
In 2023, approximately three years have passed since 5G (5th generation mobile communication system) began to be rolled out in Japan. Along with 5G, there is a technology that is attracting a lot of attention as it will revolutionize the communications industry.
That is ``Open RAN,'' which makes the specifications of radio access networks (RAN) open. In the telecommunications industry, which is expected to continue to grow significantly in the future, there is no doubt that knowledge regarding this technology will be one of the key indicators for telecommunications carriers and telecommunications equipment vendors to achieve further growth.
Therefore, this time, we will deliver an explanation of Open RAN by Katsuya Hino and Seishi Tsukada, two members of the Consulting Division, Security Consulting Department, Macnica DX Consulting Division. .
This article is divided into two parts: the [Security] section explains things to be careful about in terms of Open RAN security, and the [Summary] mainly explains the basics of Open RAN. Masu.
First, learn the basics with “Open RAN Security Report”
--How can I learn more about security, which is important even in Open RAN?
Hino: As a first step, I recommend reading the Open RAN Security Report. This is a report published by QUAD (a coalition of Japan, the United States, Australia, and India) in May 2023, and as the name suggests, it describes Open RAN security in detail and in an easy-to-understand manner.
Regarding security, 13 basic Open RAN Alliance security specifications have been published (as of November 2023) and are updated every three months. Furthermore, with many guidelines and white papers published by multiple organizations, there was a concern that users would end up in a situation where they did not know what to look at. Therefore, QUAD has aggregated and organized the latest information from each document in the Open RAN Security Report.
There are three main elements in the report. The first is an analysis of security issues, which separates issues specific to Open RAN and issues common to existing RAN. The second is the verification results using actual equipment, which was conducted in accordance with the Open RAN Alliance security specifications. The third one organizes the security checklists that were scattered across each document.
Tsukada: I would like to add some additional information to the first point, ``Analysis of security issues.'' In fact, there are groups that do not want Open RAN to spread quickly, and their voices are being raised from that perspective. This is because existing vendors and related parties have the advantage of locking in customers by having them continue to use their own all-in-one wireless base stations. However, claiming that ``openness is undesirable'' is often not accepted by others, so we present warning messages and use cases such as ``openness may have security concerns.'' doing.
In addition, several countries have published reports pointing to security concerns regarding Open RAN. It is unclear whether these reports are intended to support or protect domestic vendors, but they come from institutions with some credibility and influence. As a result, vendors are using these reports to reach out to mobile carriers and say, ``There are risks to openness, and an initial all-in-one approach will solve the problem.'' Trying to avoid such influence from specific vendors can be said to be one of the major challenges for QUAD.
With this background in mind, the Open RAN Security Report presents an analysis that shows that many security-related concerns are not caused by openness. We discuss the latent security issues that existed with all-in-one wireless base stations that have become apparent due to openness, as well as new concerns that have arisen with Open RAN.
The report states, ``Opening will make necessary security measures clearer,'' and refers to the security specifications, issues, and countermeasures defined by the O-RAN Alliance. In this context, security is not a traditional "black Box," but rather the intention is to improve safety through transparency. This is an important point to convey to users.

