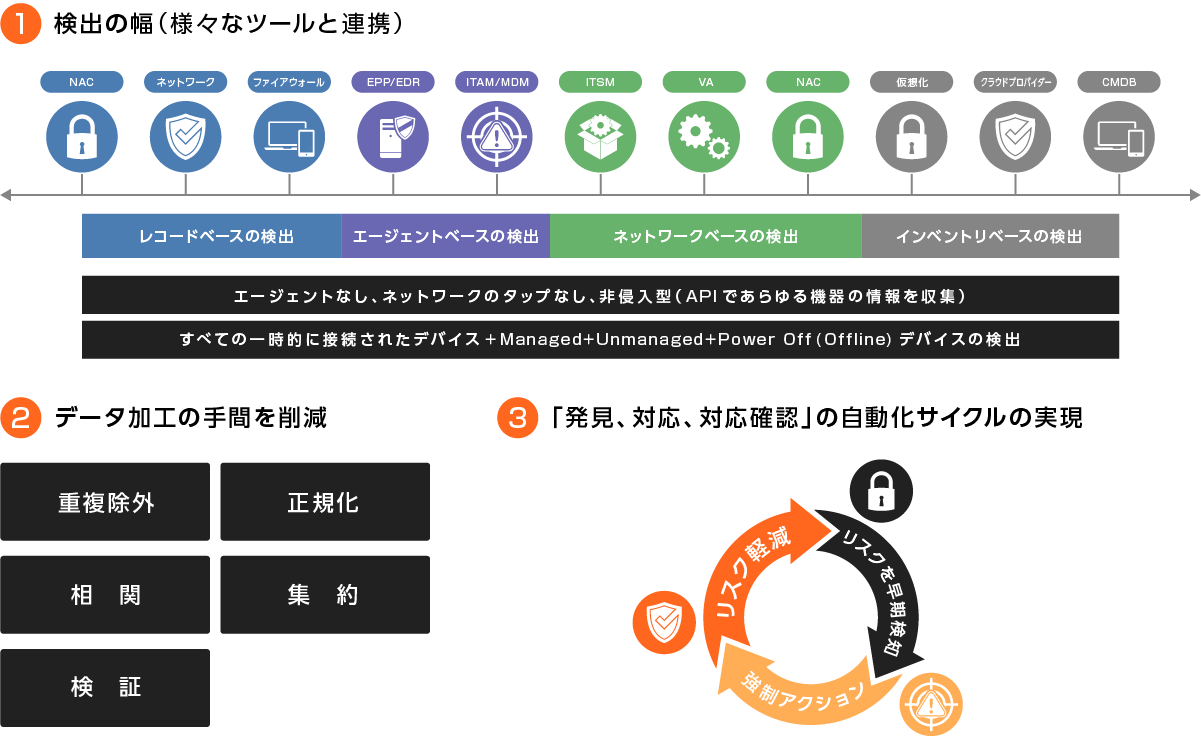
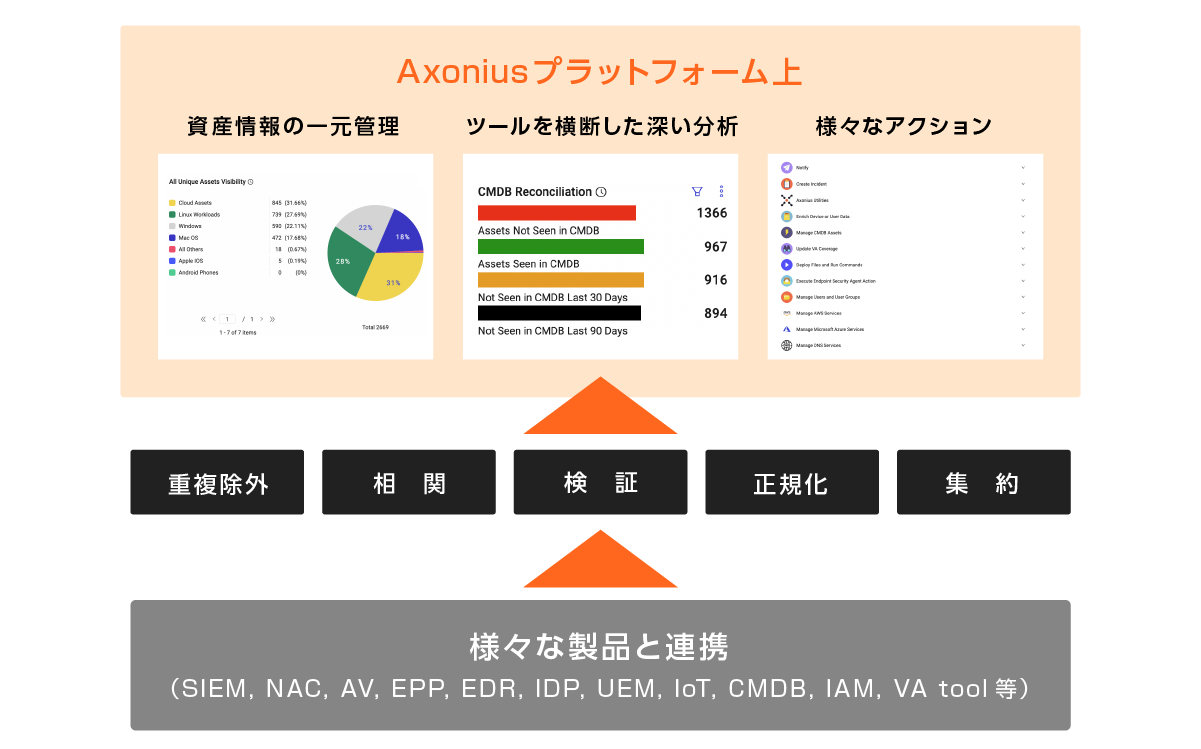
Axonius is a tool that integrates asset/vulnerability information management by linking with each tool through API. It aggregates information from agent-type security tools such as EDR and antivirus software, vulnerability scanner tools, network devices such as DNS, FW, switches, and Network Access Control, IT asset management tools such as CMDB, IoT device management tools, manual management information such as CVS, ticket management systems, cloud environments, and user and device information from Active Directory.