Six categories of Open RAN security
--What security issues does Open RAN actually pose?
Tsukada: The report describes potential security challenges for Open RAN in six categories. This time we will introduce each category.
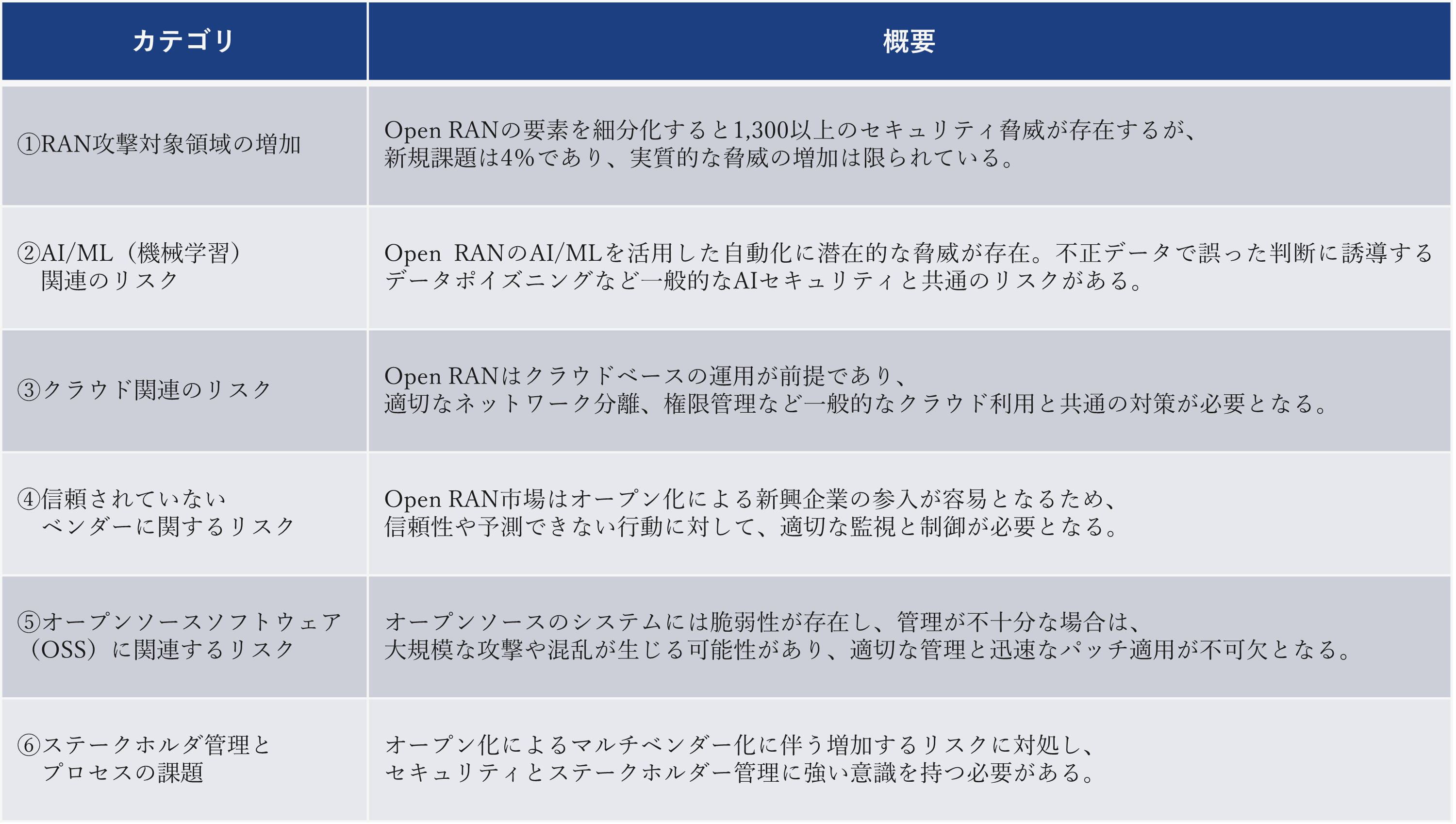
▲Open RAN security issues.
① Increase in RAN attack target area
Tsukada: The report analyzes that if you subdivide the elements that make up an Open RAN base station, there are over 1,300 security threats to the components and interfaces. This exposes a significant and large attack surface to attackers. However, the components / interfaces have been around for a long time, and only 4 % of the challenges are new and unique to Open RAN. Even as Open RAN becomes more widespread, the actual threats have not increased that much.

②AI/ML related risks
Tsukada: Security related to AI and ML (machine learning) is currently the hottest topic, and it is also attracting attention in the field of Open RAN, where AI is expected to play an active role in the future. For example, by using AI/ML, operations such as how to allocate resources to base stations and which traffic should be prioritized can be automated using new interfaces and AI.
On the other hand, there is a concern that by making the interface open, the control program may be hijacked by malicious parties. Data poisoning can also occur, where an attacker disrupts the control process by feeding false data. To address these risks, efforts are being made to create systems to authenticate applications and monitor data. These challenges are not unique to Open RAN and are of common concern in the general AI security context.
Hino: Regarding AI/ML, Open RAN is more advanced than conventional wireless base stations, and it is also a technology that will make it easier to introduce. In this sense, it is essential that Open RAN takes the lead in areas including security.

③Cloud-related risks
Tsukada: Currently, in the IT world, many systems are operated on the cloud. This trend has spread to telecom, with Open RAN premised on cloud-based operations. Cloud operating models can be divided into two. One is a private cloud, where the company owns its own cloud infrastructure. The second type is public cloud, which provides cloud resources from outside.
A common concern with these operating models is when the cloud is used by multiple organizations. If your security settings are incorrect, even if your company has implemented its own security measures, it may be attacked through other organizations, and vice versa. Proper network isolation is essential to prevent these problems.
Additionally, when cloud-native applications are used on the cloud, images such as virtual machines and containers may be replaced. It is also important to properly manage permission settings, such as who can deploy from storage to a shared environment.

④Risks related to untrusted vendors
Tsukada: As multi-vendoring progresses, it becomes necessary to appropriately manage the reliability of each vendor as part of the supply chain. For example, when introducing new components like AI, you're more likely to work with vendors with non-traditional characteristics. The field of Open RAN requires high-level security requirements, but many AI-related vendors are expected to have new approaches that are not bound by the constraints of traditional communication base stations. Therefore, new development and operation methods are required to accept their different perspectives and approaches, integrate them appropriately, and ensure security.
Additionally, since Open RAN is still in its development stage, it is easy for venture companies and start-ups to enter the market. While this low barrier to entry provides flexibility, it also comes with uncertainty, as it is difficult to predict who will enter the market. Additionally, although the Open RAN specifications specify the functions of components, there may not be sufficiently clear regulations regarding what they should not do. Therefore, as AI vendors enter the market, it is important to remain cautious about their reliability and unpredictable behavior, and to ensure appropriate monitoring and control.

⑤ Risks related to open source software (OSS)
Tsukada: As is widely recognized, open sources contain various vulnerabilities and bugs, and these can also be potential threats. As an example, an open source module for logging is widely used as a useful tool, but a few years ago a vulnerability was discovered in that module, leading to a large-scale attack by attackers, and There have been cases where the system has been thrown into chaos.
The above problem is also due to the fact that many companies do not properly understand the open source software included in their systems. In Open RAN, the supply chain includes vendors in the position of secondary and tertiary contractors, making module management complex. As a result, even information such as whether module replacement is allowed and who is responsible may become unclear. Open source has many benefits, but it is essential to have a system that can properly manage these and quickly apply patches when problems occur.

⑥ Stakeholder management and process issues
Tsukada: Conventional wireless base stations were generally managed centrally by a specific vendor. However, in the future, openness will increase the possibility that system integrators and other players will enter the market. Therefore, mobile carriers must consider the process of how to manage and coordinate these players.
A few years ago, a mobile carrier introduced a system from overseas, but during the operation process the system could not be authenticated and service was interrupted. While in this case the vendor who manages and operates the system is considered to be at fault, many people seem to have placed the responsibility on the mobile carrier providing the service.
In conjunction with the previous content, it is certain that potential risks will increase as Open RAN becomes more widespread and multivendors become more common. Mobile carriers who manage and operate wireless base stations will need to be more aware of security and stakeholder management than ever before and take measures.

--We've heard a lot of things so far, but what should we do first to start working on Open RAN?
Hino: I recommend that you pick up the Open RAN Security Report, which is extremely useful for understanding the overview of Open RAN. However, I think there are some parts that are difficult to understand even if you look at each item individually. In such cases, it is important to check with the mobile carrier or vendor that your company is considering as a partner.
Tsukada: In Open RAN, there are situations where mobile carriers ultimately have to take full responsibility. Therefore, the starting point is to read the Open RAN Security Report, which serves as a guideline, and understand the measures your company should take. It is important to consider that the level of risk will vary depending on the functions and scale of the system being introduced, but it is important to understand these details in advance so that you can prepare for the right start.
--What kind of support does Macnica want to provide to customers promoting Open RAN?
Hino: We mainly want to be able to check risks for our customers and support and accompany them in implementing countermeasures. Since the 3G era, Macnica has been providing support for ensuring security for domestic telecommunications carriers. I would like to make full use of that experience in promoting Open RAN.
Tsukada: I myself have experience working in the mobile communications industry, and have experience with the difficulties of introducing and operating networks. We will be able to leverage our many years of experience and know-how to provide support to companies involved in addressing the changes and challenges that Open RAN brings to the telecommunications industry, including through evaluations using the report's checklists. .