As a result, we will not only be able to determine CVSS (Common Vulnerability Scoring System) scores, but will also be able to implement security operations in line with the importance of your company's assets and help discover rogue devices that are not registered in the asset management ledger.
CAASM (Cyber Asset Attack Surface Management) is an approach to visualizing all IT assets owned by a company (on-premise, cloud, SaaS, etc.) and identifying and mitigating security risks. In today's network environment, the spread of cloud and SaaS means that IT assets are distributed across multiple environments and managed by a variety of IT management and security tools. This results in information being fragmented across each tool, making it difficult for security teams to accurately grasp "what needs to be protected." CAASM visualizes "invisible risks" by linking with each tool and aggregating information.
*For a list of Axonius compatible tools, please see https://www.axonius.com/adapters
An overwhelming number of solution collaborations
It can be linked to over 1,200 tools. Information can be obtained by setting authentication information for logging in to the API or admin screen.
Highly accurate data matching and deduplication
Automatically matching and normalizing data aggregated from each tool enables highly accurate asset inventory management.
Identifying security gaps and managing risks
It analyzes and visualizes "devices without antivirus installed" and "unmanaged cloud accounts."
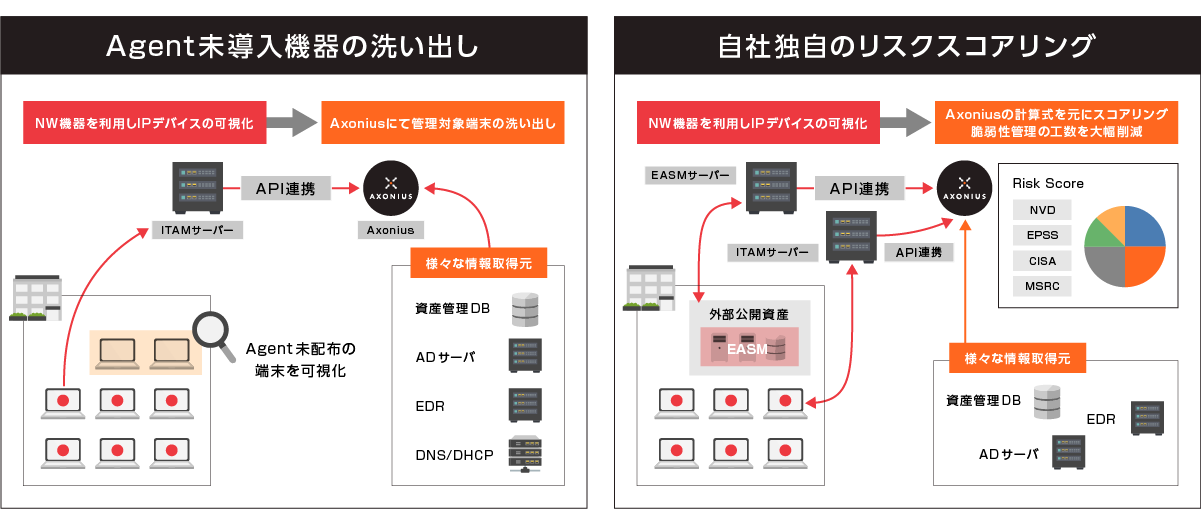
Usage example
- Discover assets where IT management/security products (agents, etc.) are not deployed correctly
- Example: I want to visualize how many of the assets with IP addresses assigned by DHCP from the company's DNS server do not have an agent installed.
- Define and operate a “company-specific risk score”
- Example: In addition to vulnerability information (CVE, CVSS, CISA-KEV, etc.) that the IT assets themselves have, we would like to manage risk by taking into account the importance of the assets, the implementation status of standard security tools, and the results of validation of vulnerability scanners.
video on demand
company description
| company name | Axonius |
|---|---|
| Established | 2017 |
| location | New York, New York, United States |
| representative | Dean Sysman |
| website | https://www.axonius.com/ |
Inquiry/Document request
In charge of Macnica Axonius Co., Ltd.
- TEL:045-476-2010
- E-mail:axonius-sales@macnica.co.jp
Weekdays: 9:00-17:00


